OpenVPN Bridge Problem
-
Apologies for the long read…
A few weeks ago, I bought two Netgate 2100 BASE pfSense+ to be VPN gateway for 2 remote offices, and one Netgate 3100 BASE pfSense+ as the VPN “server” in our main office.
I’ve looked thru just about every post, page, reddit I could find on OpenVPN TAP in the forum trying to figure out this myself and I admit defeat and need help. I think I have 99% of this setup but I must be missing one small detail that is causing problems.
Based on the other threads, I anticipate your first question will be why do I need TAP? It’s clear from nearly every post I have read, TUN is preferable, but because we have hardware media boxes which use both multicast AND layer 2 communication packets to communicate with each other, we have no choice.
The setup looks like this:
REMOTE A/B OFFICE | Netgate 2100 | <--> | ISP Router | <- internet -> | ISP Router | <--> | Netgate 3100 |Both site A and B are Netgate 2100 behind an ISP router. The Netgate 3100 (Office) is also behind an ISP router, which has UDP port 1149 forwarding to it. The ISP router at Office is the DHCP server.
A/B Site (Netgate 2100)
Basic Setup:
- WAN is connected to the ISP router
- LAN 4 is setup as a service port to access the Netgate 2100. It’s set to VLAN 4084, Static IP 192.168.120.1, DHCP is setup on LAN 4 to give out 192.168.120.x IP to anything connected.
- The remaining LAN ports (1-3) are setup with no IP address, DHCP is disabled.
- BRIDGE0 IP is set to DHCP. It’s setup as bridge between OpenVPN TAP and LAN (1-3).
- Firewall rules allow all/any on the TAP/BRIDGE0/OpenVPN/LAN(1-3)/LAN4.
- Outbound NAT is set to Hybrid, there’s a rule on BRIDGE0 any/any/any (not sure if needed for bridging?)
OpenVPN Setup (Client):
- Certificates are setup.
- Peer to Peer (SSL/TLS)
- UDP / TAP
- Interface = WAN
- Server IP + Port 1194
- Use TLS Key (same as on server)
Office (Netgate 3100)
Basic Setup:
- Only 1 physical connection - OPT1 which is connected to the ISP router (the DHCP server). No IP or gateway set.
- BRIDGE0 IP address is set to static IP 192.168.2.10 (outside of the DHCP range), Gateway is set to 192.168.2.1 (ISP Router), and is bridged to OpenVPN TAP interface and OPT1.
- Firewall rules allow all any on the TAP/BRIDGE0/OPT1/OpenVPN.
- Outbound NAT is set to Hybrid, there’s a rule on BRIDGE0 any/any (again, not sure if needed?)
OpenVPN Setup (Server):
- Certificates are setup.
- Remote Access (SSL/TLS)
- UDP / TAP
- Interface: BRIDGE0
- Server IP + Port 1194
- Use TLS Key (same key on clients)
- Bridge DHCP - ON
- Bridge Interface: BRIDGE0
- Bridge Routing Gateway: OFF (I have tried ON also and didn’t seem to help)
- Server Bridge DHCP Start/Finish: 192.168.2.205 and 192.168.2.220 (outside of the ISP router DHCP range. I have also tried clearing these values)
- Redirect IPv4 Gateway: ON (Also tried OFF)
- IPv4 Local Network 192.168.2.0/24 (this field disappears if you set Redirect IPV4 Gateway ON)
- Allow communications between clients connected to this server – ON
- Dynamic IP – ON
- Provide a DNS server list to clients – ON and set to 8.8.8.8 and 8.8.8.4
- Block Outside DNS – ON
- Force DNS cache update – ON
The results:
On Remote A/B Netgate 2100:
- TAP adapter receives IP 192.168.2.205 (from Office OpenVPN?)
- BRIDGE0 gets an IP 192.168.2.190 (from Office ISP router)
- Connecting a laptop into LAN(1-3), it receives IP 192.168.2.141 and gateway 192.168.2.1 (assuming comes from the Office ISP router).
- I can ping the gateway 192.168.2.1, the remote openvpn server 192.168.2.10, all other devices on that LAN.
- I can ping the locally attached laptop 192.168.2.141.
- I can ping outside to the internet. Traceroute shows traffic going thru 192.168.2.10, then 192.168.2.10
On Office Netgate 3100 and all other devices on the LAN with it:
- Can ping Remote Netgate 2100’s TAP adapter 192.168.2.205 and bridge adapter 192.168.2.190.
- Can ping the internet, the gateway, all other devices on the LAN.
- I can even ping the remote IP of the laptop connected to Netgate 2100 - 192.168.2.141
And the problem…
On the laptop I can ONLY ping the Netgate 2100 BRIDGE0 (192.168.2.190) and any other local clients attached to the same Netgate 2100. I can’t ping any other IP address. FYI - the firewall is disabled on the laptop.
The frustrating part is, when I Wireshark ethernet on the laptop, I see all my LAN multicast AND layer 2 packets coming from my media boxes via VPN from the Office LAN, so I know the basic setup is somewhat working. But I can't send anything outbound.
Since the Server Bridge DHCP Start/Finish is set to: 192.168.2.05 - 192.168.2.220, I expected that anything connecting to OpenVPN Server would be assigned addresses by OpenVPN, so I am a little confused why anything connected to LAN(1-3) on Remote is getting an IP directly from the Office ISP router… and why would the bridge get the OpenVPN address range .205?
Can anyone please guide me to get the outbound working correctly on the laptop (and all other devices that may be connected to Netgate 2100)?
Thank you in advance.
-
I hate to be the one replying to my own topic, but I discovered the problem was the firewall on Client Netgate Box:
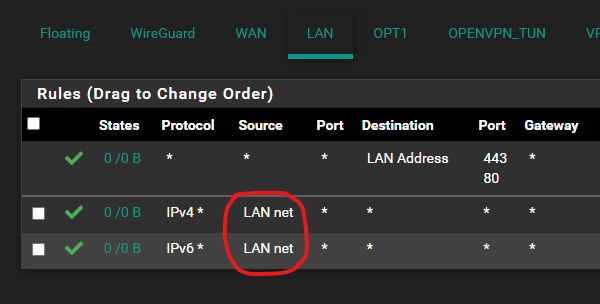
The default firewall rule for the LAN assigned ports out-of-the-box is accept Source: LAN net.
When bridging with layer 2, the client will receive an IP from the remote DHCP. The IP assigned to the client will be not known to this interface. I needed to change this to Source: any and now its working.