GRC closed instead of stealth ports?
-
PfSense 2.5.2.
So I've basically added 3 vlans (no fw rules yet), installed pfBlockerNG-devel, and added a NAT redirect for NTP on my LAN... I did a GRC scan when I first installed and all ports came back as stealth but at some point, that changed and now the ports are rejecting instead of blocking. I haven't touched the default firewall rules and pfblocker floating rules are in place. Any ideas what might have changed?



-
I doubt those are getting to pfsense, those are prob being rejected upstream of pfsense. Those are 135,139 and 445 ports - ie cifs/smb - almost never allowed over the public internet by isp..
example - here is comcast block list.. you will see 135,139 and 445 which your seeing as blocked
https://www.xfinity.com/support/articles/list-of-blocked-ports
Here is another isp blocking those, etc.
https://www.spectrum.net/support/internet/blocked-ports/Validate that traffic actually gets to pfsense wan via snif.. There is nothing in your rules where pfsense would send back a reject.
-
@johnpoz The above used to be the case with my ISP.
-
I just find it suspect that up to a few days ago, when I ran the test, they all came up stealth.... I wasn't running the check a lot so i'm pretty sure my ISP didn't change something behind the scenes... Is there any way to check on the implied block rules on PFSense?
One other setting I played with while I was figuring out the NAT redirect was the "Enable NAT Reflection for 1:1 NAT" and "Enable automatic outbound NAT for Reflection" under System / Advanced / Firewall & NAT. They were disabled, then saw an article that those needed to be enabled... then i've since turned them back off. "NAT Reflection mode for port forwards" is set to "Pure NAT". Not sure if those would have any bearing or not.
-
@nogbadthebad exactly - it could even be in the cable modem.. I recall looking into mine one time and 445 was blocked right in the modem config. It didn't send a rst or anything. But it was blocked - those ports are not really valid over the public internet.. They will be blocked almost everywhere.
But pfsense wouldn't send a reject. Now if they were actually forwarded through and could get to that something - it might send a reject..
Simple way to check for sure is to just sniff on pfsense while running that and look to see if those ports even get to pfsense..
Here I just ran grc test on my wan IP. While sniffing - only port not stealth is 443, which I do have open on purpose.
GRC Port Authority Report created on UTC: 2021-07-23 at 17:56:29 Results from scan of ports: 0-1055 1 Ports Open 0 Ports Closed 1055 Ports Stealth --------------------- 1056 Ports Tested NO PORTS were found to be CLOSED. The port found to be OPEN was: 443 Other than what is listed above, all ports are STEALTH. TruStealth: FAILED - NOT all tested ports were STEALTH, - NO unsolicited packets were received, - A PING REPLY (ICMP Echo) WAS RECEIVED.And you can see from the sniff - those 135 ports not even seen by pfsense.
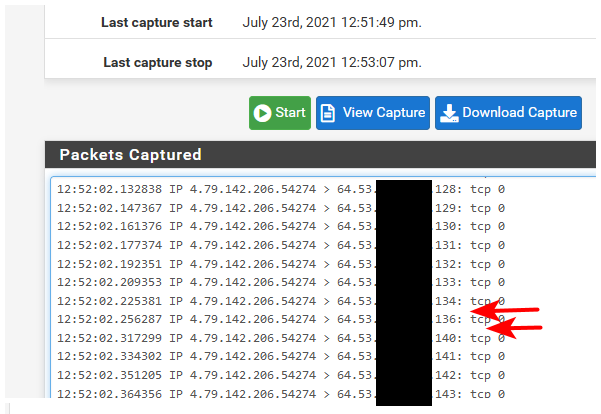
Do a sniff if believe pfsense is doing it..
-
So yea... officially confused... tested the usual 1056 ports and this is what it caught. I'm really hoping it's just the way I captured, because this doesn't make any sense... the ports are repeating and they're NOT what I told it to test for.

I'm a programmer by trade, but learning a WHOLE new level of respect for you network guys!
-
that looks like return traffic from you hitting website.. and not what was scanning.
the source port is 443, ie website you went too and whatever your source port was this 15623..
You will want to make sure you remove the 100 count limit when capturing or that will fill up quick after you start with you just talking to the website.
I can pretty much promise you there is no way pfsense is sending anything back that would show those ports "closed" vs the stealth.. If you had set pfsense to send rejects (which isn't something easy to do like a mistake in a button click or checkbox) - it should be sending them for all ports. Or you have those ports forwarded into something that could be sending a rst back and it showing closed.
-
That makes sense...probably those little boxes being sent back on the page. So if i'm capturing on the WAN interface... and all I see is the above, on an unlimited capture ("Count"=0), but no actual "real" port hits... it would be the ISP rejecting it?
-
Exactly - if you do not see that port that they are showing closed hitting your wan, but its showing closed on the scanner - then something between you and them did something that shows that port closed, like sent a rst is the only way, or it answered with a syn,ack - which should show it as open then, etc.
As you see in my scan - those ports 135 for example never get to pfsense.. Nothing in the path sends anything back on those, but they never get to me. Blocked somewhere between them and me. Like I said many isp block those ports on purpose..
Could be your isp changed how they block those ports, or device pfsense is connected to is sending them? Or something else between you and them..
Really the only way you could see something like that if the traffic was actually getting to pfsense is you have that port forwarded to something internally that is sending back a rst.
BTW - Reject on a wan facing interface is a horrible horrible idea.. Like I said you could do it on pfsense - but its not something you should ever do by mistake or accident. And not something you should ever really do ;)
-
@johnpoz said in GRC closed instead of stealth ports?:
But pfsense wouldn't send a reject. Now if they were actually forwarded through and could get to that something - it might send a reject.
Wouldn't pfsense send a reject, if that was selected? The choices are "block" which does not respond at all and "reject" which sends a reject.
From the manual:
A packet matching this rule will be discarded and for supported protocols, a message will be sent back to the originator indicating that the connection was refused.
I use block on the WAN interface so that an attacker would waste time waiting for a reponse and reject internally to end the attempt as quickly as possible.
However, in this case above, there is no reject on the WAN interface.
-
It wouldn't via the rules he has shown was my point. As I said it would have to be a specific reject..
You would have to specific do that - and even the floating rule he has as reject couldn't do it - its to all ports.. So if that was doing it - all the ports would be coming back closed. And its not set for wan anyway, and how would his own wan be in that pb alias? etc..
-
My old shitty cable-ISP used to do this, after maybe 60 days or so, I got this. I then had to manually reconnect and it was gone again and I had my open ports back.
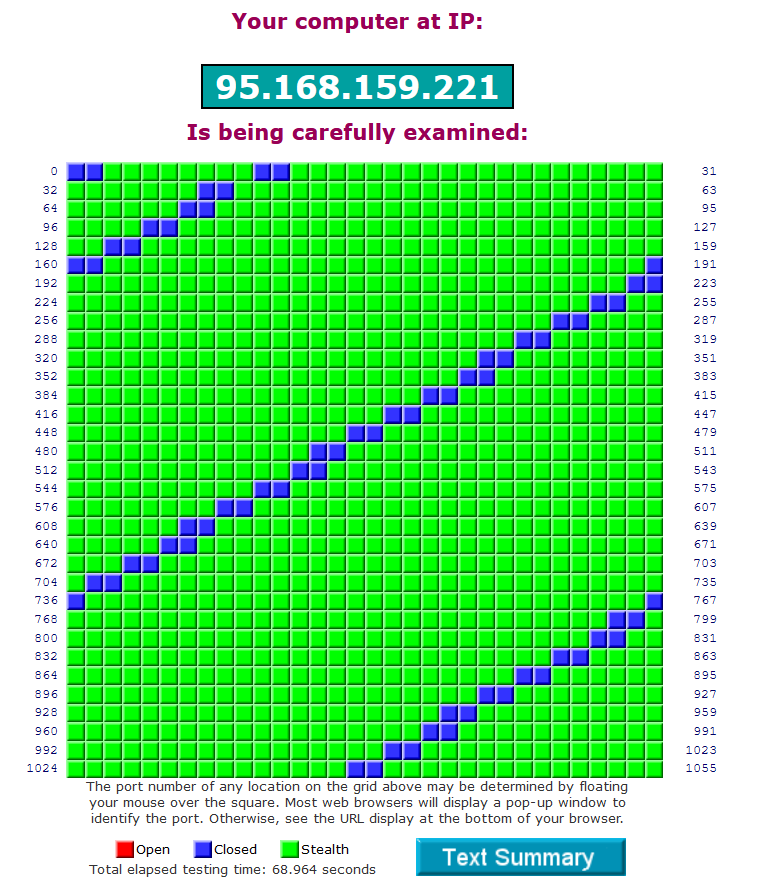
Somehow it is still fascinating to me to look at.

-
Ok, finally got this figured out. It was my gateway that was rejecting the requests. After a hard reset, it switched over to blocking, but the gateway was still the one doing the work, so had to put it in DMZ+ mode so I could get traffic on the PfSense box. I'm seeing the individual port requests now via the packet capture and they're ALL showing as stealth. Woot!
Thanks all for your help!
-
@bob-dig ha that is odd graph to be sure.. WTF?? BTW, I take it that is some old IP, so no concern with posting that public IP?
@mjgtp glad you got it sorted.
-
@johnpoz I never had a static IP with any ISP around here. And I even do things that those dynamic IPs change more often.

-
I don't have static, and my IP hasn't changed in 2 some years.. Why would it ever change? It just keeps renewing the same lease, because my device is on 24/7/365.. I am glad it doesn't change to be honest..
Some people have an aversion to posting their public IP is all.. If your ok with it..
-
@johnpoz said in GRC closed instead of stealth ports?:
If your ok with it..
I am ok with it, I have another one every morning.

Also I am not with that ISP anymore, thanks god. -
@johnpoz said in GRC closed instead of stealth ports?:
Why would it ever change?
I think some ISPs do it to be nasty.

Mine is virtually static.
I don't worry if my address becomes known. I just don't go out of my way to advertise it.
-
@jknott said in GRC closed instead of stealth ports?:
I don't worry if my address becomes known. I just don't go out of my way to advertise it.
Exactly..