OPENVPN (Site-to-site) tunnel up but no network traffic
-
I have a site-to-site VPN using pfsense 2.5.1, the vpn tunnel is up but when validating the network traffic I noticed that it is sending the requests to the lan interface instead of the tunnel interface.
Site A Lan:192.168.0.0/24
Site B Lan: 192.168.40.0/24tunnel server:
[2.5.1-RELEASE][admin@Firewall.surfamom.local]/root: cat /var/etc/openvpn/server1/config.ovpn
dev ovpns1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto tcp4-server
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local 192.168.1.33
ifconfig 172.17.0.1 172.17.0.2
lport 1197
management /var/etc/openvpn/server1/sock unix
route 192.168.40.0 255.255.255.0
secret /var/etc/openvpn/server1/secret
ncp-disable
cipher AES-128-CBC
allow-compression noTunnel client:
[2.5.1-RELEASE][admin@pfSense.localdomain]/root: cat /var/etc/openvpn/client1/config.ovpn
dev ovpnc1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_client1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto tcp4-client
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local 192.168.15.138
lport 0
management /var/etc/openvpn/client1/sock unix
remote xxx.xxx.X32.54 1197 tcp4-client
ifconfig 172.17.0.2 172.17.0.1
route 192.168.0.0 255.255.255.0
secret /var/etc/openvpn/client1/secret
ncp-disable
cipher AES-128-CBC
allow-compression no
resolv-retry infiniteSome evidence:
Tuneel UP:
Site A
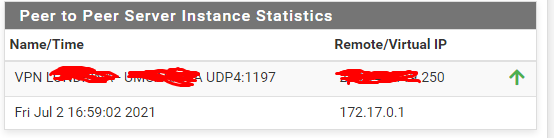
Site B
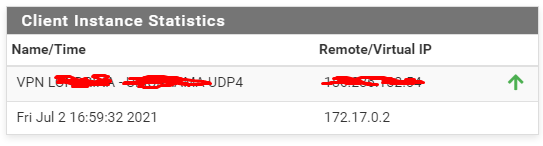
Firewall Rule
Site A
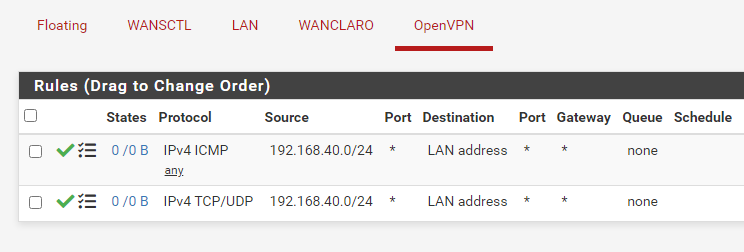
Site B
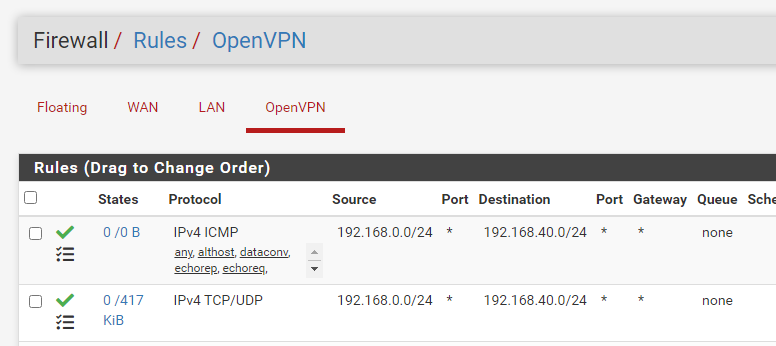
Route Site A
Shell Output - netstat -rn | grep ovpns1
172.17.0.2 link#8 UH ovpns1
192.168.40.0/24 172.17.0.2 UGS ovpns1
fe80::e269:95ff:fe62:ab5%ovpns1 link#8 UHS lo0Route Site B
Shell Output - netstat -rn | grep ovpnc1
172.17.0.1 link#7 UH ovpnc1
192.168.0.0/24 172.17.0.1 UGS ovpnc1
fe80::%ovpnc1/64 link#7 U ovpnc1
fe80::523e:aaff:fe0c:d2af%ovpnc1 link#7 UHS lo0Ping site A to site B
C:\Users\administrador>ping 192.168.40.10 -t
Pinging 192.168.40.10 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.Ping statistics for 192.168.40.10:
Packets: Sent = 3, Received = 0, Lost = 3 (100% loss),
-
@pedrobelliato I would suggest that you modify your OpenVPN rules to allow all while you're getting it working. I have a site to site config running. Do you have a LAN rule to direct the traffic to the OpenVPN interface and the outbound NAT rule?
-
@pedrobelliato
The config looks good. At least one contributing factor is the fact that site A is only allowing incoming traffic to hit the IP assigned to the LAN interface instead of the LAN subnet or an IP on the LAN.My suggestion, collapse the rules on the OpenVPN tab @ both ends into this:
Site A:
Protocol = Any
Source = 192.168.40.0/24
Destination = 192.168.0.0/24Site B:
Protocol = Any
Source = 192.168.0.0/24
Destination = 192.168.40.0/24 -
@KOM , @marvosa thanks for the feedback, the problem occurred after upgrading from version 2.4 to 2.5.1 of pfsense.
I performed a clean install on both sides with version 2.5.1 and recreated the rules again working correctly, I don't know if due to this update there was some inconsistency in the rules or internal routing of pfsense causing the problem.