Can’t get guest WiFi VLAN to serve up IPs
-
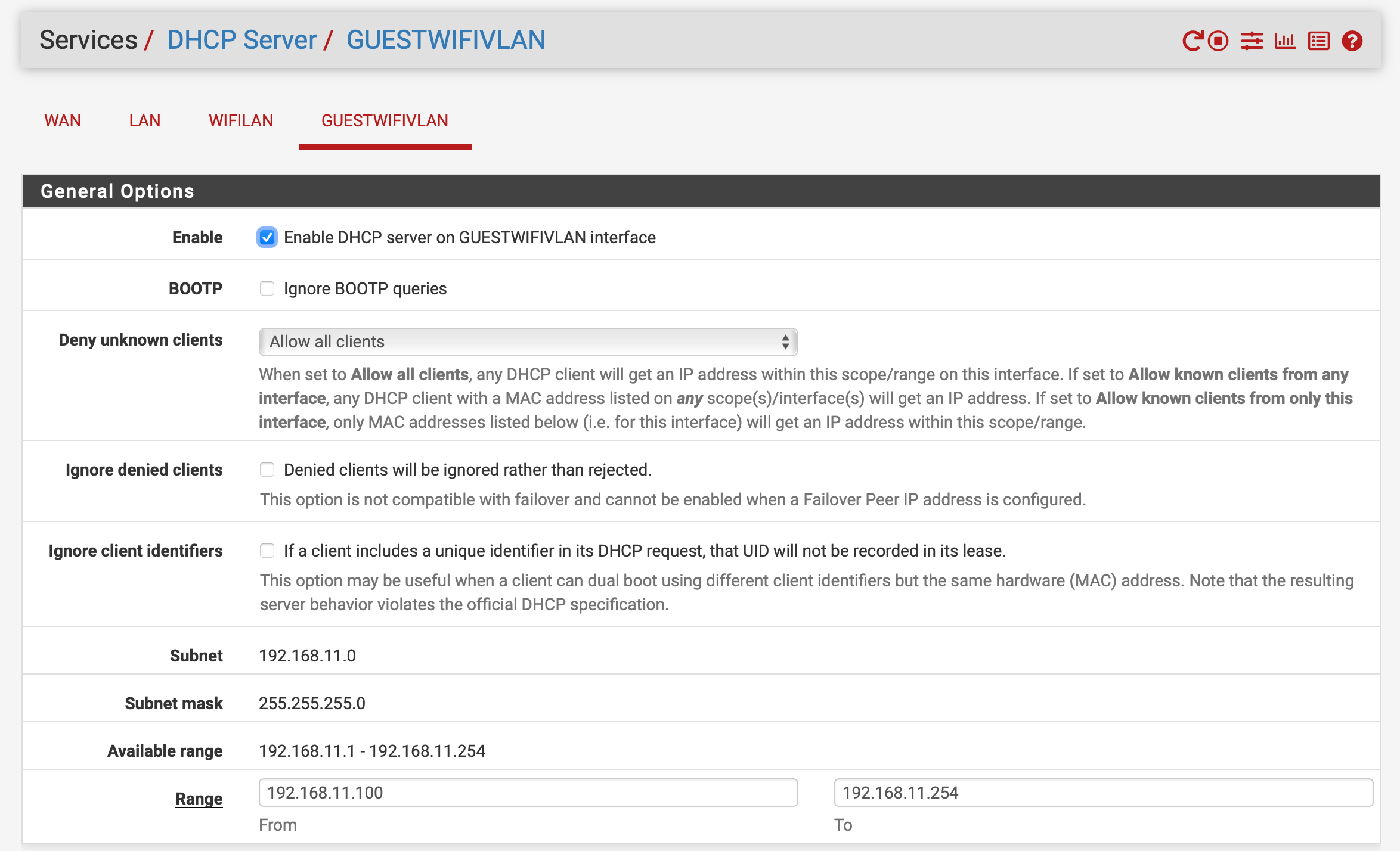
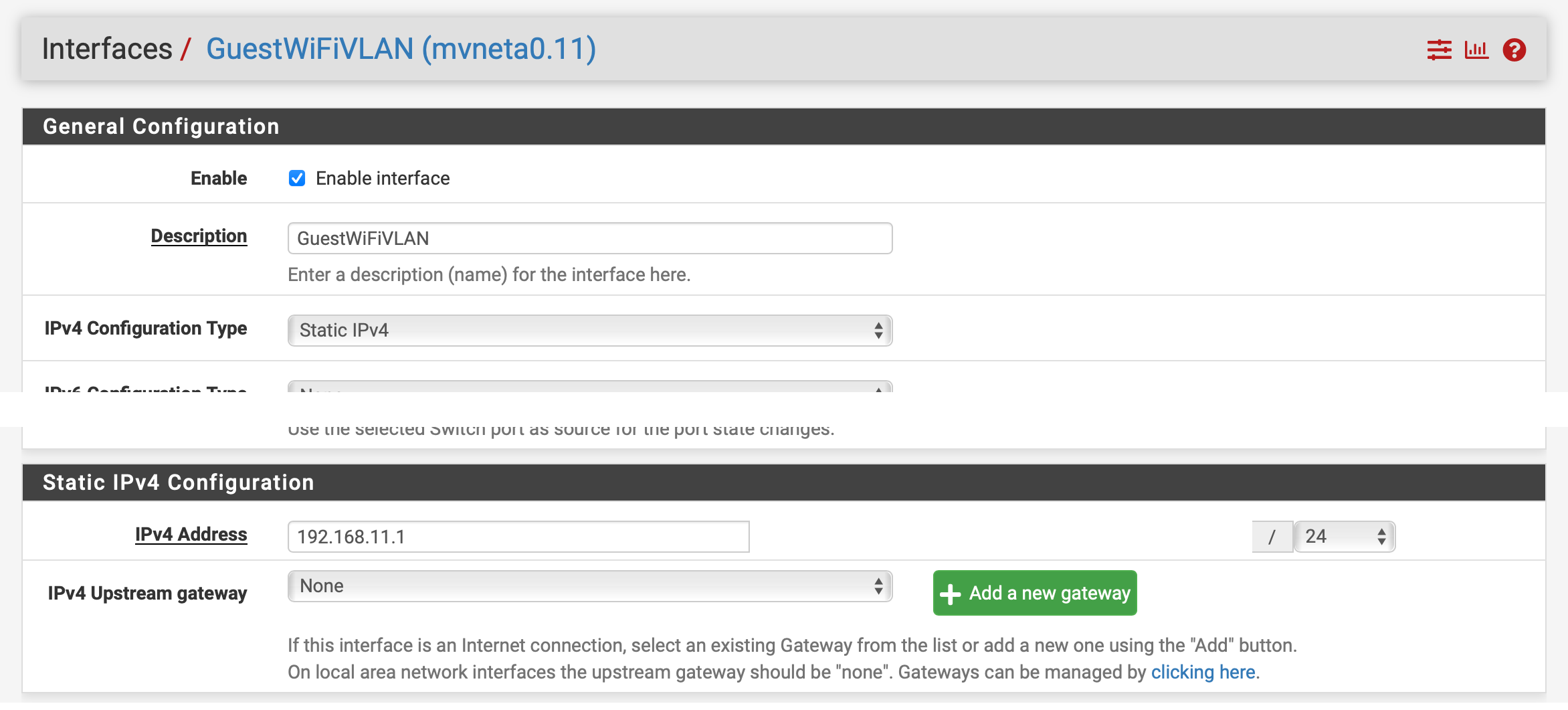
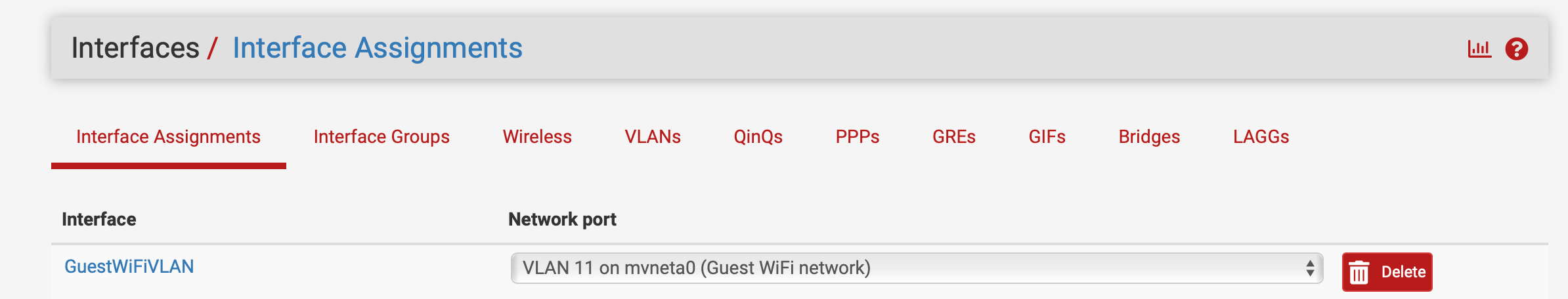
I have set up a VLAN intended to be used by guests who connect to a secondary SSID guest network.
When I connect to the guest SSID, my host does not receive an IP address from the DHCP server, and I don’t understand, why.
I have taken these configuration steps:
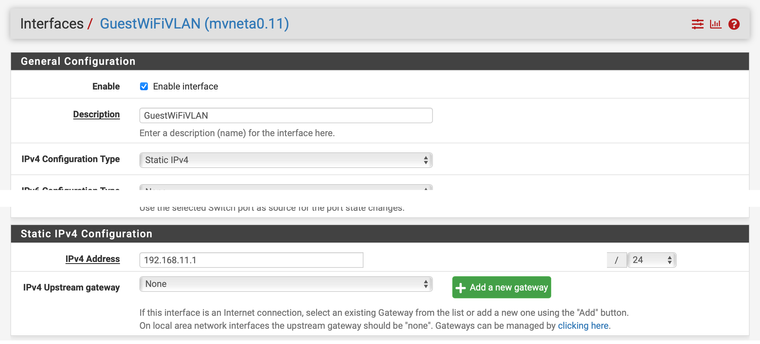
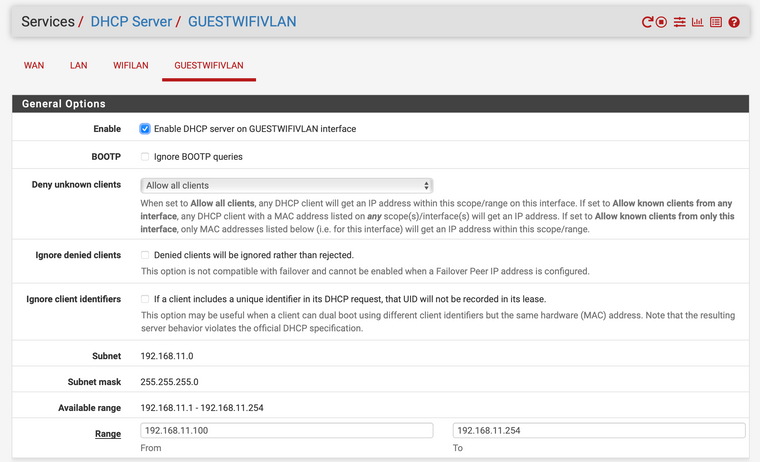
… and on my EnGenius EWS357A:
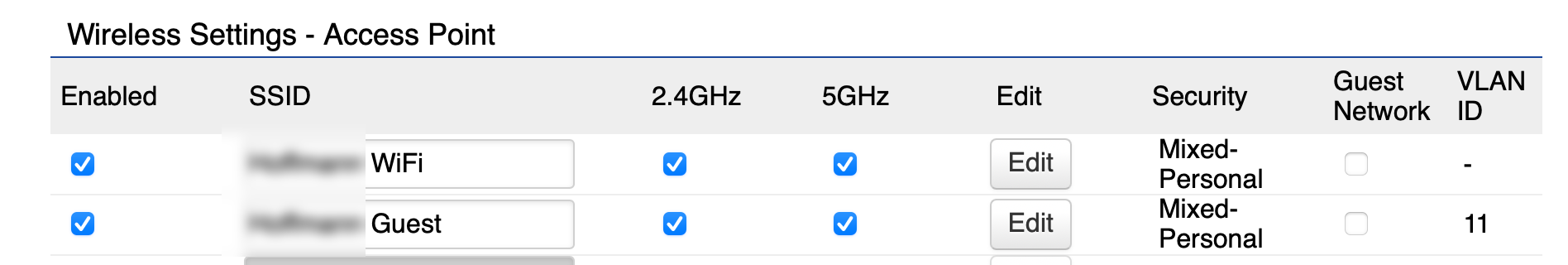
I am missing something. I just don’t know what. Any help would be very much appreciated.
-
@dominikhoffmann Does it work when you connect a pc directly to a port that is untagged in VLAN 11?
Do you see DHCP requests when doing a packet capture on VLAN 11?
-
@nogbadthebad: Every time I see the suggestion to do a packet capture, I get the hives. I’ll see what I can do, when I get home.
In the meantime, I was able to change the subnet mask of the POE switch’s IP address to include the VLAN 11 subnet. The POE switch is a managed switch which powers the APs. Wired hosts on that physical subnet, which is plugged into the pfSense’s OPT port, get their addresses from a DHCP server serving up 192.168.4.x addresses. The switch has an address on that subnet.
The VLAN is supposed to receive addresses in the 192.168.11.x. I therefore shortened the subnet mask of the switch to 255.255.240.0 with the thought that it would possibly that way let traffic on the 192.168.11.x subnet pass. Again, I will try that first, when I get home.
-
@dominikhoffmann said in Can’t get guest WiFi VLAN to serve up IPs:
Every time I see the suggestion to do a packet capture, I get the hives.
Why its as simple as diagnostic menu - packet capture. And put in some stuff, like what interface, what you looking to capture, etc..
-
@nogbadthebad: The packet capture on the interface GuestWiFiVLAN was completely empty.
-
@dominikhoffmann well dhcpd can not offer up an address if it never sees the discover or the request.. So you need to figure out why dhcp (pfsense) is never seeing the traffic.
-
Getting closer to setting it up properly.
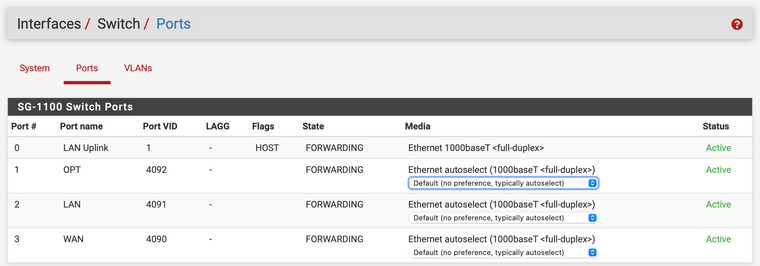
From that I learned that the switch internal to the Netgate 1100 (formerly SG-1100) has a trunk Port 0, and OPT, where my access points are connected, is Port 1.
Therefore, on the VLAN tab:
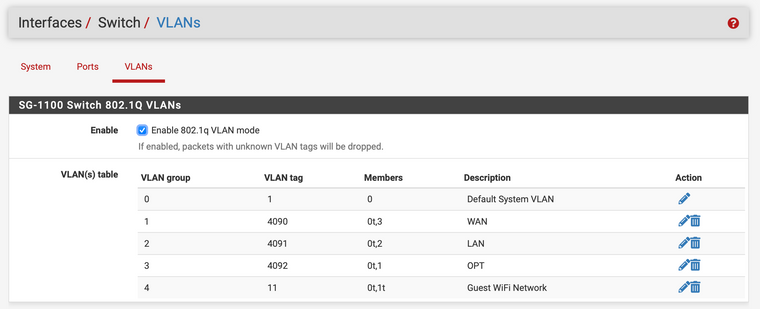
I had to add the VLAN Tag 11. I had to add “0” and “1” as members and make sure that they are tagged. The way I understand this is that this routes packets with Tag 11 to both Port 0 and Port 1.
Then I had to do something equivalent on my Netgate switch.
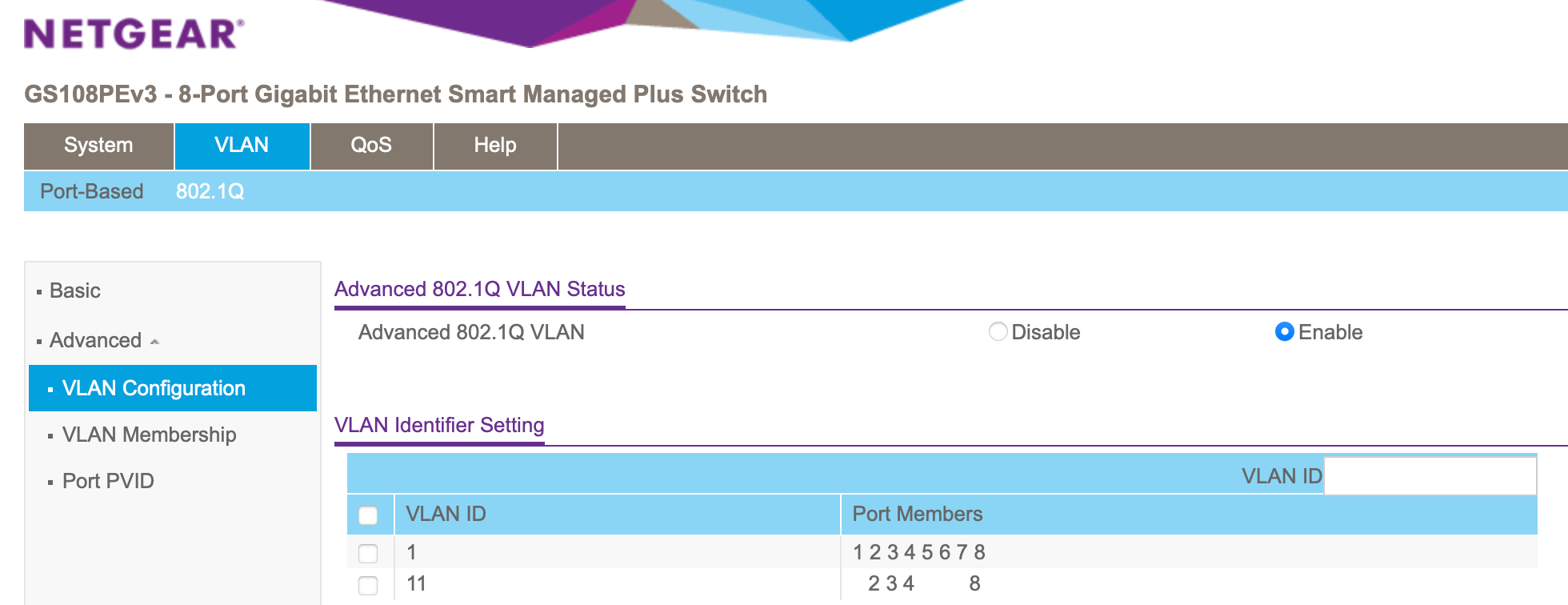
Tag 1 is the default for untagged traffic. I had to add a Tag 11 and then add the trunk port (Port 8) and the ports with my access points (Port 2–4) as members of the VLAN 11 tag.
Now, when I have my computer hop on the guest network, it gets a 192.168.11.x address. Yippee!
I still don’t have connectivity to the Internet through the guest network, though, but I suspect that is a question of configuring the firewall.
-
So, it was indeed the firewall rules. I followed the example given by @DERELICT in the thread Guest Network Firewall Rules, and I am now a happy camper.
-
@dominikhoffmann Have no idea what you did or think you did - but firewall rules have ZERO to do with seeing anything via sniff..
Yes you would need firewall rules to allow access to the internet, etc. - but not needed for dhcp to work, etc.
-
@johnpoz: I agree with you completely, and that’s exactly what I encountered. Once I had worked out the tagging on the various SG-1100 and switch ports, DHCP was working. It then required a better set of firewall rules to get out to the internet.