DNS Resolver - Content Filtering - NSLOOKUP - Server Unknown
-
Good morning Netgate family...!
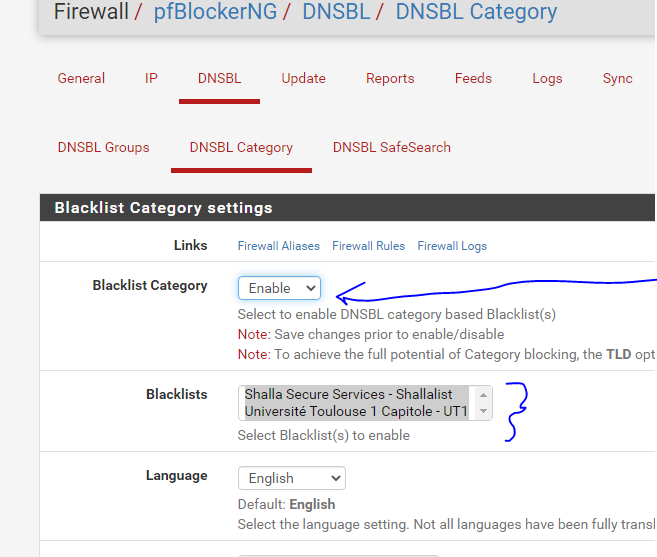
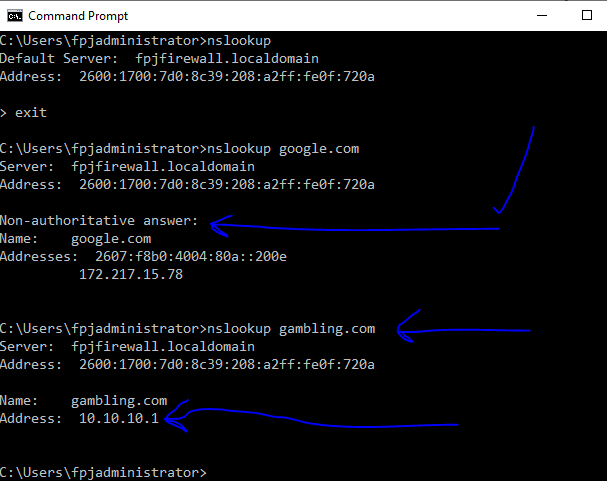
I recently (yesterday) upgraded from 21.02 to 21.05 (SG-3100). Prior to that, an NSLOOKUP from Windows 10 - would point to 10.10.10.1. This gave me an indication that DNS was being referenced internally and using the pfBlocker splash page if someone tried to go to a page protected by the items I click off on for protection such as TOP level items like Shallalist and UT1 (gambling, porn, etc..). After the upgrade to 21.05 the NSLookup is not resolving. I'll show snipits below. I've removed / uninstalled (keeping the pfBlocker settings) and re-installed it after upgrade to 21.05. I've clicked off of DNS Resolver enabled to test and perhaps I didn't wait long enough, but NSLookup still crokes. Anybody have some ideas to help me? I also have an HP multi-function printer that connects to the HP Web Services and it's not connecting out. I don't know if DNS Resolver is messing with that either? After deploying DNS Resolver and Content filtering I never checked the HP Web Services on the printer so I don't know if that is related or not. The idea here is to content filter on the network (home environment). I'd consider the predominant configure rather basic here.
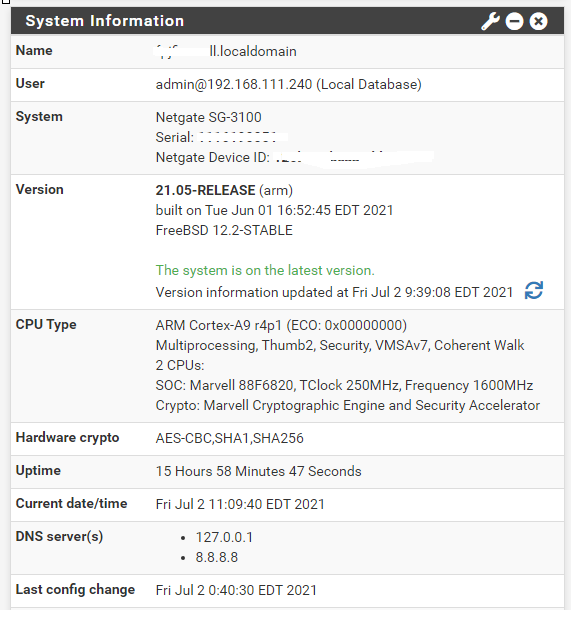
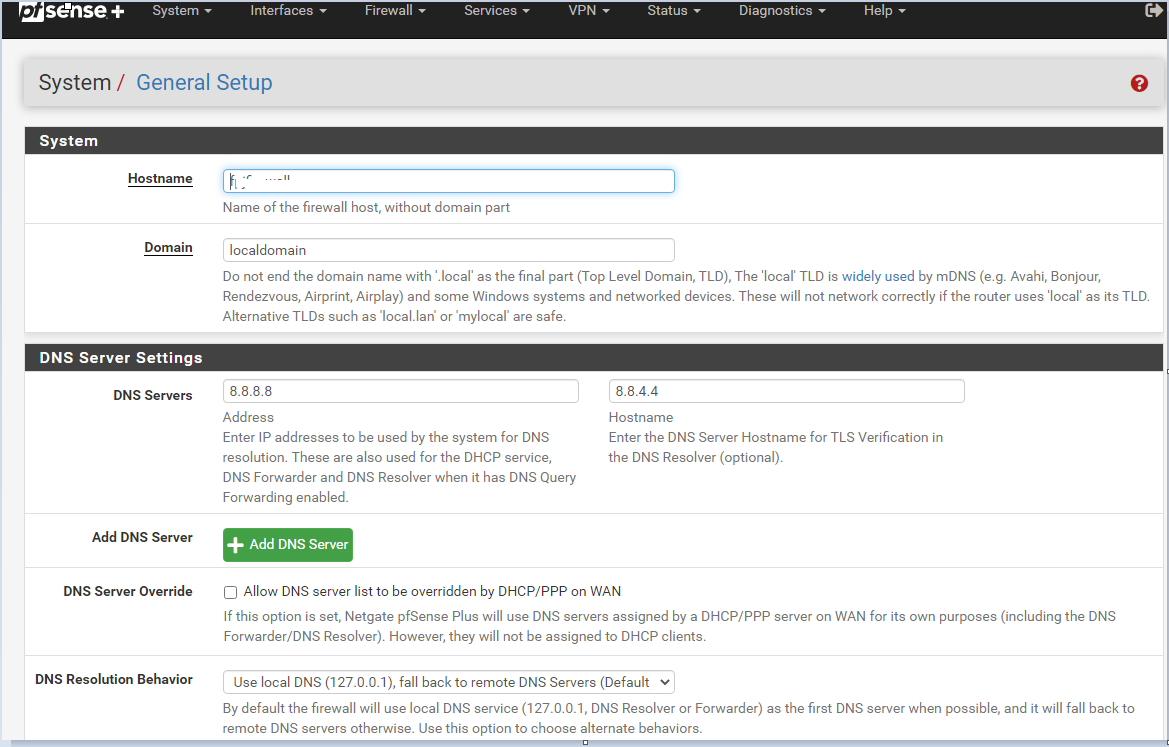

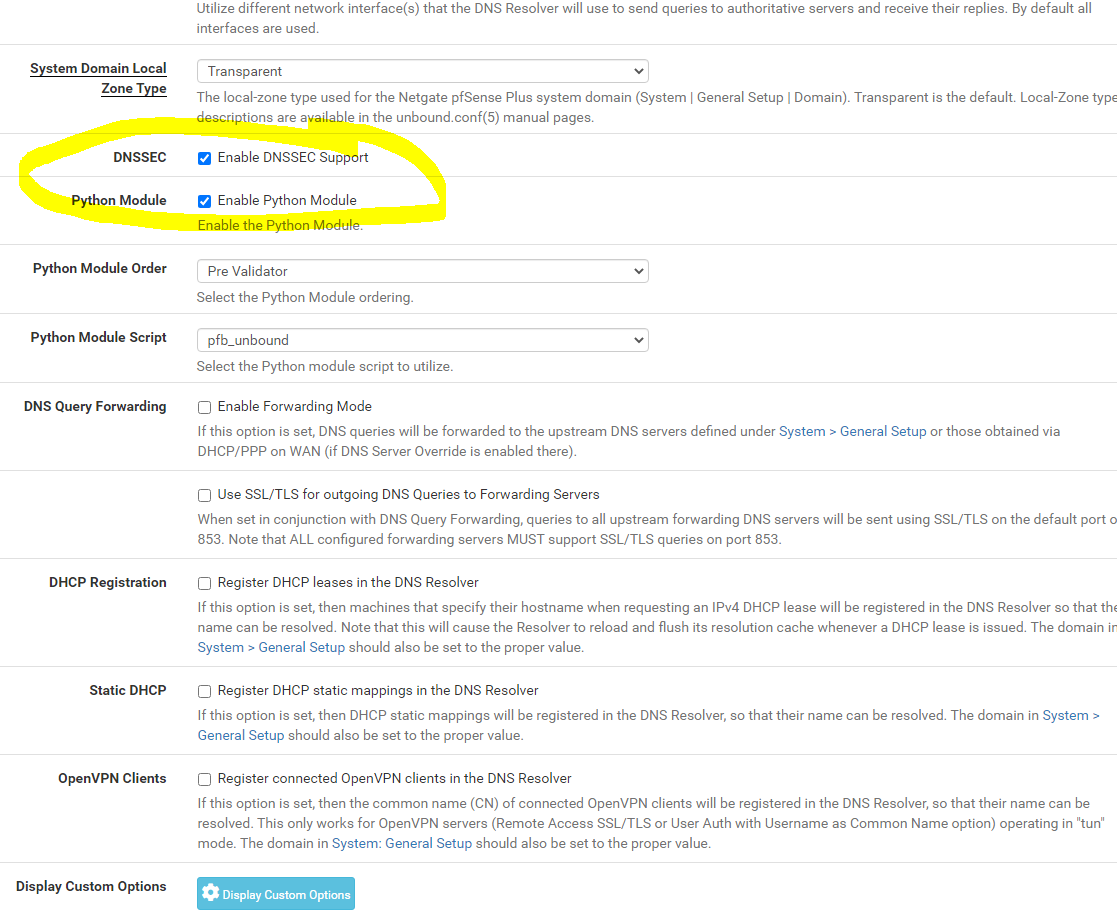
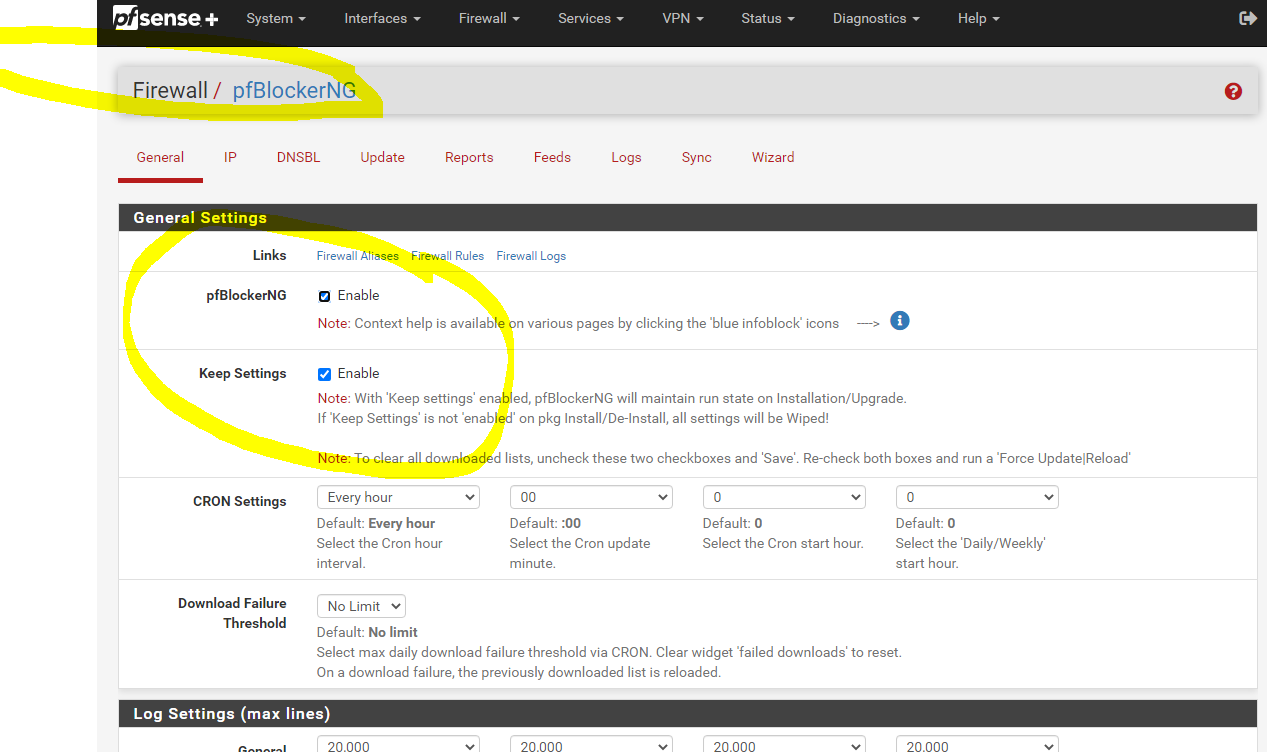
Regards, Franklin
-
This :
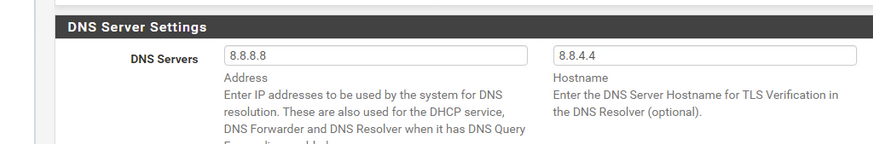
Is unneeded, and even scary.
"8.8.4.4" isn't the hostname of 8.8.8.8 ......
Just delete that "8.8.8.8" - use the default settings and it will be just perfect.I guess you don't quiet understand what the "10.10.10.1" can do for you (very little) but it is not a service that listens for DNS requests. So 'nslookup' doesn't deal with "10.10.10.1".
Except if that "10.10.10.1" is your actual LAN ..... and in that case you actually are in trouble.Can you show the
ipconfig /allfrom your PC ?
DHCP and LAN setting from pfSense - if you decided not the use the default settings.
Btw :
Just forget about this 'thing' :
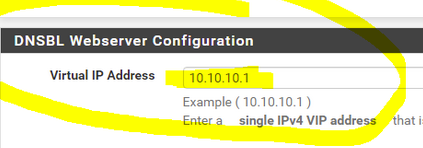
because you can't break TLS/SSL.
And you will not want to break it neither ;)Because my "Win10" PC has default network settings
and
My pfSense has default network settings,
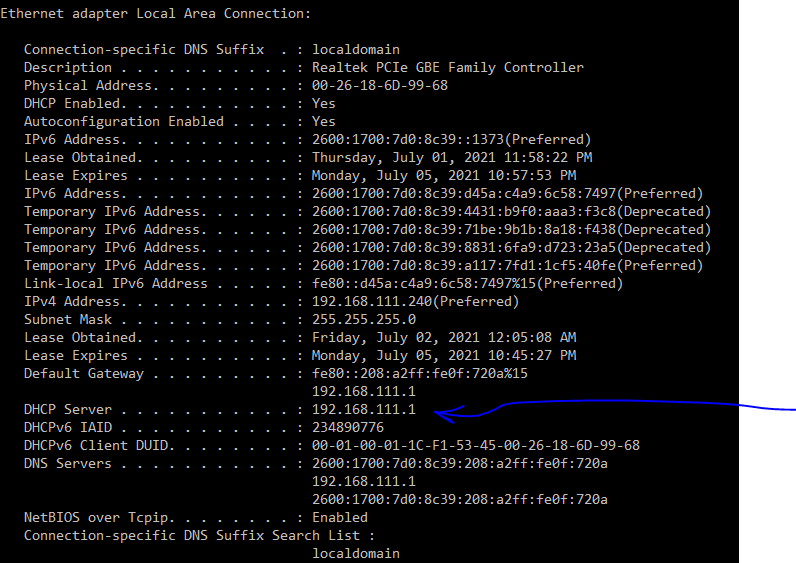
I see aC:\Users\gwkro>nslookup Serveur default : pfsense.my-local-network.net Address: 2001:470:dead:beef:2::1(
It decided to use my IPv6 (pfSense LAN IP) which is actually assigned to me by my IPv6 ISP
It would have been a better demo if it was showing :
Address: 192.168.1.1
which is my pfSense LAN IPv4
))
-
@gertjan - Thanks for the response and help here.
I didn't see the "hostname" where I put 8.8.4.4....I took it out and the 8.8.8.8 as well (Google's DNS servers). I was using them versus my current ISP.
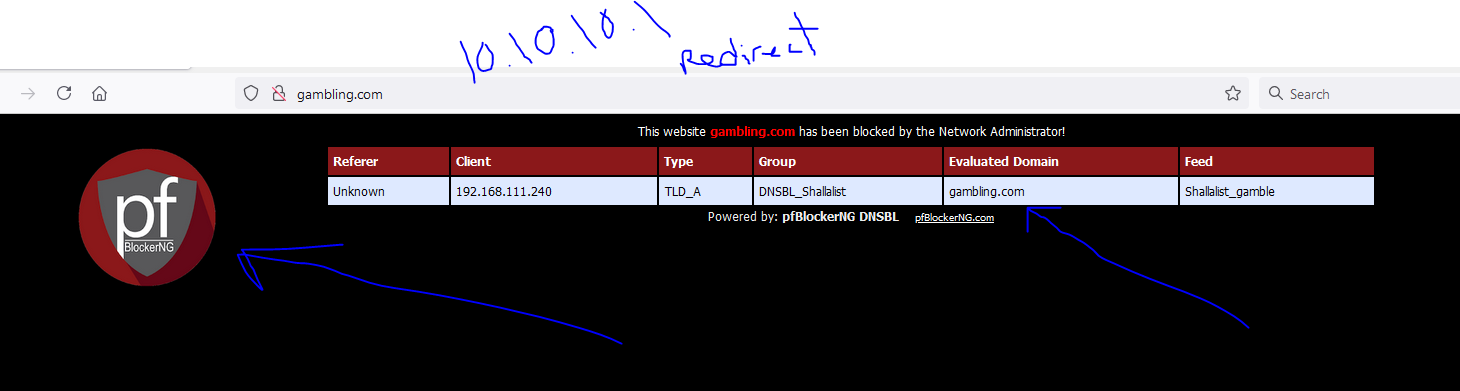
I'm on the 192.168.111.x subnet. At one point, when I set up the content filtering and DNS Resolver, I watched this video and the guy pointed out things to do. When I made those changed and did an nslookup, it pointed-resolved to 10.10.10.1 which gave me the impression it pointed to my pfSense and if someone ended up going to a site that should be blocked, the internal pfBlocker webpage was shown.
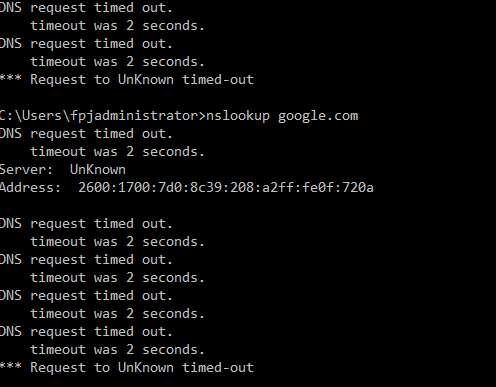
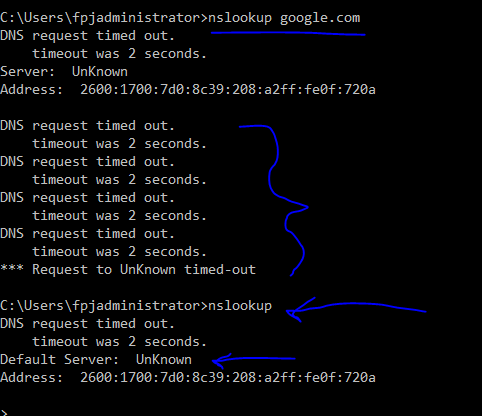
I did do some recent updates for my Windows. I just can't get around why windows is not resolving properly. Why the "DNS Server unknown"? Things are resolving because I can still get out to webpages, but content filtering does not appear to be working.
https://www.youtube.com/watch?v=luXhXisoWhA
My current IP of the network...
-
@detfree23 said in DNS Resolver - Content Filtering - NSLOOKUP - Server Unknown:
I didn't see the "hostname" where I put 8.8.4.4....I took it out and the 8.8.8.8 as well (Google's DNS servers). I was using them versus my current ISP.
See your :
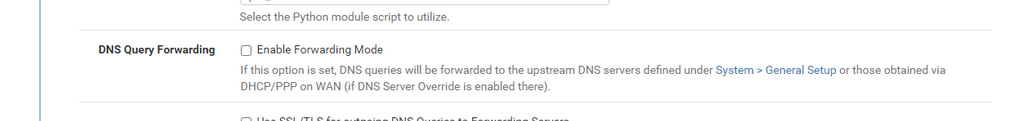
so you are resolving, not forwarding. 8.8.8.8 etc aren't used at all.
The resolver is resolving ;)
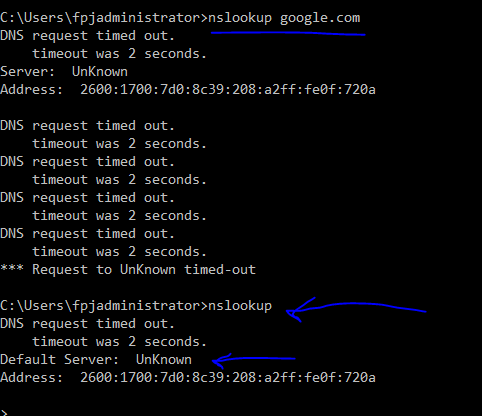
There is no need to add any DNS IP, that's something of the past.Your nslookup examples :
nslookup (or windows actually) prefers IPv6 over IPv4.
Is 2600:1700:7d0:8c39:208;a2ff:fe0f:720a an IPv6 used by pfSense, and is it answering to DNS request over port 53 on this IPv6 ?Type
server 192.168.111.1to force it to use the IPv4 of your LAN.
Now nslookup works ?I guess, when you de activate IPv6 on the interface that your PC uses, the issue is gone..
On the resolver (pfSense) side :
The Services > DNS Resolver > Advanced Settings page :

if this option is uncked, the ACL list isn't taken in account, and unbound just accepts all nternal networks.
If it is checked, check the ACL list, and make sure "2600:1700:7d0:8c39:208;a2ff:fe0f:720a" is part of a listed network.Also : can you
ping -6 2600:1700:7d0:8c39:208;a2ff:fe0f:720a -
@Gertjan - once again, I appreciate your time.
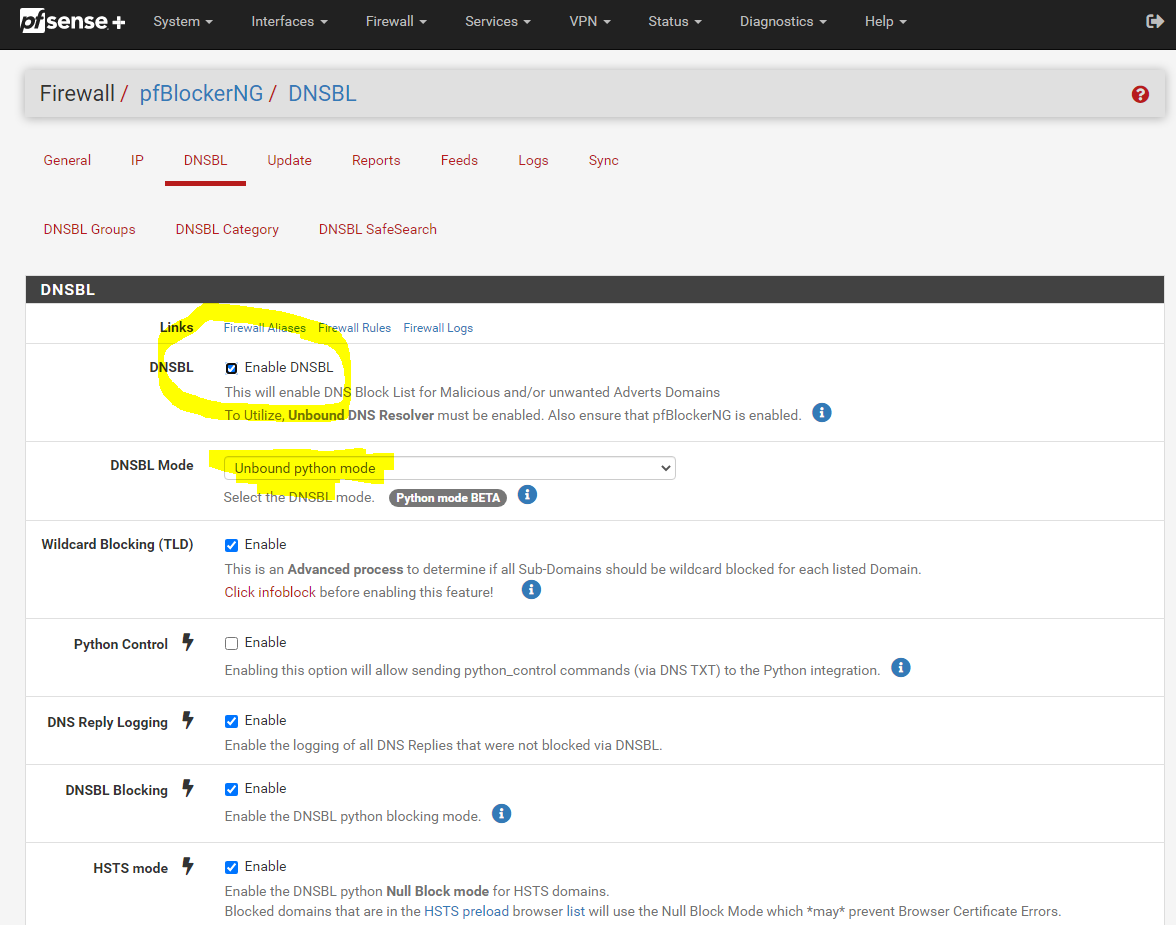
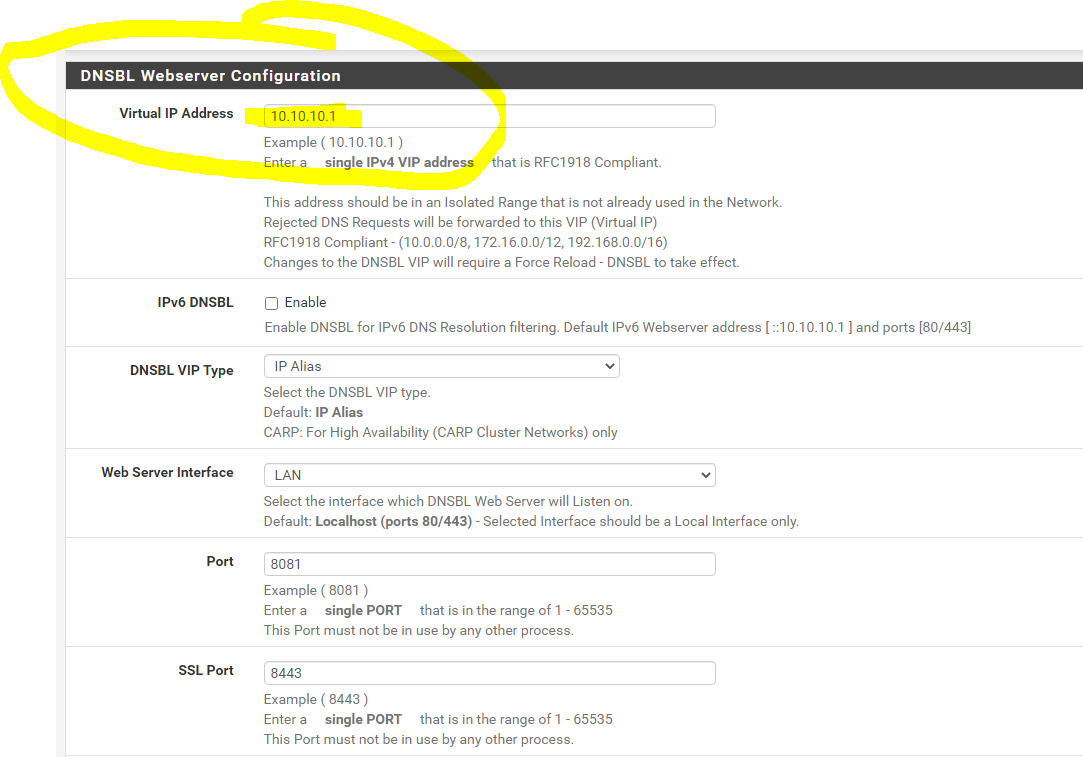
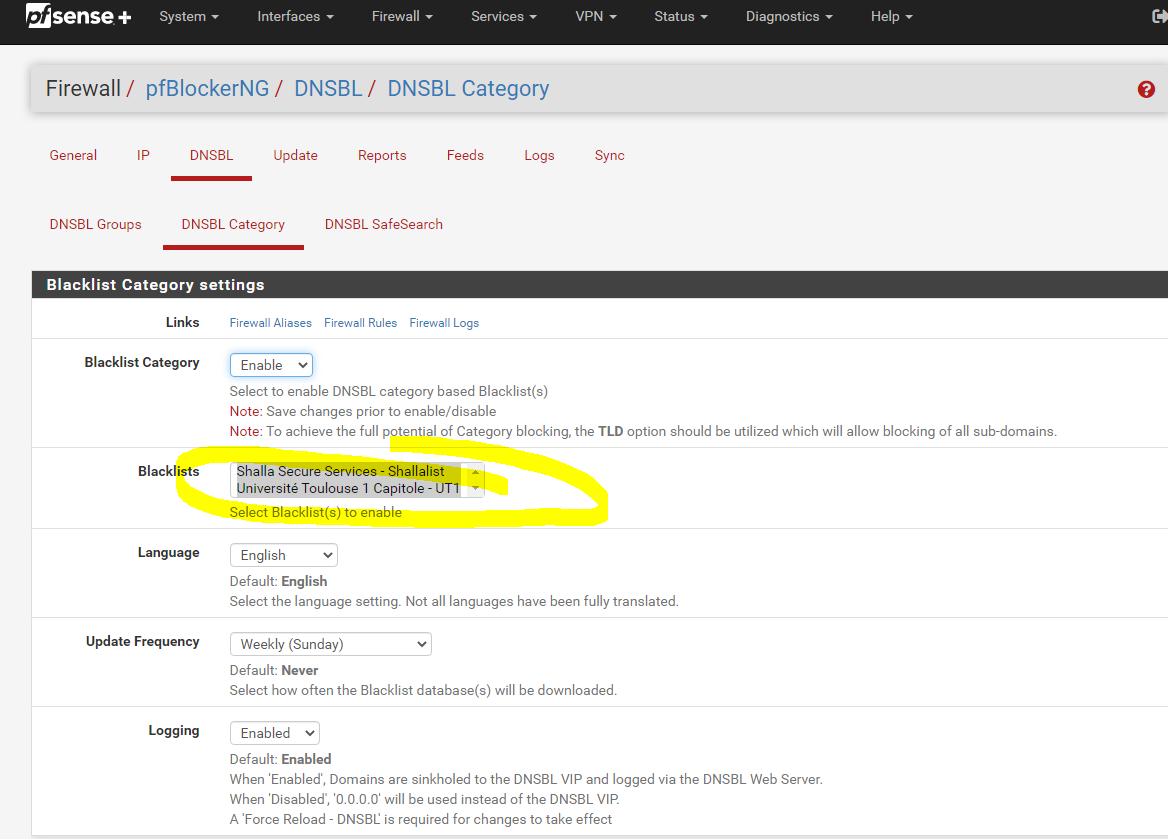
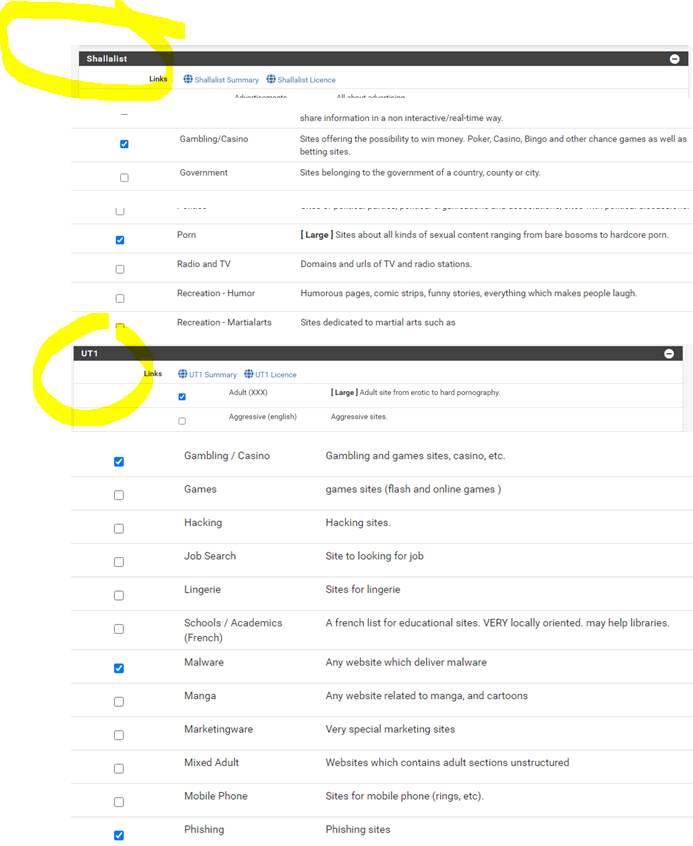
I decided to take the path of least resistance for the moment and I default reset pfBlocker, then reloaded the below, added in my shallalist and UT1. Looks like the redirect IP for sites you can't go to on the lists (10.10.10.1) are working. I'll see how this holds up for the next few days. Unbound python mode because it uses less resources. I think I might enjoy a more robust PC or netgate so I can load up other things like Snort. Are you using a Netgate appliance or a PC of sorts (community pfsense)? Got a recommendation? Franklin