Gateway Change on Alias Not Applying
-
I have an alias called "VPN_Hosts" which contains IP's of hosts that will be using the OpenVPN gateway instead of the WAN. VPN interface is up, I've created the rule to change the gateway of the aliased hosts, and added the outbound NAT however the rule never gets hit and the traffic continues to use the WAN interface.
Alias:

LAN Rule:
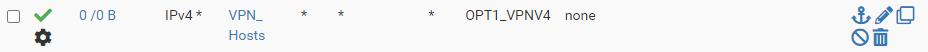
Outbound NAT:
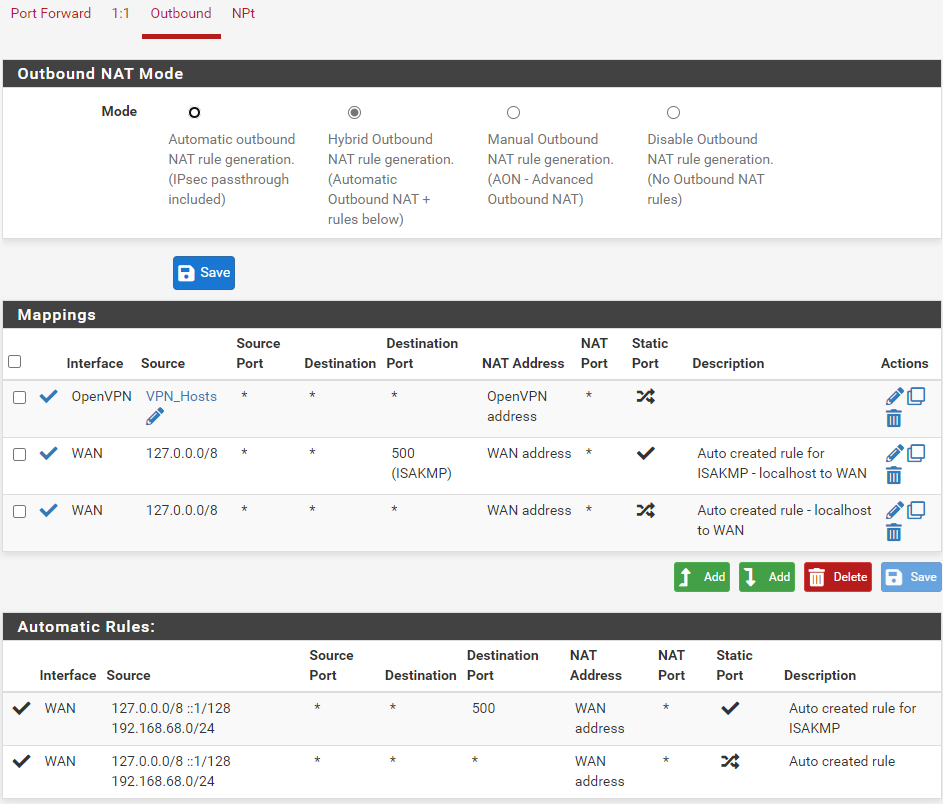
Could someone point out the obvious that I'm surely missing. Thanks.
-
@wgallt said in Gateway Change on Alias Not Applying:
I've created the rule to change the gateway of the aliased hosts
Is this rule on the top of the LAN rule set?
Maybe there is a floating rule or one on an interface group which your LAN is belonging to matching the traffic before.
-
@viragomann
I don't have any floating rules and yes it's towards the top below the anti-lockout rule. This is a fairly new installation. This is the first rule I'm adding and it won't match.
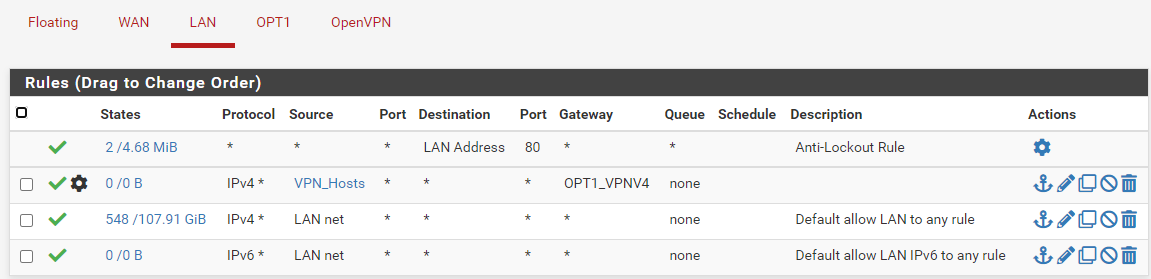
-
@wgallt
Also consider that already existing connections are not affected by the newly added rule. You might have to delete the states. -
@viragomann
Thanks for the suggestion. I did clear the states a couple times before posting. Just to rule out an issue with the alias I set the source of the rule to the IP of the host, cleared the states again and still no hit on the rule. -
@wgallt
And the VPN gateway is really shown a "up"? If it isn't (maybe cause the server doesn't respond to pings) the policy routing rule is omitted.Also I just saw that your outbound NAT rule isn't using the correct interface. You should change it to the VPN interface you have assigned to the client instance.
-
@viragomann
The VPN interface is up:
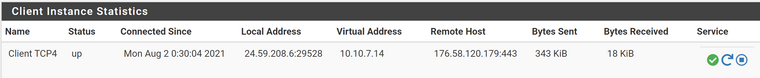
I thought it should point at the OpenVPN instance but I have updated the interface to the parent OPT1:
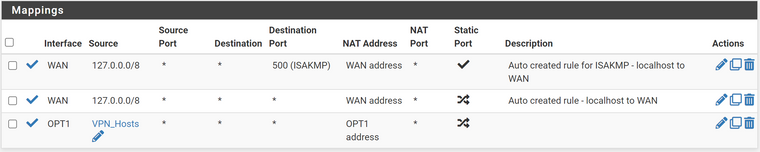
I cleared states and rule not hit and traffic is exiting the WAN interface.
-
@wgallt said in Gateway Change on Alias Not Applying:
The VPN interface is up:
No, the point is what Status > Gateway is showing for the OpenVPN gateway.
-
@viragomann
Ok. The Status -> Gateway shows Offline
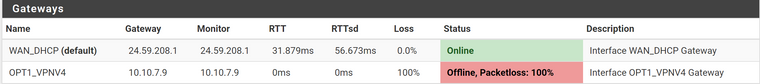
The OpenVPN log shows Initialization Sequence Completed and I'm assigned and IP so not sure why that would be. So this is why the rule isn't hit being that I have the "Skip rules when gateway is down" option enabled.
-
@wgallt said in Gateway Change on Alias Not Applying:
Ok. The Status -> Gateway shows Offline
So that's the problem.
Gateway offline doesn't necessarily mean that your VPN is not working, it tells you that to gateway does not respond to pings.
So you can either deactivate the gateway monitoring for the VPN gateway in System > Routing > Gateways, or if monitoring is desired, enter an alternative monitoring IP (a public IP which is responding to pings).
Also you can check System > Advanced > Miscellaneous > Skip rules when gateway is down if you don't want the rule to be omitted when the gateway is down.
-
@viragomann
Success! I set the monitoring IP to 8.8.8.8 and the rule is getting hits now and the host is definitely using the VPN for egress. Thank you!