pfSense with Server 2019 AD DS and Netgear ORBI (as AP)
-
Hello All,
My first post - please bear with me.

I am a home user, and looking to setup my home. I am looking to remove the Netgear ORBI RBR50 (with a satellite) as my router/dhcp/dns and put an HP t6220 Plus with an added 2-port NIC installed and a Server 2019 box (not a VM) to be used a an AD DS and handle the role of DHCP and DNS as well. I would like to use the pfSense as firewall and VPN - everything will go through it to my COMCAST modem. I am also hoping to start deploying IPv6.
I have a lot of of things in the house which are wifi and many wired. So the ORBI will be put into AP mode, and the Satellite is in my office which talks to the MAIN in the other end of the house. Currently everything works flawlessly. Eventually I will get CAT-6 run through the entire house and may move to a UBITQUITY system.
My questions are as such:
-
I have used to the web interface on the pfSense - and I think I have it all setup with 1 WAN interface (which I know will connect to my cable modem) and 1 of the 2 ports on the dual NIC card is set to LAN - the other is not in use at the moment. It appears that DNS is enabled on the pfSense, but I wish to have the Server 2019 (AD DS) do this, as well as DHCP. What steps do I need to do, to accomplish this? Will I need to setup some sort of pass-thru mode on the pfSense to make sure that Internet traffic makes it through/out?
-
I am setting up the AD DS server today, it is a brand new install of Server 2019 Standard and the box has 2 NICs as well (one on-board, one as PCI NIC (disabled)). Originally I was going to put VMware on the system and stand up 2 VMs (one for the AD DS and one for pfSense) - but decided to use the HP t620 instead as it has AES NI built into the CPU. This has been setup/enabled already. I am familiar with setting up the DNS and DHCP on this AD DS box, but want to make sure I do not have any conflicts with the pfSense. Currently the box is using the ORBI as the router/dns/dhcp - this will all switch once I put ORBI into AP mode. So I need to have every thing setup before this.
-
The WAN on pfSense is set to DHCP for IPv4 and DHCPv6. The LAN is set to STATIC and set to 192.168.10.254. I will make that my GATEWAY on the AD DS box when I am ready to switch over. The AD DS is set to 192.168.10.250. I am still working on the best way (learning) how to set Static IPv6 for the AD DS as right now it appears to be pulling it from the ORBI and I get this:
IPv6 address: 2601:c9:200:11b0:xxxx:xxxx:xxxx:xxxx (masking full IP)
Link-local IPv6 address: fe80::110:55e:425a:26c7%7
IPv6 DNS servers: fe80::7ad2:94ff:fe36:3dee%7
fe80::7ad2:94ff:fe36:3dee%7
IPv4 address: 192.168.10.250
IPv4 DNS servers: 192.168.10.1 <<< Static set
192.168.10.254 <<< Static setI am seeking any advice for a better way to set this up, given that I would like the Server 2019 box to do DCHP (and DHCPv6) / DNS (IPv4 & IPv6) / AD DS (with LDAP).
Thanks in advance,
Curtis -
-
Re DNS:
First make sure your M$ box can resolve on the internet ....
Ie. on M$-DNS lan make a permit TCP/UDP M$-Box to "any" , port 53.Then ...
It Depends ....
If you want pfSense to be able to resolve your M$-DNS , entries too. You would have to point pfSense to resolve via the M$ box too.I do that on my system , but use dual linux DNS servers as pfSense forwarders , M$-DNS/DHCP is not my idea of stability.
Under System --> General Setup , in the DNS section , do like this.
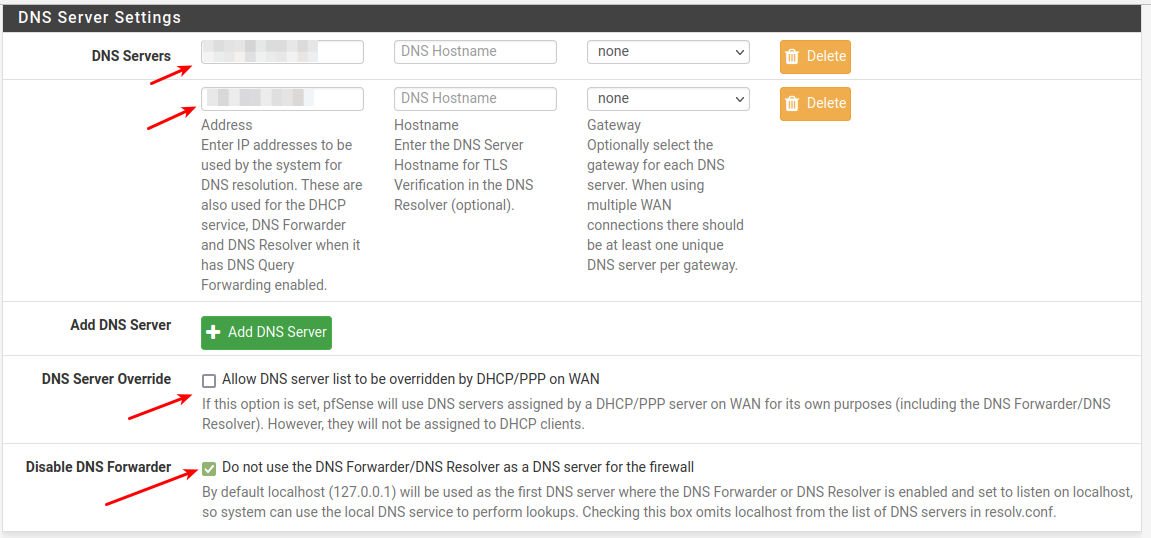
Since you just have one DNS server no to fill in two servers at the top.
Now pfSense will use your M$-DNS to resolve dns queries.How do you want your clients to resolve DNS ??
Directly to the M$-DNS or via pfSense Unbound (and then Unbound resolves at the M$-DNS) -
DHCP forwarding to M$-DHCP
In
Services --> DHCP RelayEnable the service (DHCP Server must be disabled)
Select the interfaces to "Relay DHCP from" ...
Thet would be all your interfaces you want to receive DHCP resuests from ...
Hint - Don't select WANDestination server IP addr of M$-DHCP server.
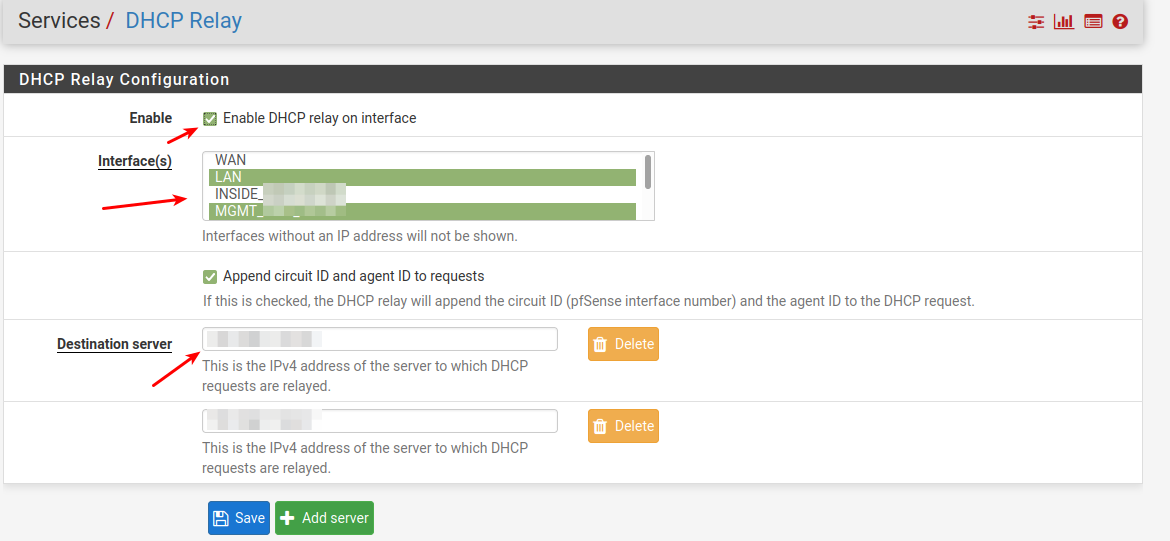
Save
Now make sure that UDP port 67/68 is allowed incomming to your pfSense "DHCP-Relay enabled" interfaces , else DHCP requets will be blocked from entering pfSense , and no relaying will happen.
Edit:
Hint2: Don't select the interface your M$-Box is connected directly on./Bingo
-
I realize that what I want to do is probably the most stable - and I am willing to go down another path. My biggest goal is to setup a home domain, and get the ORBI out as my router/dns/dhcp. So willing to take suggestions. As I realize that if the AD DS box is down - I have no DNS. Both the pfSense box and the AD DS box have their own UPS (speaking of which - does pfSense have a UPS plug-in)? It is an APC UPS.
I was looking at having the SVR_2019 do the DNS and DHCP, as DNS gets installed when you install AD DS. Should I not go this route?
I most definitely want to start enabling and using IPv6 in my home - just about everything here will support it (except my Android phone).
So far since my posting - I have promoted the server to DC role and it has rebooted and is asking for DNS setup.
Thanks again,
Curtis -
DNS Part2
Once you have decided if your DHCP Clients should ask pfSense for DNS or directly to the M$-Box
You need to either "just" include the M$-Box as DNS server in your DHCP scopes , and permit TCP/UDP "Client-lan Network" to M$-BOX IP - Port 53
Or Setup Unbound too
Enable Unbound
Select interfaces here Unbound should listen for DNS requests
Hint: Not WAN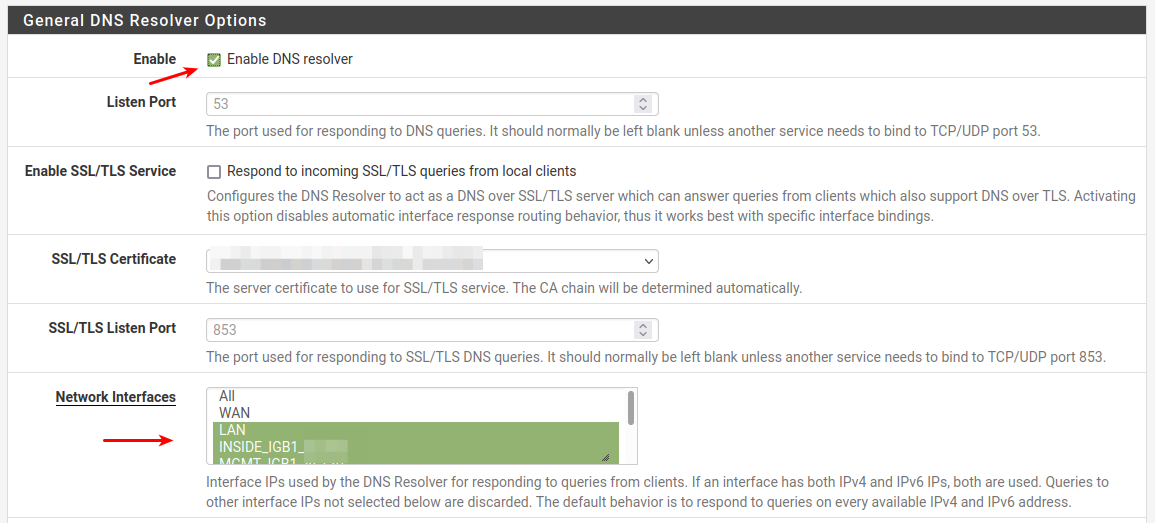
Select interfaces that Unound is allowed to use to send DNS requests via.
Seems like ALL is a good choice , due to some "quirks".Local Zone Type : Transparent
Important:
TICK Enable forwarding mode.Now unbound will use (forward to) the same server(s) setup in System --> General Setup - That was your M$-Box
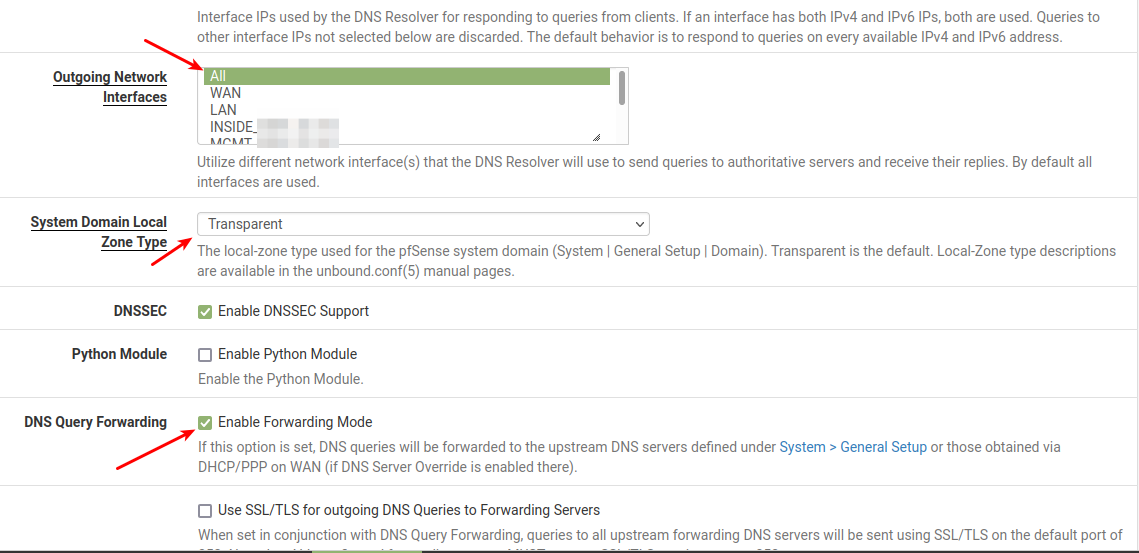
NB:
The enable DNSSEC support - Should probably NOT be ticked in your setup.Save
"On all local interfaces" , Permit DNS from network-range to the pfSense interface ip.
Now on every Active DHCP scope on your M$-Box , set the DNS server to the ip address of the pfSense interface.
Hint: Prob the same ip as you use for "scope" default-gw (router).DONE
I would suggest you get DNS working without Unbound at first.
Aka clients ask M$-Box directly.When that's stable , you can play around with Unbound.
/Bingo
-
@bearhntr said in pfSense with Server 2019 AD DS and Netgear ORBI (as AP):
I realize that what I want to do is probably the most stable - and I am willing to go down another path. My biggest goal is to setup a home domain, and get the ORBI out as my router/dns/dhcp. So willing to take suggestions.
If you would like your DHCP clients to register in DNS , and be able to use DNS to reach them.
pfSense won't do that Unbound is horribly broken in the way it registers DHCP clients in the DNS.
So for that feature you will have to use another solution , like M$-DHCP/DNS.
I like that feature and use linux for DNS/DHCP - it can also dynamically (DDNS) resolve DHCP clients. But i suggest you use M$ , or prepare for a loong read up on linux bind9 and isc-dhcp server.
If you can live without being able to DNS resolve your DHCP Clients (I won't) , pfSense have excellent DNS & DHCP servers built in.
/Bingo
-
UPDATE
I now have the DHCP being handled by the Server 2019 (setup Scope and Exclusions and Reservations that I wanted) - and all appears well. I turned off the DHCP server on the pfSense.DNS is also working on the Server 2019 box, and pfSense is set as DNS Forwarder only. Everything seems to be working. Server is set with pfSense only as the Gateway. The server seems to have no issue getting to the Internet and working through a few BPA warnings (that I hate to see in DNS) and all of them for DHCP are resolved now.
I have yet to JOIN any of my machines to the domain yet, but all of them seem to be working using the server and pfSense as my DNS and Gateway. So I am thankful for that. The ORBI is just a wireless AP now. {whew}
I still want to get IPv6 working properly - COMCAST is issuing a /128 IPv6 address to the WAN connector on the pfSense - I just gotta figure out IPv6 for the rest of the network.
Thanks again everyone for your input.
Curtis -
@bearhntr said in pfSense with Server 2019 AD DS and Netgear ORBI (as AP):
Thanks again everyone for your input.
No need to call me everyone

a few BPA warnings (that I hate to see in DNS)
What's BPA warnings ?
Did you see the "Thumbs up" below the posts ?
/Bingo
-
BPA is the Best Practices Analyzer tool which is in Server OSes since 2008.
It checks settings and that everything is on the up and up. Some of them are bogus, but a lot are not (like permissions settings for DHCP to update DNS, etc.)
I am getting some ROOT HINT errors with IPv5 addresses, as I have not completely figured out this protocol and set it up properly.
Curtis
-
OK - so far so good - until - I got here. I tried to enable the DNS resolver and I get an error that states the DCHP server is not enabled in pfSense, after I hit SAVE.
So I have DNS full (well almost) working on the MS Server - see below. DHCP appears to be working and the DHCP relay feature in pfSense appears to be working. Devices in my home are getting an address from MS Server - and even the reservations that I have set are working too.
I have given up (for the moment) using IPv6 - I think I have it working --- then reboot a device and it gets a completely different IPv6 address...even the MS Server which has an RSVP set -- frustrating. But this site did get to 17/20 working ( https://ipv6-test.com/ ). Still need to learn a little more about IPv6 I rekk'n.
So something that is gnawing at me is this point. In my DNS setup on the server. I cannot get the pfSense to resolve a name in the DNS Forwarder setup (for ipv4 -- it would under IPv6, before I turned it all off).
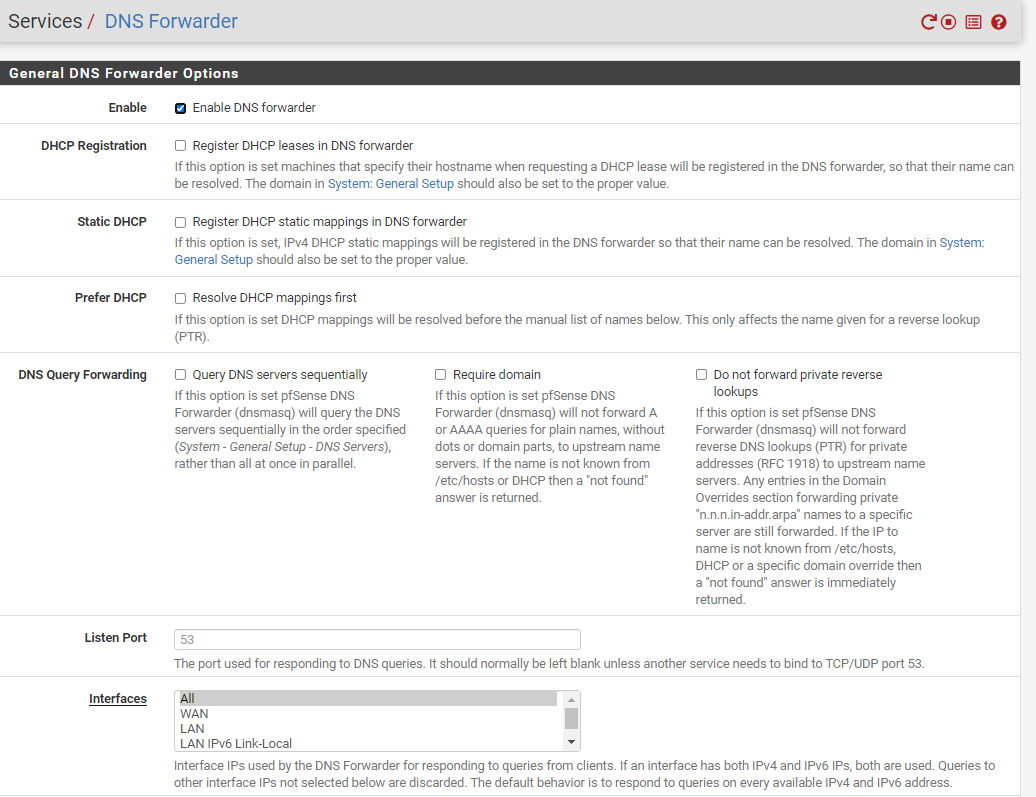
This is what my pfSense looks like.
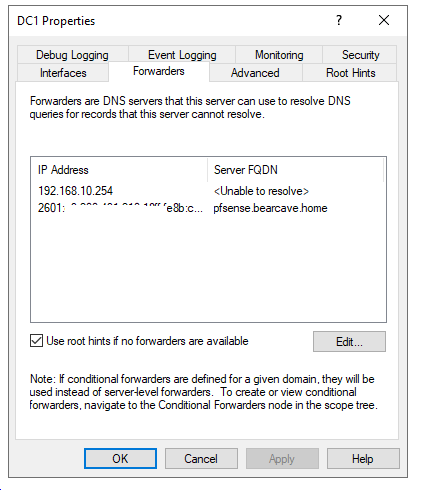
When I had IPv6 setup with what I thought was a proper format of addresses and went to the DNS Forwarder setup in Windows....I added the STATIC address of the LAN port in pfSense. The name resolved in IPv6, but never has in IPv4 - albeit I get an OF under the validation setting. Which indicates it is working.
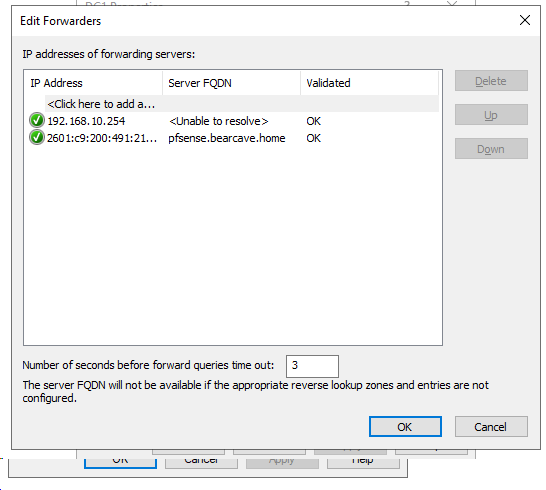
Why does it not resolve the name? I am thinking it has something to do with the fact that also cannot PING the LAN port of the pfSense from any of my networked devices.
I appreciate your help so far - and I think I am at about 90-95% there (well more like 85% since I do not have IPv6 working). If there is anything you want to see, let me know. I will get a screen shot.
Maybe once I get all this working - I write a book. LOL
Curtis
-
How did you do that cool signature? I do not see that anywhere in the profile settings area.
Curtis
-
Can you resolve external dns names
Ie. 8.8.8.8 to "google"
or "google.com" to ... whateverI had some issues with the "Unbound Resolver" , when it had to accept RFC1918 responses from my bind9̈́s - It wouldn't by default accept "private ip" responses
I had to add this to the "Customs options" in the bottom
server:
private-domain:"your-domain.ext"The forwarder is using dnsmasq , so the same options might not work.
I have never used the forwarder.Maybe @johnpoz have a hint here
/Bingo
-
I am totally confused by your response.
Resolve the 8.8.8.8 specifically where?
You got pictures of what I should look at?
Curtis
-
@bearhntr
In your Server 2019 DNS, place a static entry for your PFSense LAN IP~PFSense Hostname. Then the name should resolve from any client that is using your server for DNS. Remember, there is no need to resolve a name from an IP in the Forwarders tab of MS DNS, it doesn't mean it can't be used/isn't reachable/isn't working (shows as OK) it just means it can't find a DNS entry for it.However, you should be able to use PFSense DNS in resolver mode, not forwarder. I don't get why you are getting a DHCP error message. I'm using Server 2016 DNS/DHCP, and forward DNS to the PFSense box with DNS in resolver and it works well. If unbound craps out, my DNS servers will then fall back to using root hints, so I find it works quite well set that way.
Maybe I missed it here, but I don't think you are using any VLANS- just one internal LAN network? So the MS Server is in the same network as the desktops and the LAN IP of the PFSense? If that's the case, DHCP Relay is not needed/used. Being on a single broadcast domain, (DHCP is a broadcast) the clients can reach your server's DHCP just fine without it. I use it as I have my servers on another VLAN.
-
I meant if you could resolve those ip addresses on a "Client computer" , using the new setup
-
You are correct. One LAN network 192.168.10.xxx everything is in that network. Do not think (at this time) I need any VLANS.
I am not sure what you mean to add an entry in my Server DNS for the pfSense -- would not need to be in the DHCP? Where specifically are you referring that I add it. It is almost as if the connection fails because of ICMP (I know that I cannot ping the pfSense LAN port (IP or name).
Call me silly - but I am fanatic about seeing "unknown" - "not found" etc.. Even run the BPA over and over until all messages are gone -- except for those 2 damn ones from MS about not having more than one DNS setup -- maybe at some point I will setup another system on my old HP T610 to be a secondary DNS. LOL And the other message that the loopback must be in the DNS on the AD DS box, just not as first entry. I mean REALLY?!?!? Microsoft - that error has been around 2 decades.

If you got some pics of what you are suggesting - or want a picture of mine. At this point, I have not done anything more with the domain (joining machines to it, etc.) until I get all these 'quirks' sorted.
In the past I let the ORBI handle everything - but when the old DC died, I decided to go pfSense and DC and let the ORBI be my AP....until I eventually move to Ubiquiti UniFi system....which I have been following the forums - appears to be its own nightmare. LOL
I really want to get more abreast with IPv6 as well...as I am considering requesting my own IPv6 address from ARIN (North America).
Curtis
-
From the AD DS (DC):
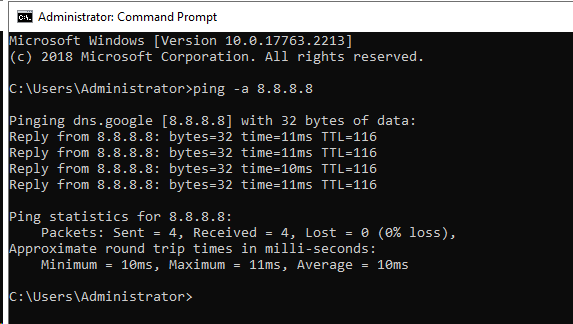
From one of my networked computers:
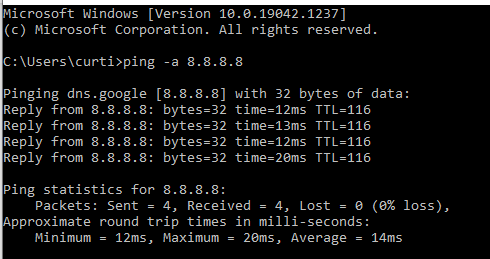
Have not ever had a problem with that once I enabled the DNS Forwarder.
Curtis
-
@bearhntr
Your Forwarders screenshot shows that 192.168.10.254 DNS server had that green checkmark, which meant that it was visible on the network, but not resolvable to a name. I understand it is set static. BUT it does not appear to have a record in MS DNS, if it did and DNS was functioning correctly, it would resolve to a name. But the more I think about it, the 192.168.10.1 is PFSense, and 192.168.10.254 is the ORBI? If that is still UP (why?) and you want that to resolve to a name, you would need to add a static DNS record for it to the Server 2019 DNS, but frankly, now that I read through this again, that's not what I would do. If you have the DNS running on your Server 2019 box, I would disable DNS and DHCP on the ORBI as soon as MS DHCP is setup and giving out my server DNS to clients. No reason to forward to the ORBI either, unless I am missing something.
How I set mine up is, all the clients point to my two Server 2016 machines- I use MS DHCP, and I set it to provide my two servers as DNS servers, as part of the lease. I then setup DNS to forward to the lan interface of my PFSense box, which I put in resolver mode (I see no reason to forward from PFSense, but you may have a reason to).
So the DHCP scope options:
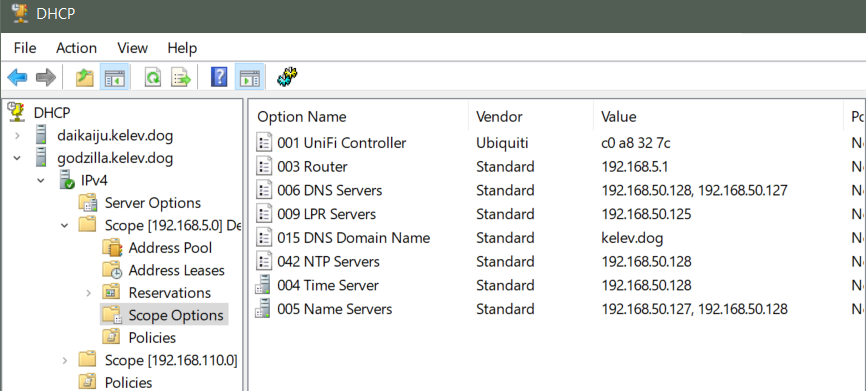
That points my stuff to my servers. I set DNS forwarding to the PFSense box:
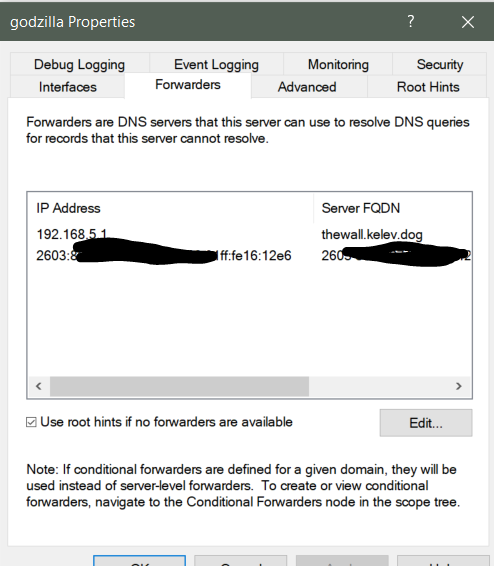
But I set it to also use root hints in case the PFSense DNS (unbound) was borked, so it will just go directly to the internet. Yes, if my servers go down (this is why I have two) I will have no internet unless I manually set the IP info on the client using PFSense as the DNS. I only have the 'standard' version of Server 2016, but that gives me two virtual licenses, so my server box is running Vmware ESXI, and I used both my virtual licenses to create two domain controllers running DNS and DHCP. -
-
I am still not clear, but maybe I am reading something wrong. Let me see if I can clarify things.
Version 2.5.2-RELEASE (amd64)
built on Fri Jul 02 15:33:00 EDT 2021
FreeBSD 12.2-STABLEpfSense WAN port is DHCP and DHCP6 and connected to Cable Modem (I get an address on both of them). The v6 address is 2001:558:xxxx:xxxx (it appears to me to be a 128 bit number but I have WAN set to a /64 prefix).
pfSense LAN port is STATIC at 192.168.10.254 and IPv6 is "Track Interface" and pointed to the WAN port. I appear to also be getting a V6 address on that one - but it is 2601:c9:xxxx:xxxx:xxxx:xxxx:xxxx:cb24 (masked - but the last 2 octets appear to be some portion of the MAC address) - whereas the one from WAN does not follow that convention.
pfSense has DNS Forwarder enabled see image - are the settings.
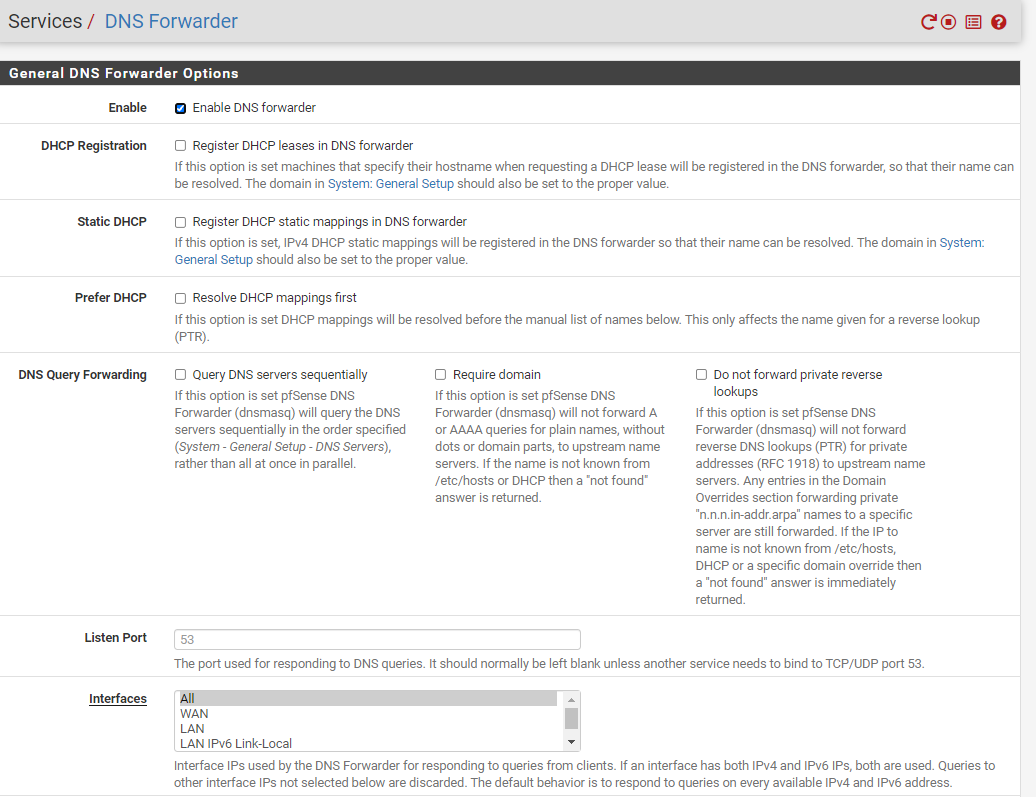
pfSense does not have DNS Resolver enabled - when I tried to enable it I got an error. See images 1 & 2.
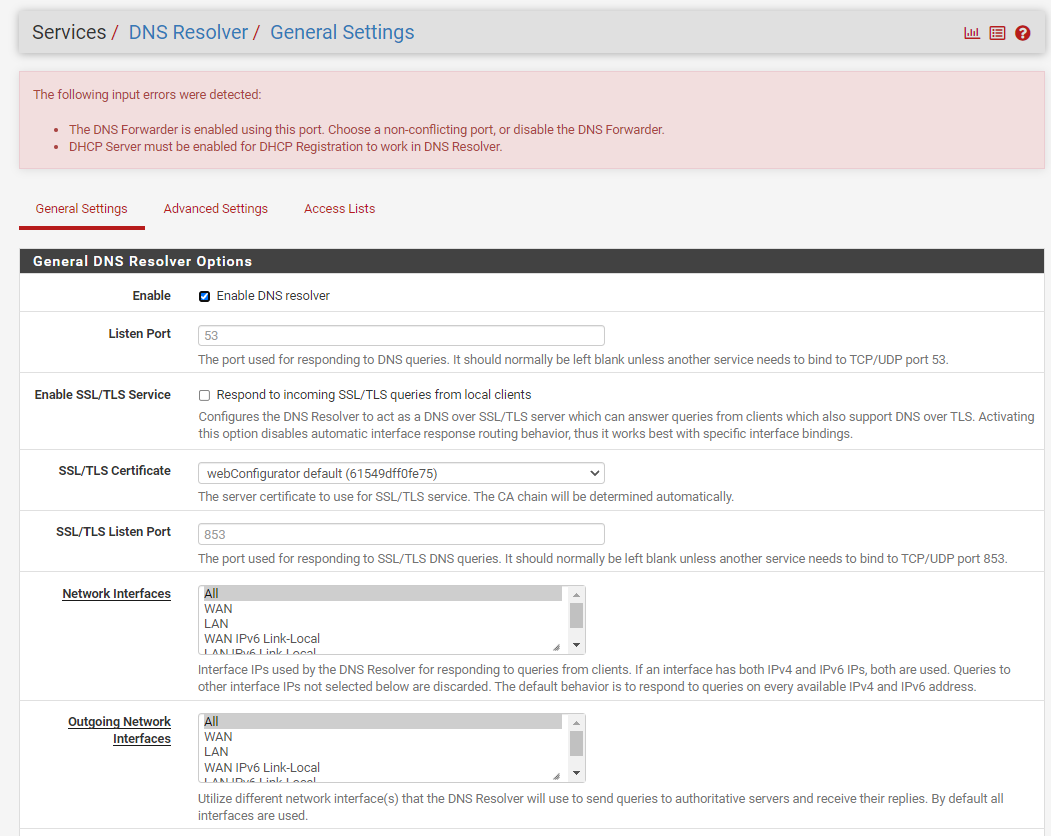
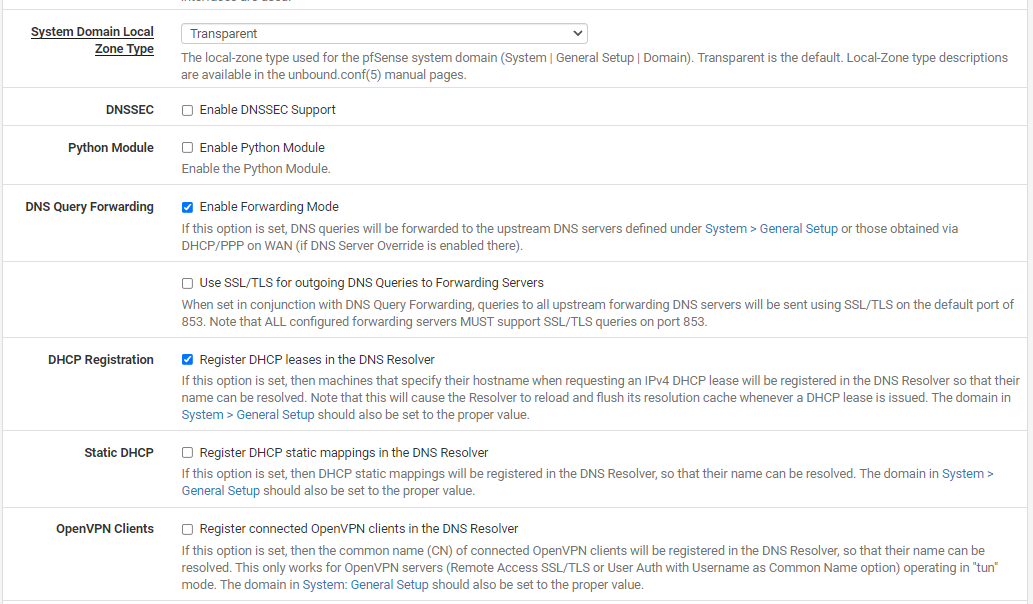
pfSense also has DHCP Relay enabled on LAN and the 192.168.10.250 programmed in - as my server is desired to handle all DHCP.
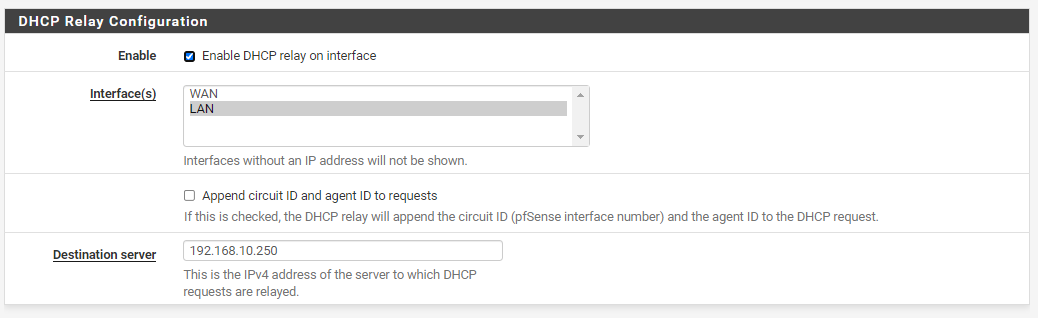
The ORBI is set to AP mode and does no DHCP or DNS at all. It has an RSVP on my Server 2019 Standard machine in the DHCP so that it is always 192.168.10.1 (and the satellite is always 192.168.10.2 - always RSVP). I have a SmartThings HUB which has an RSVP to .3 and a HomeSeer box which is .4. All of these work.
The Server has 2 NICs - but one I have disabled - as it was originally an ESXI box with Server and pfSense both on it. Decided to stand up a separate pfSense box. So ESXi went bye-bye for just Server 2019. It has a Static address of 192.168.10.250 (using 255.255.255.0) and the Gateway is the pfSense LAN (192.168.10.254). DENS entry 1 (is 192.168.10.250) nothing in #2 (it did have 127.0.0.1) - but made no difference in the error I was getting in DNS Best Practice Analyzer. So took it out.
So as it is now. Server is handing out address to anything on my network (1 day lease at the moment). The only device that seems to change addresses is my Samsung S10+ - as it changes its MAC address. My NAS has a Static IP address on it now. As trying to get it to allow AD DS logins would not work with it set to DHCP with an RSVP. (still fighting with that one). LOL
DNS appear to be working, and everything seems to have no issues getting to the Internet. Root Hints seem to resolve also with no problems.
The only issue I seem to have is the FORWARDERS tab in the DNS will not resolve the address of pfSense LAN - but gives me the Green check. Here are some screen shots of the DNS settings. What I guess I do not understand is making an entry in DNS for the pfSense LAN address/name.
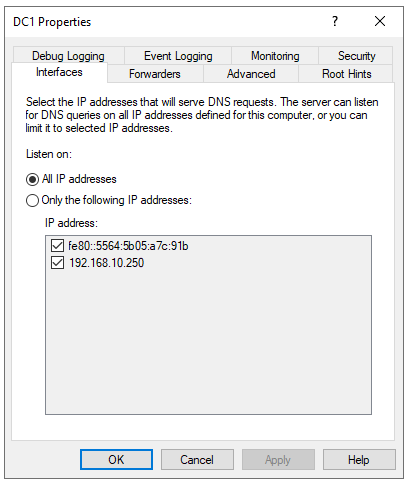
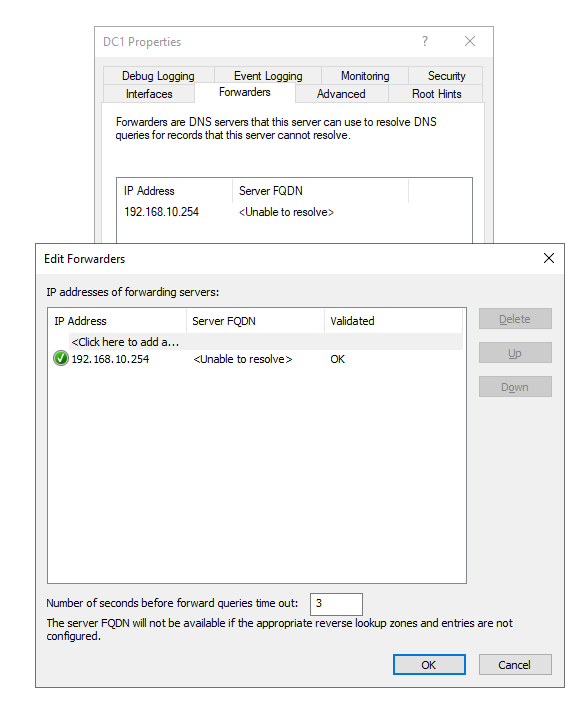
I also have a DHCP RSVP for the Server 2019 box in DHCP - just to make sure that its v4 address is always there. There was an issue when I was playing with the v6 stuff - where it switched the IPv4 back to DHCP and not static. Had to hook up a monitor and KB to find out what address it got - so that I could RDP back into it. (that was fun - NOT)
I truly appreciate the help - as I am sure I will get into a bind when I start messing with v6 again.
Curtis