Home network config with VLANs for Guest, IOT, and shared printer
-
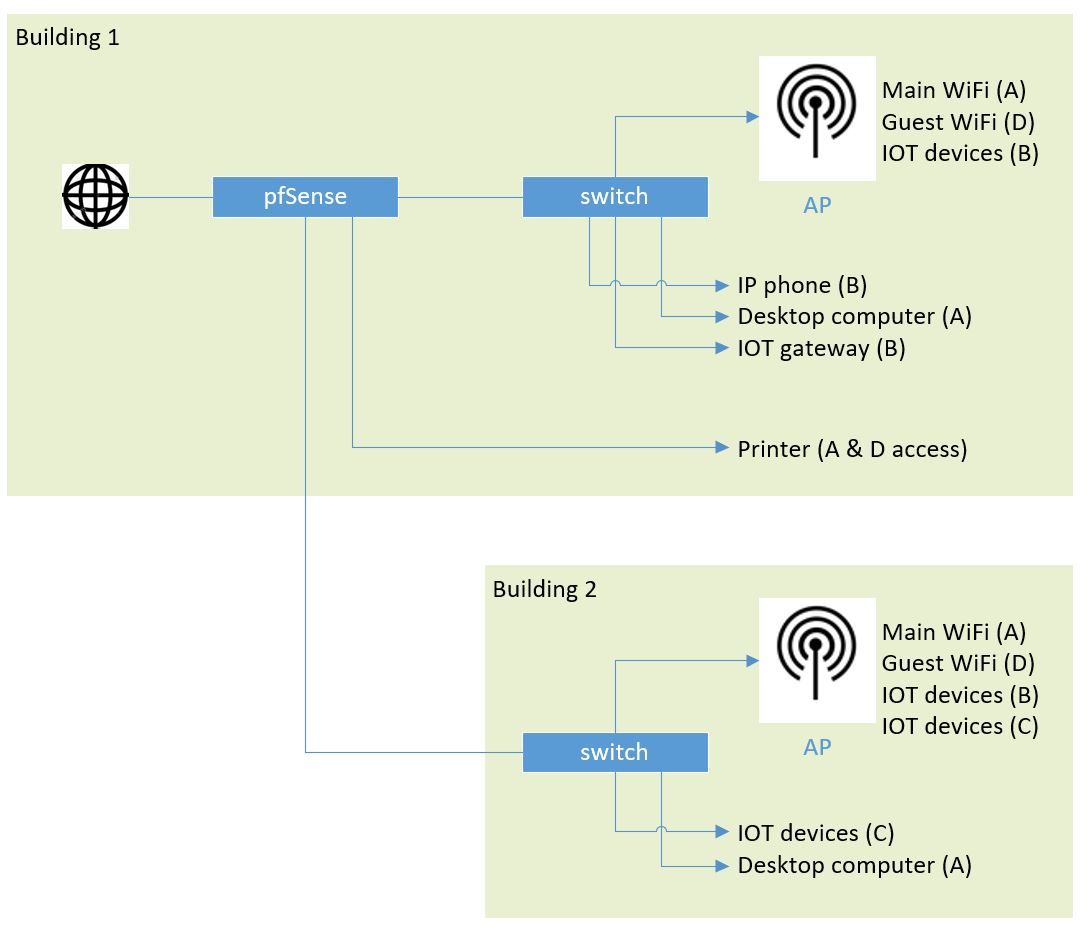
My current topology is two buildings with dd-wrt routers in each (AP mode in Building 2), with several wired and wireless devices. I cannot achieve the device isolation I want (and there are stability and broken bridging features related to Broadcom routers). I'm throwing it all out. What I want to build…
A - The Main LAN has wired and wireless in both buildings. Full access to the internet, other devices on main, and to the printer.
B - IOT-Ext - Some devices only need internet access and no access to the main network - streaming devices, some smart switches, thermostats
C - IOT-Int - Some devices must be available on the main lan (accessed by other computers) but do not need internet access - locally controlled smart switches, local IP cameras
D - Guest access will only be via WiFi, and only needs access to the internet and to the printerpfSense will be the DHCP server. Some devices on groups A, B, and C will have DHCP IP address reservations so as to provide fixed network names and IP addresses to these devices.
I'm thinking that I need to set up
1) The Default VLAN is the Main LAN
2) A VLAN for Guest WiFi (D)
3) A VLAN for IOT-Ext (B)
4) A VLAN for the printer, bridged from Main (A) and Guest (D)Questions
• For the APs, do I configure the main SSID and Virtual AP SSIDs for Guest, IOT-Ext and IOT-Int devices, and on the APs map the VAPs SSIDs to VLAN IDs?
• In this network topology do I run one DHCP range on the pfSense device since the isolation is handled by VLAN assignments, or do I need to set up subnets and DHCP for each VLAN?
• How do I set up access to the printer from both the Main and Guest VLANs, while keeping them isolated? Do I configure the routing between VLANs on the pfSense device?
• Is it correct that the pfSense router will be able to ping all devices on the network?
• I've been looking at Ubiquiti APs (eg, Ubiquiti Unifi Ap-AC Long Range) and TPLink switches (eg, TL-SG108E). Suggestions on key features to look for or avoid? As needed, I would have a PoE injector between the switch and AP, rather than a PoE capable switch. Once configured, I do not want to have any support/management software running all the time on the network. -
@cjnazz I would stay away from tplink switches to be honest - they have a bad track record. Current models might be fine. But previous they had an issue where you could not remove vlan 1 from any port.. So they were not actually isolating your vlans.. Tread with caution - there are many other switches in the same price point area that have not demonstrated a complete an utter lack of understanding of how vlans are suppose to work ;)
I have used unifi AP for many years - I have had no issues with them, and setting up vlans to ssid is very simple. I have multiple vlans running on mine (have 3 AP in the house). And use poe injectors.
No real need to setup "routing" out of the box really any router (pfsense included) will auto know how to talk to networks its directly attached to. What you allow or don't allow between your networks/vlans is simple firewall rules.
You would setup different IP ranges for your different vlans, if you want to run dhcp on pfsense for these different networks then yes you would need to set that up on pfsense.
Pfsense should be able to ping anything in a network its attached to yes - unless some firewall on the device your wanting to ping blocked that.
I am not sure how easy or even possible to setup vlans on the unifi APs without the controller. They do have like a phone app you can run to set them up. But not sure if supports setting up vlans. But once they are setup the controller software does not need to be running 24/7.. But you might find it useful in the sense it provides info into your wifi devices - what band and speeds they are connected to, which AP, etc. I run my controller on a vm on my nas..
As to your printer question - access to the printer from other vlans would be a simple firewall rule to allow that.. Discovery might be problematic, airprint for example does not work across vlans. You would want to setup say avahi to allow for discovery if that is something you want to allow and need. But anything that can just put in either the fqdn or IP for the printer would be able to print as long as you allow the printing protocol/port your using via firewall rules.