Help with rules on vlans
-
Hi all,
So I thought I knew how vlan rules worked, but its seems I dont.
I have 2 VLAN's - IOT & CCTV
Pfsense is installed on an unraid vm (lan net)
Blue Iris is installed on an unraid windows 10 VM with a static IP in the CCTV net VLAN
What i'm trying to achieve is block CCTV vlan from accessing everything except 3 IP's
I thought the rules below would work, but when im on the windows vm i can ping any IP address in the lan net and IOT net.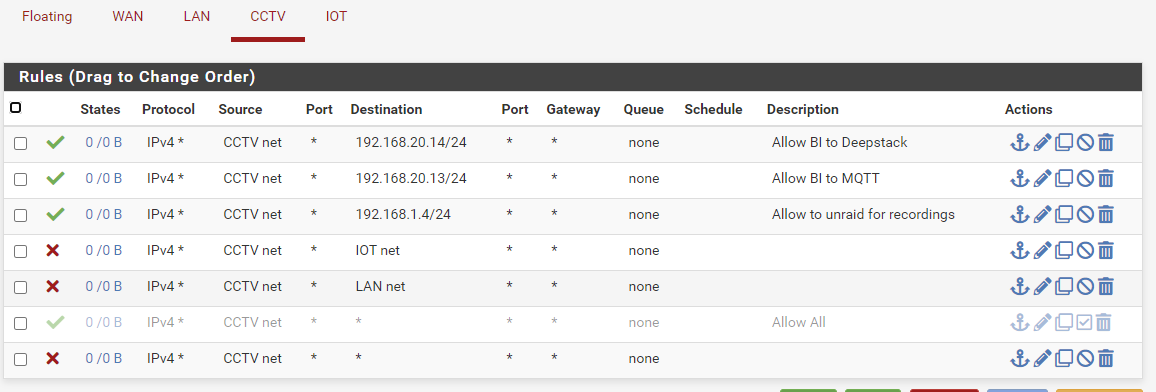
Am i on the right track with rules, or way off??
Thanks -
First off, separate this into two parts, VLANs and pfsense. A VLAN is just another interface to pfsense. Nothing special about it. Get your VLANs up, so that each device is configured appropriately. Then configure your rules for the VLAN interface as you would any other interface. The fact that they're VLANs is irrelevant to pfsense.
-
@sneakynuts Are you sure your in cctv net with this windows machine? I see no hits on any of those rules see the 0/0 on all them.
In general your rules look correct for allowing access to specific IPs other than destinations if wanting to allow access to 1 specific IP those should be /32 is single ip set as network. Since its showing the mask, means you picked network vs single host or alias, and while that is a host address 192.168.20.14/24 since .14 is not a subnet boundary - it could be seen as the whole 192.168.20/24 network which would allow anything to any IP on the 192.168.20 network.
If I set a rule for a specific host - it would look like this.
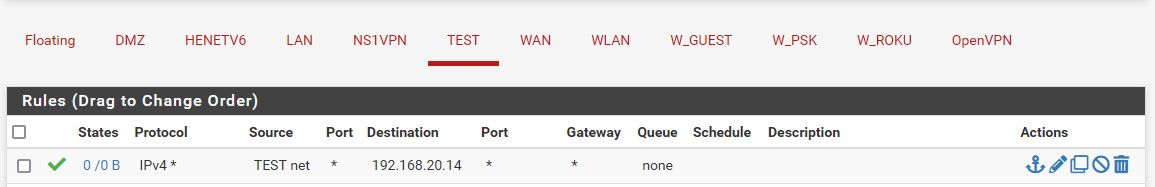
Also keep in mind that once a state is created, creating a rule to then block that traffic would still be allowed until the state goes away via close or timeout, or you kill it.
-
@jknott
Sorry, don't quite follow, when you say to separate into parts!!
As a test, I disabled the 2nd rule - To me, this should stop BlueIris from communicating with mqtt on the IOT vlan.
But it doesn't!! - It only stops, if I disable the 1st rule aswell... -
@sneakynuts see my post - you have set destination a network not single IP.. there would be no mask if single IP or if set as network and you only want to allow 1 IP, then the mask should be /32
And don't forget states might be active allowing - no matter what your rules say.
States are looked at before rule, rules allow for states to be created. If a state is created it would allow that traffic regardless if you add a block rule.
-
@johnpoz
Just saw you posted while i was writing my reply.The blue iris vm is definately on the .10 (vlan10) network

I will change the destination to single IP as u said.
Thanks
-
@johnpoz
Thanks! Changing to single IP done the trick
Am i right in assuming that unless i have an allow rule, everything else will be blocked... ie: I dont need a block all rule?? -
@sneakynuts said in Help with rules on vlans:
@johnpoz
Thanks! Changing to single IP done the trick
Am i right in assuming that unless i have an allow rule, everything else will be blocked... ie: I dont need a block all rule??Yes, there is an implicit block all rule at the end of the rules you created.
-
What I mean is recognize that having VLANs does not affect rules. You are setting up rules for multiple networks and that would be exactly the same whether on physically separate networks or VLANs.
I have noticed people will often assume the problem is more complex than it really is, simply because VLANs or VPNs are involved. It's all just a collection if IP networks and you use the rules and routing appropriately to do what you want.
-
@sneakynuts said in Help with rules on vlans:
Am i right in assuming that unless i have an allow rule, everything else will be blocked.
Default is deny yes - there is never a reason to add a block rule at the end - unless you want it to not log, or change it to reject vs block..
Default is deny on every interface - unless you allow something it is blocked.