Setting up OpenVPN when Pfsense is Behind another Firewall
-
In a new location the building provides internet to the tenants. They have Unifi equipment setup with a Unifi firewall of some kind and Unifi switches in each Suite. I need to get OpenVPN up and running but not sure how in this situation. The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10. What would I need to do to get OpenVPN to connect in this situation? Any help would be greatly appreciated!
-
Are you planning on using OpenVPN to connect to your network? Or to another network? If to yours, you're out of luck, unless the landlord will port forward to you.
-
I suppose you mean that the pfSense will be setup as OpenVPN server, as clients usually will run wo. any Nat Trickery.
If you by "Public IP w. Full Nat" to 10.x.x.10 , mean that everything hitting the Public IP , will be forwarded to 10.x.x.10 , then you are good to go.
Just remember if you are using the OpenVPN Client export ,
to set Host Name Resolution to : Other , and enter the public ip in the field below. Else it will use 10.x.x.10 (pfSense WAN IP) as the OpenVPN connect ip , and that would never work if accessing via internet.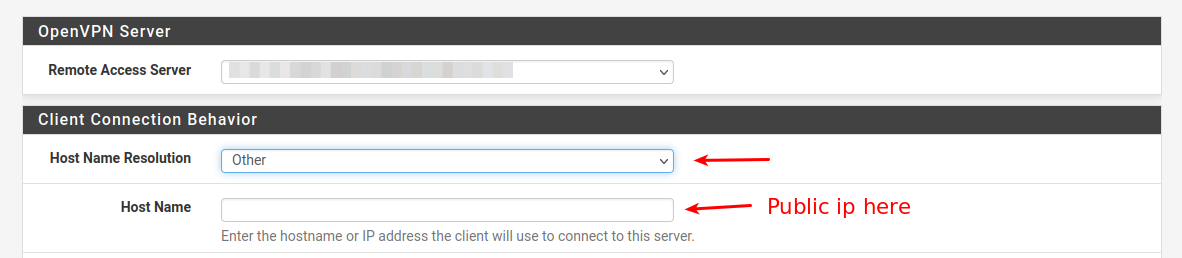
/Bingo
-
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
If you by "Public IP w. Full Nat" to 10.x.x.10 , mean that everything hitting the Public IP , will be forwarded to 10.x.x.10 , then you are good to go.
He refers to "each suite". That means he's not the only one. The question still remains whether the port will be forwarded to him. What if another unit wants to run OpenVPN too? Now, you're talking multiple port numbers, only one standard.
-
I focused more on this info:
The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10.
And expected that meant he got his own public bidir nat ip , for the pfSense.
What if another unit wants to run OpenVPN too? Now, you're talking multiple port numbers, only one standard.
I'm running 3 pfSense OpenVPN servers , and NONE are using the "default 1194" , client export easily handles the selected "server" port.
What seems to be the issue here ??/Bingo
-
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
Are you planning on using OpenVPN to connect to your network? Or to another network? If to yours, you're out of luck, unless the landlord will port forward to you.
Yeah, we were using OpenVPN inside Pfsense to connect remote clients to the network. The IT of the building said they set up a public IP that forwards to the private IP of the firewall. I tried dynamic dns with it but it didn't work and the public IP that shows for my network is different then the one he gave me that forwards to the Pfsense.
-
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10.
That says nothing about port forwarding. The default port for OpenVPN is UDP 1194. Suppose they forward that port to you. What happens if someone else also wants to use OpenVPN? If they give you NAT, then you likely don't have a unique public address, to separate units that way. If you did have one, there would be no need for them to do NAT.
This is a perfect example of why the world should move to IPv6 as soon as possible. Because of the IPv4 address shortage, hacks such as NAT are needed to get around that shortage. However, NAT also breaks things, such as providing access to your VPN. It requires other hacks, such as TUN servers, for VoIP and some games to work and more.
In your situation, a single address is shared by all units. On IPv6, they could easily give at least an entire /64 prefix to each unit. A single /64 contains 18.4 billion, billion addresses. I get a /56 prefix from my ISP, which provides 256 /64s. Some ISPs provide a /48, which has 65536 /64s
-
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
I'm running 3 pfSense OpenVPN servers , and NONE are using the "default 1194" , client export easily handles the selected "server" port
Again, are they providing port forwarding? If you have 3 servers, you need 3 different ports forwarded.
-
@duvan34 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
I tried dynamic dns with it but it didn't work and the public IP that shows for my network is different then the one he gave me that forwards to the Pfsense.
Depending on the ISP, that could be a moving target. A friend of mine runs into this with a Jitsi server. He's on Bell Canada and it takes very little to trigger an address change. With my ISP (Rogers) the IPv4 is virually static and the host name is based on modem and firewall MAC addresses, so no need for dynamic DNS. On IPv6, my prefix is also virtually static, in that I have to change hardware to force a different one.
-
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10.
That says nothing about port forwarding. The default port for OpenVPN is UDP 1194. Suppose they forward that port to you. What happens if someone else also wants to use OpenVPN?
What do you interpret "Full Nat" as ?
I did interpret it as a 1:1 nat to 10.x.x.10.Why do you have to run OVPN on 1194 ?
It's not like the client is difficult to point at an alternate port.All my servers are fully functional on "alternate" ports.
/Bingo
-
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
I'm running 3 pfSense OpenVPN servers , and NONE are using the "default 1194" , client export easily handles the selected "server" port
Again, are they providing port forwarding? If you have 3 servers, you need 3 different ports forwarded.
If i get a "Full Nat" 1:1 , everything is forwarding to the pfSense.
No need to do specifics ....I have such a setup at home.
And have made many of those setups in the Corp. Enterprise world.
/Bingo
-
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
What do you interpret "Full Nat" as ?
Network Address Translation. Consider the people stuck behind carrier grade NAT. They have NAT for usual traffic, but they won't be able to set up a server, VPN, etc. To do that, they have to assign a specific port to a specific computer behind the NAT. As I said, 1194 is the default port. I didn't say it was the only one that could be used. Regardless, whoever is providing this will have to map the target port to the target computer. Will they do that?
-
Thank you for all the responses, I really appreciate it! Each suite has it's own Unifi Switch in it and I am guessing they have the suites vlan'd up in the firewall, but the support I talk to for the place doesn't really seem to know. I have a guy that is supposed to help out Monday from that company but figured I would ask on here to get an idea of what I may need to do in case he doesn't know.
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10.
That says nothing about port forwarding. The default port for OpenVPN is UDP 1194. Suppose they forward that port to you. What happens if someone else also wants to use OpenVPN? If they give you NAT, then you likely don't have a unique public address, to separate units that way. If you did have one, there would be no need for them to do NAT.
This is a perfect example of why the world should move to IPv6 as soon as possible. Because of the IPv4 address shortage, hacks such as NAT are needed to get around that shortage. However, NAT also breaks things, such as providing access to your VPN. It requires other hacks, such as TUN servers, for VoIP and some games to work and more.
In your situation, a single address is shared by all units. On IPv6, they could easily give at least an entire /64 prefix to each unit. A single /64 contains 18.4 billion, billion addresses. I get a /56 prefix from my ISP, which provides 256 /64s. Some ISPs provide a /48, which has 65536 /64s
Yeah, I am not sure if they forwarded 1194 specifically but they said that all traffic hitting that public IP was forwarded to the 10.x.x.10 which I assume would include 1194, but will ask him that on Monday. I agree, IPV6 needs to take over sooner rather than later, but who knows when that will happen.
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
I'm running 3 pfSense OpenVPN servers , and NONE are using the "default 1194" , client export easily handles the selected "server" port
Again, are they providing port forwarding? If you have 3 servers, you need 3 different ports forwarded.
If i get a "Full Nat" 1:1 , everything is forwarding to the pfSense.
No need to do specifics ....I have such a setup at home.
And have made many of those setups in the Corp. Enterprise world.
/Bingo
I was also looking at setting up the 1:1 NAT in the Pfsense but wasn't really sure how that would work. Would I do External subnet as the Public IP they assigned to me and then internal IP as the static 10.x.x.10 of the firewall and Destination would be LAN? In my head that makes sense but not sure lol.
@jknott said in Setting up OpenVPN when Pfsense is Behind another Firewall:
@bingo600 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
The building internet provider said they setup a public IP address with "Full Nat" to the Private IP of the Pfsense which is 10.x.x.10.
That says nothing about port forwarding. The default port for OpenVPN is UDP 1194. Suppose they forward that port to you. What happens if someone else also wants to use OpenVPN? If they give you NAT, then you likely don't have a unique public address, to separate units that way. If you did have one, there would be no need for them to do NAT.
This is a perfect example of why the world should move to IPv6 as soon as possible. Because of the IPv4 address shortage, hacks such as NAT are needed to get around that shortage. However, NAT also breaks things, such as providing access to your VPN. It requires other hacks, such as TUN servers, for VoIP and some games to work and more.
In your situation, a single address is shared by all units. On IPv6, they could easily give at least an entire /64 prefix to each unit. A single /64 contains 18.4 billion, billion addresses. I get a /56 prefix from my ISP, which provides 256 /64s. Some ISPs provide a /48, which has 65536 /64s
Just one firewall running OpenVPN currently, I will have to find out what ports they forwarded if any. It annoying because it is easy to setup with Gateway IP and usable IP but all this stuff they have setup in the complex has really thrown me off.
-
@duvan34 said in Setting up OpenVPN when Pfsense is Behind another Firewall:
Yeah, I am not sure if they forwarded 1194 specifically but they said that all traffic hitting that public IP was forwarded to the 10.x.x.10 which I assume would include 1194, but will ask him that on Monday.
What that means is when you connect to the Internet, with a browser, etc., your return traffic will automagically forwarded to you. This on it's own will not support a VPN or other server. They have to specifically forward whatever port is used to your network. Normally, that would be UDP port 1194, but it could be any other port that isn't used by something else. Again, this has to be done by whoever manages the NAT.
-
They forwarded 1194 from the static IP to the private ip and I used ddns and everything is working now. Thanks for the tips!