Ipsec & OpenVPN mixed VPN
-
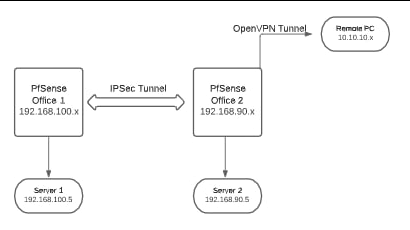
Can anyone help me for this problem? The remote pc in openvpn pings and accesses the servers in office2, the networks between office2 and office1 communicate perfectly, but from the remote pc I can't see the office network 1. Is there a way to make it communicate? Traceroute from 10.10.10.x to 192.168.100.x stops at pfsense2 and that from a machine in office 1 to 10.10.10.x stops at pfsense1. The IPSec tunnel is always active.
Thanks. -
First off, the type of VPN is irrelevant. Both are just another IP path. Your problem has to do with routing. The remote PCs know how to reach the network they connect to, but nothing beyond. What is your default route? Do you have a specific route, if the default doesn't cover it?
-
@jknott
For remote PCs the remote networks are 192.168.90.0/24, 192.168.100.0/24, infact traceroute from 10.10.10.x to 192.168.100.x stops at pfsense2.
I don't know how to handle further steps because pfs2 should already know where 192.168.100.x is and the route to take. But it stops. -
When a remote computer is connected via VPN, what is the default route? Is it whatever you get from your ISP or is it through the VPN to pfsense? If the first, then, unless you specifically add a route, the remote does not know how to reach beyond the other end of the VPN. One of the settings it to force all traffic through the VPN, which makes it the default route and should fix the problem. On the other hand, if you do not want all traffic to go through the VPN, you will have to add a route to reach beyond pfsense.
In the server config, there is a box where you can configure which routes to push. You'd have to add one to reach the other site(s). For example, since I force all client traffic through the VPN, here's what I use:
push "route 0.0.0.0 0.0.0.0";push "route-ipv6 ::/0"If you don't send all client traffic through the VPN, you will have to configure your routes as needed. It could be a matter of simply adding the other site in that box. Of course, the two servers would have to configured to provide the route to the other. Also, the other server will need the route back to your remote computer.
-
@jknott
As you can see below, the route is already passed to the client192.168.90.0 255.255.255.0 10.10.10.1 10.10.10.25 259
192.168.100.0 255.255.255.0 10.10.10.1 10.10.10.25 259infact it reach pfs2.
-
What about the route back from the other site? This is where packet capture comes in handy. See how far your ping reaches and how far any response gets.
This is a simple routing issue, unless you have some filters in the way.
-
@jknott
That's the problem I think, since the pfs1 is the default gw for that lan, but the same pfs1 does not handle correctly the route to 10.10.10.x and I don't know to add a second remote network to the ipsec tunnel. -
You don't add a route to a tunnel. You add it to the routing table. You do that in System / Routing / Static Routes. Any device on the LAN will use pfsense as the default gateway and pfsense will use the routing table to determine where to send the packet.
Routing is done on a hop by hop basis, with each router determining what the next hop is to get closer to the destination.
-
@jknott
I finally solved creating another phase2 in ipsec, now works fine.
As described here:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/multiple-subnets.htmlThanks again for help.
bye.