HEADS UP: DST Root CA X3 Expiration (September 2021)
-
You may see a notification about an ACME CA expiring. This is normal and expected. One of the older CA entries is being retired. See https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/ for the details.
That said, because the old intermediate and new intermediate use the same subject and key, it can confuse the pfSense GUI a bit about which certificates use which CA.
To make sure things are correct:
- Check the CA manager and make sure you see the
ISRG Root X1ACME CA and a copy of theR3CA which shows theISRG Root X1CA as its issuer. Any current cert should have shown this for a while. - Find the old copy of the
R3CA which should be shown as expiring onWed, 29 Sep 2021(exact time/date will vary by time zone) and delete this CA entry - Check the CA list and find any ACME certs which now show
externalfor the issuer - In the ACME package, manually renew the certificates noted in the previous step
- Confirm that all the ACME certs in the cert manager now show the correct
R3or equivalent CA as their issuer, and that the certificate count for that CA is correct on the CA manager tab. - Restart any services which utilize the certificates in question, or reboot for good measure.
- Check the CA manager and make sure you see the
-
 J jimp pinned this topic on
J jimp pinned this topic on
-
Thanks for the detailed info and validation process.
-
@jimp Thanks for the heads up :). Just put that right here !
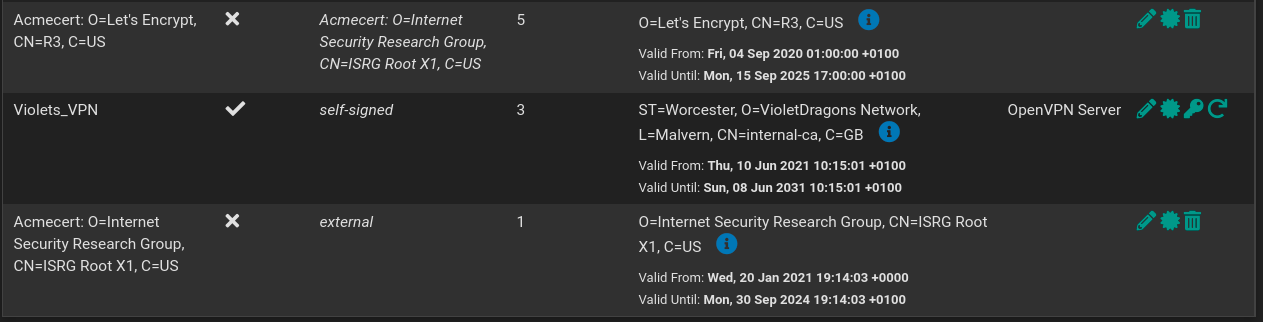
-
@jimp Something to mention, The Cert in the Browser and on MXToolbox still shows its going to expire on the 30th. Im guessing this is normal?
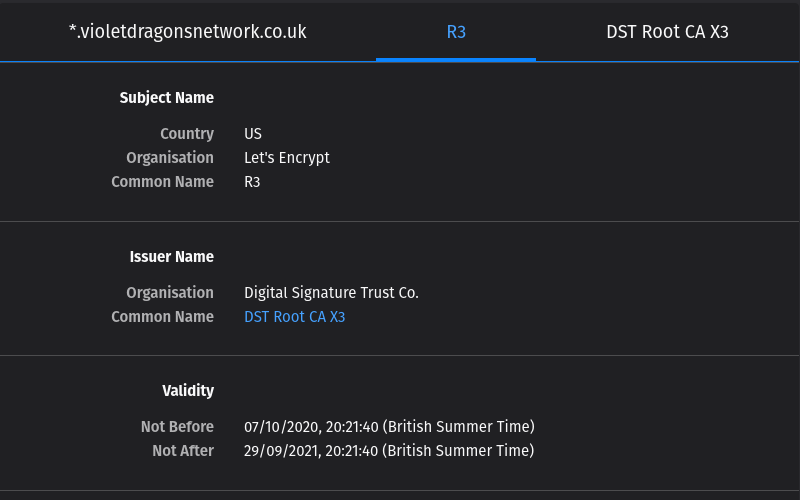
-
@violetdragon Did you restart the services that used the certificate (chain)? If not, the service might still have the old intermediate loaded and cached. If everything is correct your browser, checks etc. should not see the old intermediate that will expire in a few days.
-
@jegr Hi, yeah I restarded haproxy and restarted the firewall and all certs for all domain are showing the same. Tested on another browser but the same. It's strange.
-
@violetdragon Then could you do me favor with the following steps:
- Head over to the Cert Manager
- Delete both LE CAs - the root and the newer R3 - the old R3 should be already gone
- Renew the cert(s) in the acme package
- Check the Cert Manager: the LE CAs should have been recreated as needed
- Then restart the services as needed and check again if the new certificate chain is correct now
Cheers
\jens -
@jimp Thanks for the detailed instructions. I’d seen the expiry warning and wondered why my automatically renewing certificate was still using the old CA. All good now.
-
@jegr Hi, Thanks for your reply. That is what i did the second time as i tested your guide with only one Cert for a different Domain I have and it did the same then i deleted both CAs as you mentioned above but the problem is still there I also restarted Haproxy and the Firewall.
Interesting this is that Certificate Manager Shows it updated the new Cert is also updated as it has the date of creation on it.
Thanks.
Jack.
-
@jegr Update, Just re-new a Cert and deleting both LE's and its still doing the same. Heres another Domain of mine. So not sure what is going.
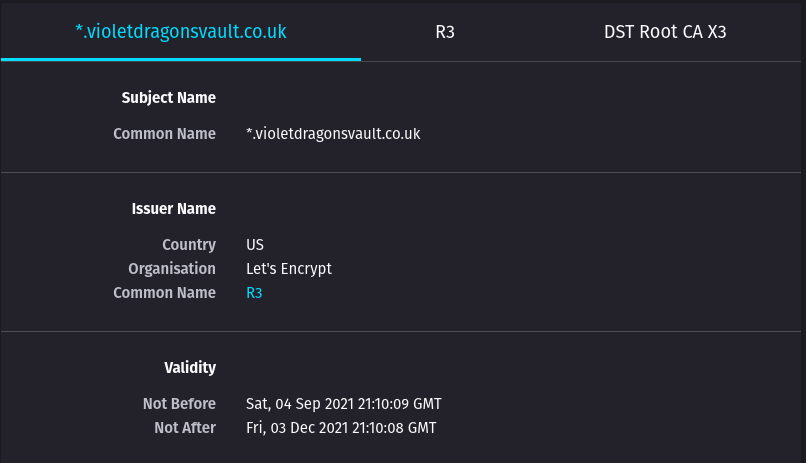
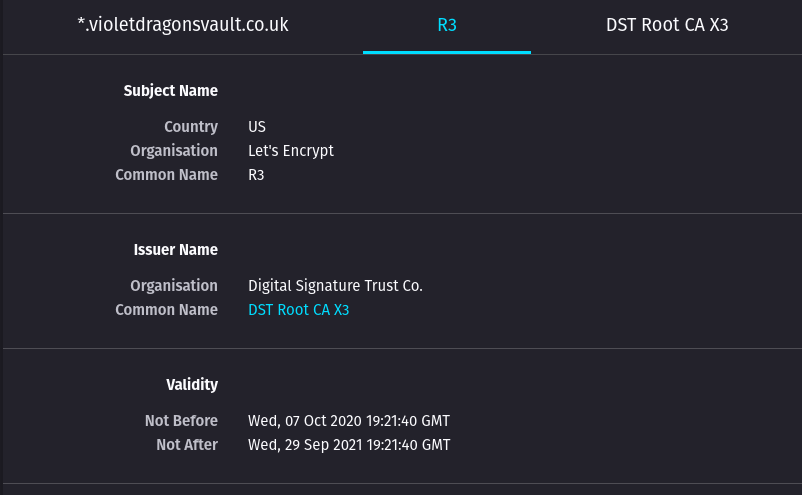
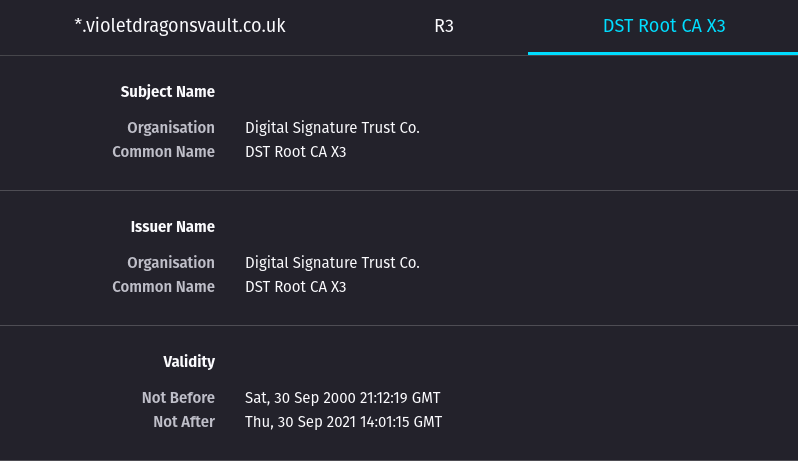
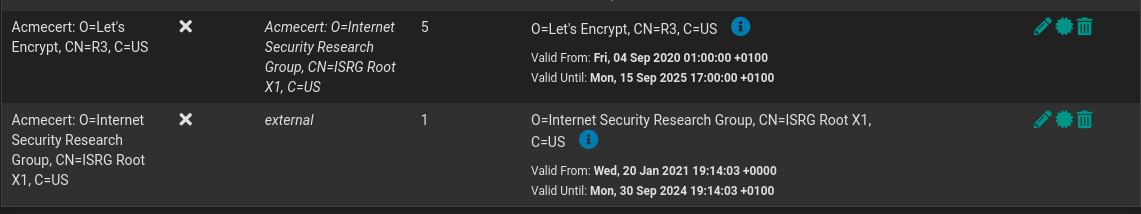
Update,
The Certs are fine it seems to be a Firefox issue as Chrome/Brave Shows different I also checked it against https://decoder.link/sslchecker/ and checks out fine.
Thank for your help guys :)
-
@violetdragon Ah so more of a browser/caching thing - yeah that's a pain in the ass. Good to see it fixed anyway so you won't run into issues at the end of the month :)
-
@jegr Firefox seems to handle it differently. I've noticed that it only happens when signed into a Firefox account so not sure if the account saves the cache but it's a strange one.
-
The browsers / Windows have their own trusted root CAs. I expect that once the old ones expire/get removed/revoked from those built-in stores, the new chain will take precedence and show correctly.
-
for testing while the SSL expire, We did:
Delete the expiring Root CA from the client browser.
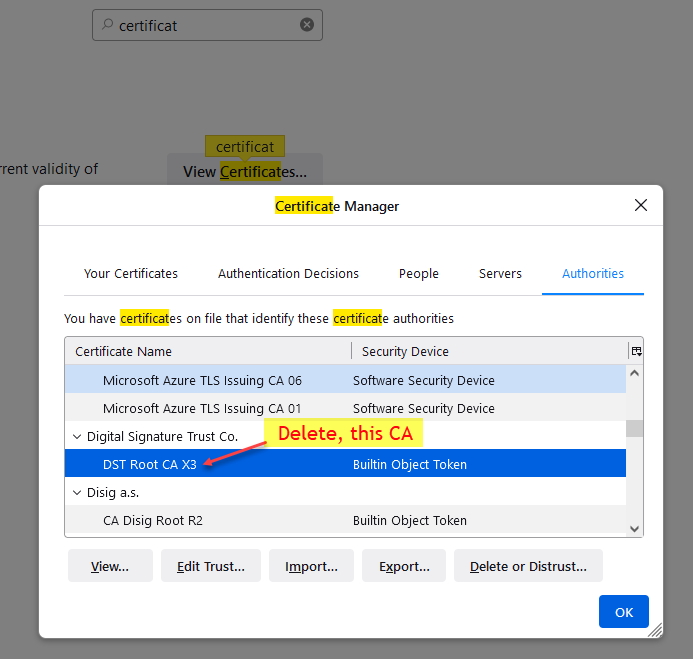
Then, Open private browser:
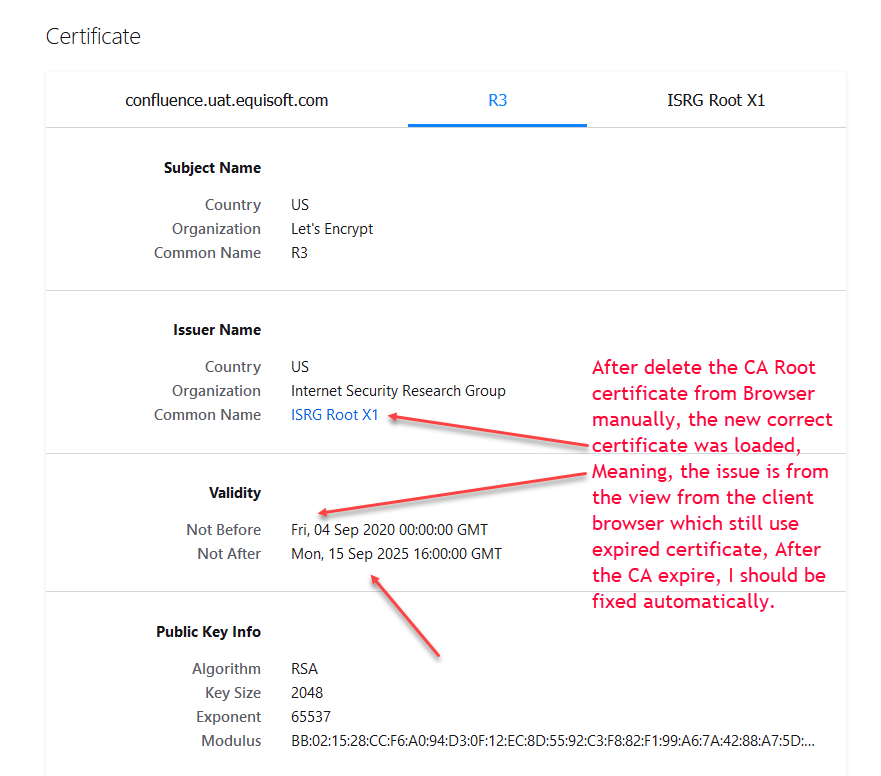
-
@sergio-londono That's solved the problem, Cheers :)
-
Hi all.
We use pfsense 2.4.4 version.
I did all the steps and all looks ok.However reading about openssl, will acme (or any other thing) have issues when renewing certs? Like acme accessing le api which use le cert naturally?
If so, is there a way to fix it as we are unable to upgrade.
Thanks.
-
@maverick_slo why such a old version of pfsense? I would recommend updating.
-
@violetdragon said in HEADS UP: DST Root CA X3 Expiration (September 2021):
I would recommend updating.
While I would too - but I also have some units still on 2.4.4p3 - covid being the reason, with nobody on site.. And I can not go in - can not risk it. They might have to stay on that version until things really get back to normal. And I can be onside for update, and other remote sites have people there that can be my smart hands if things go belly up. Things normally go fine - but just not something can risk at this time. Maybe he is in the same sort of boat.. I hope he meant p3, this was the latest version before covid became a factor..
-
@johnpoz that makes sense. I have worked with people that neglects updating or just too lazy to do updates. Certs should be fine providing you have done the fix in this thread. Openssl has been updated since. You can try doing a dry run to see if it fetched a fake Cert if it does then you will be fine until you can update.
-
@violetdragon I hear ya - you should always be current completely agree 110% Its kind of eating at me that they are not current ;)
But these are different times for sure.. Before this I would of pulled the trigger on a sunday evening from home on the update, even if version just came out on saturday ;) Because I knew I could just go in bit early monday if it went belly up..
So I am currently more willing to give some people slack on the update.. But yeah stay current I am with ya.