Allow LAN to Access Devices from OPT1
-
Hi, im new to Pfsense and I stumbled upon this problem. I can access LAN devices from OPT1 by configuring a wide open rule. However, I cannot access any device connected to OPT1 from the LAN Network. Both networks can access the internet. I can also ping OPT1 (gateway) from LAN.
Here's my config:
LAN: 192.168.10.1
OPT1: 192.168.11.1I would like to be able to access devices back and from both interfaces. Hopefully you can help me on this. Thanks
-
@aldrinjohn96 well what are your rules? The default lan rule is any any - so lan should be able to access anything on opt1 out of the box.
If you can not then you altered the rules, or the device your trying to access on opt1 has host firewall blocking.
Post up your rules.
-
@johnpoz
Here are my OPT1 Rules
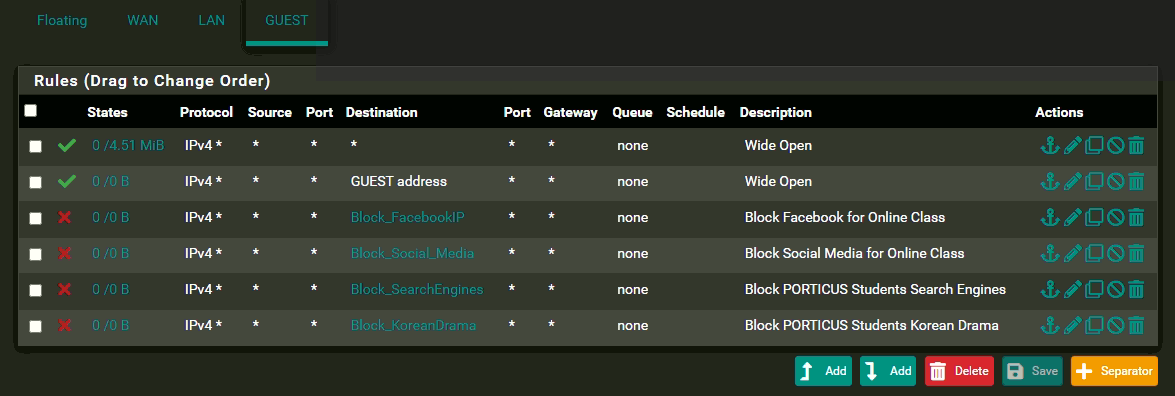
Here are my LAN Rules
I have existing block rules in LAN that are intended for specific websites.
-
None of those blocks are going to do anything.
Rule are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Your top rule allows lan net to go anywhere - so it would never get to any rules below that..
Your rules on opt1 (guest) all below your any any are pointless and would never trigger...
Do you have any rules in floating - since those rules would allow access from lan to guest, and guest to lan.. If you can get to something on the other network its because its firewall is blocking you, or its not using pfsense as its gateway.
-
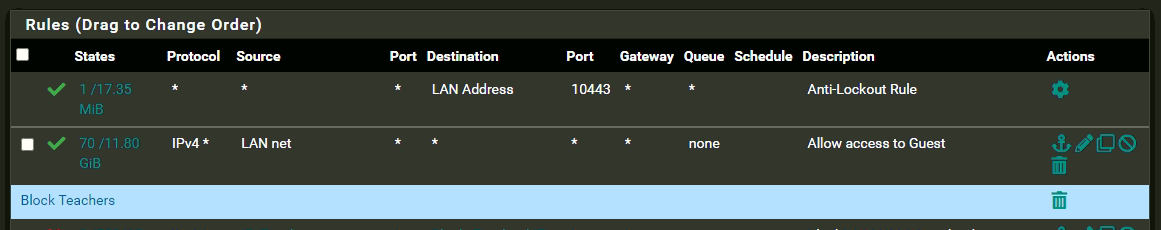
Your second LAN rule and before last LAN rule are "pass all" for LAN traffic to all destinations.
If something is blocking, it must be here :

You could see for yourself what rule is blocking your traffic : look at the firewall logs.
If traffic was matching no GUI rules, it would hit the default (last - hidden) block rule : make it log by checking :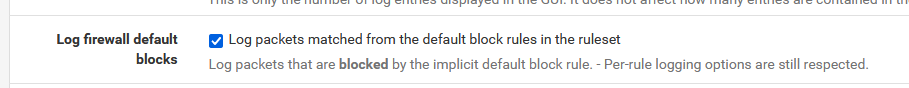
but, as said above, already your second LAN rule matches/accepts all traffic that is IPv4 and has a source addresses based on the LAN network, like 192.168.10.x where x is from 2 to 254.
What are the devices you try to access from LAN, on the OPT1 network ?
edit : I definitely should type faster.
-
@gertjan said in Allow LAN to Access Devices from OPT1:
edit : I definitely should type faster.
hahaha - sorry dude ;) hehehe
-
@johnpoz
The rules in between where you might think is blocking traffic is just the same with the other block rules for IP Aliases that I have made. Something like this:
I have an update though, if I plug a device to OPT1 and use RDC from a device connected to LAN, I can do so. However I still cant ping.
Here's the idea of what I'm trying to achieve, on my LAN is the group of computers where the computers of my students are connected to that I want to have a static map for easier management. It is where I also connect our NAS. On OPT1, this is where I would like to put all other devices that will use internet connection and still be able to connect to our NAS and some other devices.
PS: Yeah, really waiting for someone who knows better for help. hehe
-
@chooks And again rules are evaluated top down, first rule to trigger wins no other rules are evaluated.
If you want to block something, it needs to be above the rule(s) that allow it.. If you have a rule that says any any - you can do anything want. A rule below that blocks from going to X will never be evaluated.
If you want lan to go to opt ip:port - then that rule is above, where you put a rule that blocks lan net from going to opt net.
You showing specific sections of you rules isn't helpful - really need to see all the rules - because of the way they are evaluated top down..
If you have a any any rule that allows, and you can remote desktop too it, but not ping - then rule is not allowing icmp, or the devices firewall blocks the ping. Which is by default windows rules for example. The windows firewall out of the box will block access from anything other than its local network.. If it was on opt network, it would block lan network.. Unless you allowed it on the devices firewall.
If you allow remote desktop but not ping, then yeah you would be able to remote to it - but it wouldn't answer ping.
While pfsense firewalls between the network - you still have the local firewalls on devices running that could be blocking what your allowing on pfsense.
-
Example :
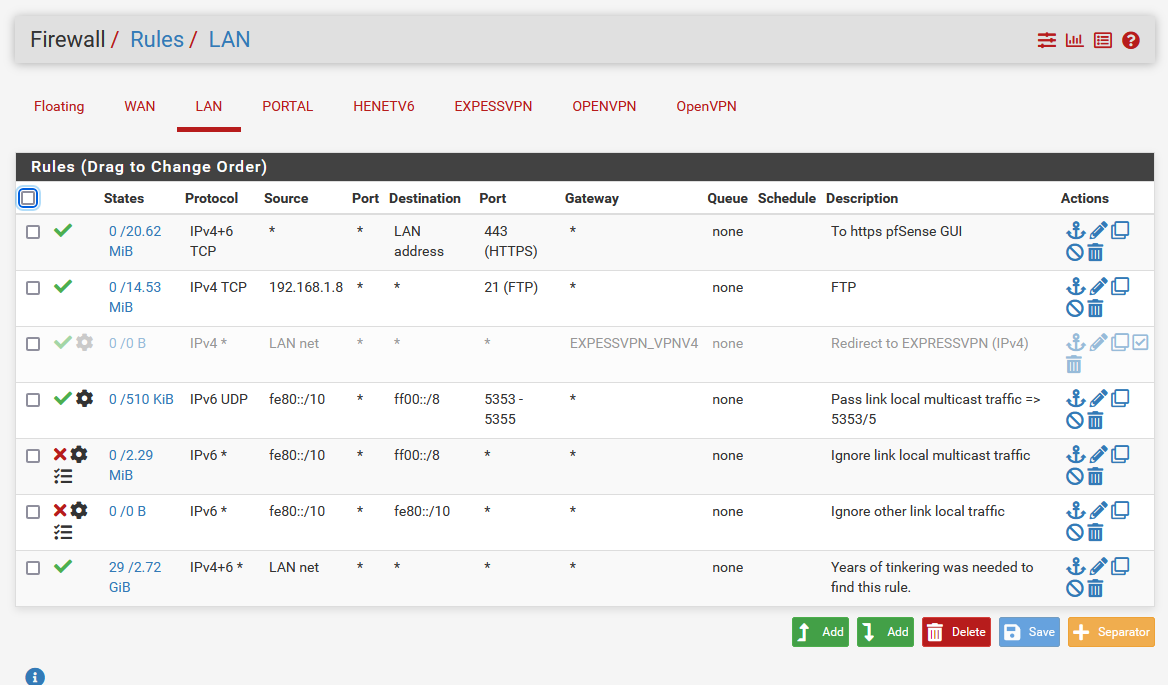
Line 1 is my own "anti lockout" rule.
Line 2 is disabled,
Line 3 is disabled,
Line 4 : consider it disabled as is a IPv6 rule.
Line 5 : consider it disabled as is a IPv6 rule.
Line 6 : consider it disabled as is a IPv6 rule.
So, for simplicity's sake : forget about lines 2 to 6.Line 7 : like yours, a pass all rule for IPv4 and IPv6.
With rule 7 I can reach the entire world. That includes my own, local OPTx interfaces.
-
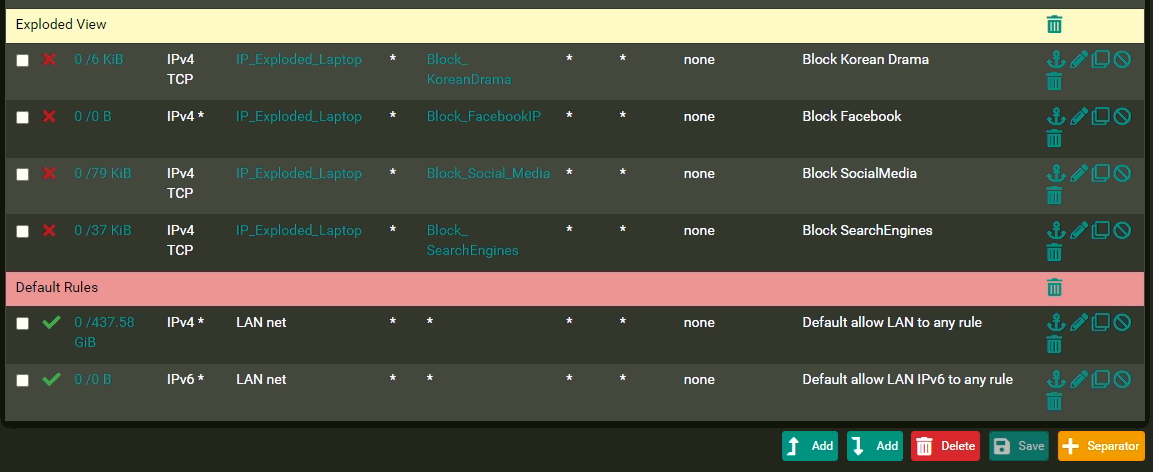
@johnpoz
Here's the long list of rules that I have in my firewall. I understand what you are telling me about the firewall in my device. That might be the answer, but still here's the list of rules, you might see something: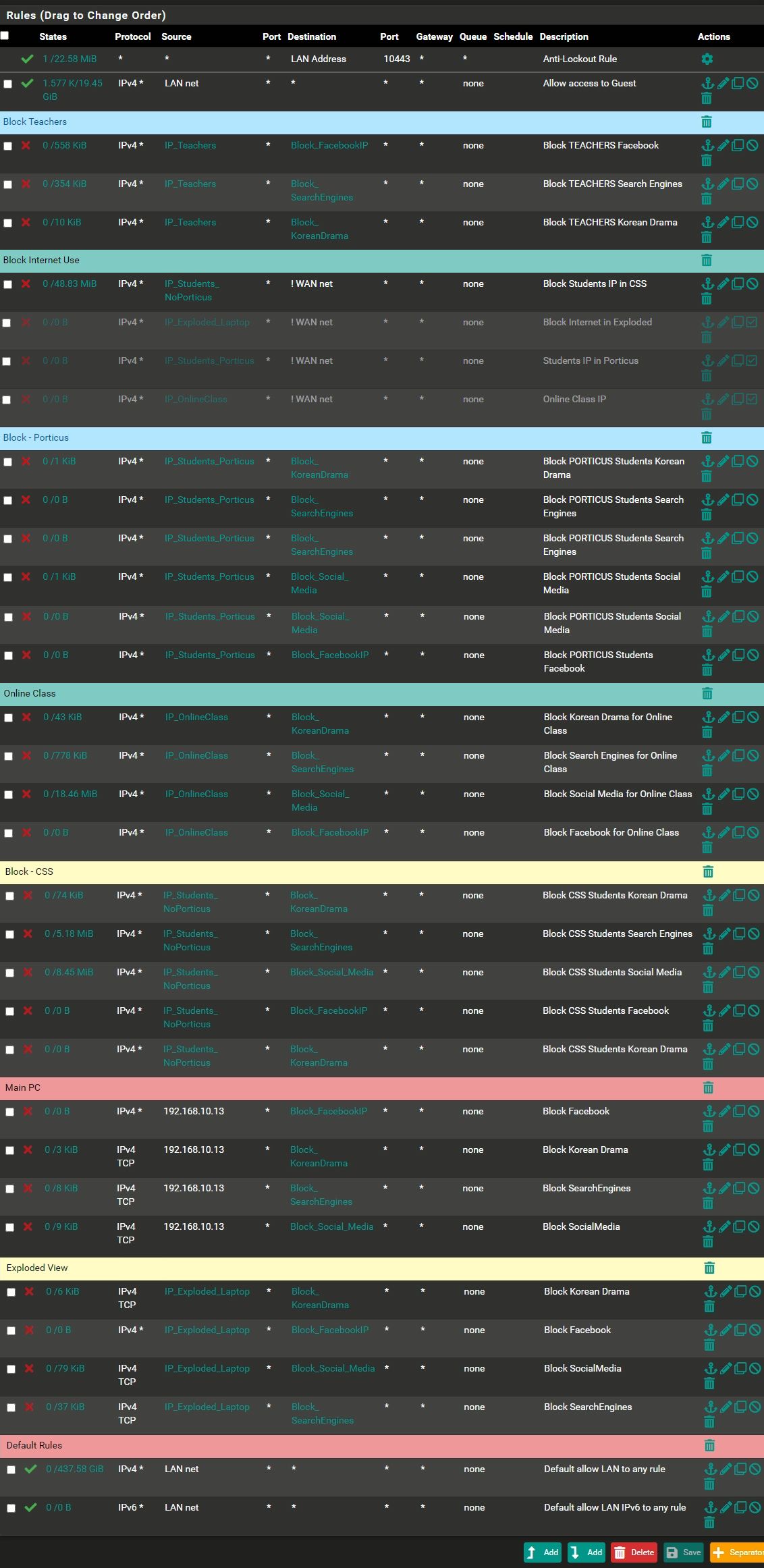
-
-
@chooks none of those rules do anything below this one..
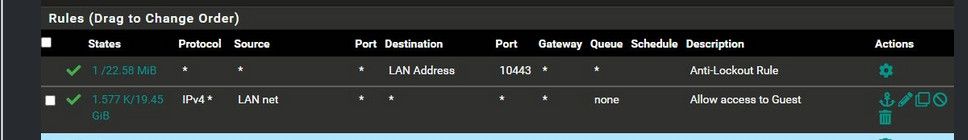
The only reasons you seeing traffic on them - is at some point the rules were in different order. Reset you counters and you will see none of those rules will trigger.
run pfctl -z
it will clear all those counters.
Since you have any any rule at bottom - change that rule to lan net to opt net to allow access to your opt net.. putting that rule at the top like you have it invalidates all the rules below it.