Is it wise to disable logging of default block rule?
-
Sometimes I want to troubleshot firewall issues, so I go to logs and check if the communication is blocked or not - I expect everything which is not allowed to be blocked by default, this is how the firewalls works.
I also have "Log firewall default blocks" checked, because this is default behavior.
But nowadays I start to thinking is it good to keep it as it is, because when I try to find some useful info in the logs I'm unable to do it, why? Two things appear in my mind - some logging issue in the webUI or the firewall log is flooded with block events which comes from outside (WAN interface), so the log get overwritten very quickly.
- Is there a way to activate logging of default blocking rule per interface?
- What will happen if I disable logging default blocking rule - do softwares like SNORT/Surricatta relies on this information?
- Can I simply create deny all rule on every interface and selectively enable/disable login on it?
What do you think?
Thanks -
@kpucko said in Is it wise to disable logging of default block rule?:
But nowadays I start to thinking is it good to keep it as it is, because when I try to find some useful info in the logs I'm unable to do it, why? Two things appear in my mind - some logging issue in the webUI or the firewall log is flooded with block events which comes from outside (WAN interface), so the log get overwritten very quickly.
I add this : IMHO, you understood the advantage and disadvantage of this option.
Normally, it should be 'off', except, when add or change your own firewall rules, the this option permits to debug and test your new rules rules.@kpucko said in Is it wise to disable logging of default block rule?:
Is there a way to activate logging of default blocking rule per interface?
Sure.
Instead of making use of the default hidden 'block all and everything' rule, make your own for each interface, and put it on the bottom of the GUI-list f firewall rules.Btw : It's time you get to know these hidden rules : see /tmp/rules.debug : these are the rules fed into 'pf', the pfSense firewall. You will find your GUI rules, and many other things.
Among them are the default hidden 'block all and everything' rule for every known interface.@kpucko said in Is it wise to disable logging of default block rule?:
do softwares like SNORT/Surricatta relies on this information?
Hummm, I'm not sure.
These apps hook themselves up into the interface, and will receive traffic even before it is parsed through the firewall (rule set).@kpucko said in Is it wise to disable logging of default block rule?:
Can I simply create deny all rule on every interface and selectively enable/disable login on it?
As said above : yes.
-
@kpucko said in Is it wise to disable logging of default block rule?:
Sometimes I want to troubleshot firewall issues, so I go to logs and check if the communication is blocked or not - I expect everything which is not allowed to be blocked by default, this is how the firewalls works.
- What will happen if I disable logging default blocking rule - do softwares like SNORT/Surricatta relies on this information?
What do you think?
ThanksNeither IDS/IPS package uses anything from firewall logs, nor do they depend on any user-created firewall rules. The packages are completely indepedent of the user-created firewall rules. This is because the packages intercept packets as they leave the physical NIC driver BEFORE the packets get to the kernel networking stack (and thus the
pffirewall).Here are two diagrams that illustrate the inbound network packet flow for the two blocking modes offered by each IDS/IPS package.
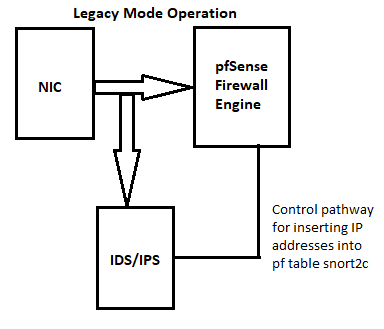
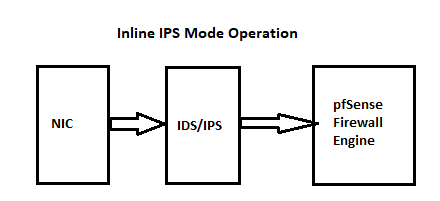
-
Clarified. Thanks for the detailed explanation guys.
Nice evening