pfSense HA LAN Interfaces Only
-
@iptvcld
Out of curiosity, which devices are belonging to your NOT subnet? -
@viragomann
That is my Network of Things VLAN which I have Smart switch devices such as Tasmota bulbs/switches that i dont want them to reach out to the internet or other devices on my lan. They are all internal controlled/accessed devices. -
@iptvcld said in pfSense HA LAN Interfaces Only:
That is my Network of Things VLAN which I have Smart switch devices such as Tasmota bulbs/switches that i dont want them to reach out to the internet or other devices on my lan.
Ahh. I don't have such devices in my network. All I have want to access at least internet.
-
@viragomann
For that i have the Internet of Things VLAN which those devices have internet access but cannot talk to other vlans/networks on my LAN (inter-chatter) -
@iptvcld
Yes, I have an IOT subnet as well. On this only access to none-RFC1918 is allowed. -
@viragomann said in pfSense HA LAN Interfaces Only:
none-RFC1918
I have this - i guess pretty much the same; IOT can talk to each other on the same vlan but cannot chat to others outside of IOT including the firewall it self
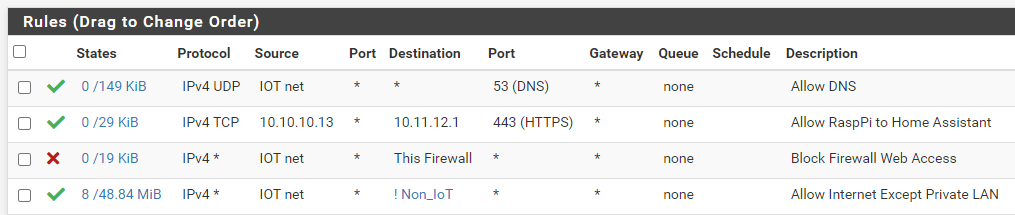
-
@iptvcld
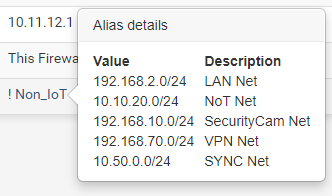
I use an RFC1918 alias on pfSense which simply includes all private networks (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16).
So I'm still save, when I add or change a subnet without the need of modifying the alias. -
@viragomann
This makes sense! -
@viragomann
I was able to locate a video as per below that advises that both Master and backup nodes will share the DHCP lease information and also both hand out IP'sYouTube link at the section he talks about that..
https://youtu.be/Ac6U4xMFaxY?t=2423 -
@iptvcld
Interestingly. Didn't know that. Was assuming only the master is handing out DHCP leases and only the lease state is synced to the other node.