LAN traffic not routing through OpenVPN
-
I have a home network with a local ip subnet of 192.168.1.0/24. I am running pfsense 2.5.2 in a VM with both virtual ports connected to the same switch, and the idea is to expose a second gateway in 192.168.120.0/24 (no DHCP) and any computer that uses that gateway rather than the routeur gateway will connect through the internet via a VPN (express VPN). The rationale for doing this is to make certain machines connect to the WAN through ExpressVPN while remaining fully accessible locally to machines that are not connecting to the VPN (by having two IPs but only one gateway).
Summary of the network:
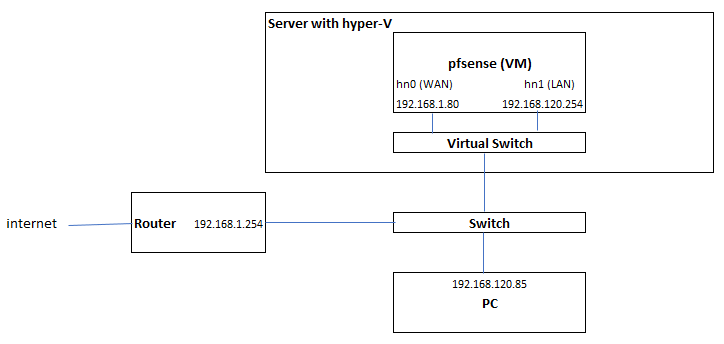
I set up a PC with a 192.168.120.85 IP, and 192.168.120.254 as a gateway, and as expected its traffic is going through the pfsense VM (I can see that by doing a traceroute from the PC, the first hop is 192.168.120.254, the second hop is 192.168.1.254), however instead of coming out on the internet from an ExpressVPN IP, it is coming from my public router IP (which I can see on any what-is-my-ip website). So it looks like within pfsense, the LAN traffic is not being routed to OpenVPN interface internally. IPv6 is disabled on both the PC and pfsense.
I looked at various how-to for setting up pfsense but I can't find what I am doing wrong.
the OpenVPN connection to express VPN seems to be OK, the status is up:
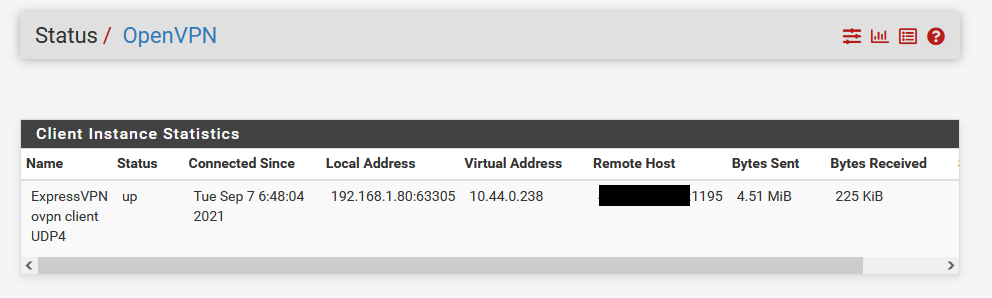
and in fact, within pfsense, if I go into Diagnostics/TraceRoute, and run a TraceRoute setting the ExpressVPNInterface as my Source address, the IP does come out of ExpressVPN's network rather than my home network. So there is no question that OpenVPN is connected and has access to the internet via ExpressVPN servers.
In term of the configurations that I believe are relevant to the routing, here are the screenshots:
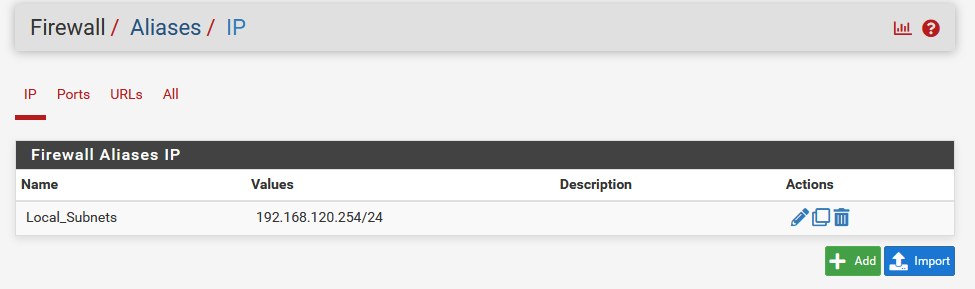
First I setup an Alias "Local_Subnets" for the LAN network:
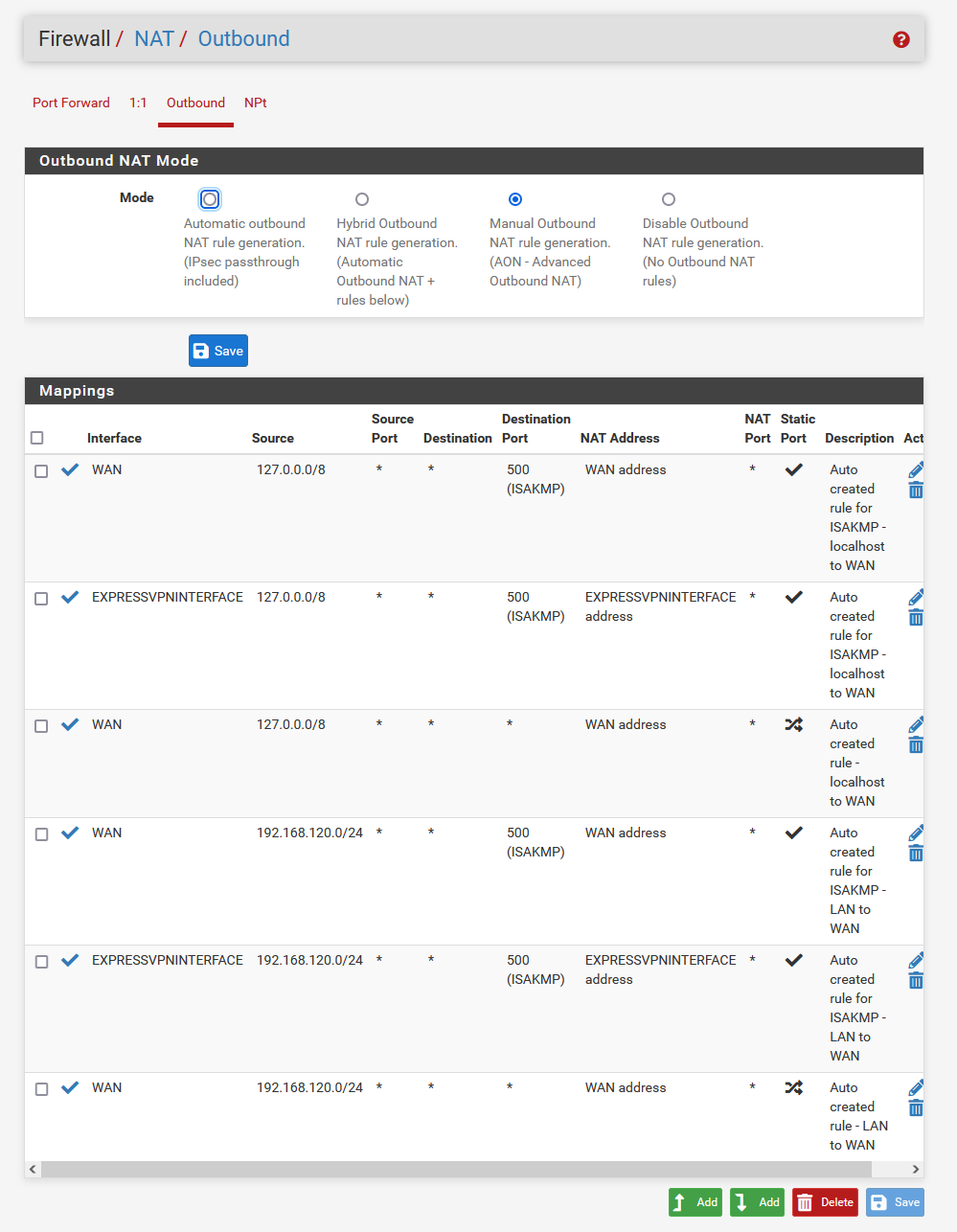
I replicated the Firewall/NAT/Outbond rules by setting the interface to the ExpressVPNInterface as suggested in all tutorials:
And I set up the Firewall Rule to either route "LAN net" or "Local_Subnets" traffic to the ExpressVPNInterface (same result for both configurations)
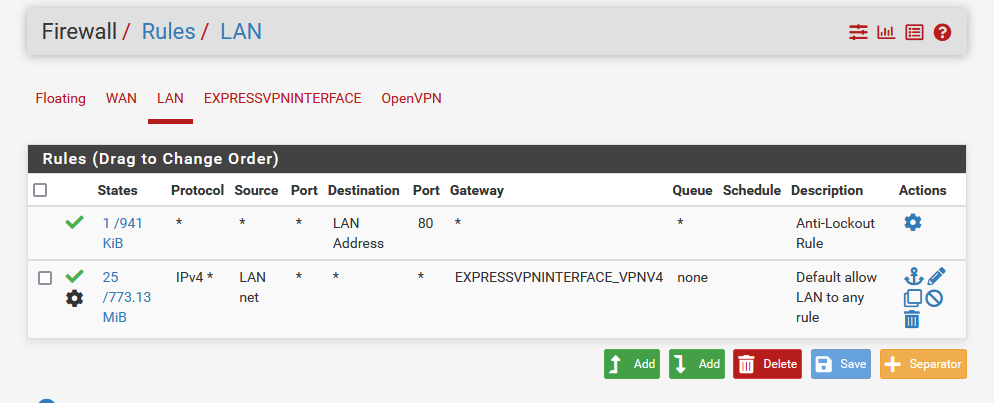
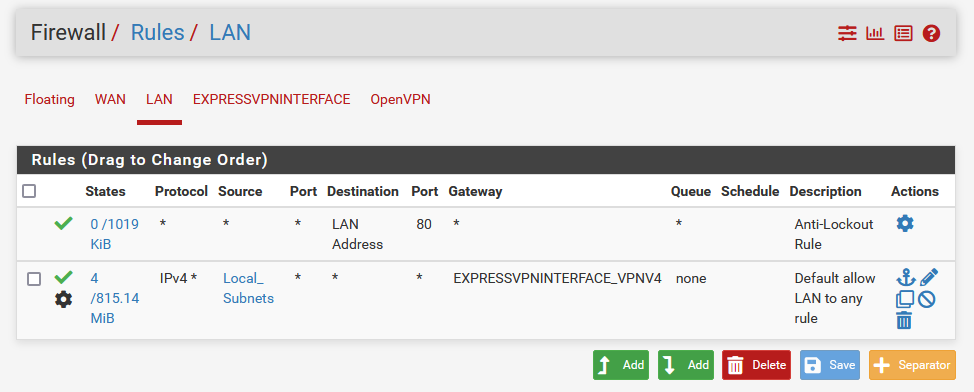
Would anyone have any suggestion to get the LAN traffic to route through the OpenVPN interface?
-
@cfq3q You seem to be missing an outbound NAT entry for your network. The two EXPRESSVPN entries that you have are only for port 500 which is IPSEC stuff. Btw I find Hybrid mode to be better than Manual mode for outbound NAT.
-
@kom Apologies, I think I got lost in the many iterations.
I corrected the NAT Outbound rules (and this is a configuration that I tried in the past, i.e. duplicate all v4 rules changing the interface to the VPN interface), and I seem to run into the same problem, i.e. the PC has access to the internet but it doesn't go through the VPN, it goes directly through my public IP (and I can see 192.168.120.254 as my first traceroute hop).
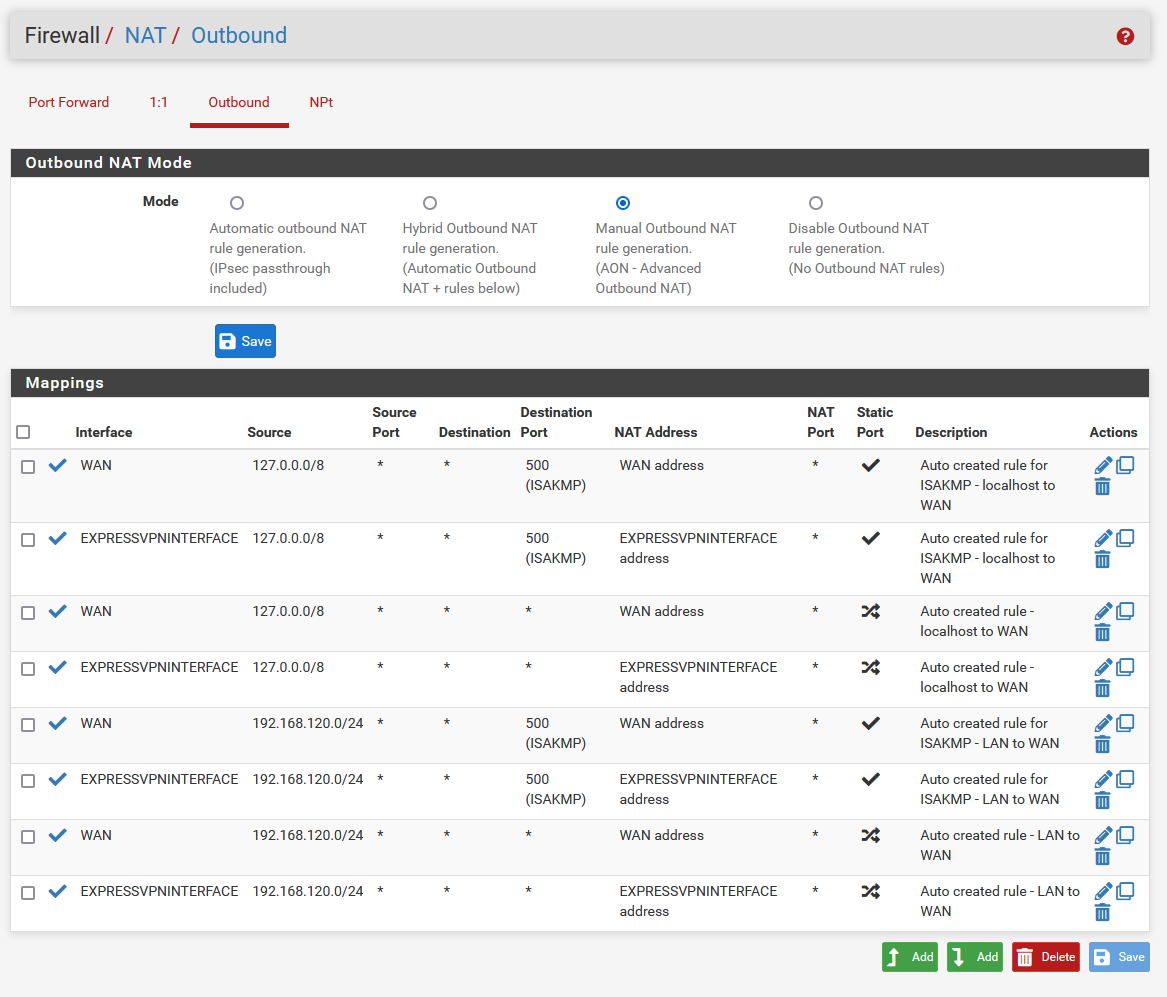
-
@cfq3q OK then it should be working. I don't know why you created an alias called Local_Subnets, just use LAN net. What makes you think your traffic is coming out WAN instead of your VPN?
-
@kom For Local_Subnets, that was one of the instructions I found, but I just changed it to LAN net and it doesn't seem to fix anything.
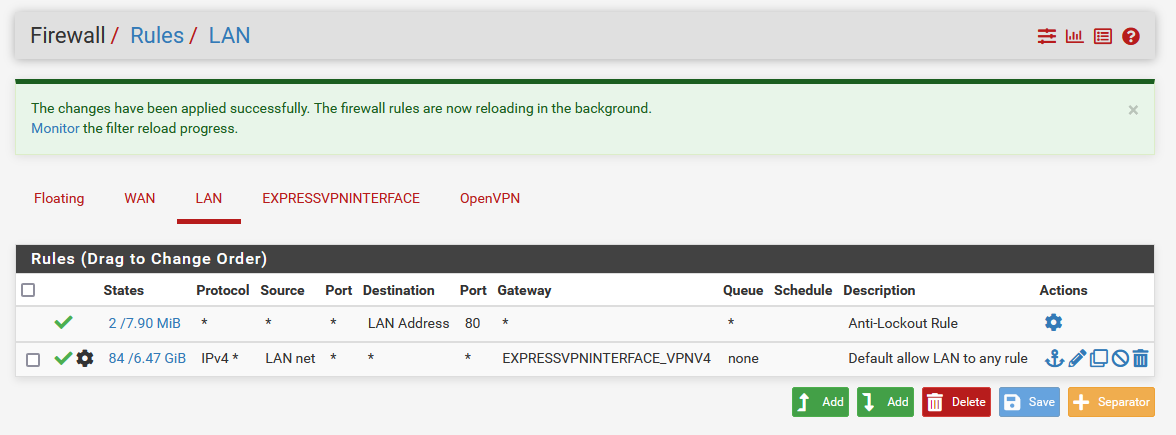
Two things tell me I am not going through the VPN. 1) when I go on a what is my IP website, I get an IP that belongs to my ISP instead of an ExpressVPN IP from another country. 2) when I do a traceroute from within my PC, the first hop is 192.168.120.254 (the pfsense gateway, makes sense), then the second hop is 192.168.1.254 (my router gateway, not good, I should be in the VPN) and after the 3rd hop, I see lots of IPs that belong to my ISP.
I managed to get it work in a different setup where the pfsense VM was connected to two different virtual switches, one external virtual switch for the WAN port (like in my diagram above) and one private switch for the LAN port and a windows virtual machine also connected to the private switch. That works like a charms in such setup.
It must be something related to the fact that both the WAN and the LAN port are on the same switch that must somehow confuse the routing in pfsense. But I don't see why it would and how to fix it.
-
@cfq3q I just noticed that. NICs are cheap. Get a second one and put it in your server then define vswitches for WAN and LAN associated with the correct NIC. Connect your modem to your WAN NIC.
-
@kom Do you mean for the router to be exclusively connected to the WAN NIC of the pfsense VM? I see how it could work but would defeat what I am trying to do.
What I am trying to do is to have a mix environment where most PC on my network are going directly through my public IP (so configured with 192.168.1.x IP / 192.168.1.254 gateway) and a few PC / VM in my network have two IPs and use the pfsense gateway (192.168.1.x and 192.168.120.x IP, and 192.168.120.254 gateway).
This way some machines are connecting to the internet via the VPN, others are connecting through my public IP, but all can talk to each others (and share files) as they are one the same 192.168.1.0/24 subnet.
I can't think of any reason why it shouldn't work other than pfsense failing to route its incoming LAN traffic via the OpenVPN interface.
-
Not sure if it helps but the gateway status shows the vpn gateway as offlline / 100% traffic loss
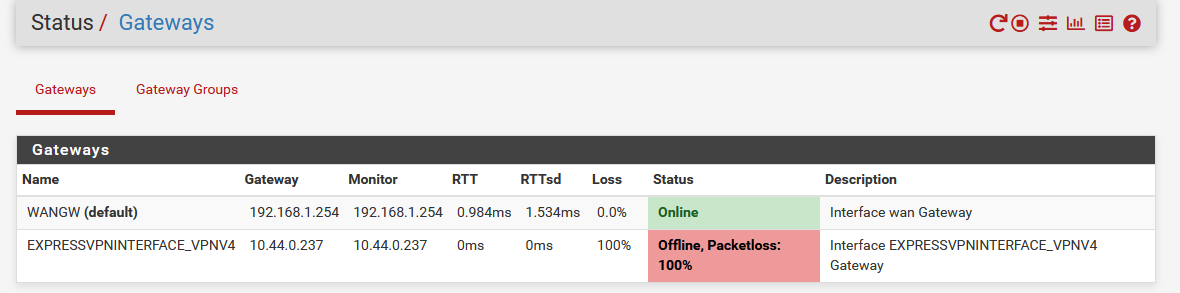
Again I think the vpn itself is online, first because its status is "up" in the Status/OpenVpn tab, and also if I do a traceroute from pfsense, selecting the Source Address = OpenVPN interface, the ips not only reach the destination but all the hops are consistent with the traffic going through the VPN.
-
@cfq3q pfSense will route out the default gateway if it can't talk to the specified gateway. That explains what you're seeing.
-
@kom OK, found the issue, it was basically this: https://forum.netgate.com/topic/82412/pia-openvpn-gateway-offline
the solution was to go into System / Routing / Gateways, and to set the Monitor IP in the VPN gateway to an IP that accepts pings (or to turn off gateway monitoring). Then the status of the gateway switches to online. Then my PC connects to the internet through the VPN.
I just don't understand why the same problem didn't occur on my private switch setup. Perhaps because it is an earlier version of pfsense (2.4.4-p2)