How to configure a VLAN for a guest network
-
I have a pretty good understanding of networking and a reasonable familiarity with VLANs but I am having trouble figuring something out from the pfSense documentation (which otherwise I find extremely good).
I have an SG-3100 which is replacing an Apple AirPort Extreme (802.11ac) unit as my router.
Currently my main (wired) network supports my primary network (no VLAN) and a 'guest' network (VLAN 1003). The 'guest' network is mainly used to support a 'Guest' WiFi network. The guest network has a completely different sub-net from the primary network.
My WiFi network is provided by 4 APs (3x AirPort Extreme, 1x TP-Link). These support two separate WiFI networks; the primary network and a 'guest' network. Internally the APs send all traffic for the primary network over the 'no VLAN' network and send all traffic for the 'guest' WiFi network over VLAN 1003.
My main switch is set such that the ports which the APs / Router connect to (only) pass both non-VLAN traffic and VLAN 1003 traffic.
The above setup works well and has been in place for a few years now.
Now that I am deploying the SG-3100, I want to replicate this setup with that. I have switched the 'router' AirPort Extreme to bridge mode so it acts as just a regular AP. I need to setup the LAN port of the SG-3100 so that it is a trunk port (so it will pass non-VLAN traffic and traffic for VLAN 1003). I also want the same setup for one of the other 4 switch ports on the SG-3100 (so I can connect an AP to it). I plan to use the SG-3100 to provide DHCP and DNS service for the 'guest' network.
How exactly should I configure / assign VLAN 1003 on the SG-3100? Should the LAN port be the parent interface for the VLAN (will that still allow it to pass non-VLAN traffic too?)? If so, how do I also get the same behaviour for one of the switch ports on the SG-3100? The pfSense documentation just isn't clear (at least to me) on these points and I am concerned that if I make a mistake I will cause a lot of problems for myself (such as making the LAN port carry only VAN 1003 traffic, which would be quite a problem).
Hoping someone can advise, thanks.
-
You put the guest SSID on a VLAN with the native LAN as the parent and main SSID on the native LAN. Here I use VLAN 3 and here are my rules:
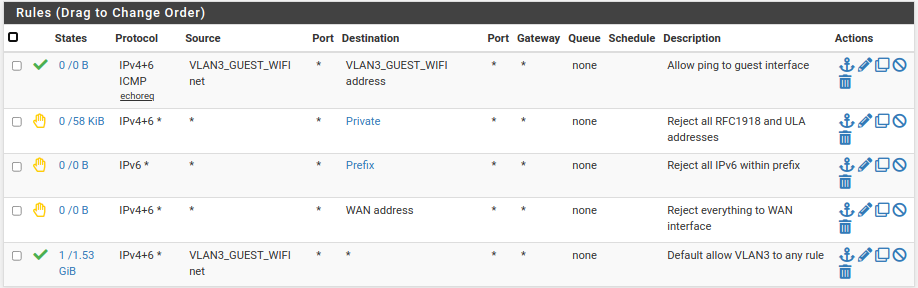
-
@jknott Thanks for the reply. So, you created the VLAN interface with the native LAN interface as the parent and then both untagged traffic and VLAN traffic can flow through that physical interface (seems it must or this would not work)? That's what I wanted to confirm, thanks!
-
@jknott Just checked with an old timecapsule that I had hanging about, its tagging the guest wifi with 1003 and using the native vlan for normal wi-fi.
You want all 4 AP's to connect to the 3100, you'd be better connecting them to a managed switch.
-
@nogbadthebad That's right, Airport units use VLAN 1003 for the guest wifi and native for normal wifi (I mentioned that above). I have a managed switch (as I mentioned) and 3 of the APs are indeed be connected to that. One however will be located right next to the SG-3100, and also I don't have any spare connections back to the switch from that location (switch is elsewhere), hence my desire to connect it to one of the switch ports on the SG-3100.
May I ask why you recommend connecting all the APs to the managed switch rather than have one connected to the (LAN side) of the SG-3100?
-
@chrisjenk If they're all connected to a managed switch you'd be able to tag both SSIDS vlans when they exit the 3100 and just have the non guest untagged the managed switch end and the guest tagged with 1003.
Its a bit cleaner IMO.
-
@nogbadthebad I see what you mean, though I do not need/want to tag the main network at all either at the SG-3100 or my managed switch. Thanks for the info though; I think I have enough to get it working as I want.
-
Yes, the whole point of VLANs is to have multiple virtual networks share a single physical network. In my case, I use it to carry guest WiFi to pfsense. In offices, the computers might share the cable and switch port with VoIP phones, etc..