I am unable to connect to OpenVPN Server
-
Hello,
I am unable to establish OpenVPN connection to OpenVPN server configured on pfsense.
I get a message, in Client log file:- added as an attachment to avoid akismed...Pfsense - post contecnt.txt
Firewall rule is attached below:
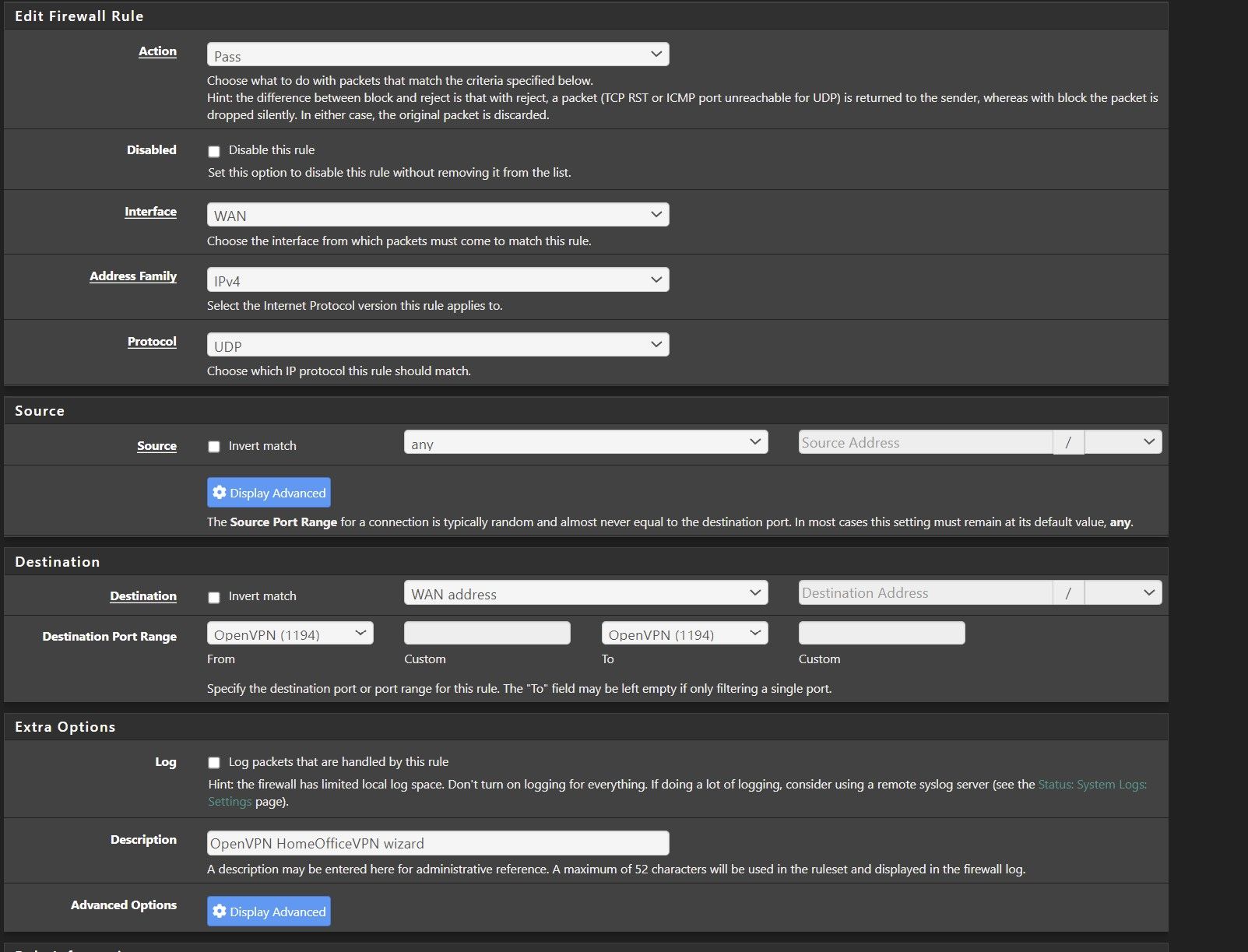
I know this issue has been already discussed many times, although no solution works for me so far :/
Please advise.
-
@jacekgle
Add this line to the client config:lport 0 -
@viragomann said in I am unable to connect to OpenVPN Server:
lport 0
Thank you for your help, I am one step further. Although now it looks like that:
Client side:Wed Jul 21 16:24:13 2021 OpenVPN 2.5.2 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021 Wed Jul 21 16:24:13 2021 Windows version 10.0 (Windows 10 or greater) 64bit Wed Jul 21 16:24:13 2021 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10 Wed Jul 21 16:24:15 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]MYEDITED_IP:1194 Wed Jul 21 16:24:15 2021 UDPv4 link local (bound): [AF_INET][undef]:0 Wed Jul 21 16:24:15 2021 UDPv4 link remote: [AF_INET]MYEDITED_IP:1194 Wed Jul 21 16:25:15 2021 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Wed Jul 21 16:25:15 2021 TLS Error: TLS handshake failed Wed Jul 21 16:25:15 2021 SIGUSR1[soft,tls-error] received, process restarting Wed Jul 21 16:25:20 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]MYEDITED_IP:1194 Wed Jul 21 16:25:20 2021 UDPv4 link local (bound): [AF_INET][undef]:0 Wed Jul 21 16:25:20 2021 UDPv4 link remote: [AF_INET]MYEDITED_IP:1194Server side:
Jul 21 16:24:26 openvpn 45804 DEPRECATED OPTION: ncp-disable. Disabling cipher negotiation is a deprecated debug feature that will be removed in OpenVPN 2.6 Jul 21 16:24:26 openvpn 45804 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning. Jul 21 16:24:26 openvpn 45804 WARNING: POTENTIALLY DANGEROUS OPTION --verify-client-cert none|optional may accept clients which do not present a certificate Jul 21 16:24:26 openvpn 45804 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021 Jul 21 16:24:26 openvpn 45804 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10 Jul 21 16:24:26 openvpn 45914 NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet. Jul 21 16:24:26 openvpn 45914 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Jul 21 16:24:26 openvpn 45914 WARNING: experimental option --capath /var/etc/openvpn/server1/ca Jul 21 16:24:26 openvpn 45914 TUN/TAP device ovpns1 exists previously, keep at program end Jul 21 16:24:26 openvpn 45914 TUN/TAP device /dev/tun1 opened Jul 21 16:24:26 openvpn 45914 /sbin/ifconfig ovpns1 10.1.1.1 10.1.1.2 mtu 1500 netmask 255.255.255.0 up Jul 21 16:24:26 openvpn 45914 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 10.1.1.1 255.255.255.0 init Jul 21 16:24:26 openvpn 45914 UDPv4 link local (bound): [AF_INET]192.168.0.8:1194 Jul 21 16:24:26 openvpn 45914 UDPv4 link remote: [AF_UNSPEC] Jul 21 16:24:26 openvpn 45914 Initialization Sequence Completed Jul 21 14:24:26 openvpn 42936 event_wait : Interrupted system call (code=4) Jul 21 14:24:26 openvpn 42936 SIGTERM[hard,] received, process exiting Jul 21 16:24:27 openvpn 73370 WARNING: file '/var/etc/openvpn/client2/up' is group or others accessible Jul 21 16:24:27 openvpn 73370 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021 Jul 21 16:24:27 openvpn 73370 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10 Jul 21 16:24:27 openvpn 73370 neither stdin nor stderr are a tty device and you have neither a controlling tty nor systemd - can't ask for 'Enter Auth Password:'. If you used --daemon, you need to use --askpass to make passphrase-protected keys work, and you can not use --auth-nocache. Jul 21 16:24:27 openvpn 73370 Exiting due to fatal error -
@jacekgle
Seems you're running multiple OpenVpN isntances on the server. Not all log lines are belonging to that one which you try to connect to here.Form the client log I suspect that the client is not able to reach the server.
You server is listening to a privat IP, so you have to forward the OpenVPN traffic to it properly. Did you do that? -
@viragomann
How cna I find out whats wrong?These are more client logs:
Wed Jul 21 19:40:24 2021 SIGUSR1[soft,tls-error] received, process restarting Wed Jul 21 19:40:24 2021 MANAGEMENT: >STATE:1626889224,RECONNECTING,tls-error,,,,, Wed Jul 21 19:40:24 2021 Restart pause, 5 second(s) Wed Jul 21 19:40:29 2021 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 19:40:29 2021 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 19:40:29 2021 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 19:40:29 2021 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 19:40:29 2021 MANAGEMENT: >STATE:1626889229,RESOLVE,,,,,, Wed Jul 21 19:40:29 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]Wed Jul 21 20:24:21 2021 NOTE: --user option is not implemented on Windows Wed Jul 21 20:24:21 2021 NOTE: --group option is not implemented on Windows Wed Jul 21 20:24:21 2021 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning. Wed Jul 21 20:24:21 2021 OpenVPN 2.5.2 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021 Wed Jul 21 20:24:21 2021 Windows version 10.0 (Windows 10 or greater) 64bit Wed Jul 21 20:24:21 2021 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10 Wed Jul 21 20:24:21 2021 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340 Wed Jul 21 20:24:21 2021 Need hold release from management interface, waiting... Wed Jul 21 20:24:22 2021 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340 Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'state on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'log all on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'echo all on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'bytecount 5' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'hold off' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'hold release' Wed Jul 21 20:24:22 2021 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 20:24:22 2021 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 20:24:22 2021 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 20:24:22 2021 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 20:24:22 2021 MANAGEMENT: >STATE:1626891862,RESOLVE,,,,,, Wed Jul 21 20:24:22 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]EDITED_IP:53647 Wed Jul 21 20:24:22 2021 Socket Buffers: R=[65536->65536] S=[65536->65536] Wed Jul 21 20:24:22 2021 UDP link local (bound): [AF_INET][undef]:0 Wed Jul 21 20:24:22 2021 UDP link remote: [AF_INET]EDITED_IP:53647 Wed Jul 21 20:24:22 2021 MANAGEMENT: >STATE:1626891862,WAIT,,,,,, Wed Jul 21 20:25:22 2021 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Wed Jul 21 20:25:22 2021 TLS Error: TLS handshake failed Wed Jul 21 20:25:22 2021 SIGUSR1[soft,tls-error] received, process restarting Wed Jul 21 20:25:22 2021 MANAGEMENT: >STATE:1626891922,RECONNECTING,tls-error,,,,, Wed Jul 21 20:25:22 2021 Restart pause, 5 second(s):53647 Wed Jul 21 19:40:29 2021 Socket Buffers: R=[65536->65536] S=[65536->65536] Wed Jul 21 19:40:29 2021 UDP link local (bound): [AF_INET][undef]:0 Wed Jul 21 19:40:29 2021 UDP link remote: [AF_INET]MYEDITED_IP:53647 Wed Jul 21 19:40:29 2021 MANAGEMENT: >STATE:1626889229,WAIT,,,,,, Wed Jul 21 19:41:29 2021 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Wed Jul 21 19:41:29 2021 TLS Error: TLS handshake failed -
I have created completly new OpenVPN Server on TrueNAS server, while disabling the pfsense before.
I have the same issue of
openvpn TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)I have no idea how to workaround it. I am even trying to conneect to VPN Server internall, having internal IP in the ovpn config file - still the same.
I have already re-created all 3 certificates, 3 times. I am out of ideas.
-
My latest client config:
client dev tun proto udp port 53647 remote "my.fqdn.com" user nobody group nobody persist-key persist-tun lport 0 <certificates> verb 3 remote-cert-tls server auth RSA-SHA1 cipher AES-256-CBC <TLS key>Result:
Wed Jul 21 20:24:21 2021 NOTE: --user option is not implemented on Windows Wed Jul 21 20:24:21 2021 NOTE: --group option is not implemented on Windows Wed Jul 21 20:24:21 2021 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning. Wed Jul 21 20:24:21 2021 OpenVPN 2.5.2 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 21 2021 Wed Jul 21 20:24:21 2021 Windows version 10.0 (Windows 10 or greater) 64bit Wed Jul 21 20:24:21 2021 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10 Wed Jul 21 20:24:21 2021 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340 Wed Jul 21 20:24:21 2021 Need hold release from management interface, waiting... Wed Jul 21 20:24:22 2021 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340 Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'state on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'log all on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'echo all on' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'bytecount 5' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'hold off' Wed Jul 21 20:24:22 2021 MANAGEMENT: CMD 'hold release' Wed Jul 21 20:24:22 2021 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 20:24:22 2021 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 20:24:22 2021 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Wed Jul 21 20:24:22 2021 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Wed Jul 21 20:24:22 2021 MANAGEMENT: >STATE:1626891862,RESOLVE,,,,,, Wed Jul 21 20:24:22 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]EDITED_IP:53647 Wed Jul 21 20:24:22 2021 Socket Buffers: R=[65536->65536] S=[65536->65536] Wed Jul 21 20:24:22 2021 UDP link local (bound): [AF_INET][undef]:0 Wed Jul 21 20:24:22 2021 UDP link remote: [AF_INET]EDITED_IP:53647 Wed Jul 21 20:24:22 2021 MANAGEMENT: >STATE:1626891862,WAIT,,,,,, Wed Jul 21 20:25:22 2021 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Wed Jul 21 20:25:22 2021 TLS Error: TLS handshake failed Wed Jul 21 20:25:22 2021 SIGUSR1[soft,tls-error] received, process restarting Wed Jul 21 20:25:22 2021 MANAGEMENT: >STATE:1626891922,RECONNECTING,tls-error,,,,, Wed Jul 21 20:25:22 2021 Restart pause, 5 second(s) -
I have disabled my main firewall - no difference.
-
@jacekgle
No way to help, when you don't respond to my questions. Sorry. -
@viragomann said in I am unable to connect to OpenVPN Server:
You server is listening to a privat IP, so you have to forward the OpenVPN traffic to it properly. Did you do that?
I have forwarded traffic on my router to the VPN Server.
I use dynDNS to resolve the IP. So in my config file I have that, and as i try to connect - it resolved correctly.Also i replaced the dyndns with WAN IP address in client config file.
Same result.I have other web server on my local NAS box and i can connect to it.
-
@jacekgle
As I wrote above, from the clients log I suspect that the client cannot reach the server, though the firewall on pfSense allows it.
Possibly UDP 1194 is blocked by your ISP or it cannot pass the router.To investigate, you will have to sniff the traffic on some interfaces.
On pfSense you can use the Packets Capture tool in the Diagnostics menu to do this. Select the WAN, enter 1194 into the port filter box, start the capture and try a connection from outside.Maybe you have also a possibility on your router in front of pfSense to sniff the traffic and on the client side to get sure what's going on.
-
@viragomann
@viragomann
Thank you so much for your reply. I have managed to do some magic by following this forum discussion:www.truenas.com/community/threads/truenas-12-openvpn-service-testing.85461/page-2