OpenVPN site-to-site setup
-
I am trying to setup site to site OpenVPN tunnel but facing some strange issues. I did several openvpn setups in the past successfully, but this is the first time that I am using pfSense for the purpose.
Here is simple sketch of setup. On the sketch I call one side client and other side server, although it is symmetrical.
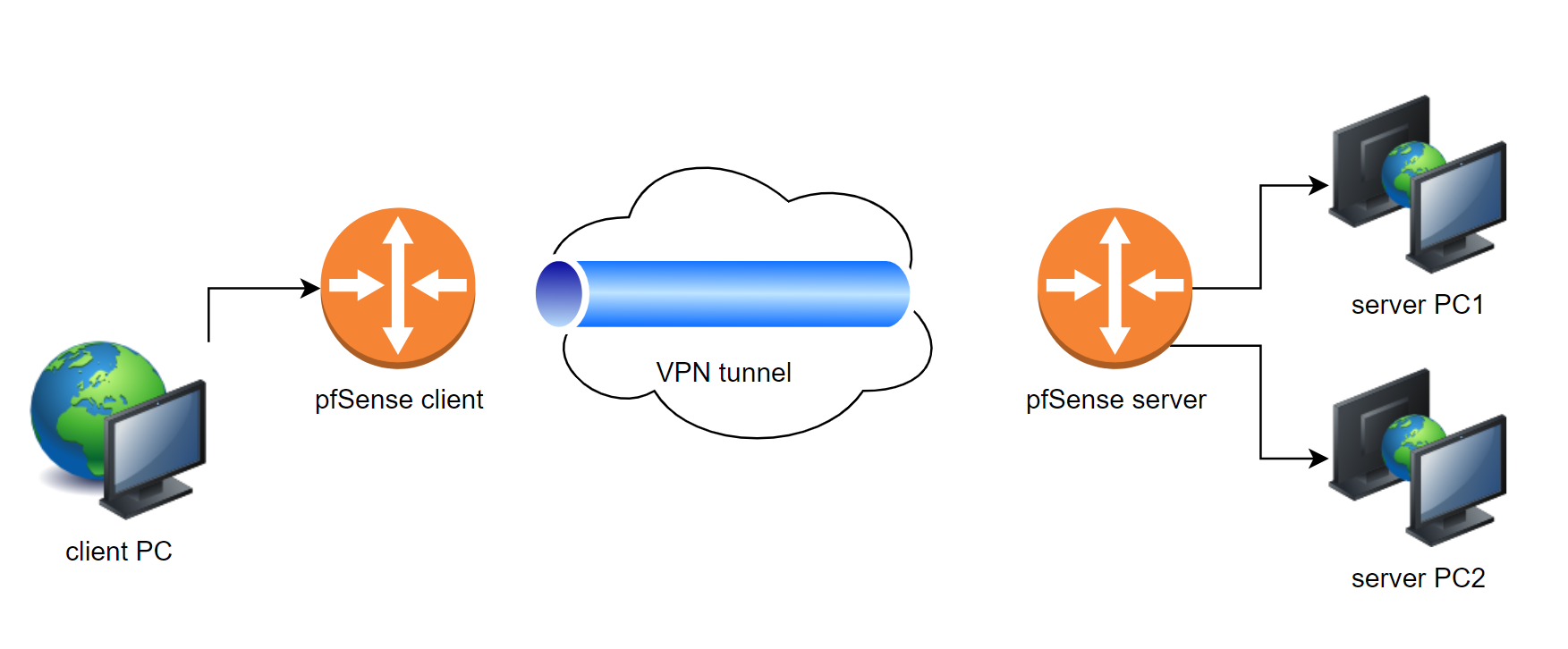
On both sides I have pfSense device, and tunnel show up as established. I can ping remote tunnel address from both sides. From pfSense client device on one side I can even ping on the remote network successfully.
What works:
- pfSense client can ping pfSense server tunnel ip
- pfSense client can ping pfSense server LAN ip
- pfsense client can ping server PC1, server PC2
- pfSense server can ping pfSense client tunnel ip
What does not work:
- pfSense server cannot ping pfSense client LAN ip
- pfSense server cannot ping client PC
- client PC cannot ping server PC1, server PC2
- server PC1, server PC2 cannot ping client PC
Additionally:
- When I try to ping server PC1 from client PC I see packets entering OpenVPN tunnel on the client side, but I don't see anything coming out on server side (using packets capture functionality of pfSense).
- When I try to ping server PC1 from pfSense client, I see packets entering OpenVPN tunnel on the client side and coming out on the server side, as well as responses to ping.
Any hint what I am missing in the setup? Why are the packets blocked and by what?
-
I have progress.
I added CSO, although at this moment I only have one client connecting to server.
After I added NAT rule on both sides so that the traffic is NAT-ed before entering tunnel - it works. This is strange since on at least one side the pfSense is the default gateway!
I will keep investigation to find real issue. At least now I believe this is a routing issue.
-
@mmarco
If you set up a site2site OpenVPN select "peer to peer" server mode and use a /30 tunnel subnet.
So there is no need for a CSO.