Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs
-
Wondering if I have misconfigured something. If I have LAN and VLAN (IoT) assigned to the same network port, in my case igb1, do I need to have 2 instances of Suricata running? I.e. One for LAN interface and one for the IoT VLAN.
This is what I currently have, and was puzzled to see one of my IoT devices (ring cam) show up on both LAN and IoT vlan Suricata logs.
I have my TV connected to my Unifi switch and assigned the IoT profile, and as expected only shows up on the IoT Suricata alert logs which probably answers my question, but then why is this not the case with my ring cam?
Unsure if it matters, but my ring device and other IoT devices are connected to a Unifi AP with an SSID that is tagged with the IoT vlan.
-
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
Wondering if I have misconfigured something.
Hi,
Is it important to know whether we are talking about IDS or IPS?
Is also of importance parent interface or virtual in relation to the above installation.I don't know if the situation has changed(?), but there are/were ongoing problems with the NETMAP stuff on VLANs (IPS mode!), see Bill's comments here:
https://forum.netgate.com/topic/151825/suricata-inline-mode-ips-and-vlans/13
and/or
https://redmine.openinfosecfoundation.org/projects/suricata/wiki/VLAN_Handling
++++edit:
Helping you to learn, slightly old but usable:
https://forum.netgate.com/topic/70170/taming-the-beasts-aka-suricata-blueprint/11
-
Its true that multiple instances of Suricata is neded on every interface that you wish to run IDS/IPS on.
A device cannot connect on two networks at once and show up in the logs.
-
Suricata (and Snort, too) actually runs on the physical interface. This means it sees all traffic moving over the connection. That's why you are seeing IoT alerts from that VLAN combined with LAN alerts. I assume LAN is the parent interface here, and the IoT VLAN runs on the LAN parent.
If you run the same rule set on both interfaces, then just put a single instance on the LAN (or whatever constitutes the physical, parent interface) and call it a day.
Today, the IDS/IPS packages are not well suited for use with VLANs. They will work much better when protected networks are on separate physical interfaces. This is particularly true with Inline IPS mode operation, because the netmap kernel device used in that mode does not get to see VLAN tags.
-
@cool_corona So have I misconfigured something in my network?
-
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
I assume LAN is the parent interface here, and the IoT VLAN runs on the LAN parent.
This is correct.
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
If you run the same rule set on both interfaces, then just put a single instance on the LAN (or whatever constitutes the physical, parent interface) and call it a day.
That would be my thinking, but my TV which is physically connected to a port and assigned the IoT vlan profile on the switch does not show up on the alerts for LAN.
Whereas my devices connected to wifi on an SSID tagged with the IoT vlan, do appear in the LAN alerts.
Could this be because the AP has an ip from the LAN network?
-
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
That would be my thinking, but my TV which is physically connected to a port and assigned the IoT vlan profile on the switch does not show up on the alerts for LAN.
Whereas my devices connected to wifi on an SSID tagged with the IoT vlan, do appear in the LAN alerts.
Could this be because the AP has an ip from the LAN network?
Not sure I am following the connections here. When you say "port" and "switch" with regards to the TV, can you be more descriptive? Do you mean a separate port on the firewall connected to a switch that then connects to the TV? If so, and Suricata is not running on that physical port, then no traffic will be seen by Suricata on that port. Assigning a profile has no impact there.
In the case of an AP, connected to the LAN port of the firewall (or to a switch port of a switch that comes directly off the firewall's LAN port, then the traffic for hosts using that AP will traverse the physical layer interface for the LAN and thus will be seen by Suricata running there.
-
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
Not sure I am following the connections here. When you say "port" and "switch" with regards to the TV, can you be more descriptive? Do you mean a separate port on the firewall connected to a switch that then connects to the TV?
My apologies, let me clarify.
I have the LAN interface assigned to the igb1 port on my netgate device which is where the Unifi switch is currently connected to. Both the TV and AP are connected via ethernet to a port on the switch.
Below you can see my really basic setup.
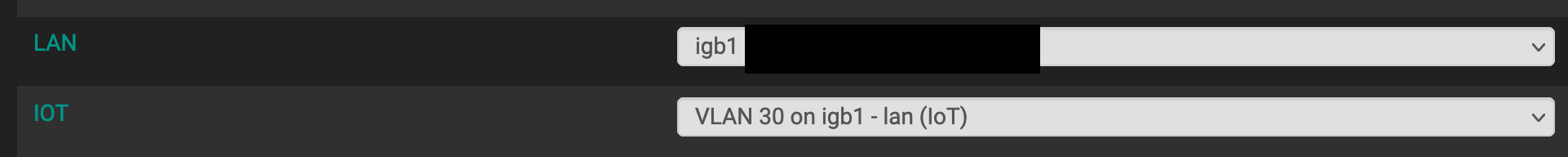
The port profile for the TV is the IoT Vlan, and I correctly dont see its alerts on my Suricata LAN alerts.
The AP has an IP address belonging to the LAN network, and this AP has two SSIDs (one for LAN and one for VLAN). This is where I am puzzled, where the IoT devices on the SSID show on both LAN and IoT vlan Suricata alerts.
So is it due to the AP being on the LAN network that the IoT devices appear in both Suricata alert logs?
-
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
In the case of an AP, connected to the LAN port of the firewall (or to a switch port of a switch that comes directly off the firewall's LAN port, then the traffic for hosts using that AP will traverse the physical layer interface for the LAN and thus will be seen by Suricata running there.
So this answers my question at the end of my first reply, correct?
-
@daddygo thanks a lot for the information! I currently only have it in IDS mode.
-
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
Not sure I am following the connections here. When you say "port" and "switch" with regards to the TV, can you be more descriptive? Do you mean a separate port on the firewall connected to a switch that then connects to the TV?
My apologies, let me clarify.
I have the LAN interface assigned to the igb1 port on my netgate device which is where the Unifi switch is currently connected to. Both the TV and AP are connected via ethernet to a port on the switch.
Below you can see my really basic setup.

The port profile for the TV is the IoT Vlan, and I correctly dont see its alerts on my Suricata LAN alerts.
The AP has an IP address belonging to the LAN network, and this AP has two SSIDs (one for LAN and one for VLAN). This is where I am puzzled, where the IoT devices on the SSID show on both LAN and IoT vlan Suricata alerts.
So is it due to the AP being on the LAN network that the IoT devices appear in both Suricata alert logs?
It's not the IP address that really matters so much as it is the physical interface where Suricata is running. With the VLAN defined on physical interface igb1, and Suricata running on that interface, it will see all traffic coming across the interface. Evidence of that is the fact it is alerting on some of the IoT devices as well as the LAN devices (and showing IoT alerts in both instances).
It should produce alerts from your TV assuming a rule signature has triggered for your TV. Perhaps no rules have matched on the TV traffic. Are you 100% sure your TV has traffic that matches a configured rule?
-
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
It's not the IP address that really matters so much as it is the physical interface where Suricata is running
This certainly helps clear things up. I was unaware of this.
For reference here is a screenshot of the Suricata instances.
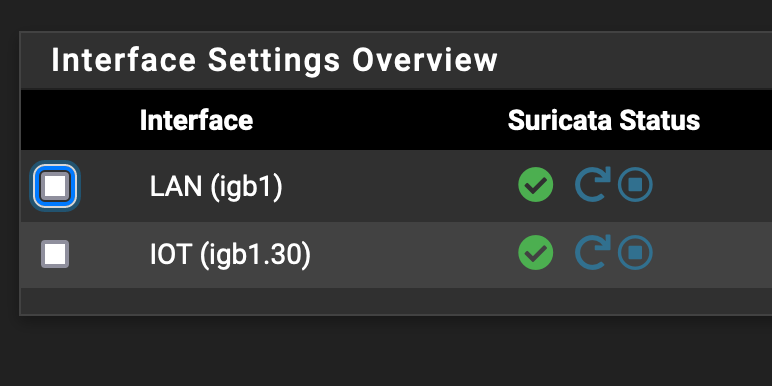
And to answer your question, yes I believe I am sure. I filtered the logs for both instances for the IP address of the TV. In the IOT instance, I see a lot of Stream errors with a destination ip to netflix. In the LAN instance, none show up :/
-
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
It's not the IP address that really matters so much as it is the physical interface where Suricata is running
This certainly helps clear things up. I was unaware of this.
For reference here is a screenshot of the Suricata instances.

And to answer your question, yes I believe I am sure. I filtered the logs for both instances for the IP address of the TV. In the IOT instance, I see a lot of Stream errors with a destination ip to netflix. In the LAN instance, none show up :/
But are you running the exact same enabled rules on both instances of Suricata? It's the rules that determine what triggers, not the IP addresses of the hosts. What also matters greatly is how HOME_NET and EXTERNAL_NET are configured, since many, many rules check those variables and also direction to determine when to fire.
-
@bmeeks ah yes. I do have the same rules enabled on both instances. In fact, i just duplicated LAN instance and assigned to the VLAN.
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
HOME_NET and EXTERNAL_NET
Are these variables in the config?
Also sorry for the dumb question, but the IPs help see which device made the traffic to trigger the alert right?
-
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
@bmeeks ah yes. I do have the same rules enabled on both instances. In fact, i just duplicated LAN instance and assigned to the VLAN.
@bmeeks said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
HOME_NET and EXTERNAL_NET
Are these variables in the config?
Also sorry for the dumb question, but the IPs help see which device made the traffic to trigger the alert right?
You are misunderstanding what I meant by the IP remark.
It appears that IDS/IPS administration is perhaps quite new for you. Some research on Google might prove helpful in understanding the inner workings of tools such as Suricata and Snort. HOME_NET and EXTERNAL_NET are vitally important parameters when it comes to how rule signatures fire. The actual content of those variables can be seen in the
suricata.yamlfile for the interface. -
@code4food23 said in Puzzled about the number of Suricata instances needed for LAN and VLANs due to device showing up on both alert logs:
Also sorry for the dumb question, but the IPs help see which device made the traffic to trigger the alert right?
Hello,
Forgive me (pls.) for butting into the conversation here, but Bill is absolutely right that the management of IDS/IPS systems is a challenge for many well trained administrators too.
To run them in your home, I don't think it's absolutely necessary....
pfSense basically drops all unwanted traffic on the WAN interface +++++ if you use a well configured pfBlockerNG you are safe, this can be said.
The Suricata, Snort can cause a lot of headaches, if you are not skilled enough to handle them, I would start with a VM install and practice before deploying it on my system.
You can also get away with a lot of the abuse your family sends you when the internet isn't working in your home.

(and it can limit a lot of other things in the background if it's set up wrong, which you haven't even discovered yet, FTP, SFTP, Torrent, P2P other, streams, etc.)BTW:
The physical interface is the "igb_" interface (Intel PHY) that physically connect to the port (RJ45) on your pfSense box, those IDS/IPS systems listen to the traffic on the physical interface, so if you create virtual things (VLAN) on that interface, their traffic will pass through it, but as written the VLAN handling is not really functional at the moment (because of the tags)
++++edit:
Don't get me wrong, I'm not trying to dissuade you and welcome to the team, but at least run it in alert mode first to avoid a lot of unwanted problems.