-
I upgraded my hardware and installed the latest 2.5.2-RELEASE.
After restoring the configuration from the old 2.4.5-p1 installation/hardware and mapping interfaces everything is working except OpenVPN clients.
When I try to start OpenVPN client on my new setup I get this error:
Jul 21 14:53:39 openvpn 57939 Exiting due to fatal error
Jul 21 14:53:39 openvpn 57939 Cannot load certificate file /var/etc/openvpn/client3/cert
Jul 21 14:53:39 openvpn 57939 OpenSSL: error:140AB18E:SSL routines:SSL_CTX_use_certificate:ca md too weak
Jul 21 14:53:39 openvpn 57939 Initializing OpenSSL support for engine 'devcrypto'I checked and the /var/etc/openvpn/client3/cert exists.
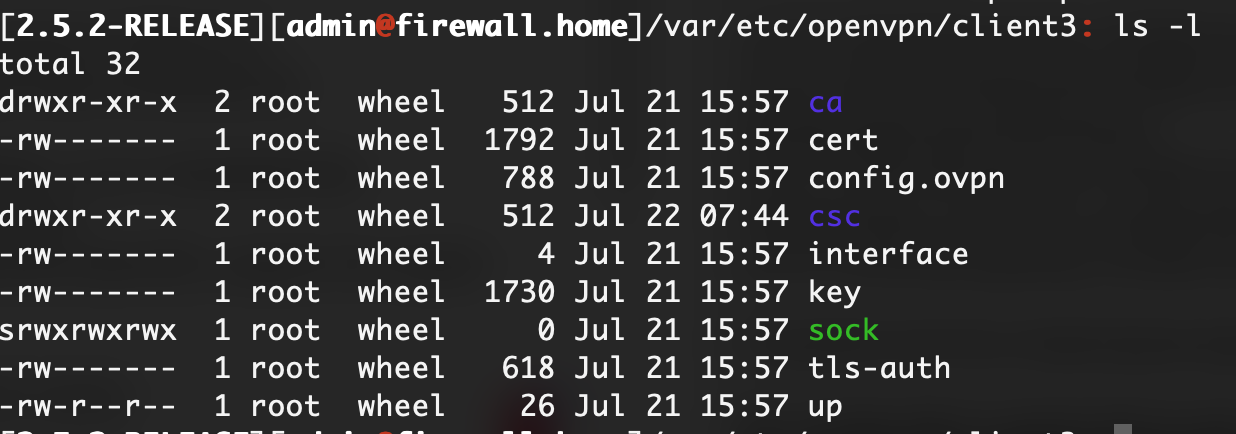
So, this is possibly related to the previous message:
OpenSSL: error:140AB18E:SSL routines:SSL_CTX_use_certificate:ca md too weakAny suggestions on how to fix this?
Thanks.
-
Answering my own question...
Adding this string to custom options allows things to work:
tls-cipher "DEFAULT:@SECLEVEL=0"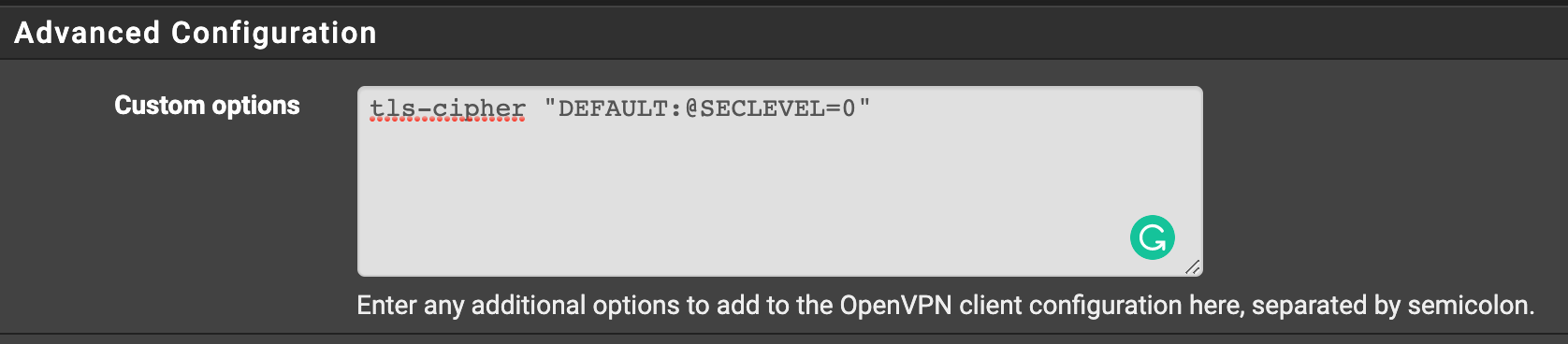
However, I am looking for a better way to do this.
-
Have a look here
https://www.infopackets.com/news/10414/how-fix-openvpn-sslctxusecertificateca-md-too-weak/Bingo
-
@bingo600 thanks for the link. This looks like a better solution but I am not sure how to make this work on pfSense.
I am using VPN vendor, so I did not create the original certificates as they were given to me by the vendor.
Am I misunderstanding something?
-
From the url above , it seems that your vendor needs to sign with SHA instead of MD5
Getting new updated certificates would be the correct solution.But with some vendors ... "Good luck w that"

/Bingo
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.