Which rule is this? Default deny rule IPv4 (1000000103)
-
This post is deleted! -
@crak said in Which rule is this? Default deny rule IPv4 (1000000103):
the traffic is getting blocked using Default deny rule IPv4 (1000000103).
If you had rules to allow traffic that was matching - then that rule would not be triggered.. So if you have placed a rule to allow traffic, but its being blocked by the default deny then your allow rule is not triggering for some reason.
Could you post up your rules so we could see..
-
I know this topic is old, but I get exactly the same message. I'm try to solve an intermittent DNS issue, (I think) and the troubleshooting step suggesting looking for blocked connections and examining the associated rules.
I get this as the deny:
Nov 11 04:02:07 LAN Default deny rule IPv4 (1000000103) 192.168.1.71:53998 216.239.32.223:443 TCP:PA Nov 11 04:02:07 LAN Default deny rule IPv4 (1000000103) 192.168.1.71:53998 216.239.32.223:443 TCP:RA Nov 11 04:22:29 LAN Default deny rule IPv4 (1000000103) 192.168.1.71:47738 142.250.81.234:443 TCP:RA Nov 11 04:22:29 LAN Default deny rule IPv4 (1000000103) 192.168.1.71:40272 216.239.36.223:443 TCP:RAcontinues, and from a small number of other IPs in my internal network. Why would it deny these? I don't see them in the rules at all (see below):
.....
WAN Rules:
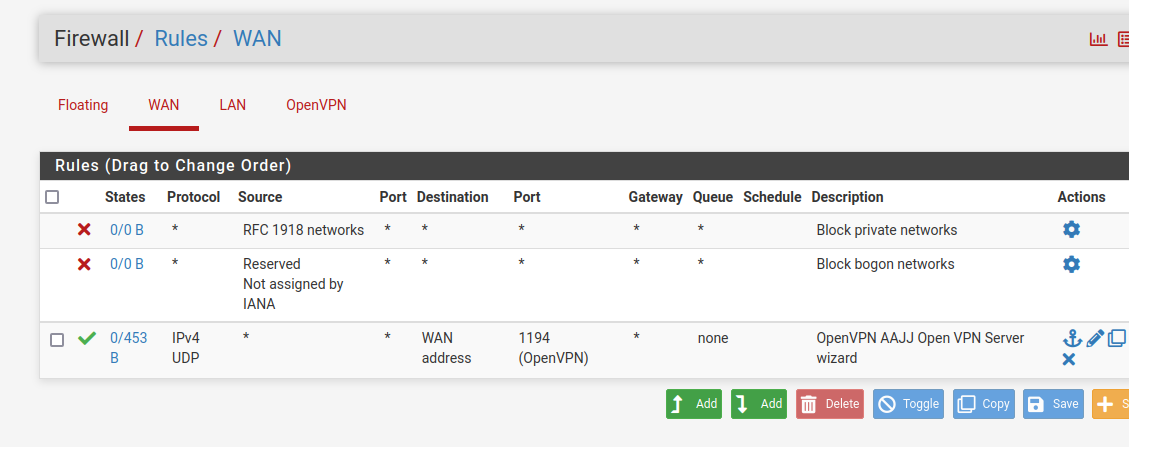
.......
LAN Rules:
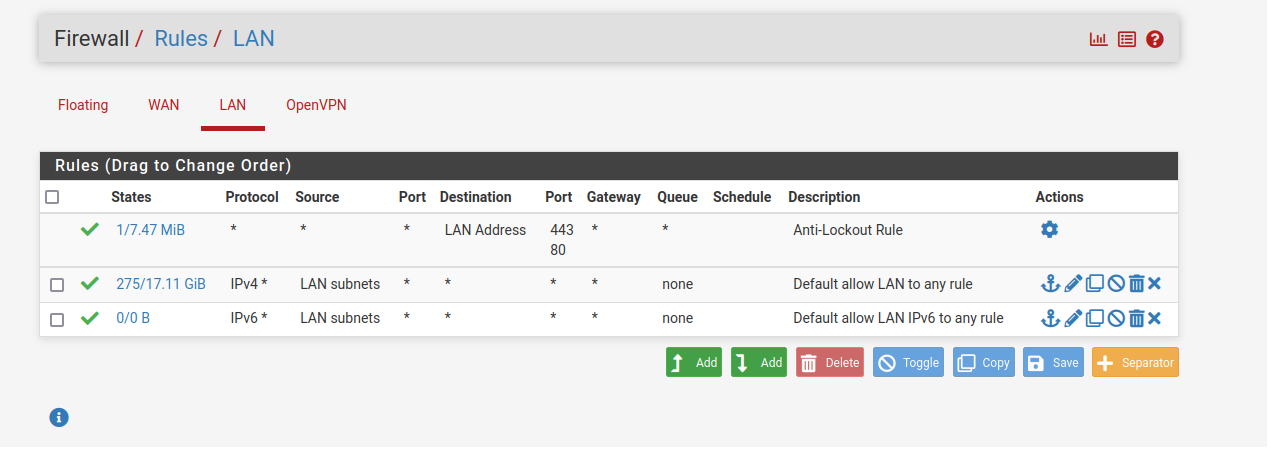
......
Floating Rules:
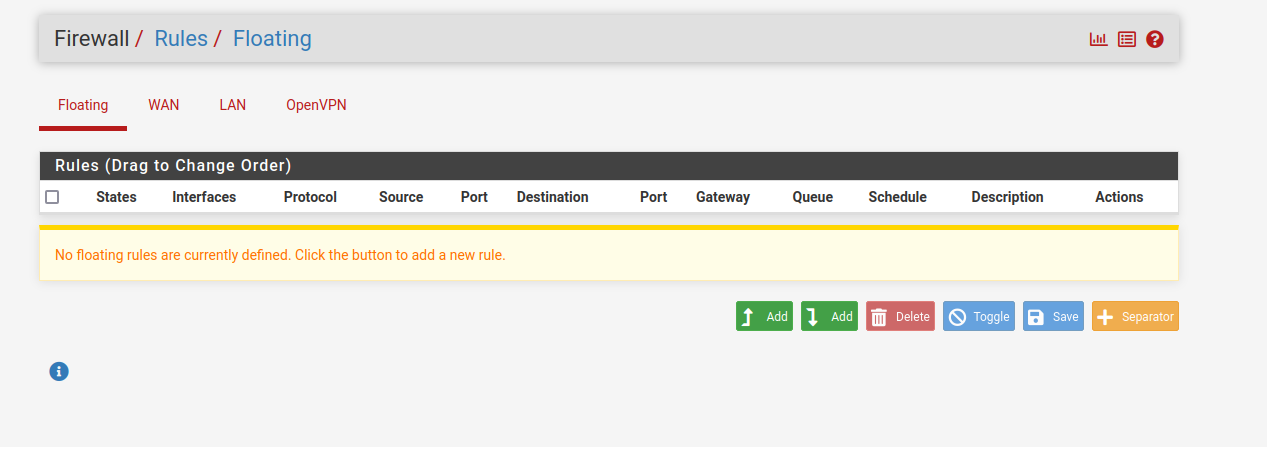
.....
OpenVPN Rules:
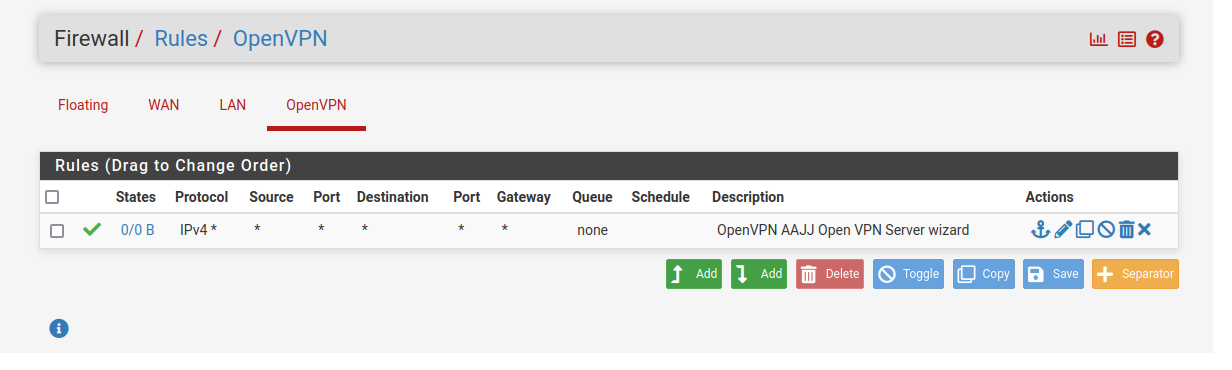
-
@jacobrale said in Which rule is this? Default deny rule IPv4 (1000000103):
Why would it deny these?
Those are out of state, the PA is a psh,ack and the RAs are reset,ack - ie close this session.
If you see SYN (S) that is the firewall saying hey I have no rules to allow this, when you see other like A, or PA, FA or RA, etc.. those are firewall saying hey I don't have a state to allow this. Ie out of state block.
-
@johnpoz THANKS!
What does "out of state" mean? And how can you tell?) How does that relate to them being deny on the way out of my network?
-
@jacobrale like I said SYN is what opens a state, if there is no state and no firewall rules to allow it then it would blocked. If you allow it and your seeing those points to the state was closed, and the client if wants to talk would have to reopen with a syn. They can closed because the session timed out and the client is trying to reuse an old session, or the state was closed either on purpose on the firewall with a kill state, or maybe set to reset states on loss of gateway, or possible the firewall already saw the fin and fin,acks to close the state already and these are late packets or retrans, etc.
Could be the client sent a fin, and firewall closed the state so the client didn't see the fin,ack so it sent a RST..
If you see a block that is anything but SYN then its a given there is no state in the firewall. It's not uncommon to see these now and then for a bunch of varied reasons.. The ones to worry about more would be SA (syn,ack) this points to something wrong with asymmetrical routing quite often.
Not sure why 443 would be dns related? Do you have clients using doh? Those IPs seem to be google owned, but not sure why a client would be sending doh to those specific IPs? The IPs you should see if you were sending doh queries to google would be IPv4: 8.8.8.8 and 8.8.4.4..
-
@jacobrale See if this helps:
IOW it may be nothing.
-
@SteveITS exactly.. Notice the RAs to those 3 IPs.. Its possible their was fin that closed the state but the client didn't get them for whatever reason, so it sent an RA (reset)..
@jacobrale I wouldn't worry about them too much to be honest.. Unless your log is just being flooded with them, then you might have something going on that you should look into. Those don't have anything to do with some dns related problem your having - again if your client was doing doh to google dns, it wouldn't be going to those IPs - so those for sure are not related to any sort of dns problem you might be having.
I personally don't even log default deny.. I log specific rules. And for noise coming into my wan, I only log syn blocks and common udp ports.. The rest of the noise I just have no desire to fill my logs with.
If something wasn't working and thought it might be helpful to see the default deny logs, can always click and they are now logged. But day to day its not really of interest to me to see a bunch of noise filling up my logs be it local side interfaces or the wan.