No traffic on UDP tunnel
-
I've got a weird issue.
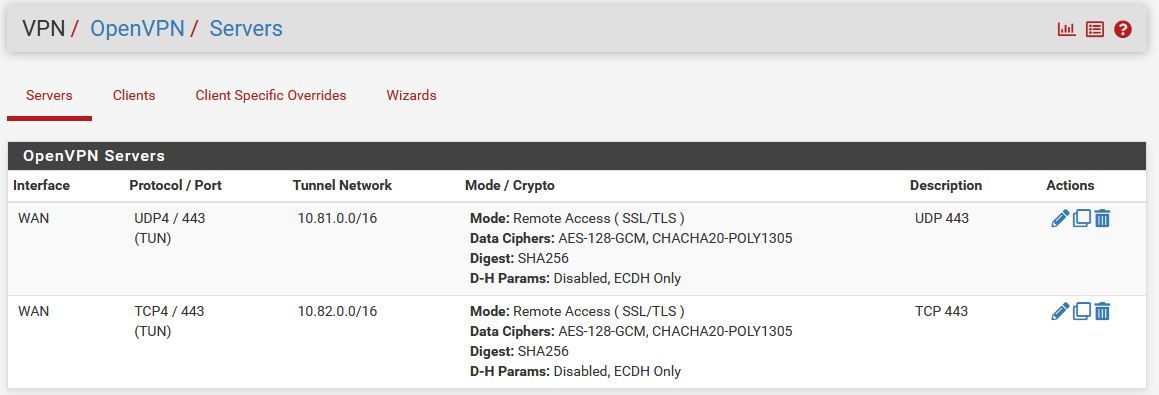
I've set up OpenVPN on pfSense. My goal is to use UDP port 443 and have TCP port 443 as a backup.
Environment
Cisco ASA sitting at network edge.
This device does all NATing and firewalling for the network. I have access to this device but I cannot remove it. (Government network)PfSense 2.5.2
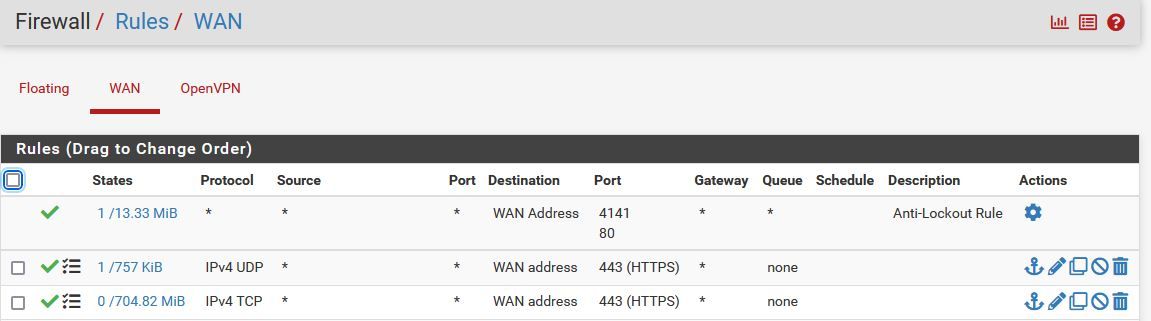
I've got the ports forwarded from the upstream Cisco ASA to the internal "WAN" IP of pfSense and OpenVPN is set up using PKI.
TCP 443 connects and works perfectly.
UDP 443 will connect just fine but will not allow traffic across the VPN.These two servers are set up identical to each other. The only difference is the protocol.
I've created rules in pfsense to allow the required traffic through. I've turned on firewall logging to see if the firewall was blocking the traffic. (It's not)
The Cisco ASA does not show any ACLs blocking UDP ports. I tried moving to UDP 1194 but I have gotten the same results.
TCP 443 connects and passes traffic just fine. UDP 443 or UDP 1194 will connect, give the client the correct IP from the pool, and add routes for local networks.
I've done a packet capture for both UDP ports with pfSense. I am getting UDP packets from both directions.
I know the Cisco ASA is not causing the issue because I can connect to the internal IP of pfSense and I get the same results.
Has anyone run into this issue?
-
I've found that if I redirect all traffic through the VPN, traffic works normally across the VPN.
I used the following in the server config.
push "redirect-gateway def1"So is this a client issue?
Route print on the client shows the local networks correctly in the clients routing table when I push "route x.x.x.x x.x.x.x"
But no traffic will traverse when when I push route. It only works when I push "redirect-gateway def1"