VLAN confusion
-
I have this setup:

I only have two NICs in my pfSense box. 10.1.1.x (trusted) and 192.168.1.x (untrusted)
I bought a UniFi layer 3 switch (USW-24-PoE) to run a series of IP cameras. Apparently it isn't an actual layer 3 switch though???
I dont want the cameras accessing the internet.
I want to be able to manage the USW-24-PoE and the cameras from the 192.168.1.x network. I dont want the cameras talking out.
Dont know how to set this up.
Do I need to setup two VLANs on the pfSense box? probably not since I dont need the cameras talking out. Would the switch need a VLAN?
Maybe I should buy a true layer 3. Any recommendations?
I've been researching for days trying to figure out what to do so any help is appreciated.
-
10.1.1.x is the WAN?
If pfSense had 3 NICs you could have the third be a CAMERA interface and set firewall rules to not allow CAMERA access to "any," but allow 10.1.1.x access to CAMERA.
If you give the cameras static IPs you could block those IPs via firewall rule, however there's not a way to block them from accessing non-cameras in 192.168.1.x. For that you'd need a VLAN (essentially, the third interface mentioned above). Can the cameras be configured with a VLAN? -
yeah I dont have an additional NIC.
The reason I bought the USW-24-PoE was to do VLANs and segregate traffic and mainly prevent anything on the camera subnet from accessing 192.168.1.x. I dont need the cameras accessing the internet.
Problem is, I dont know how to implement this.

-
Perhaps a simple rule will do the trick?
Create an alias with your cameras. Easier to read and easy to add more camera.
Create a FW rule on the LAN interface.
Action: Block
Interface: LAN (or whatever it is called)
Source: Single Host or Alias - Camera aliasPlace the rule above any allow rules for the internet. This will prevent the cameras from getting to the internet, but will not stop them from getting to the NTP server on the FW or anything on the same network, like your laptop.
-
@andyrh said in VLAN confusion:
but will not stop them from getting to the NTP server on the FW or anything on the same network, like your laptop.
exactly what I am trying to avoid.
Please check the post:
The reason I bought the USW-24-PoE was to do VLANs and segregate traffic and mainly prevent anything on the camera subnet from accessing 192.168.1.x. I dont need the cameras accessing the internet.
-
@amrogers3 said in VLAN confusion:
@andyrh said in VLAN confusion:
but will not stop them from getting to the NTP server on the FW or anything on the same network, like your laptop.
exactly what I am trying to avoid.
With the firewall , you can't prevent any 192.168.1.x device to access another 192.168.1.x device ... The only exception is that you can get the firewall to reject access to the firewall interface ip, on 192.168.1.x.
What are you trying to avoid ?
Cameras going to the internet, or also accessing anything firewall interface ?If my cameras could use NTP , i would certainly allow them to access NTP on my firewall 192.168.1.x interface , that might get the stream to show the correct time.
Accessing ie. NTP on the 192.168.1.x firewall interface does not need any client internet access.
Please check the post:
The reason I bought the USW-24-PoE was to do VLANs and segregate traffic and mainly prevent anything on the camera subnet from accessing 192.168.1.x. I dont need the cameras accessing the internet.
You do know we help out "for free" ....
/Bingo
-
Hello @bingo600
Apologies if I am confusing the issue. Basically, I have a 192.168.1.x network with all my home devices. I bought a UniFi layer 3 switch and want to plug the IP cameras in it and assign the ports to a VLAN and prevent that VLAN from accessing anything outside of it. Cameras need to be blocked from accessing the internet as well.
However, I need to be able to manage the switch from the 192.168.1.x network.
What is the best way to implement this?
-
To recap:
You want 3 different L2 lans with just 2 phys. interfaces , right now WAN + Lan.
Wan : 10.x.x.x Lan : 192.168.1.x Cam : 192.168.2.x Cam devices should be prevented from accessing anything but the local lan .. 192.168.2.x The L3-Switch should have the management ip address in the Lan network.I would keep Wan as "Phys IF 0" , and as you mention : Make "Phys IF 1" a Vlan capable interface.
1:
Personally i would make both Lan and Cam , a new Vlan , and change the ip addresses to reflect the Vlan ie:
Vlan 10 - Lan - 192.168.10.x/24
Vlan 20 - Cam - 192.168.20.x/24Most decent managed switches would allow you to set the "Management Vlan" , and here it would be set to Vlan 10.
This setup could be a bit "tricky" to migrate too , if you don't have any networking/switch experience , as it would be easy to lock your self out.
2:
You could continue with your "existing" setup , and have "Lan" being "Native Vlan / Untagged".
Then Lan would be on "every port" in the switch assigned to Vlan1
I assume Vlan1 is the default Native/Untagged Vlan on a UBI switch , have newer worked with one.Make a Vlan enabled uplink interface on the UBI switch , allowing for Vlan1 (Untagged) , and Vlan10 Tagged.
Then you would add Vlan10 to pfSense Phys IF1 (Old Lan IF), maybe see .
https://forum.netgate.com/post/944383/Bingo
-
Assuming you will go with 2 , from the above.
If you haven't done so already , you might want to connect your Lan interface to the Switch now , and connect your Lan devices to the switch (on Vlan1 ports),
That should work right out of the "Box", i would assume.Now you should enable "tagged" Vlan10 on the Switch port you have connected the Lan interface to. I have no experience with UBI switches.
Then you should enable Vlan10 on the pfSense Lan interface.
Set it up , enable DHCP , and the appropriate rules.
Make some Vlan10 ports on the switch, connect the cameras.
Done.
/Bingo
-
Thank you very much @bingo600 ! I realized something reading your reply.
You are correct, VLAN1 is the default untagged VLAN on UBI.
I set up pfSense similar to what you suggested and I can post screenshots but I believe the issue lies with the UBI switch. It is advertised as Layer 3 but it doesnt do true layer 3 routing.
Please correct me if I am wrong but I dont think I need to set up VLANs in pfSense. Let me explain. The L3 switch does the routing and doesn't need pfSense to route traffic. Lets say I create a VLAN3 for cameras and a VLAN1 profile for the pfSense port. Then VLAN1 should be able to reach VLAN3 but VLAN3 will not be able to reach anything outside of VLAN3. Is this correct?
Could you recommend a L3 switch? 24 GB + PoE + layer 3 with good throughput and switching capacity. A couple 10GB ports would be a bonus!
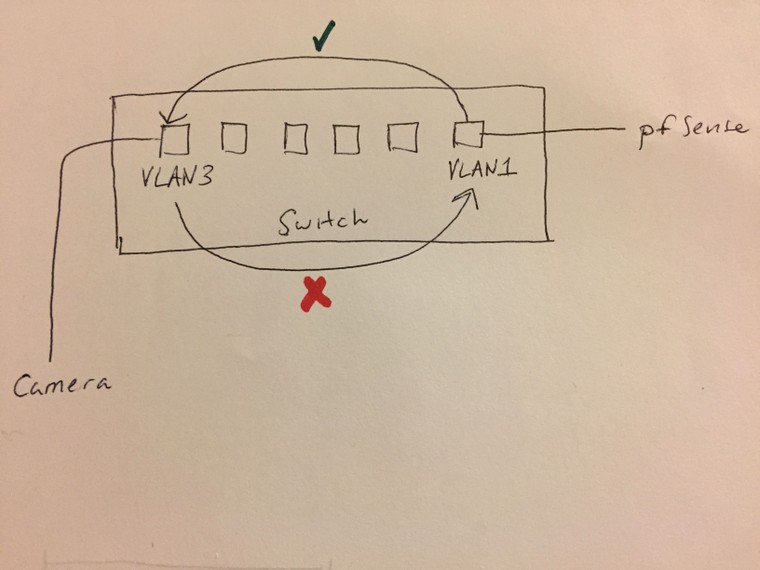
-
Layer2 (L2) Vlan IP data can not communicate with any other L2 Vlan , without the help of a Layer3 (L3) device (Router/Firewall etc) , to route the IP (L3 data) from VlanX to VlanY.
So i recommend NOT to enable ANY L3 routing features on the UBI Switch.
That way the only L3 device that can transport IP data between Vlans is the pfSense , where you have filtering capabilities.
I would expect your UBI SW to be ok , so give it a try.
Just make sure NOT to enable routing (L3) etc ... Then only pfSense can transport packages beween Vlans.Btw: What is the "ISSUE" ??
You haven't described it with a single word.Edit:
If you enable L3 routing on the switch , it would "default" work "both ways".
IMHO you would want to let the pfSense be the L3 device , as it is has the "best" filtering capabilities. But it is your setup
You decide./Bingo
-
The "issue" is this particular switch, the USW-24-PoE. It allows inter-VLANs traffic by default. From the ui.com website it says:
Inter-VLAN routing is enabled by default between all Corporate LAN networks.In this example, I can ping between VLAN2 <<--->> VLAN3. Even with blocking firewall rules.
Therefore, I need to buy a different switch, maybe Cisco, I am not sure. I would like the switch to route traffic in particular situations so I am looking to keep routing on the switch and get a layer 3.
-
@amrogers3
Maybe you could buy a "cheaper L2" switch, and connect your pfSense Lan , and Lan devices to that one. Then on that switch make an Untagged "Vlan3 / CAM" port to connect to the UBI.And thereby still Re-Use the Ubi for Cams (leave all ports on Ubi in "Vlan1" or "Vlan 3").
Now the L2 switch will see All UBI ports via Vlan3 , and the UBI will just have 1 vlan , hence L3 routing won't be an issue.
Maybe @johnpoz can recommend a switch that's "payable in the US" , it seems my favourite D-Link DGS-1210-28 is quite expensive over there.
@johnpoz
Would a refurb. C200 do ?
Cisco 200
https://www.amazon.com/Cisco-Mini-GBIC-SLM2024T-NA-Certified-Refurbished/dp/B07F6HGNLX/I have no experience with "Non Enterprise Cisco's"
/Bingo
-
@bingo600 said in VLAN confusion:
Would a refurb. C200 do ?
Sure why not - there are plenty of cheap switches that can do vlans.. SG200 for sure can do them.
If you don't need a lot of ports you can get say multiple different brands 8 port gig that can do vlans. Like $40
-
-
@amrogers3 hmmm - what is your budget? That is not going to be $40 ;)
Maybe something off ebay.. But problem with highend enterprise stuff off ebay is NOISY!! and power hungry.. You really need 24 POE ports?? That many? That is a lot of poe stuff.. You have that many cameras? Or would like 12 or 8 poe ports out of 24 work?
unifi prob cheapest option - but I really don't think any of their stuff actually does L3, even though they have been talking about it for years. My sg300-28 does L3, and I got it new under 200, but it not any poe.
If you really want L3, and poe (how many ports really need) - if cameras you could prob just break them out downstream to your L3 on their own poe switch.. Camera's don't really need all that much bandwidth.
-
@johnpoz said in VLAN confusion:
unifi prob cheapest option - but I really don't think any of their stuff actually does L3, even though they have been talking about it for years. My sg300-28 does L3, and I got it new under 200, but it not any poe.
yep, that has been my unfortunate experience with Ubi and L3.
The "L3" 24 PoE I bought from Ubi was $800 so a Cisco for a bit more with better functionality will be worth it.