Bypassing DNSBL not working
-
Hi,
We have a list of sites and domains we are blocking on our network through DNSBL user defined feed.
I am looking to test bypassing this list for specific computers on the network that I've already set reserved IPs for in the DHCP server.
I've changed the DNSBL Mode to Unbound python mode
I've enabled DNSBL Blocking & Python Group Policy.
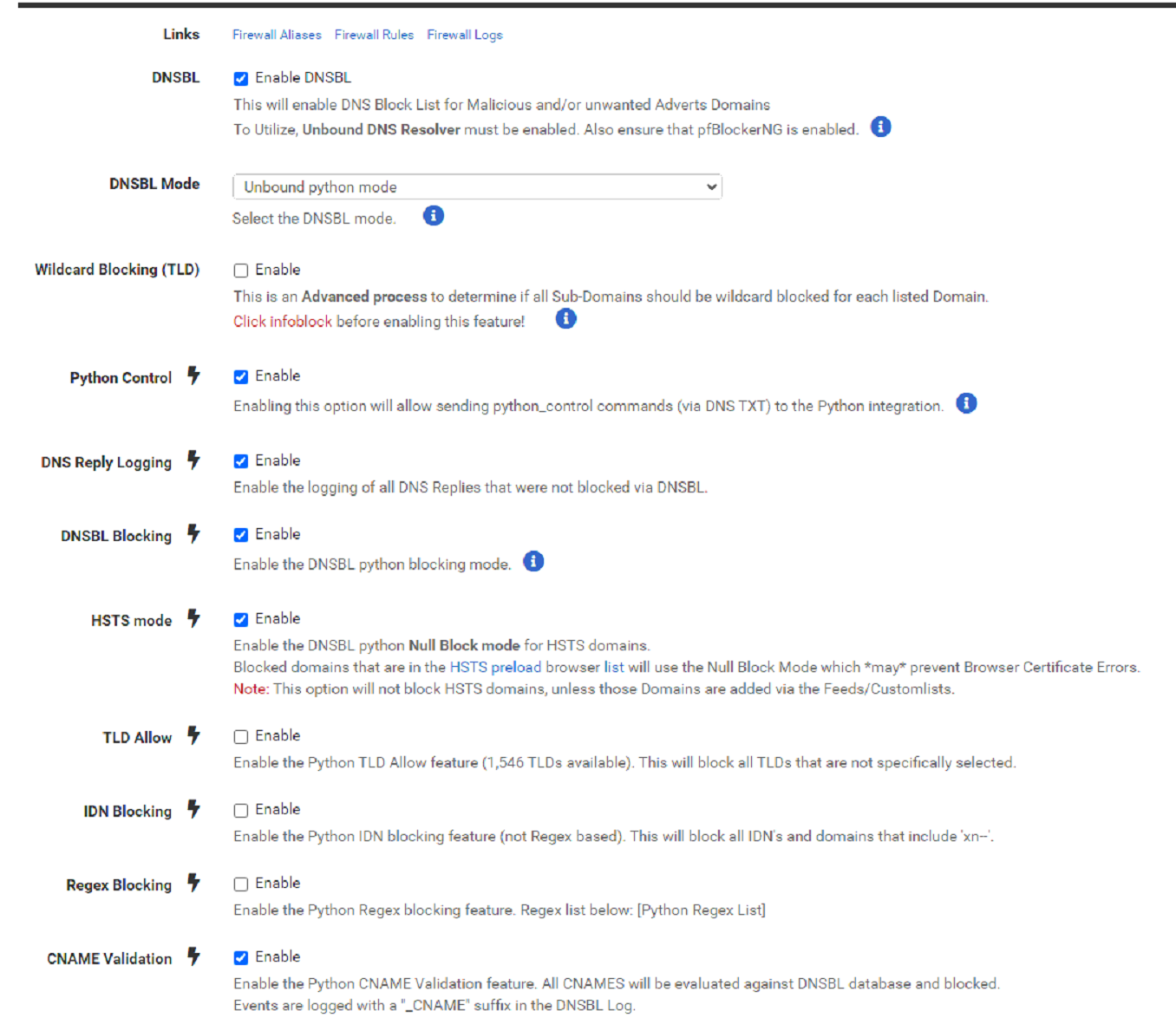
In the Python Group Policy, I've added my client IP address I want to allow as "192.168.192.200/24" [I also tried just 192.168.192.200 instead of /24 didn't work.]
Reloaded "All" under Update. yet those domains are still inaccessible on the computer I've whitelisted.
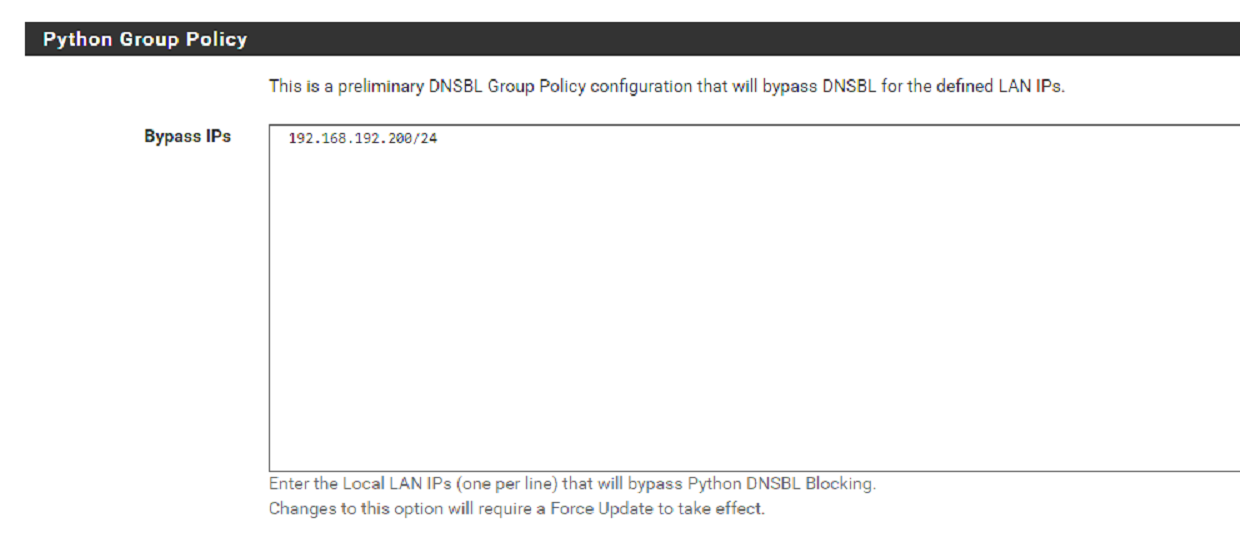
-
What do you want to show with the first image ?
Not the activation of the Group Policy as you cut it out .The ByPass IPs list is a list with IP's, not a network like 192.168.192.200/24
Use one line per IPv4.
Don't forget the IPv6 if your devices uses them and pfSense uses IPv6 to access the Internet.Furthermore, you need to know that host names are resolved, and cached on several stages.
A step-by-step way of testing could be :
Disable pfBlockerNG totally.
Executeunbound-control -c /var/unbound/unbound.conf reloadto reload unbound, with the side effect of flushing the cache.
Or restart unbound with the GUI.
On your Windows PC, close all browsers, and wipe the local DNS cache :ipconfig /flushdnsCheck that with an test site like https://d3ward.github.io/toolz/adblock.html that nearly nothing gets blocked. Some might still show sites seem to be blocked, that is because the host names tested simply do not exist any more.
Activate pfBlockerNG.
Do a full reload of pfBlockerNG.When I tested with two PCs, like :
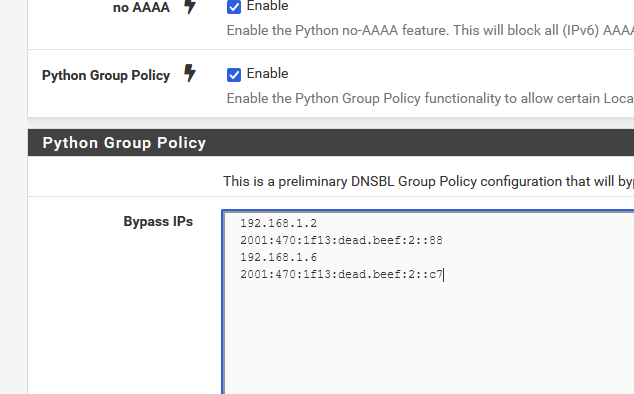
the two PC's showed all the usual adds.
When I emptied the Group Policy list, and reloaded pfBlockerNG,, my "addblock score" on these PC's jumped to nearly 80%.
-
Hi, Thank you for responding... sorry for the delay in responding.
Here is the screenshot that its enabled
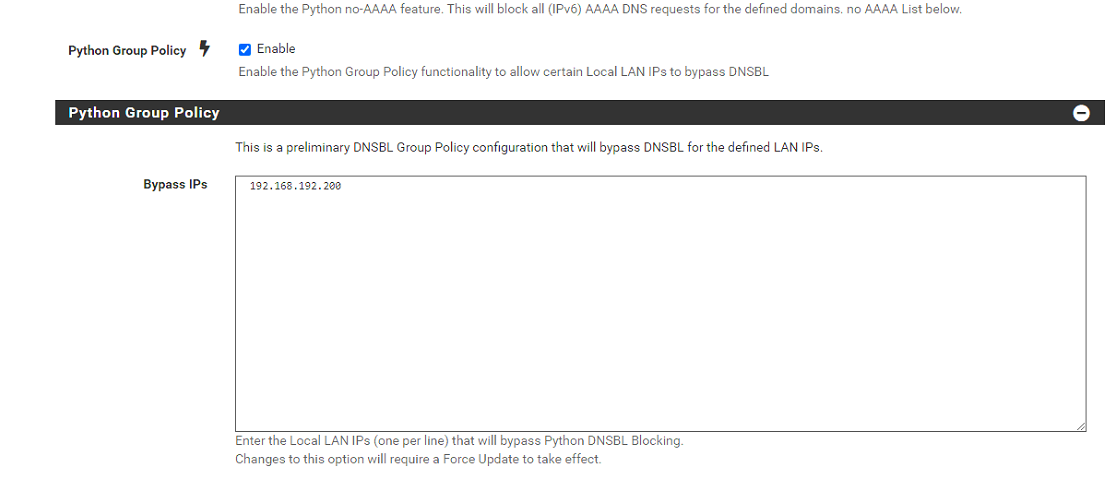
I ran the command you gave me
unbound-control -c /var/unbound/unbound.conf reloadThen ran "ipconfig /flushdns" on that client computer with x.200 IP
It didn't help. Started Chrome in Incognito to see if it was caching anything but didn't work, sites that are in the block list in DNSBL is still being blocked.I do remember something but I don't know if it's correct or not. In DNS Resolver, "Custom Options" there used to be some code there which is no longer there
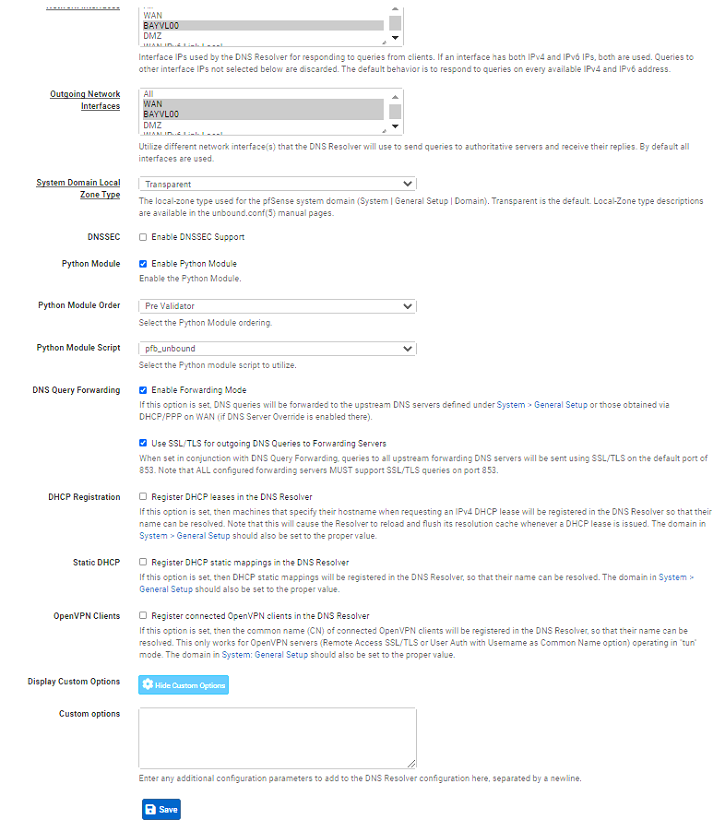
Even with the above settings applied to filter my computer, I still get 98% score in the adblock test.

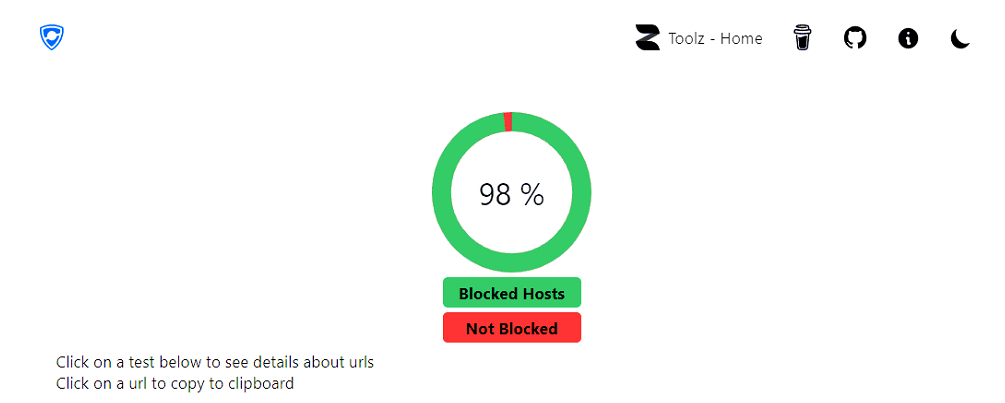
-
@aasimenator said in Bypassing DNSBL not working:
Chrome
Chrome uses what DNS ? pfSEnse ? Or 8.8.8.8 ?
Your PC uses what DNS ?
Type "ipconfig /all" to see it (them).Btw :
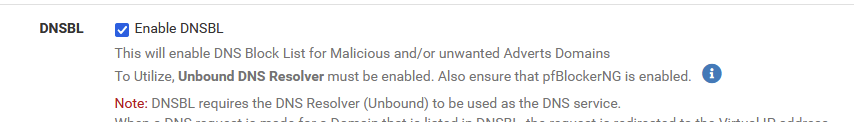
What I make of this is : Unbound should be run as a Resolver, not as a forwarder.
Your are forwarding.With an empty "Group policy box" - on my PC right now :
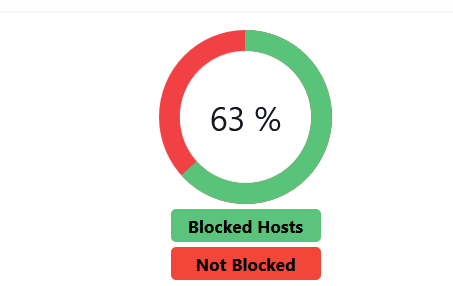
I added the IPv6 and IPv4 of my PC.
After a reload of pfBlockerNG :
( and I used another browser) :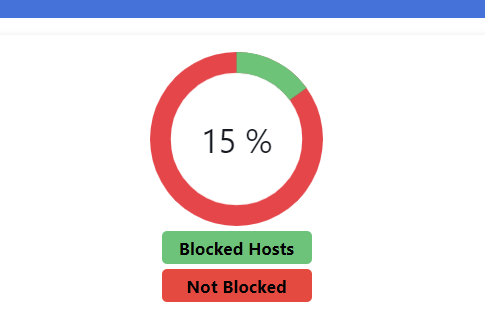
-
Chrome has not custom DNS configured.
We are in a domain environment so all PCs on the network are pointing to 2 DC's on the network.
The DCs have the IP address of the pfsense configured under it as a "Forwarders" with no other server's defined. (with Use Root Hints option unchecked)The PFSense has 1.1.1.1 & 8.8.8.8 configured as the DNS Server in General Setup. DNS Forwarder is disabled and In DNS resolver
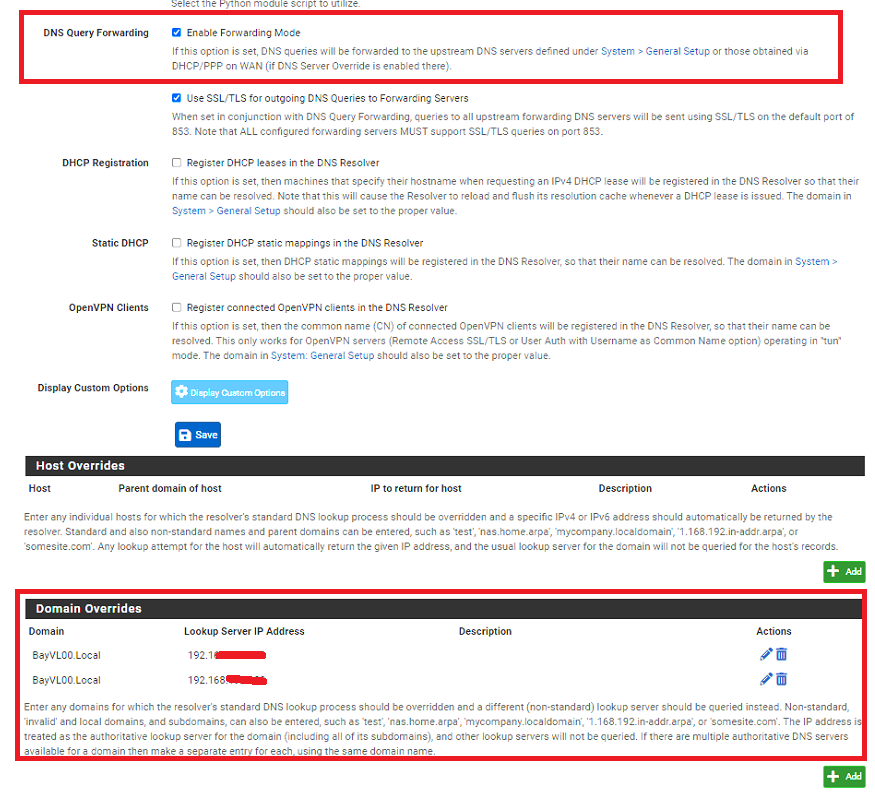
-
still no solution to this issue
-
@Gertjan
A bit of investigation revealed the following:I enabled "DNSBL Event Logging" made a bunch of requests from the whitelisted IP address of the client machine, then in pfSense logs, I went through 'DNSBL_Reply.log' file and saw that the sites I visited were sending DNS requests from the DC's on the network and not the actual client IP address. which means pfSense doesn't actually know which client is requesting.
And it makes sense because all client requests are going through the DNS servers which are the DC's.
So my only option is to set pfSense as the default DNS server instead of the Domain Controllers and set all clients to send requests to pfSense instead of the DC's, unless someone has a better alternative to this? -
A lil bit later, but I was having this same problem, and I fix it doing this:
My DNS was: Host -> Active Directory DNS -> pfSense
I changed to: Host -> pfSenseNow all hosts I put in Python Group Policy bypass DNSBL rules.
- If you have Active Directory, you need to add your local domain in DNS Resolver -> Domain Overrides to resolve internal hosts.