VLAN - Did I do it right here in PFS? (not sure how to do it on Linksys VLAN switch).
-
pfsense+ on Netgate 1100 SG
Assigned interface: VLAN 20 - name: WiFi
Added VLAN to port 0(Lan Uplink) and port 2(LAN), both tagged.
Interfaces/WiFi: Enabled Interface - STatic Ipv4 - Ipv4 Address: 192.168.20.1
Services/DHCP Server / WiFi: Enabled DHCP - Allow All - Range(192.168.20.10 to .99).
Firewall / Rules / WiFi: Added Pass - IPv4 - Protocol=Any - source/Dest: Any/Any rule.
Anything wrong or missing here?For informational purposes:
Linksys LGS308 8-port managed VLAN switch connected to pfsense(LAN port) from port 1 on switch.
ASUS AC66U Router in AP mode connected to switch port 5
Everything works fine. WiFi clients get internet and other wired connections on switch has internet too.But creating VLAN 20 on LGS308 and add it to port 5 doesn't work as far as having my router add DHCP leases in the 192.168.20.10-99- range.
My technical skills and knowledge on VLAN, tagged/untagged, PVID or not PVID, aso.. are very limited. Don't know if the port need to be member of default VLAN1 too, or just VLAN20..Why create VLAN? For learning experience, and for being able to seperate all WiFi clients from other. Maybe add more VLAN later.
I will appreciate any help, tips and tricks :) thank you.
-
VLANs are often used with WiFi APs to provide multiple SSIDs, such as for a guest WiFi. Every device that the VLAN passes through must be configured for the same VLAN. So, if you're using VLAN 20, then pfsense, your managed switch and AP must all be configured for VLAN 20. The switch only has to have VLAN 20 enabled on the ports connecting to pfsense and the AP. You will also have to configure a DHCP server on the VLAN and configure appropriate rules.
-
@JKnott Thank you for your help :)
Additional question to my post: Since my current WAP is not able to understand VLAN, do I have any other way of seperating the wifi clients, lets say with another subnet configured in pfsense, that I can tell the WAP to use instead? Or any other way?
Besides buying a new VLAN-ready AP ofcourse ;-) -
FreshTomato can do VLAN.
-
No, there is no way to separate without VLANs.
-
@rafterx Your port on the switch should look something like GE2, GE1 is my router to switch interlink :-
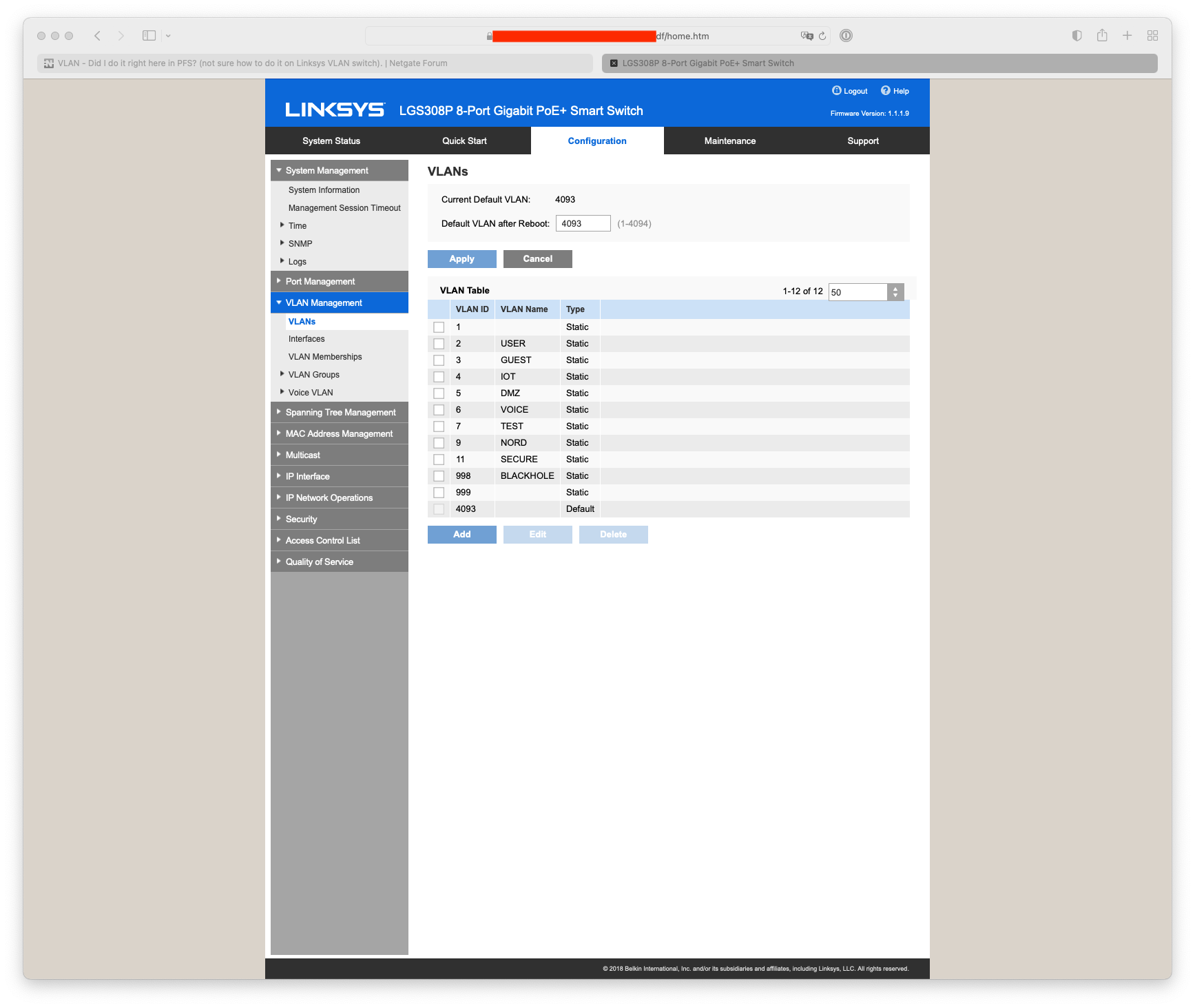
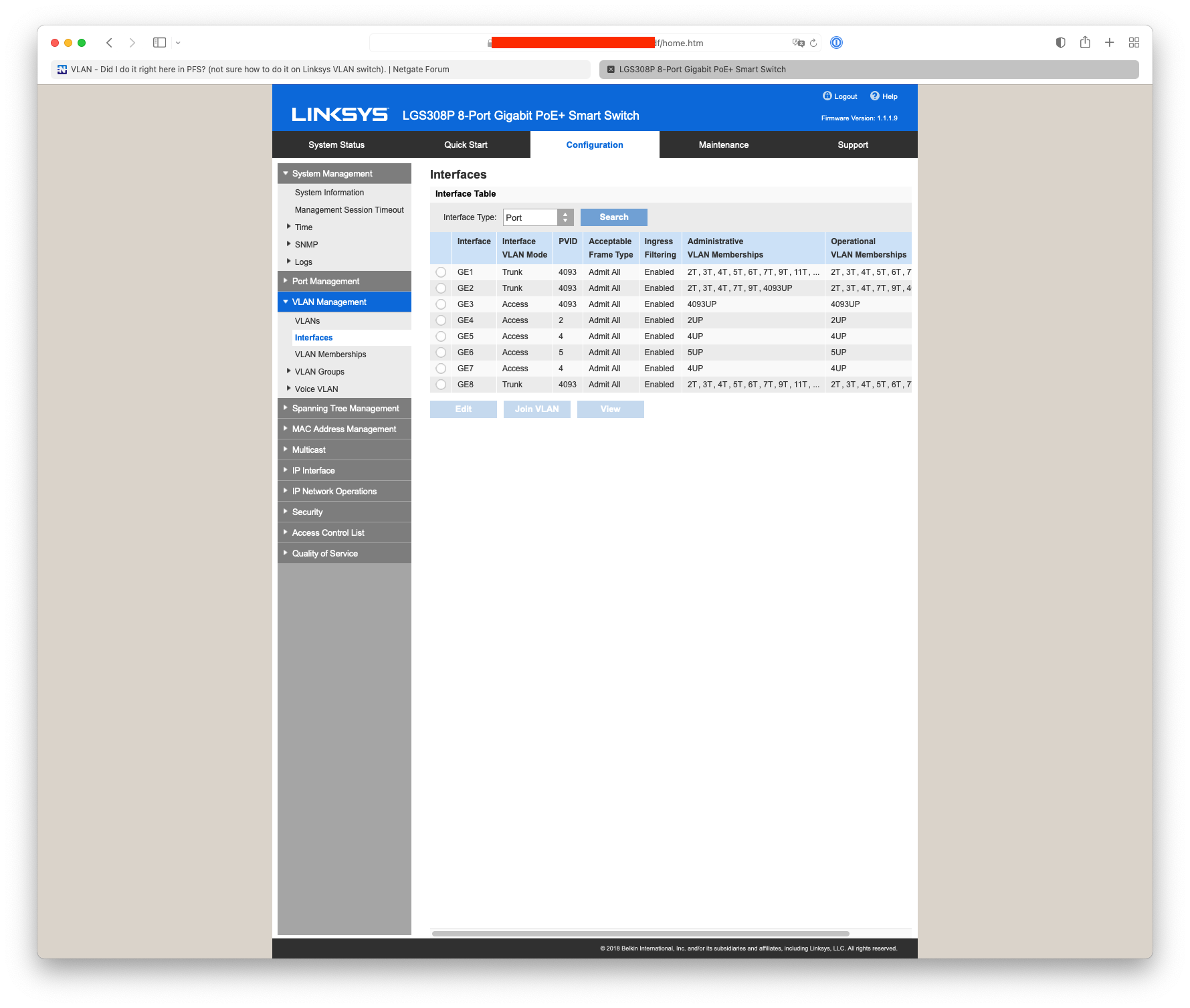
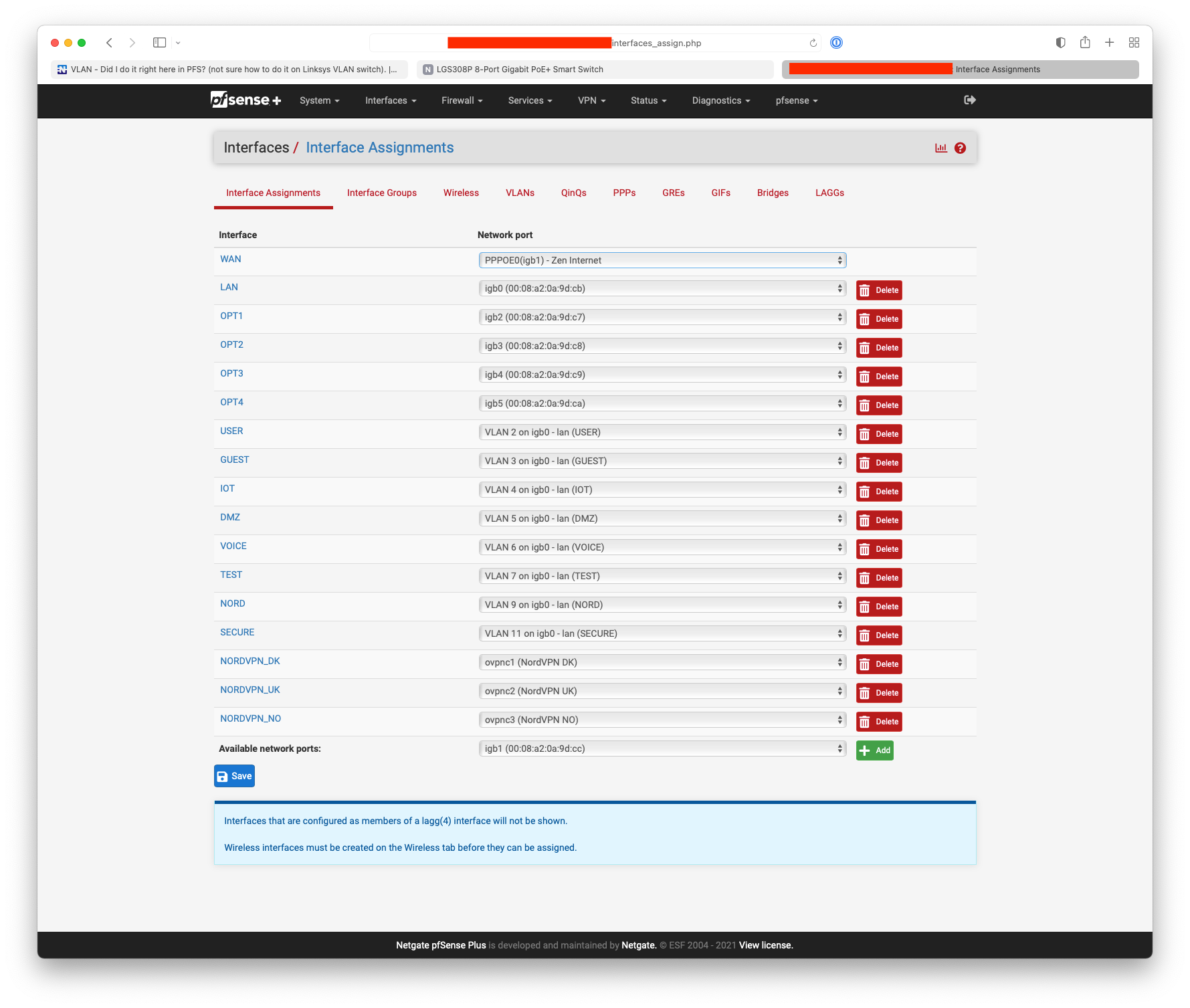
The only difference would be that I have my management network for my Aruba AP22 & switches on the untagged vlan 4903.