pfSense as openvpn client - unable to get local issuer certificate
-
I am trying to connect my pfSense box to my OpenVPN server to forward all internet traffic through the VPN server. After setting everything, the connection fails with the following log from the server side. OpenVPN server is working fine with Tunnelblick.
pid=1888 DATA len=945
<IP address>:6375 VERIFY ERROR: depth=0, error=unable to get local issuer certificate: O=pfSense webConfigurator Self-Signed Certificate, CN=pfSense-60e21b76c0db8openvpn[1235]: <IP address>:6375 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
openvpn[1235]: <IP address>:6375 TLS_ERROR: BIO read tls_read_plaintext error
openvpn[1235]: <IP address>:6375 TLS Error: TLS object -> incoming plaintext read error
openvpn[1235]: <IP address>:6375 TLS Error: TLS handshake failed
openvpn[1235]: <IP address>:6375 SIGUSR1[soft,tls-error] received, client-instance restartingclient. ovpn:
client
dev tun
proto udp
remote 94.237.74.248 1194
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
ignore-unknown-option block-outside-dns
block-outside-dns
verb 3
<ca>
-----BEGIN CERTIFICATE-----
xxxxxx
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
xxxxxx
-----END PRIVATE KEY-----
</key>
<tls-crypt>
-----BEGIN OpenVPN Static key V1-----
xxxxxx
-----END OpenVPN Static key V1-----
</tls-crypt>sever.conf
local <IP address>
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key
dh dh.pem
auth SHA512
tls-crypt tc.key
topology subnet
server <IP address> 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS <IP address>"
push "dhcp-option DNS <IP address>"
keepalive 10 120
cipher AES-256-CBC
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
verb 6
crl-verify crl.pem
explicit-exit-notify -
@senaka said in pfSense as openvpn client - unable to get local issuer certificate:
O=pfSense webConfigurator Self-Signed Certificate
Seems you have select the wrong certificate in the client settings.
Did you already import the CA cert and the client cert on pfSense?
-
@viragomann said in pfSense as openvpn client - unable to get local issuer certificate:
@senaka said in pfSense as openvpn client - unable to get local issuer certificate:
O=pfSense webConfigurator Self-Signed Certificate
Seems you have select the wrong certificate in the client settings.
Did you already import the CA cert and the client cert on pfSense?
I just copied certificates (CA cert and the client cert) from "client.ovpn" file and pasted the content at pfSense. Is there any water to import them from client.ovpn?
-
@senaka
So you will have set a distinct name for the client certificate, which you have to select on the client config page. -
-
@senaka
Using a server certificat for a client seems not evident to me at all. -
@viragomann
I am not sure what step I have missed. Is there any good step by step guide for this in Internet to follow?Really appreciate your time.
-
@senaka
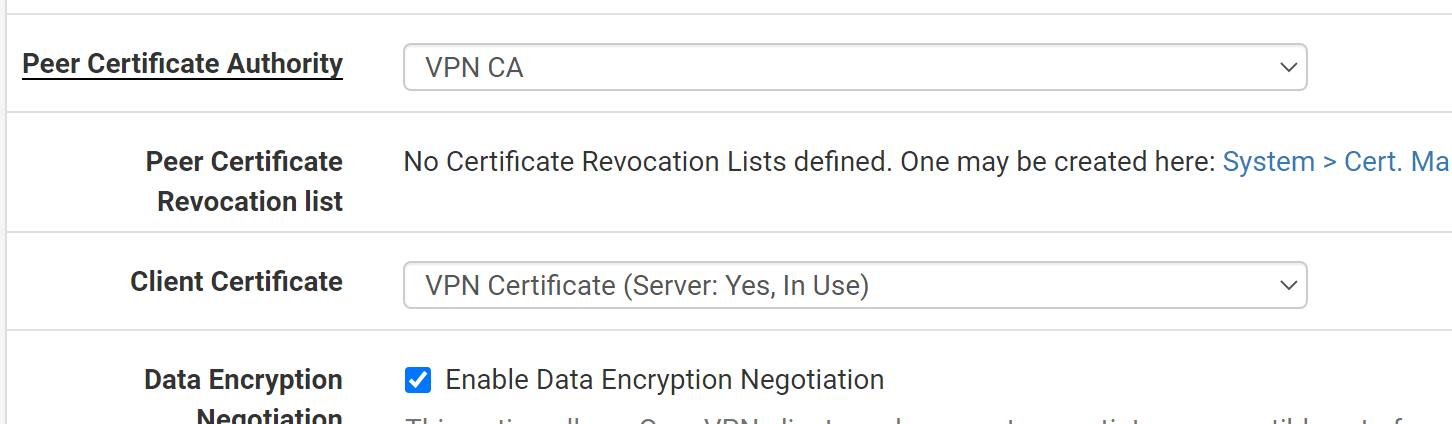
Dude! Again, you are using a wrong client certificate!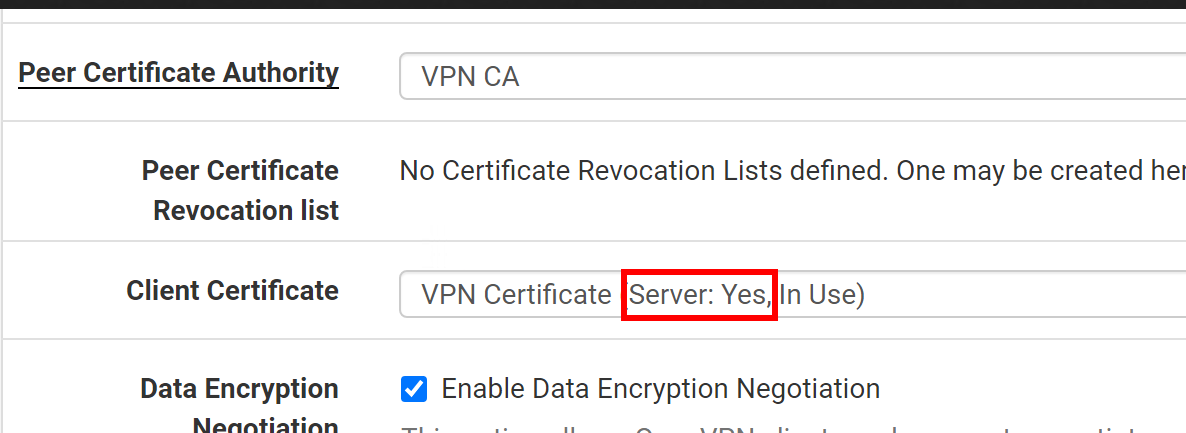
As you can read, that's a server certificate, but you need a client cert.
You have to import the CA cert from the OpenVPN file (public key) and the client cert (public and private key).
pfSense should recognize it correctly as client cert: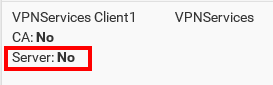
You might also find a TLS key in the file. This section you have to put into the TLS key box in the client settings:
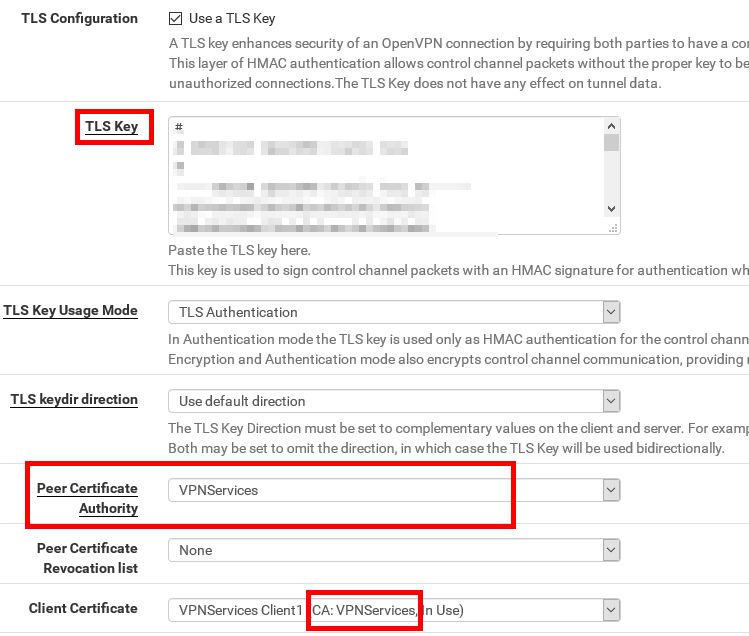
The client cert has to match to the used CA.
-
Thanks a million! You have done a great job by marking all the places to check. I have used a wrong client.ovpn file. With your help, the hard work of 3 days ended with a success.