-
My requirement:
Any devices wirelessly connect to a specific SSID on my access point will get internet access through my VPN provider (vpnunlimited) automatically.
The SSID associates with a VLAN and has a separate subnet defined in my pfSense (v.2.5.2).I'll skip the part where I setup vlan and a separate subnet on my main AP and pfSense. Just ensure your device can access internet, without VPN, after this preliminary step.
Summary setup steps:
- obtain WireGuard setup configuration from your VPN provider website
- start setup on pfSense:
2.1 create a new WireGuard VPN tunnel, interface, and gateway
2.2 create a new peer
2.3 specify VPN dns server in the dns servers section in DHCP service of your desired subnet. This will ensure no dns leak.
Detailed steps:
obtain WireGuard setup configuration from your VPN provider website
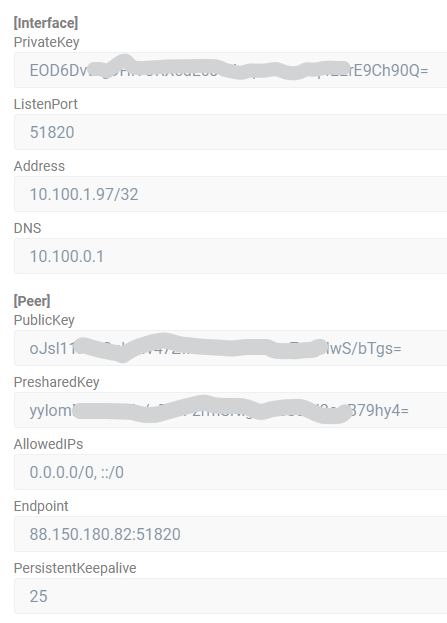
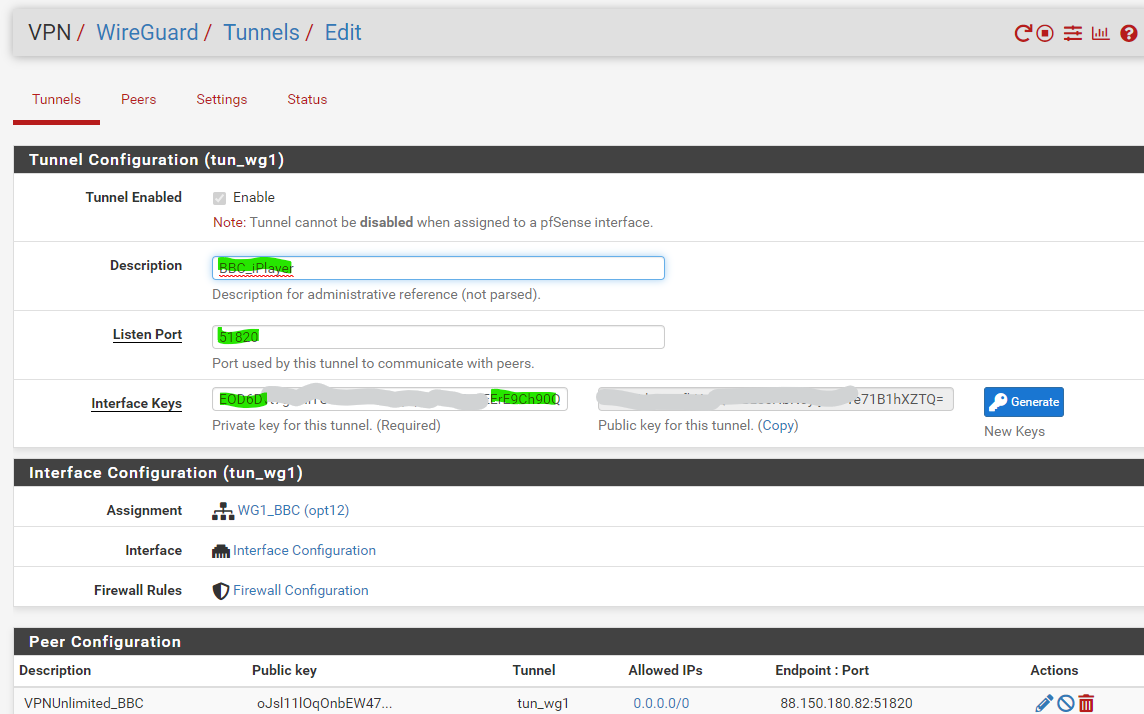
On pfSense, create a new WireGuard tunnel and peer
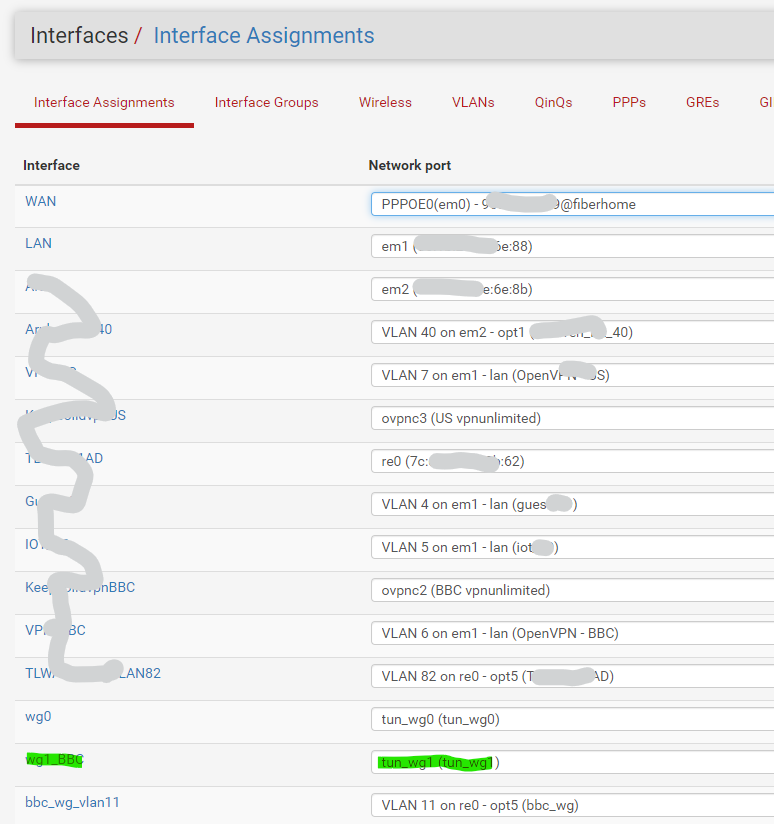
Add a new interface for the tunnel:
Interface setup and also add a new gateway
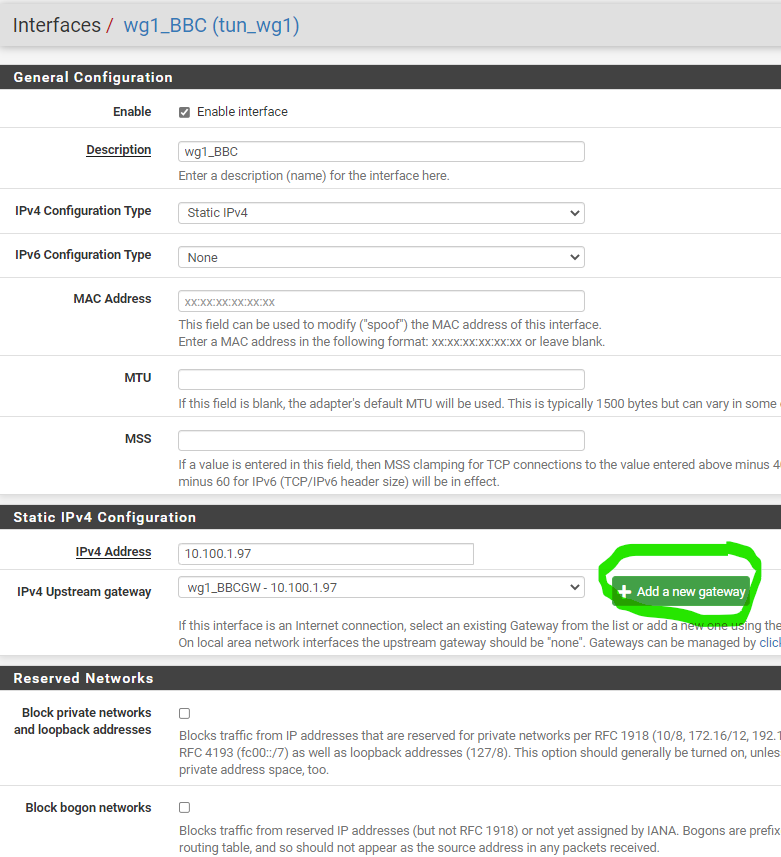
The new gateway added
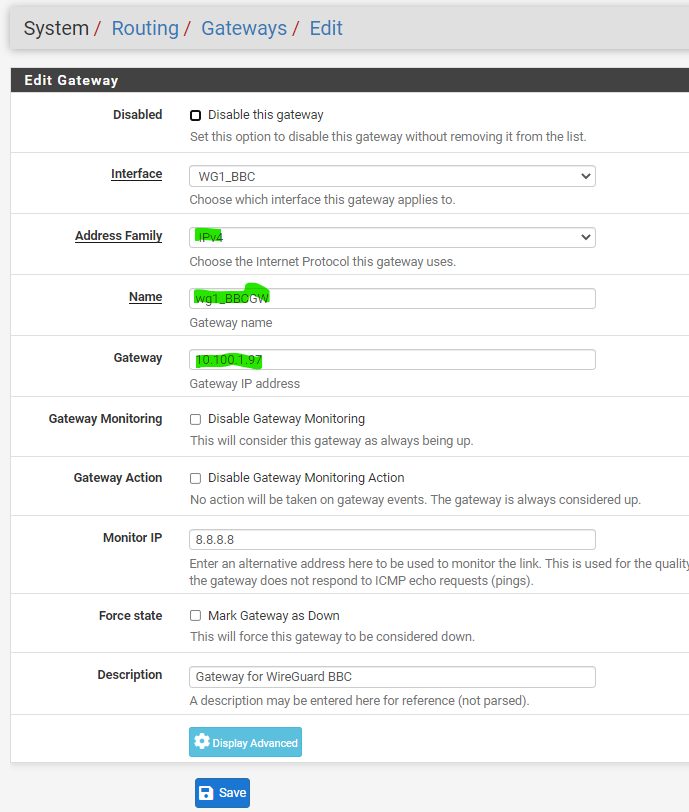
Up to this step, you should see the handshake between your pfSense and your WireGuard VPN provider
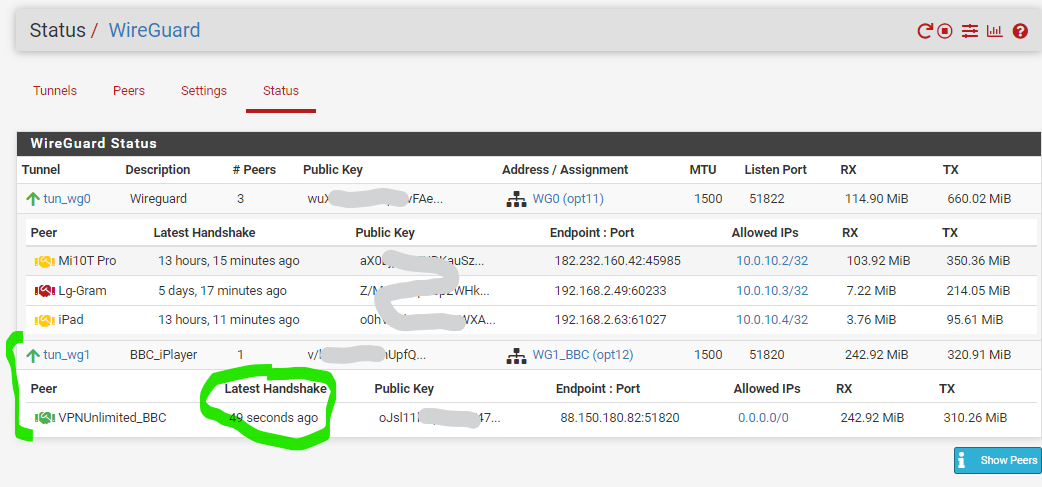
If you add the bandwidth and gateway dashboard, you should see the connection activities.
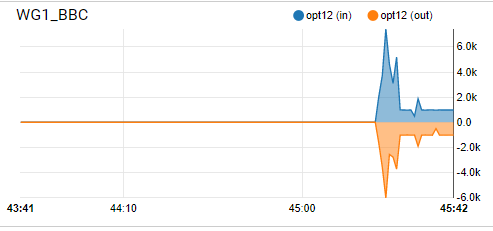
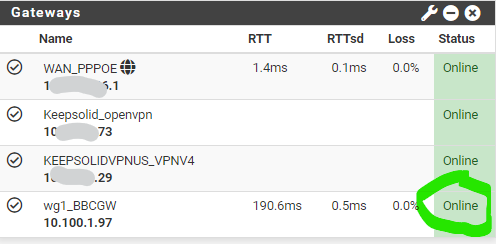
As your WireGuard has an online and good handshake status, you can now move on to define which network in your pfSense want to access through this VPN tunnel. In my case, I want the whole subnet named BBC_WG_VLAN11 to access VPN automatically. So I have to change its gateway to the WireGuard new gateway I created in the earlier step above, by going to the firewall rule:
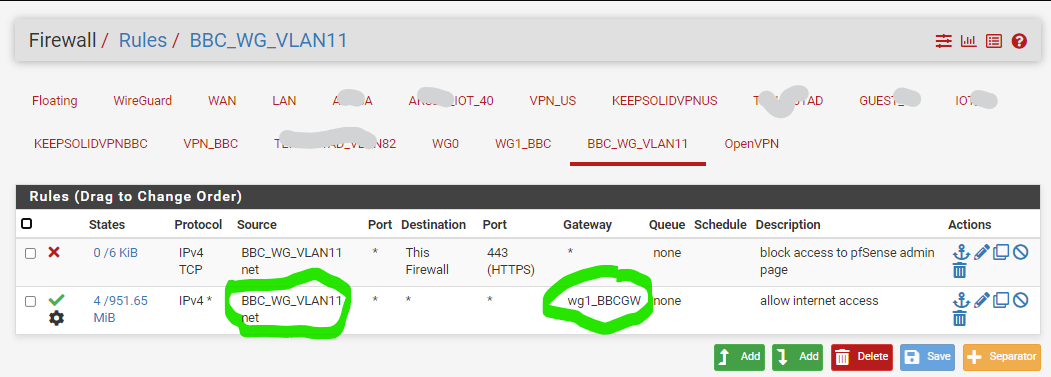
Inside the rule, ensure you choose your source to be the whole subnet (my own requirement) and under the Advanced Option, choose the VPN gateway
Note: if you want only a specific IP, on your main LAN, to always go through VPN, you may create another firewall rule in your main LAN interface, specify a single host and putting the IP. Don't forget to specify the VPN gateway for that rule too
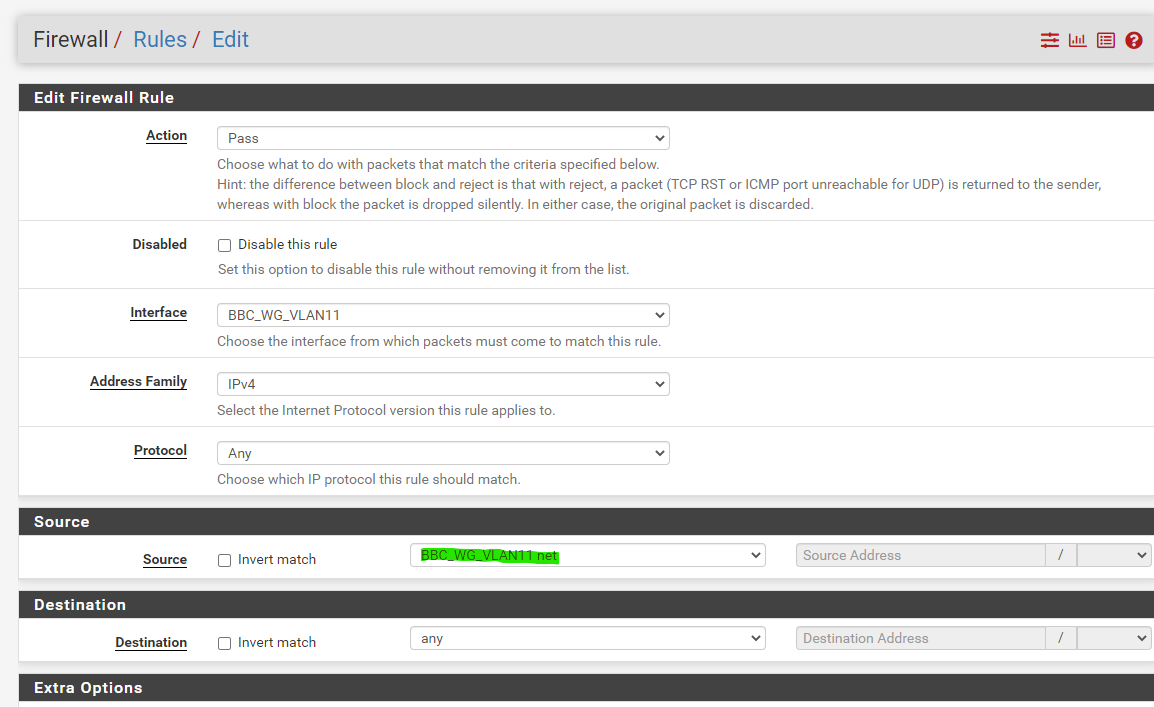
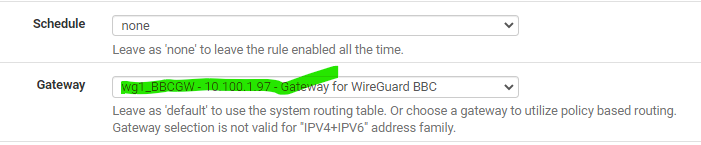
under the Advanced Option, choose a VPN gateway
That's all the setups. Now you can use your device wifi to connect to the SSID and run a speed test, you should see two strange server names.
You may also go to dnsleak.com to check whether you have dns leak or not. It won't leak if you set up right.
Please let me know whether you find this instruction useful; or I should improve any settings above.
Thank you.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.