Configuring a 3rd ISP WAN Interface to another LAN Interface.
-
Hi,
I need some help on configuring a 3rd ISP WAN Interface to another LAN Interface.Current setup I got running is Multi Wan with Failover.
ISP A Public IP - 200.55.5.1
ISP B Public IP - 6.96.6.11
LAN IP - 192.168.1.1What I added and configured
ISP C Public IP - 197.200.1.1
LAN 2 IP - 10.10.10.1 DHCP
DNS Server IP - 8.8.8.8I can’t seem to get the Internet working from ISP C to LAN 2, Lost at the firewall rules or something else I'm missing out on.
Thank you.
-
@amk
So you want the LAN2 to get out to ISP C, correct?Check if pfSense has added an outbound NAT rule for LAN2 and the WAN C interfaces automatically.If not you have to add one by yourself.
For directing out internet traffic from LAN 2 to WAN C you have to set up policy routing rules on LAN 2.
To only affect public destinations add an alias first and add all RFC 1918 networks to it. Then modify your LAN 2 firewall rules which allow outbound traffic and check invert at destination and enter the RFC 1918 alias, expand the advanced options and select the WAN C gateway.Consider that the policy routing rules direct all allowed packets to the WAN C gateway, so you will need additional rules on LAN 2 for internal access. E.g. if you use pfSense for DNS resolution, you have to add a rule for TCP/UDP, destination "This firewall" port 53.
-
@viragomann
Thanks for helping out.Yes Correct LAN2 to get out to ISP C. The Outbound NAT rule was automatically created.
Would it be possible if you could get in details how to create the alias and the Lan rules. I tried and did not work.
Thanks.
-
@amk
Firewall > Aliases > IP > Add
Enter a name, e.g. "RFC1918", select Network(s) from Type drop-down and add the concerned networks to it.The following screen shows the content of my RFC1918 alias and how I use it in the firewall rule.
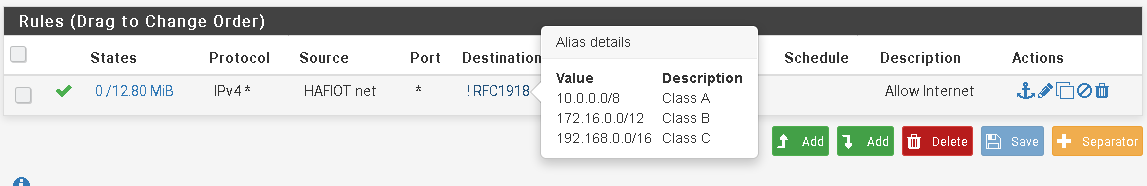
In your case you have to select the WAN C gateway additionally in advanced options. -
Thank you so much!
I struggled and finally thought of rebooting the box and it worked, I think that was the issue before as well I should have tried a reboot.
-
@amk
Glad that you get it working finally.