Single public IP subnet on WAN
-
Hello,
I found that pfSense needs to support the feature I need.
It is described: Single public IP subnet on WANAs shown in this picture https://docs.netgate.com/pfsense/en/latest/_images/diagrams-multiple-public-ips-singleblock.png
Maybe someone has instructions on how to really implement this? Because I fail.
I have 3 network interfaces (WAN, LAN, OPT1). I create Bridge "Bridges_FW" I assign WAN and OPT1 to it. OPT1 is connected to a switch with a separate VLAN.
I even tried to allow all firewall -> rules traffic from anywhere to everywhere on WAN, OPT1 and Bridge_FW.
I even tried temporarily setting Firewall -> NAT-> Outbound to "Disable Outbound NAT"
But traffic from OPT1 only reaches the WAN address and nowhere higher than the WAN on the external network. It is also not possible to access addresses connected to OPT1 from the external network. -
@winlin said in Single public IP subnet on WAN:
Single public IP subnet on WAN
Single public IP subnet on WAN I create Bridge "Bridges_FW" I assign WAN and OPT1 to it. OPT1 is connected to a switch with a separate VLAN.Not clear what you try to achieve with this setup.
Do you want to have the public IP in the VLAN on OPT1?
Maybe you can explain and give some details. -
@viragomann My situation is very well reflected in the official image already mentioned above https://docs.netgate.com/pfsense/en/latest/_images/diagrams-multiple-public-ips-singleblock.png. The difference in my case between the ISP router and my pfSense is the additional ISP switch. If necessary, I will be able to draw my own chart specifically.
I need NAT on the LAN port where the internal IP addresses are issued by pfSense DHCP. And on a network connected to OPT1 (separate switch VLAN), I would have external static IPs that are in the same range as the WAN address (mask 255.255.255.128 and are given to me by the ISP). I want to use pfSense FW to restrict traffic from the public Internet to these static IPs on OPT1 connected devices.
-
@winlin said in Single public IP subnet on WAN:
And on a network connected to OPT1 (separate switch VLAN), I would have external static IPs that are in the same range as the WAN address (mask 255.255.255.128 and are given to me by the ISP).
So why did you write "Single public IP subnet on WAN" into the topic?
You have an ISP router, however, you have public IPs behind it? So I'm wondering what's the reason for the local router.
Since you have bridged WAN and OPT1 you need to configure each OPT1 device with the proper IP, mask and the WAN gateway for proper routing.
-
@viragomann
So why did you write "Single public IP subnet on WAN" into the topic?
Because I found it so named in the official description at https://docs.netgate.com/pfsense/en/latest/firewall/additional-ip-addresses.htmlYou have an ISP router, however, you have public IPs behind it? So I'm wondering what's the reason for the local router.
We do not control the ISP router. He is to the ISP. We additionally use pfSense NAT for workplaces PC because external addresses are only enough for server services. To avoid the need to purchase additional firewall equipment for the servers, we want to use the existing pfSense server.Since you have bridged WAN and OPT1 you need to configure each OPT1 device with the proper IP, mask and the WAN gateway for proper routing.
Yes I know that. I put the external IP, mask and GW address given by the ISP for the device behind OPT1. -
For clarity I attach the diagram. It shows how it is now and how I want it to be redesigned.
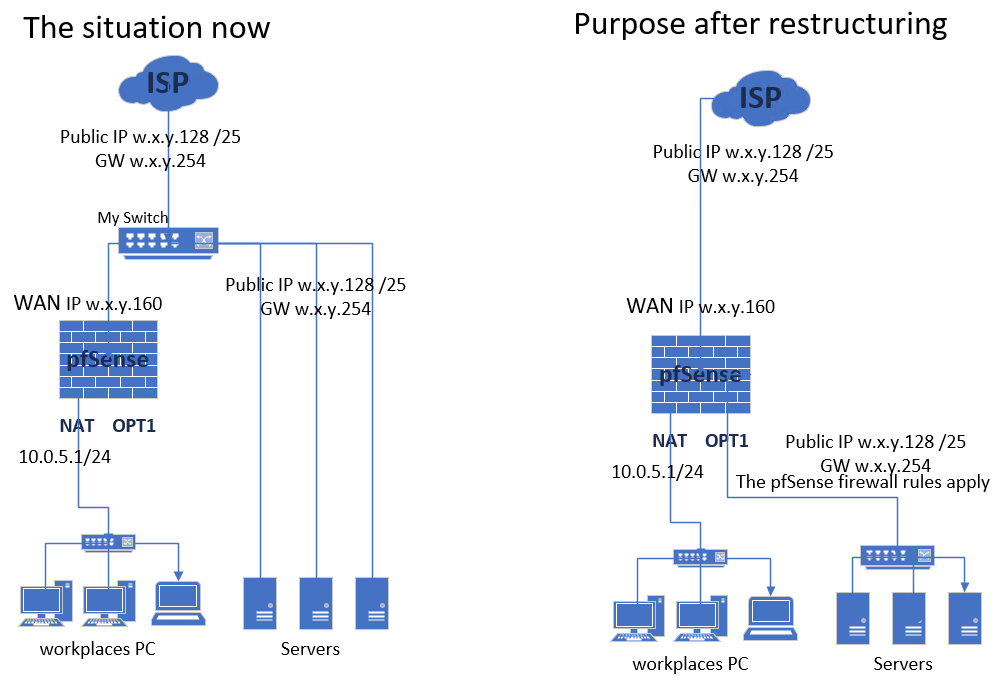
-
@winlin
Really no idea what you could have done wrong here. The set up is quiet simple.Let me recap how I'd do it (apart from basically would try it with NAT instead bridge):
Adding OPT1 interface, open the settings and enable it. No IP and gateway.
Create a bridge Bridges_FW and add WAN and OPT1 to it.
Go to Interfaces > Assignments, add Bridges_FW, open and enble, no IP and gateway.For testing :
Connect a computer direct to OPT1, give it an IP out of the /25 WAN subnet, set the correct mask and the WAN gateway. Set a public DNS server.
Add a firewall rule on OPT1 allowing anything going out.You should get connection to the internet from the OPT1 device.
-
@viragomann I tried this before writing here. Now I repeated it again, hoping maybe I was wrong. Unfortunately, the servers behind OPT1 do not even see the ISP GW (ping is not responsible).
Status -> System Logs -> Firewall does not show blocked IPv4 traffic.As recommended I tried to delete the Bridge, and put an internal IP (make NAT) on OPT1. When I place the appropriate internal IPs on the servers after OPT1, everything works. So it confirms that the physical ports and network equipment are really connected and working well.
-
-
@steveits I was thinking 1:1 NAT, but unfortunately not all services make it appropriate. There are services that answer the "client" what its IP is and which ports it opens dynamically. In the case of 1:1 NAT, the client would receive an incorrect access IP. And some other problems. Therefore, I would not use 1:1 NAT.
Is anybody who has successfully working this configuration? I am currently using pfSense version 2.5.2.
I think there really has to be someone who uses pfSense and only use FW but not use NAT. I myself know one who nadoja pfSense as FW, but it has Multiple IP subnets from the ISP and they are routed through its WAN IP. So its configuration is not right for me.
-