DNSBL Groups not filtering
-
I have setup easylist dnsbl as follows
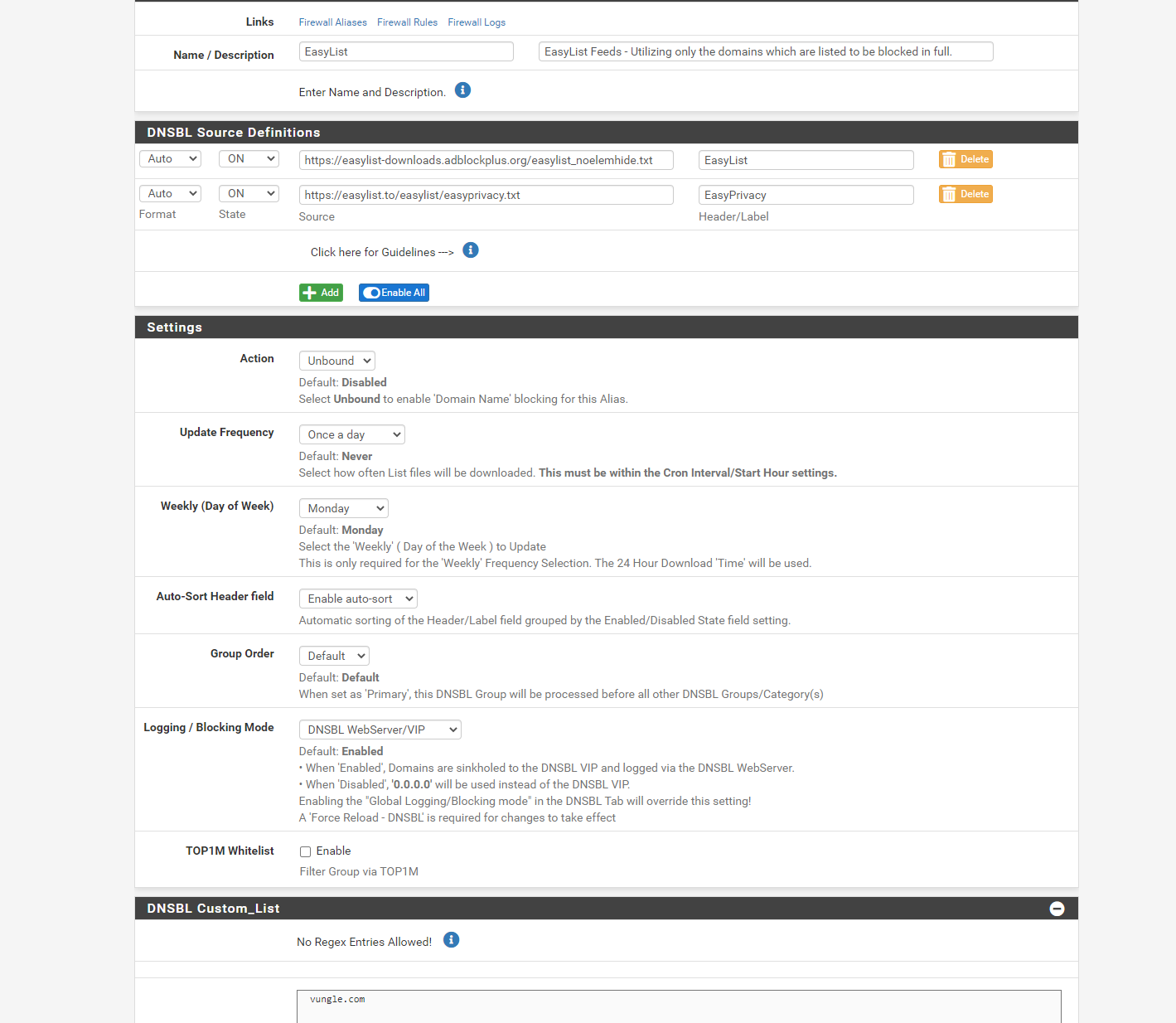
nslookup vungle.com resolves to 10.10.10.1. This should cause a block page to appear. However, it does bring up the page.
My topology is wan ---- cable router ---- netgate 1100 ---- lan
Only netgate 1100 can do wan dns lookup and dns lookups from lan to wan are blocked.
Would anyone have a suggestion how to troubleshoot this. Any help is appreciated.
Thanks in advance.
Roman
-
@rgelfand said in DNSBL Groups not filtering:
nslookup vungle.com resolves to 10.10.10.1.
So, you're fine ;)
As you already know, "10.10.10.1" is what can be considered as a virtual IP(RFC1918) hosted on pfSense.
You can see it using http (not https) access :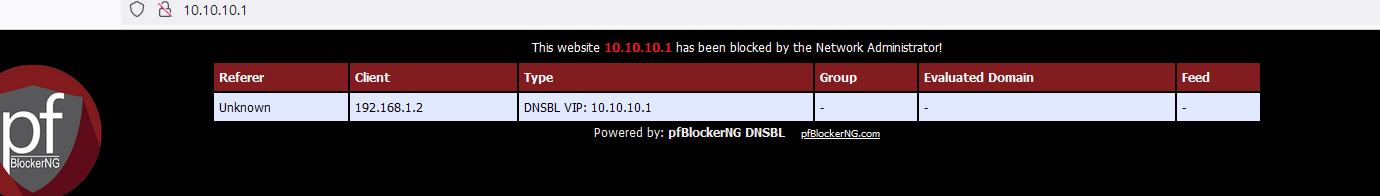
A https access will produce a browser depended error message.

To understand the 'none' issue, you have to know what https or TLS actually means, and how browsers these days related handle failures.
Short example :
You blacklist (DNSBL) twitter.
For reasons you totally already understand, twister can only be accessed using https, not http.
Open a browser, type www.twitter.com and you see .... a failure and certianly not the first image I showed above.
You were not - and your browser focs you to - visit twitter using http.
It was https.And now the good one : you can't "break" https. No one can.
So, yes, your browser, upon an initial DNS request, receives 10.10.10.1, the browser connects on that IP, using port 443.
First of all, the browser asked for certificate info.
In this certificate, it has to find that states it's "*.twitter.com". Thats what https (TLS) is all about.Now, I ask you, does your pfBlockerNG-devel has the certicate that says it's ".twitter.com" ? ;) (Can you have it ??)
Rephrase that.
Are you ".twitter.com". ?
No.The browser hangs up right away. And this means that all blocked DNSBL will not show you the nice image (see above) but a browser that complains, saying that there are protocol errors.
It will only work for plain old "http" accesses and redirects. And these do not exist any more.
Because, again, if you want to visit https://yourbank.tld you can not get redirected to https://thefakebankurl.tldNow you understand why I use :
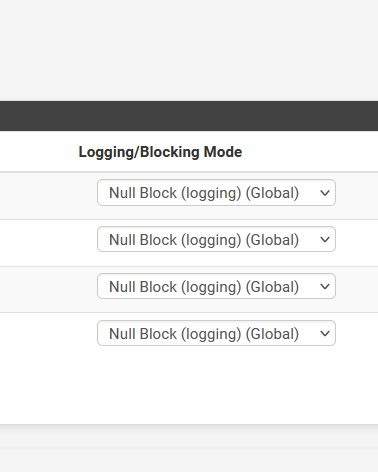
I'm not redirecting to the "10.10.10.1" nice page - but answer a "0.0.0.0" which will make the browser show a message that the requested site "has no DNS" (or some DNS issue) which is actually true.
The most simple answer : Just forget about :
