[noob question] pfSense as a OpenVPN client for selected devices
-
Hi
I'm l looking for some tutorial to create OpenVPN client but to make only selected devices (IPs) to go through it. I found one guide but it was from 2014 using v2.1 and I'm not sure if it's still accurate enough.
I don't want to use full instruction from VPN provider because they assume I want everything to go through the VPN connection and they also change DSN Resolver settings and I'm not sure that's something that is really needed as those were not touched in that old guide.My understanding is that:
- First I need to create OpenVPN client with settings that are provided from VPN provider.
- Then I need to add interface with this client.
- And then set rule that will use Gateway in Advanced section to set it to this new interface and thus forcing selected IP range to use it instead of regular WAN.
Is that all?
-
@draghmar
In the OpenVPN client settings you have to check "Don't pull routes" to avoid that you get pushed the default route by the provider.And then set rule that will use Gateway in Advanced section to set it to this new interface and thus forcing selected IP range to use it instead of regular WAN.
Consider that a policy routing rule does not allow any internal access for the matching devices.
If have the destination any in the rule and for instance need DNS access to pfSense you have to add an additional rule for the concerning devices without the gateway option and put it to the top of the rule set. -
Yeah...I failed...miserably. :D
I followed this old guide with few exceptions:- I created CA and OpenVPN Client based on NordVPN guide with UDP.
- I didn't do anything in NAT Outbound because I have this set to Hybrid with one custom mapping and wasn't sure if it's actually needed to change there anything.
- I didn't create base rule for LAN devices (last step in the guide) that should go through default gateway as this one was already there.
So knowing that I did get VPN Gateway up and even some small transfer was visible on the Traffic Graph. But the device I was testing this on couldn't get net. So I know I did something wrong but because it's all new to me I don't know what to look for. I didn't see in OpenVPN logs anything obvious that would scream "ERROR" at me. ;) The only thing that looked suspicious was that:
MANAGEMENT: Client disconnected MANAGEMENT: CMD 'status 2' MANAGEMENT: CMD 'state 1' MANAGEMENT: Client connected from /var/etc/openvpn/client1/sockAnd this shows up periodically in the logs.
I tried to ping and traceroute using VPN as a source and it did work. This is especially visible with traceroute because I can see that when using WAN I'm getting far less hoops than with VPN. Which would indicate that there's some routing issue between the device and VPN connection.
My best guess it NAT but I'm a little bit afraid of messing around with it. :P
-
Hm...I did get some courage to make changes to the NAT Outbound. The main issue I had there was that I couldn't set specific IP address...So I used Alias and it looks like it works.
-
Weird behavior: I have to restart both service and device connection in order to get through VPN when changing something. For example if I change VPN server I have to restart service after saving options (that is quite logical) but then I have to disconnect device and reconnect it because without this it fell of VPN and goes through WAN.
-
@draghmar
You can check System > Advanced > Miscellaneous > Do not create rules when gateway is down to prevent this. -
@viragomann I did that before followed bits of this guide, so I do have this option checked. But maybe it needs some additional restarting to get into work?
-
@draghmar
No, it should be applied immediatly w/o a reboot. -
@viragomann Then it doesn't do what it suppose to...wonder why. Probably some config error on my side. ;)
Edit: I remembered that I unchecked your first suggestion
Don't pull routeswhen testing. Maybe it has something to do with that? I'll check what will happen with this option tomorrow. -
@draghmar
"Don't pull routes" prevents that the default route is changed to the vpn provider, when the client connection is established.
If you leave this unchecked and the provider pushes the default route to you (what I assume) the whole upstream traffic from you local network is directed over the vpn, which is not that, what you want as you stated above. -
@viragomann Hm...I get it but I didn't see that behavior. I mean, only the two devices I was testing with, had their traffic pushed through VPN. Other devices did not. Anyway, I have the whole setup disabled currently and will check that option tomorrow. Thanks for suggestions and explanation. :)
-
Another report from VPN battlefield. ;)
So it works for me but I've notice that some detection tools still know that I'm using VPN even though I tested on different servers and at least one knew my own IP for some reason. I didn't do anything to DNS settings. Should I change something? My brother suggested that services may detect VPN by checking DNS somehow, so maybe I should do something...But is there a way to make it work in a way that everything goes as usual except for VPN traffic? Maybe I should set DNS Resolver'sOutgoing Network Interfacesto everything except VPN interface? -
@draghmar
Yes, that might be detected by leaking DNS.You can setup the resolver to send request out to the VPN interface only. However, this setting is applied also to DNS requests from other devices, which possibly isn't desired.
To affect only these certain devices you're directing out to the VPN, you can simply forward DNS traffic from the concerned devices to a public DNS server and policy route this traffic to the VPN gateway.
-
@viragomann I have one rule that directs all requests that would go outside of LAN on port 53 to local. If I would put rule above that one, where specific IPs would be directed to DNS IP from VPN provider, would that work I think it should?
-
@draghmar
Should work that way. -
Because I'm a little bit afraid I'm going to break something with DNS I'll ask if what I want to do is ok. :P
I have Port Forward set using this recipe. My idea is to create alias with DNS from NordVPN and then create new Port Forward, above previous one. Choosing LAN as a interace I will add specific devices in the source field for port 53, destination will beset to
anyfor port 53 and redirect IP to VPN DNS alias.
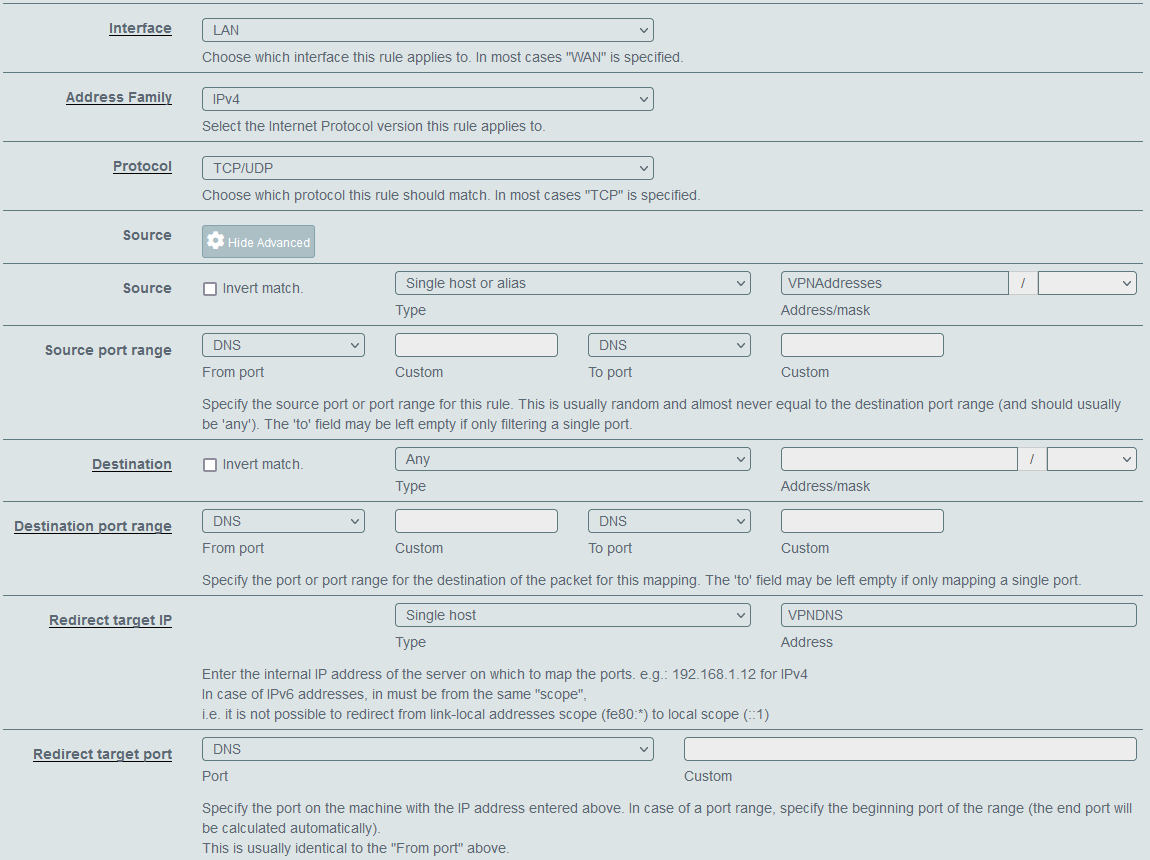
Will that be enough?
I saw in OpenVPN'sClient Specific Overridesthat I can set there DNS. Should I do that? I'd guess not but who knows. ;) -
@draghmar said in [noob question] pfSense as a OpenVPN client for selected devices:
Will that be enough?
The forwarding looks well, but you have also to direct that traffic to the VPN provider. This isn't done by NAT.
You have to add a policy routing rule with the VPNDNS alias as destination and set the gateway to the VPN.I saw in OpenVPN's Client Specific Overrides that I can set there DNS.
This is used by VPN access servers to set certain directives for specific clients. It cannot be used in your case.
Consider that the your "VPNAdresse"s may possibly use DoH for name resolution. To cover this, you have to direct their HTTPS upstream traffic to the VPN server by poilcy routing.
-
@viragomann said in [noob question] pfSense as a OpenVPN client for selected devices:
The forwarding looks well, but you have also to direct that traffic to the VPN provider. This isn't done by NAT.
You have to add a policy routing rule with the VPNDNS alias as destination and set the gateway to the VPN.Isn't that added automatically? I have a rule like that from creating Port Forward from the recipe. I guess I'd have to edit this new one then to set VPN Gateway in advanced settings, right?
-
@draghmar
Depends on the rule creation option:
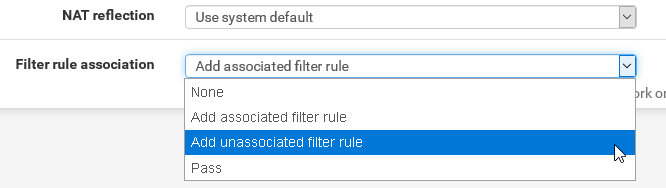
However, pfSenes cannot create a policy rule from a NAT, since there is no gateway info.
So at best you can let it create an unassociated filter rule and edit it after to set the gateway.
-
@viragomann I think I did everything but https://dnsleaktest.com still is able to detect my IP. :( I have Port Forward set as above and in the created rule I changed gateway to VPN one. What else am I missing?