DNS Not Working With Phone As Peer
-
I can't seem to get my Android phone configured correctly. I can verify that my setup successfully establishes a handshake with the router's tunnel but it will not resolve any address, whether in a local subnet or out in the internet. I am using unbound as a resolver for dns queries. Here is a picture of the Wireguard Status that clearly shows that the tunnel is up and the Peer is connected:
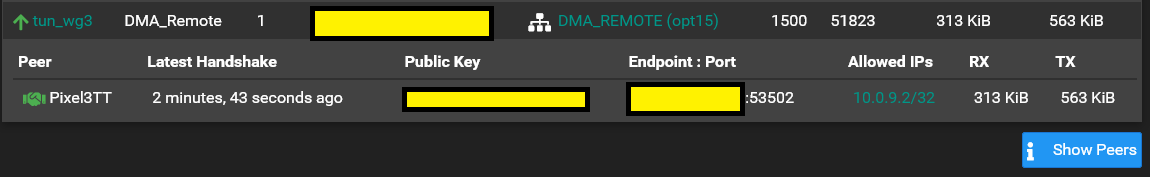
The phone is pointing to 192.168.163.1 for DNS which is the pfsense router. The 192.168.163.1/24 is the LAN network.
Here are the rules on the DMA_Remote interface:
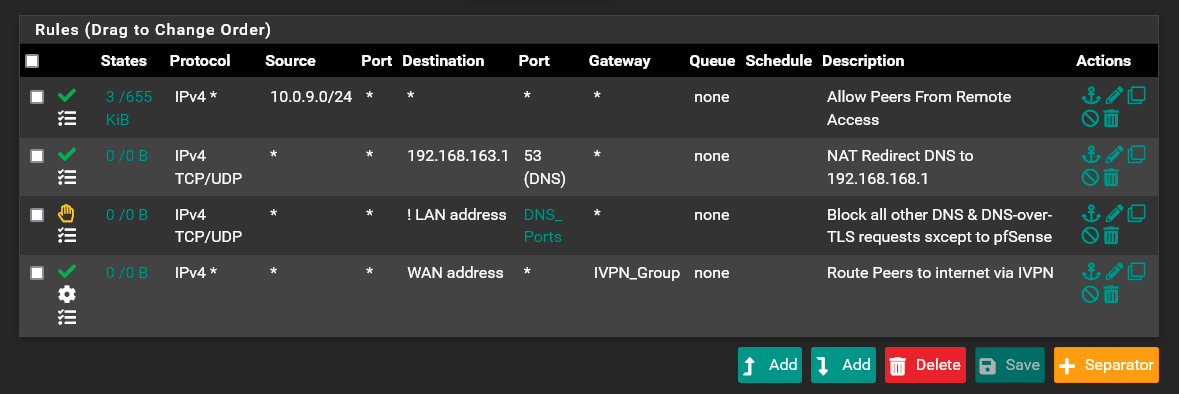
I can see from the firewall logs that the phone is making the DNS requests to 192.168.163.1 :
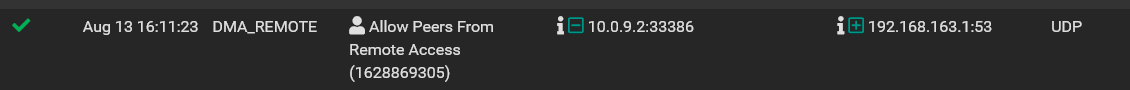
but when I do a packet capture it shows that the router is refusing the request:

I've been trying to figure this out for a few days and have run out of ideas and am stumped. Hopefully someone has some insight to share with me. It'll be greatly appreciated!
-
@dma_pf are you NATing the dns queries? Is unbound listening on the wireguard interface?
I have unbound working by having it also sat on my wg interface for mobiles accessing in and dont need any routing between subnets etc
-
@genericstudent Thanks for chiming in here to help me. I do have have an outbound NAT rule to the LAN. It looks like this:
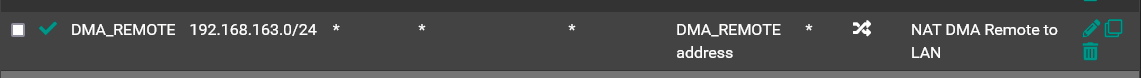
And I do have "ALL" selected in Resolver's settings:
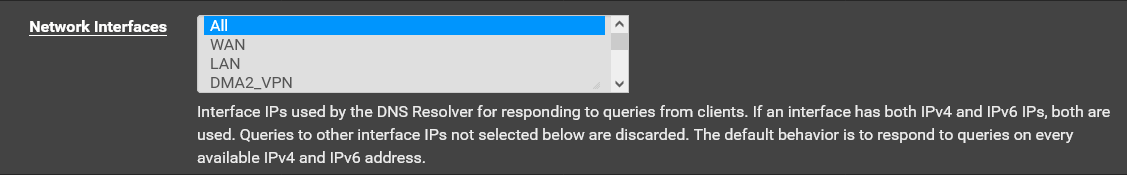
I am sure the issue is a DNS issue as I have no trouble pinging addresses out out on the internet if I use an IP Address through the Wireguard tunnel. And I can navigate to those sites in a browser as well if I use the IP address.
But everything fails when I use a FQDN to ping or surf through a browser. I have Termux installed on the phone and when I try, $dig AnyFQDN, I always get the result that says "Warning: Recursion requested but not available" and it indicates that the DNS Server is 8.8.8.8#53.
I can confirm that my android phone the Settings/Network & Internet/Advanced/Private DNS is set to "Off". I can also confirm that in the Wireguard app all applications are routed through the Wireguard tunnel and none are Excluded.
-
Unbound is rather picky , and won't answer requests from "Unknown ip addresses" ... Aka. Typically IP's not belonging to a "known interface range".
So when creating a "dial-in/vpn pool" it is not known , and have to be specifically allowed in the Unbound ACL section.
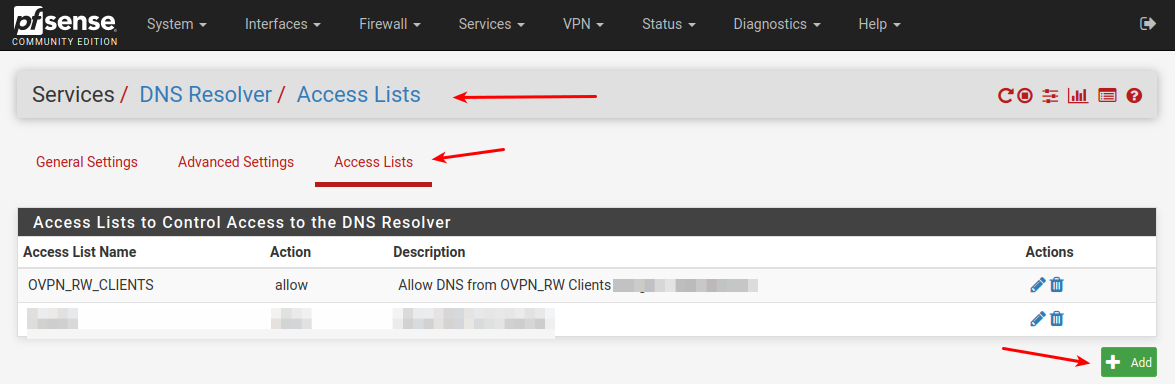
Here i'm allowing my OpenVPN ranges , in the first ACL.
/Bingo
-
Thanks to both of you for all of your help. I spent several hours this morning working on this issue and finally got it resolved. It was a combination of 3 different issues that resolved it.
Before I get to the solution I want to clarify that the setup I have is using a dedicated assigned interface with a gateway assigned to it for the remote access tunnel. Like this:
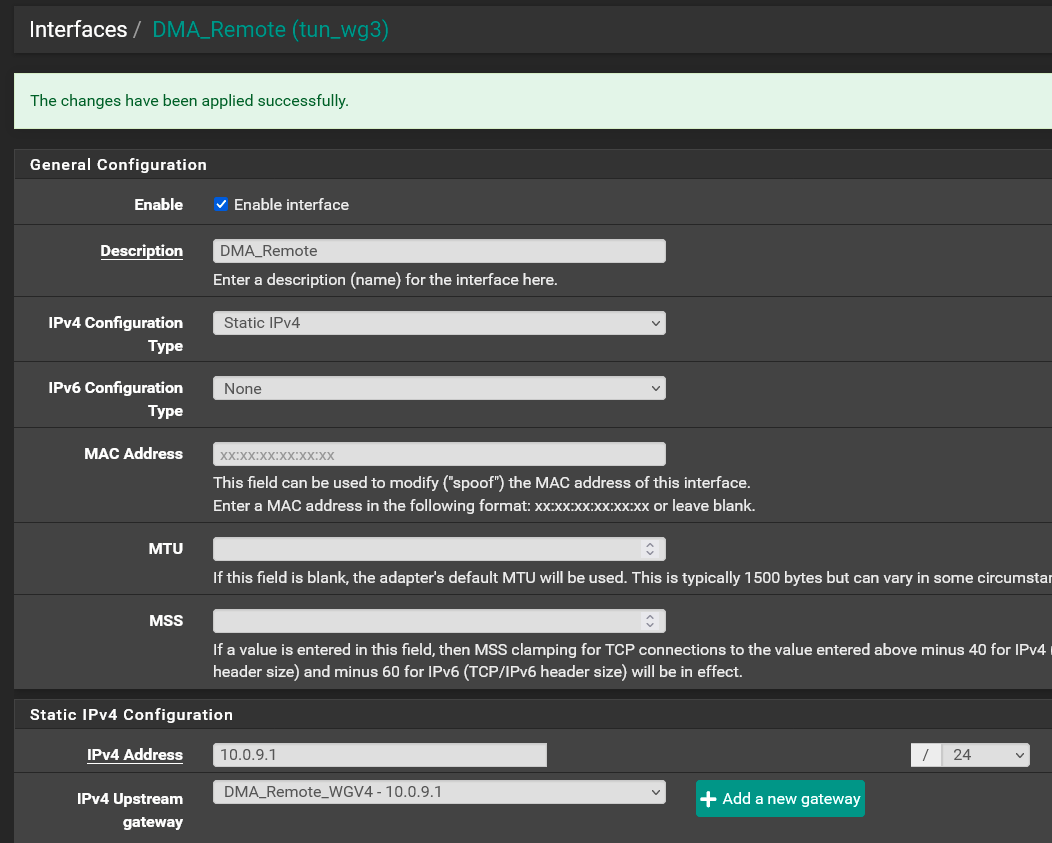
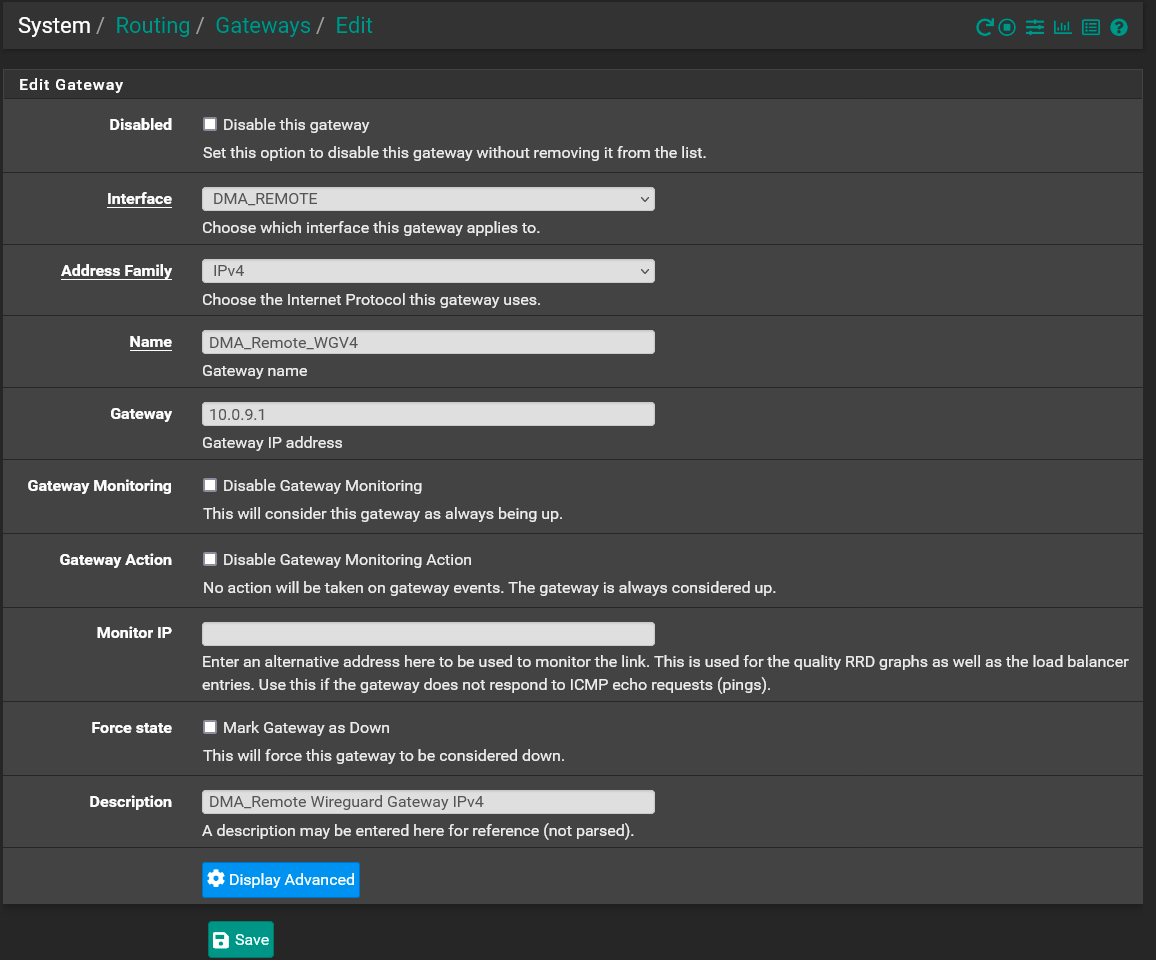
I found that first issue I had was the NAT Rule I posted above was not needed:
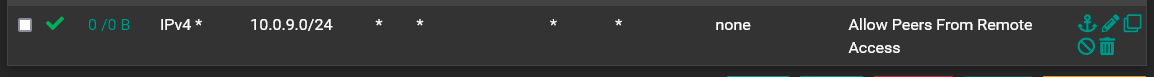
The second issue I had was the NAT Rule I posted above was also not needed:
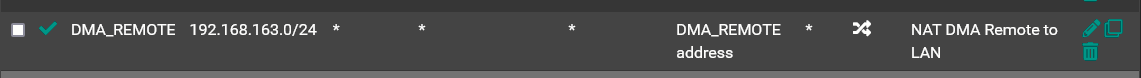
The reason it is not needed is because the 10.0.9.0 network is already know to pfsense through the assignment of that network to the wireguard interface and gateway. If there was no local pfsense interface assigned to that wireguard tunnel then the NAT rule would have been required.The third issue was exactly what @bingo600 pointed out. I did need to create a rule to allow the 10.0.9.0 network to assess the DNS resolver like this:
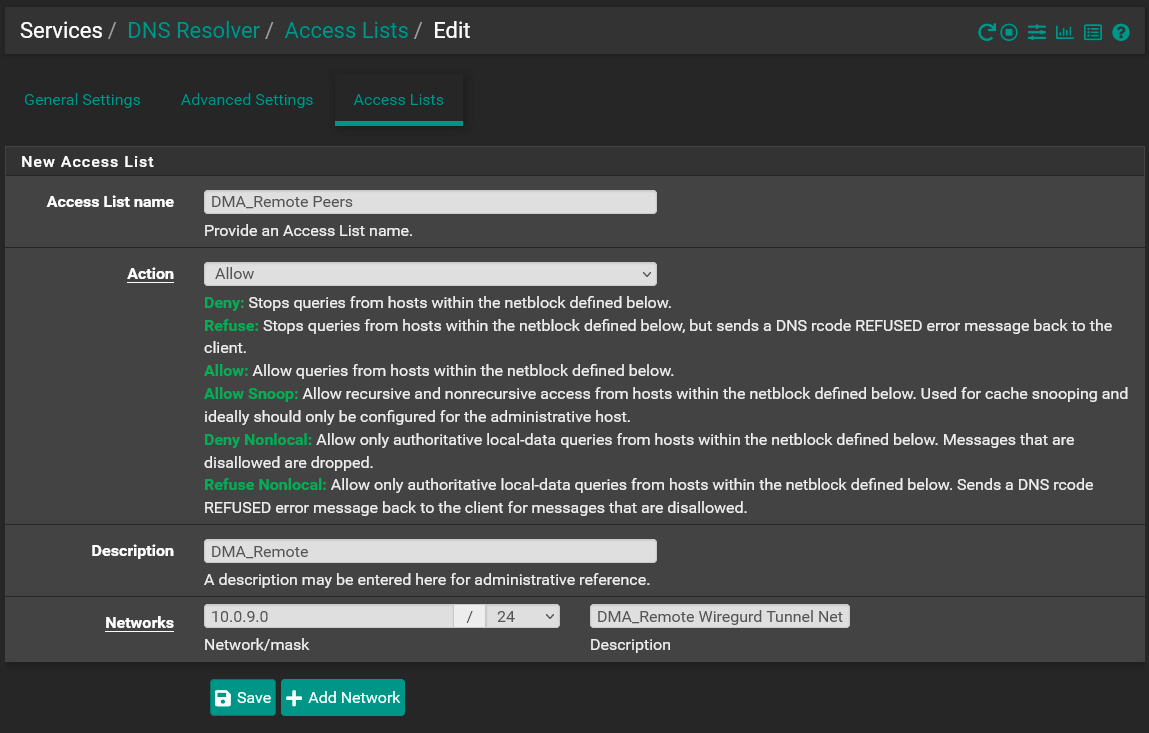
I am very perplexed as to why that allow rule had to be created. The setting I posted above,
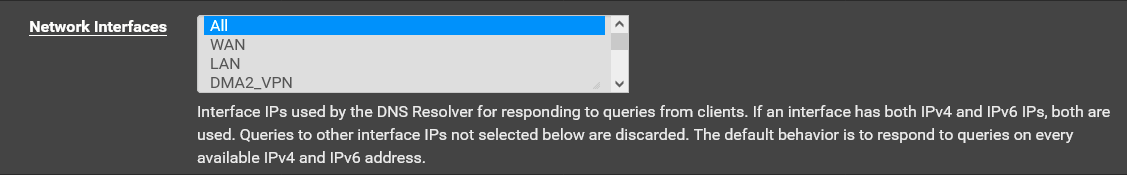
should have allowed the DNS queries as the 10.0.9.0 network is a local pfsense network. The pfsense cleary indicates that by selecting "All" there should not need an allow rule. Per the pfsense documentation: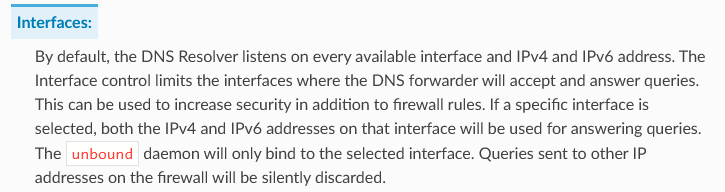
I'm obviously misunderstanding something about why that access rule is required. If you can help me understand that better I'd greatly appreciate it.
Thank you guys for all of your help. I've been trying to figure this issue out for several weeks and your input got me pointed in the right direction to get it resolved.

-
My guess would be that it might only be "physical" IF's that Unbound automatically sees (includes). Not Tunnel or other Non-Physical's.
And no worries ... I learned unbound ACL's "The hard way too" (Thanx @johnpoz )

A typical giveaway for "Unbound is upset" , is that the query is actively rejected , not just ignored/missed.
/Bingo
-
@bingo600 said in DNS Not Working With Phone As Peer:
Not Tunnel or other Non-Physical's.
Exactly.. That might be helpful if it did do tunnel networks, many users seem to run into this issue.
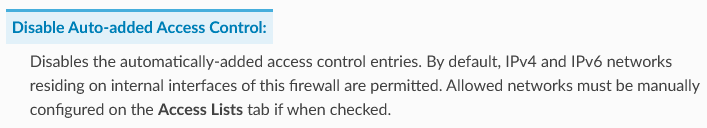
I am not really a fan of auto such rules, which doesn't allow me to see exactly what has access to what.. So I always have auto rules disabled when ever I can.. I just create my own acls - so I know exactly the details of what has access and to what exactly, etc.
-
Thanks for enlightening me on the tunnel/Non-physical. Seems to me that there are two issues which could be better addresses by the programmers of pfsense if in fact tunnels are not allowed by default in the acl..
The first, is they could clarify the distinction in the documentation and more clearly state that a tunnel is not automatically put on the acl as allowed.
And secondly they should not have those tunnels show up in the "Interfaces" check box in the resolver settings.
That would have saved me a whole lot of hours chasing my tail.
I'm still a little bit confused. Previously I was routing my remotes through OpenVpn. In that case I did not need to create an acl rule for them. The OpenVPN tunnels did work through the check box in the resolver settings. Is it possible that there just might be a bug in the programming to recognize the wireguard tunnel as opposed to being able to distinguish the OpenVPN tunnel?
-
@dma_pf said in DNS Not Working With Phone As Peer:
And secondly they should not have those tunnels show up in the "Interfaces" check box in the resolver settings.
It's a bit of time since i fiddled w. interfaces in unbound , but the IF selection box , could also tell unbound what interfaces to listen for DNS queries on.
If that is the case you would like to be able to select the WG tunnel IF there, AKA. All IF's should be selectable there.
/Bingo
-
D dma_pf referenced this topic on
-
D dma_pf referenced this topic on
-
@dma_pf said in DNS Not Working With Phone As Peer:
Thanks to both of you for all of your help. I spent several hours this morning working on this issue and finally got it resolved. It was a combination of 3 different issues that resolved it.
Before I get to the solution I want to clarify that the setup I have is using a dedicated assigned interface with a gateway assigned to it for the remote access tunnel. Like this:


I found that first issue I had was the NAT Rule I posted above was not needed:

The second issue I had was the NAT Rule I posted above was also not needed:

The reason it is not needed is because the 10.0.9.0 network is already know to pfsense through the assignment of that network to the wireguard interface and gateway. If there was no local pfsense interface assigned to that wireguard tunnel then the NAT rule would have been required.The third issue was exactly what @bingo600 pointed out. I did need to create a rule to allow the 10.0.9.0 network to assess the DNS resolver like this:

I am very perplexed as to why that allow rule had to be created. The setting I posted above,

should have allowed the DNS queries as the 10.0.9.0 network is a local pfsense network. The pfsense cleary indicates that by selecting "All" there should not need an allow rule. Per the pfsense documentation:

I'm obviously misunderstanding something about why that access rule is required. If you can help me understand that better I'd greatly appreciate it.
Thank you guys for all of your help. I've been trying to figure this issue out for several weeks and your input got me pointed in the right direction to get it resolved.

Thank you so much for this post. I was experiencing exactly the same issue and you helped to fix it!
-
D dma_pf referenced this topic on
-
D dma_pf referenced this topic on