Multiple non tagged subnets
-
I have wired ip cameras that I would like to have in a 10.30.x.x/16 subnet
If I create a vlan for it to be able to assign a new interface with DHCP server and set a device to e.g. 10.30.11.11 I do not seem to be able to ping 10.30.0.1 (interface IP) from that device and am getting no where.When I create a bridge with the LAN interface I run into the problem that I already have a bridge with that interface (10.20.x.x/16) for wired devices of a different type. Going the non tagged route seems to work because I am able to ping 10.20.0.1 (interface IP) from devices in that subnet
How can I have more than 1 non tagged (wired) subnets?
-
Did you create filter rules to allow traffic to/from the VLAN? BTW, unless you're using port based VLANs, VLANs have tags.
-
@jknott the LAN filter rules I have now are to allow any protocol in both directions any to any while I am debugging.
The point is that I am unable to set a vlan tag on IoT devices thus I can not use a vlan because vlans are lndeed like you say tagged. -
huh? If you want to run different networks, ie different L2 networks then you need to physically isolate them, ie different physical interface on pfsense and either different switches, or switch using port based vlans. Or just untagged on the switch port where that network/vlan is connected to pfsense interface
If your going to run actual vlans, where traffic is tagged. Then your switch and pfsense and say your AP needs to be setup correctly for those vlans with the appropriate tags on the correct interface what will carry multiple vlans on the same wire. Be it one vlan is untagged (native) or not.
I run multiple native networks on different pfsense interfaces, and then some interfaces where there is native and tagged vlans.
I use untagged uplink connections from the switch to those physical ports that are untagged, and then for interface that carries vlans, there is an untagged native network, and then also the vlans (tagged) that interface is handling.
Example you can see from here
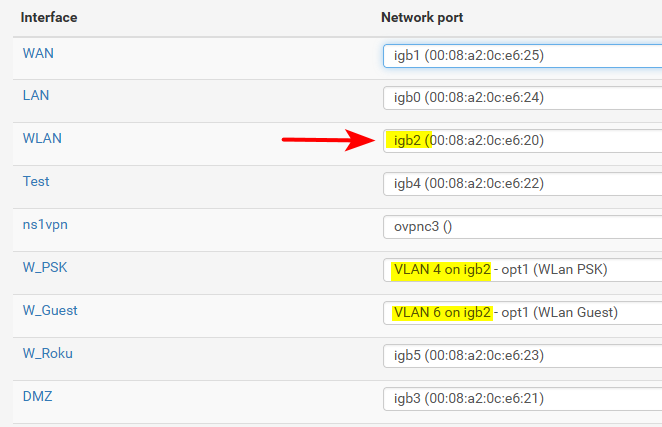
That igb2 has a native untagged network on it, and also I run 2 vlans off that same interface. The native network is untagged, and the 2 vlans 4 and 6 are tagged. All the other interfaces that have other networks on them have no tagging setup on those switch ports. They are just access ports in the correct vlan on the switch to isolate them. But pfsense knows nothing of the tags.
But those vlans are tagged on the uplink from my main switch to another switch I have in my AV cabinet. And on the ports that connects to my APs on either switch they are tagged because the wire is carrying more than 1 vlan. If there is only 1 vlan on a interface then it does not need to be tagged, another term for this is native.
So you can run multiple different networks on your pfsense physical interfaces - you just need to make sure that they are actually isolated L2 networks in your switching infrastructure. Be that with different physical switches, or correctly setup vlans on your switch be those actual 802.1q or port based. And you need to tag them were needed.
You could also run them tagged on pfsense interface without any native (untagged) network. So then it would have to be tagged leaving pfsense, and the switch port. The key to running vlans is understanding tags and when and where to use them.
-
@johnpoz thanks for your in depth response.
Please allow me to expand on my goal.
Having N interfaces, untagged or not, on a single NIC is nothing unheard of. OpenWRT for example supplies this feature via interfaces as alias of another having it's own ip range (subnet), firewall zone, dhcp server and if needed also vlanid.
Now I think I need something without vlan tags because I can't set vlan tags on the devices and I really dont want to add an additional layer of management to have my switch do the tagging.
I know it can work because my tests have confirmed that. I can ping just fine from my vm in an untagged network. And I can only ping from a device in a tagged network if the device actually sends tagged packets. Perhaps some setting I do not know of yet can remove this need.So I hope it is possible with pfsense to get this seeming ly simple use case from the ground without involving a managed switch?
-
Are you talking about multiple subnets on a single interface? Yes, you can do that, but it's generally not a good idea.
-
@jknott great, Can you please show me how it's done on this otherwise awesome piece of software.
I can live with that it might not be a good idea because I simply do not have the luxury of having multiple NIC's :(
-
You do it in Firewall > Virtual IPs.
-
@jknott great, thank you.
Now I have a virtual IP range in the firewall with description 'test virtual interface '
But when I go about setting up firewall rules I do not see the option to create rules for that interface.
I am really glad you all are helping out, but may I please be blunt and wonder if it is this hard for such a generic and straight forward use case then perhaps either documentation wise or perhaps the setup wizard could benefit from an update also taking into account newcomers like myself?
-
@pf_checker said in Multiple non tagged subnets:
Having N interfaces, untagged or not, on a single NIC is nothing unheard of.
Putting multiple IP ranges on the same L2 is just borked - sorry yeah its heard of but its WRONG..
Creating a sub interface is normally tagged.. Sorry but if your just running multiple layer 3 on the same L2 its borked - not secure and going to cause nothing but issues trying to do anything with dhcp.
-
@johnpoz said in Multiple non tagged subnets:
Putting multiple IP ranges on the same L2 is just borked - sorry yeah its heard of but its WRONG..
Yet it's commonplace with IPv6. Even the modem my ISP provides, in gateway mode has both GUA and ULA addresses.
Even with IPv4, there can be reasons to do it, but you'd better know what you're doing and why.
@pf_checker checker
When I set up security cameras, they were always on their own separate network, connected only to the DVR. The DVR had another port that connected to the LAN for access to the cameras through it. In your instance, I would go with a VLAN and managed switch just for the cameras.
-
@jknott said in Multiple non tagged subnets:
Yet it's commonplace with IPv6. Even the modem my ISP provide
My gawd how many times do we have to go over that is NOT the same thing.. Do you put 2 different boxes on the same L2 with different ULA prefixes.. Or do devices on the same L2 use the same prefix for ULA when you do that.
Using a link local address for a box on the same L2 is not the same as trying to run 192.168.10/24 and 192.168.20/24 on the same L2 and expecting them not to talk to each other, or trying to run dhcp on this L2 for multiple address ranges.
-
After my Linux box has been up for a week, it will have 8 GUA addresses, 8 ULA and 1 link local, total of 17 and 2 different subnets. One company I worked for, that provided hosted PBX service would connect a 2nd ADSL modem, with a different subnet for the phones. Because they were on the same network, the phones had to have static addresses, with DHCP for the computers. This isn't the way I would have done it, if it was my choice, but it did work. I would have gone with VLANs.
-
I have no idea why you don't understand this..
Do you have ula's in 2 different prefixes - NO!!
I don't care if you run 30 different IPs in same network... Your point of IPv6 gua and ula and link-local have ZERO to do with running multiple networks that are suppose to be isolated on the same L2..
If I want to isolate device A from device B.. I don't run them on the same L2 and just give A IP address in network A, and B ip address in network B.. Because they are on the same L2 - running multiple networks does not actually isolate them if they are in the same L2.
Your gua, and ula and link local has ZERO to do with that..
-
So how do I proceed setting up multiple subnets on a single NIC without vlanid's?
Or how do I make it possible to assign a static ip address without a vlanid on a vlan interface and have it reachable?
either of these 2 options will get done what needs to get done.
I am open for another option of course as long as that does not involve tinkering with managed switch and or getting another NIC installed.
I can accept if it is not the official way of doing, bad practice even, it as long as I can prevent devices in the IoT subnet from reaching the WAN interface using firewall rules I am happy
-
@johnpoz said in Multiple non tagged subnets:
Do you have ula's in 2 different prefixes - NO!!
I don't, but it is supported with IPv6. Also, as I mentioned, there were 2 subnets, though both NAT, with those hosted PBX phones. Aliases have been around for a long time, even on IPv4. There must have been a reason for it. In the OPs question, I can understand having a 2nd subnet for cameras, as it makes it harder to access them from outside, if NAT isn't set up for that subnet. However, as I mentioned, that would mean static addresses for the cameras. Funny thing, every security camera I have ever set up had a static address.
-
I like a good debate as much as the next guy :)
However, in this scenario I am left kind of confused :(
Am I on the correct forum to ask for help about pfsense related issues? If not then can someone please redirect me?
-
@johnpoz and I often have fun debating some points. I also like to push points that many people misunderstand or don't understand at all. However, as has been pointed out, while doable, 2nd subnets on a LAN are generally not a good idea unless you know what you're doing and why. Your question is not so much a pfsense issue as network configuration. As I mentioned, I would have put cameras on their own separate network. One reason for that is their security is poor, so you want to protect them. As for your rules, you don't have a specific interface to assign them to. The best you can do is assign them to the interface those addresses share, which can get tricky.
-
Like stated before. I am willing to go against the grain and do things not according to the 'rules' / 'convention'
Is one willing and/or able to tell me how to do it? Or perhaps can I conclude that this software and/or community and my goals are not a match?
No disrespect intended and I am still very fond of what you guys have setup. I am just confused at the moment
-
I have already told you what you need to configure a 2nd subnet on an interface and why you don't have a specific interface for your rules. Am I missing something else you need?