OpenVPN Client route traffic from LAN to openvpn Server Network
-
I have been unable to setup the pfsense router in this scenario and would really appreciate some pointers.
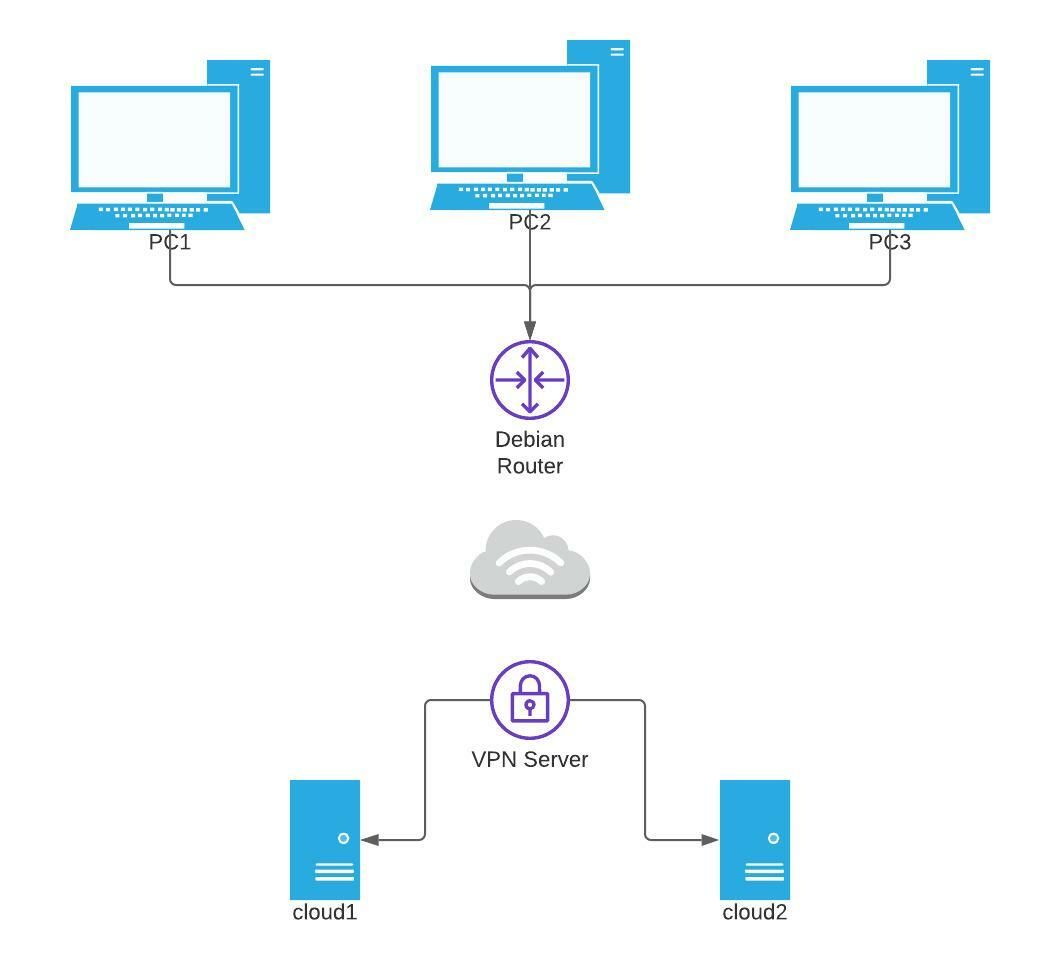
- openVPN server setup on a Debian machine. Behind the openVPN server, several machines on network range 10.8.44.0/24. openVPN network on 10.8.40.0/24 range.
- pfsense router setup on remote locations. these routers connect properly to the openVPN network. They have been set up as clients.
- from pfsense routers, connection to 10.8.44.0/24 network (VPN net) and 10.8.44.0/24 network (cloud net) works properly (ping ok, both ways).
- from local devices behind the pfsense routers at the remote sites, unable to ping either 10.8.40.0/24 or 10.8.44.0/24 network.
- from local devices behind a Debian machine setup as a router, connection to both 10.8.44 and 10.8.40 networks works properly.
I would guess something at the NAT level is not working properly.
openVPN server.
tun0 -- 10.8.40.0.1
lan0 -- 10.8.44.0.200pfsense router.
wan interface connects to the internet.
lan -- 192.168.23.200/24
ovpnc5 -- 10.8.40.177I can ping from the pfsense router to
10.8.40.0.1
10.8.44.0.200
10.8.44.0.100I cannot ping from a machine on the lan (IP 192.168.23.10/24) to
10.8.40.0.1
10.8.44.0.200
10.8.44.0.100Any ideas?
-
Are both VPN endpoints the default gateway in their local networks?
Did you configure the iroute for the client properly on the Debian server?
@conejero said in OpenVPN Client route traffic from LAN to openvpn Server Network:
I would guess something at the NAT level is not working properly.
Basically the traffic to the remote network should be routed to the respective remote VPN endpoint. So there is no NAT needed.
However, NAT could be a workaround if routing is not possible or not desired for any reason. -
@viragomann as far as I can tell, the Debian openvpn server is working properly. I have another Debian server setup in a different remote office. This Debian server (debian2) connects to the Debian VPN server, once connection is established, all PCs on the LAN side of debian2 can access the servers on the LAN side of the Debian VPN server.
This works fine with the debian2 server. PC1 can connect to cloud1 and to cloud2. The same setup with a pfsense router does not work.
With a pfsense router, the router itself is able to connect to the vpnserver, cloud1 and to cloud 2. However, PC1, PC2 and PC3, whose gateway is the pfsense router, are not able to connect to either the vpnserver, cloud1 or cloud2.
Are there any instructions as to how to setup this connection? Openvpn Client to route traffic to the VPN network for LAN devices. I am most likely missing something. This is what I have done.
- Setup the VPN client connection. VPN/OpenVPN/Clients.
Server mode: Peer to peer (SSH/TLS)
Protocol: UDP
Device mode: tun
Interface: WAN
IPv4 Remote network(s) 10.8.44.0/24
It might be noted, there is no VPN interface asssignment setup. I do not know if this is important or if it has to be manually created.
- Setup the VPN client connection. VPN/OpenVPN/Clients.
-
@conejero
Nice. But the questions I've asked above are still unanswered.This Debian server (debian2) connects to the Debian VPN server, once connection is established, all PCs on the LAN side of debian2 can access the servers on the LAN side of the Debian VPN server.
So is the traffic natted on this connection?
Does Debian2 connect to the same server?
It might be noted, there is no VPN interface asssignment setup. I do not know if this is important or if it has to be manually created.
This is only necessary for special manual routing purposes like policy routing.
-
@viragomann answering your questions:
Are both VPN endpoints the default gateway in their local networks? Yes.
Did you configure the iroute for the client properly on the Debian server? Yes.I do believe NAT is needed though.
LAN PC on network 192.168.23.0/24 --> gateway pfsense router.
cloud PC on network 10.8.44.0/24 --> gateway debian vpn server. -
Solved.
We informed the openVPN server running on Debian about the LAN behind the pfsense with iroute stanza in /etc/openvpn/ccd/ and it can access the cloud pcs now.
Thank you