how to hide connection information in openvpn?
-
hi. I used pfSense and created a client to site layer 3 openvpn connection. clients can connect to this network without any problem. but this website https://ips.ac can detect connection information of openvpn like network link and operation system of client and another information.
how i can avoid this information leak?
I added missfix into config.ovpn file and this problem fixed. but i dont want do this on client side. how i can add missfix and fix this problem on server side? -
@usus1 said in how to hide connection information in openvpn?:
but this website https://ips.ac
This site doesn't exist ??
Correction :
dig ips.ac +short 157.7.174.95It does .... but doesn't answer for me.
edit again : it's a "http" only site !! That must be the last one on planet earth.
Why would this site 'scan' VPN connections ?I think I don't understand the question.
The VPN client connects too the OpenVPN server, and when the tunnel comes up, all traffic form the client goes over the tunnel to the OpenVPN server.
The clients visits the site "ips.ac" - and "ips.ac" could see that traffic comes from the WAN IP of the OpenVPN server, but also sees details from the OpenVPN client ?
Like what : an IP ? -
This post is deleted! -
@gertjan said in how to hide connection information in openvpn?:
@usus1 said in how to hide connection information in openvpn?:
but this website https://ips.ac
This site doesn't exist ??
Correction :
dig ips.ac +short 157.7.174.95It does .... but doesn't answer for me.
edit again : it's a "http" only site !! That must be the last one on planet earth.
Why would this site 'scan' VPN connections ?I think I don't understand the question.
The VPN client connects too the OpenVPN server, and when the tunnel comes up, all traffic form the client goes over the tunnel to the OpenVPN server.
The clients visits the site "ips.ac" - and "ips.ac" could see that traffic comes from the WAN IP of the OpenVPN server, but also sees details from the OpenVPN client ?
Like what : an IP ?sorry for this mistake.
the website is : https://ipx.ac/run
in this website under tab "TCP Connection" can detect my Network link as OpenVPN Connection and also detect client OS. i do not like this. how i can avoid detecting my OS and Network link? i want to detect Network link as PPPOE replace OpenVPN Here.
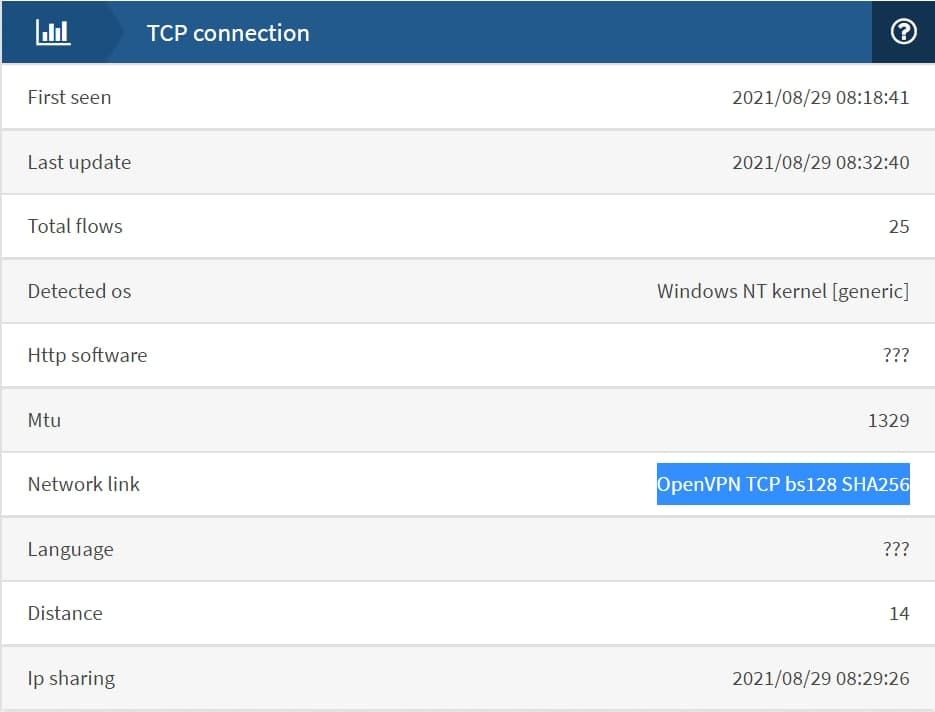
-
@usus1 said in how to hide connection information in openvpn?:
https://ipx.ac/run
I'm using my ISP connection, no VPN that I know of.
I saw :

That info is wrong.
-
That's interesting...
My results:
- ISP connection the result is PPPoE
- over my AirVPN (which is setup on OpenVPN on pfsense) it's ????
- over my own OpenVPN it's OpenVPN TCP bs128 SHA256 lzo.
- over my own OpenVPN which exits out of the AirVPN WAN it's ???
Must be something on the OpenVPN server config.
-
@gertjan said in how to hide connection information in openvpn?:
@usus1 said in how to hide connection information in openvpn?:
https://ipx.ac/run
I'm using my ISP connection, no VPN that I know of.
I saw :

That info is wrong.
no it isn't wrong for me.
how i can avoid to displaying OS and Network link in this result? -
@usus1
Most of the info you see is obtained from/via your browser.Lock your browser down.
I'm running Linux mint , and use Firefox.
I just installed this extension , can actually come in handy sometimes.
Ie. If you need to download an OSX app , on a webpage that only offers to your reported OS.
I told my agent switcher to "fake to be a Chrome on Win 10"

And it works ... Your site now shows :
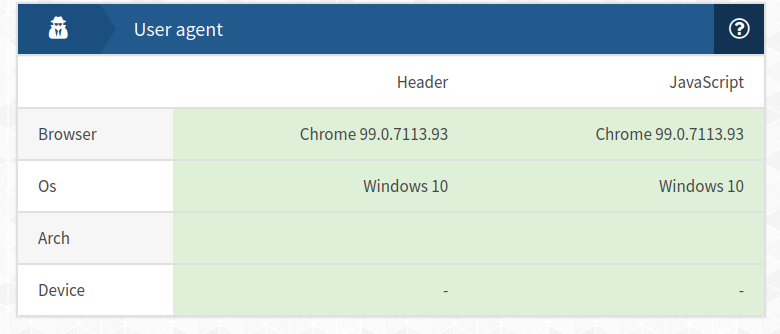

This info seems to be mostly guesswork (at least for my pc)
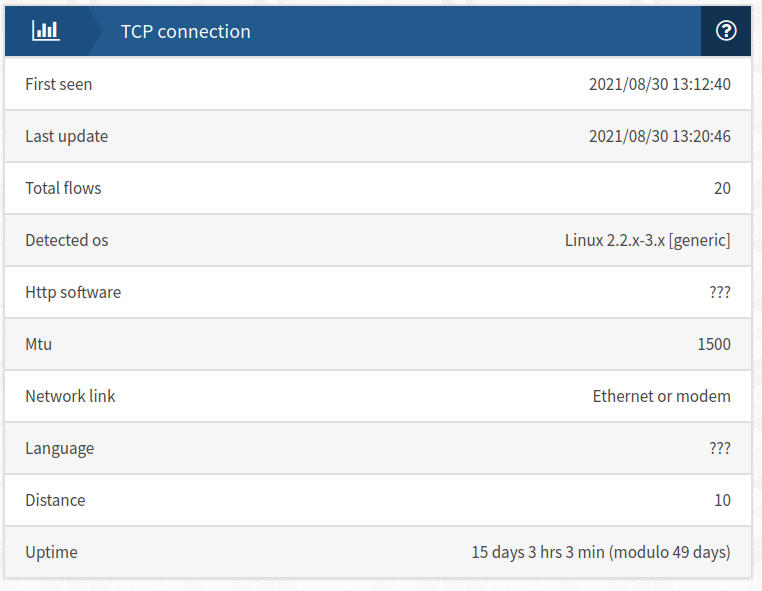
My Linux is a 5.4 not 2 or 3
uname -a Linux TXXXs 5.4.0-xx-generic #91~18.04.1-Ubuntu SMP Fri Jul 23 13:36:29 UTC 2021 x86_64 x86_64 x86_64 GNU/LinuxMy uptime:
uptime 15:30:44 up 1 day, 3:08, 1 user, load average: 0,44, 0,45, 0,39So as i wrote lock down your web browser , that's the one leaking most of the info.
I use NoScript on FF , works so nice
/Bingo
Edit...
I had to be a Mac tooJust select in the extension


-
@bingo600 said in how to hide connection information in openvpn?:
@usus1
Most of the info you see is obtained from/via your browser.Lock your browser down.
I'm running Linux mint , and use Firefox.
I just installed this extension , can actually come in handy sometimes.
Ie. If you need to download an OSX app , on a webpage that only offers to your reported OS.

I told my agent switcher to "fake to be a Chrome on Win 10"

And it works ... Your site now shows :


This info seems to be mostly guesswork (at least for my pc)

My Linux is a 5.4 not 2 or 3
uname -a Linux TXXXs 5.4.0-xx-generic #91~18.04.1-Ubuntu SMP Fri Jul 23 13:36:29 UTC 2021 x86_64 x86_64 x86_64 GNU/LinuxMy uptime:
uptime 15:30:44 up 1 day, 3:08, 1 user, load average: 0,44, 0,45, 0,39So as i wrote lock down your web browser , that's the one leaking most of the info.
I use NoScript on FF , works so nice
/Bingo
Edit...
I had to be a Mac tooJust select in the extension



hi.
i dont use anything in client side. only i want to disable this information leak on server side. -
@usus1
So your client connects to your pfSense via VPN , and then connects to : ipx.ac site , and leaks information.And you want to solve that on the pfSense (server site) ?
Good luck with that.
/Bingo
-
@usus1 said in how to hide connection information in openvpn?:
no it isn't wrong for me.
Check your MTU value.
I've set the MTU to the default '1500' value.
Now I have
When I lower the MTU a bit, like 1478, as some PPPOE connection do, then "https://ipx.ac/run" says I'm using a tunnel or VPN connection.
Plain wrong as I don't use a VPN.That is :
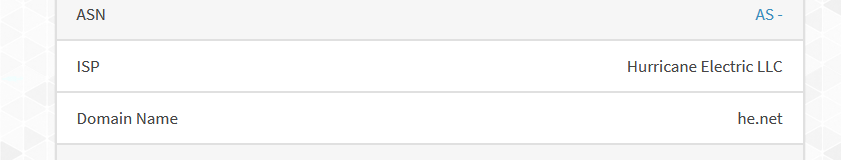
I'm using he.net as my IPv6 "ISP".
My IPv6 traffic goes tunnled out to a he.net IPv6 POP in Paris.
This means that IPv6 packets are stashed into an IPv4 'tunnel'. The MTU or my IPv6 is lower as the classic MTU, 1478. This because the IPv6 packet has to be put in a 1500 classic IPv4 packet. remove the header space, and less (less then 1500) is left over for the IPv6 packet.
So, https://ipx.ac/run thinks I'm using a VPN .... -
Split tunnel maybe ?