6100 + Zen FTTP (UK) + NordVPN Setup
-
Hi, I am going to be switching to this setup soon & want to make sure I know exactly how to configure the PFSense correctly.
Using Zen FTTP. Only IPv4. I won't be using DHCP, just Static IPs (is that really better for security, or unneccessary?)
I will be using Quad9 (filtered, DNSSEC) DNS Server:
9.9.9.9
149.112.112.112I was considering PiHole + Unbound... but I think Quad9 + PFSense "unbound resolver"(?) will be fine for me. Or, is it necessary to setup pfBlockerNG for malware/ransomware if I'm solely using Quad9? If so, is it easy to set up (i.e. just follow guidelines without really knowing exactly what you're doing)?
I read: check “DNS Query Forwarding” (this seems a must)
Then I read: also check “DNSSEC” and “Use SSL/TLS for outgoing DNS Queries to Forwarding Servers” -- however somewhere else said no need to check DNSSEC with Quad9, and the same for SSL/TLS (that wasn't so clear)?
This is still unclear [what I must do]:
"I remember now the reason for the floating rule for DNS over port 53 - DNS leak prevention! :-)
Making sure that absolutely no DNS queries go out on port 53 and only over TLS on port 853, DNS leaks are prevented. This aspect is especially important if you use a VPN provider."I will simply follow the guidelines to setup NordVPN with PFSense...
https://support.nordvpn.com/Connectivity/Router/1626958942/pfSense-2-5-Setup-with-NordVPN.htmAll devices can have the VPN on constantly, with a couple of locations setup (US, UK).
Should I bother to change the default IP: 192.168.1.1? Would this make any real difference to security? If so, I simply change it to whatever I like (within the allowed range), the access it within a browser on whatever device?
18 characters password(s) or more?
I want Static IPs (no DHCP) & only known devices. Anything else blocked...
No online gaming devices/services. Upnp turned off by default.
So basically, will I be OK just using the 6100/PFSense defaults (i.e. from Quickstart) & following the guidelines for [PFSense +] Zen, IPv4 Quad9, NordVPN? + how to setup Static IP on the devices & block anything else - I still haven't worked out exact guidelines...
At the same time I am looking to be as secure as possible, if there's anything more I can do please let me know (e.g. this goes into much more depth: https://blog.muffn.io/pfsense-guide-nat-firewall-rules-networking-101/) - should I be setting up any special rules for extra safety?
Obviously I know phishing links, etc. I'm starting from a new Macbook Pro, no wifi (with the 6100).
-
OK, now I've just read this regarding Zen's "single static IP":
https://www.zen.co.uk/business/small-business/products-solutions/network-connectivity/broadband/ip-addresses"If you're unsure whether you need more IP addresses, here are some common examples of uses for multiple IP addresses, enabling you to isolate traffic and avoid bottlenecks at the router.
...*The majority of VPN applications."
Am I going to need more 'blocks' with NordVPN?
Also, I got mixed up with WIFI MAC Address filtering / blocking devices. Of course the 6100 is wired only, so only a wired device can connect to it - OR is it theoretically possible for a 'hacker' to connect a device remotely [somehow/anyhow], unless I 'filter' and only allow certain devices & block everything else?
-
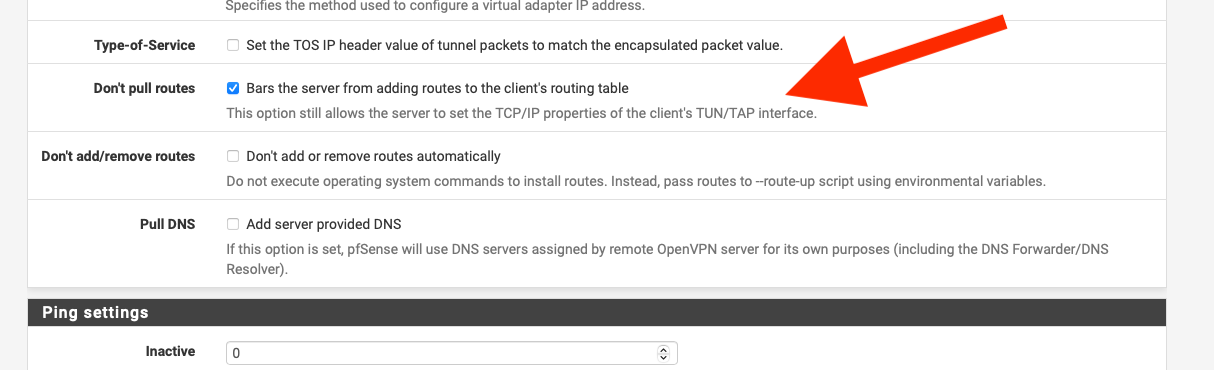
@bworks If you follow https://support.nordvpn.com/Connectivity/Router/1626958942/pfSense-2-5-Setup-with-NordVPN.htm remember to set don't pull routes, otherwise it will point the default route to Nord.
I've got everything from my NORD & IOT VLANs only being able to access the internet, the n_ipv4_local alias contains all my local subnets.
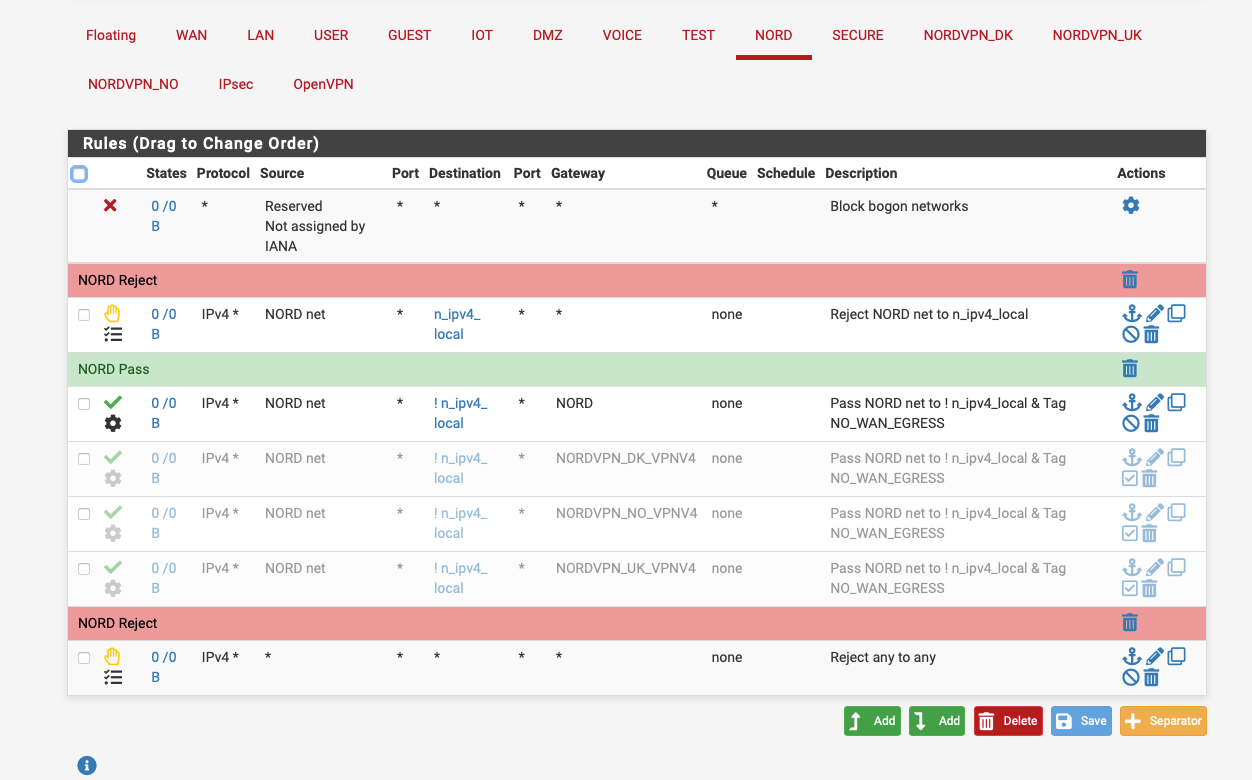
I'm a Zen user ( FTTC ) & have a bunch of VLANS hanging off a single LAN Interface.
I'm using the following packages:-
FreeRadius, pfBlockerNG-devel & Snort.
Is this for home use or buisness ?
I'd be tempted to request IPv6 address space even if you don't use it, its dead simple to set up, you'll get a /64 ND prefix and a /48 PD prefix.
Drop an email to ipv6@zen.co.uk if go for IPv6.
-
@nogbadthebad So if I understand correctly, you need to check “Don’t pull routes” for it to follow the firewall rules [and not just send every device straight to NordVPN]. And then set up the Rules to only allow my devices’ subnet IP(s). Are there any guidelines to follow exactly how to do this? I see this is in “NORD” and not “LAN” rules - does “NORD” appear automatically during setup?
I think my plan is to keep 1 network solely for business (e.g. with cryptocurrency/NFTs the result of being compromised is catastrophic - and other web developments), with no wifi, IOT, etc.
Then a second network (that I already have) for TV, streaming, gaming, everything else - until I move to the countryside when I don’t have to worry about my wifi being hacked by near-neighbours.
So I will probably only need to allow 1 device/subnet IP (my new Macbook Pro) for now & disallow everything else...
Although in the future I will likely set up VLANS / wifi network all in one.
Regarding IPv6 - do I actually need it, if everything is going through NordVPN anyway (that is only IPv4 in the end)? i.e. even if I set up IPv6, wouldn’t it just be forced through the VPN, which goes to IPv4 web addresses anyway? Or would there actually be extra security in place having a daily changing underlying IPv6 address, rather than 1 static IPv4?
But then also isn’t it more difficult to do the subnet IP filtering with constantly changing IPv6?
Many thanks!
-
Oh and another thing was, with NordVPN it seems I would be using their DNS Server, so don't have to worry about Quad9, Unbound, etc.? But I can still set up pfBlockerNG for ads/malware blocking...
-
Hmm, seems I have been misinformed about the security of VPNs anyway?
NordVPN Hacked / Breached and Private Key Compromised
https://www.youtube.com/watch?v=oq9LdMHSDksMy goal is to never be compromised by hackers, like ever. But would a VPN actually be a potential 'weak link' in the security chain?
With a solid set up of PFSense firewall, it will never matter if hackers get my IP address (so no reason to hide it)?
Or even it may be better to go down the dynamic IPv6 route with no VPN?
I don't see me needing to access this setup remotely from another location (at least not in the near future).
So the number 1 goal for my security is the firewall. Protecting my IP address doesn't matter at all?
Let's say my Macbook Pro somehow gets compromised, such as there is software that I need to download & install from 3rd parties, that could potentially be compromised - what is the best way to secure myself from this threat, with the firewall? e.g. monitoring of outgoing traffic going to back the hackers, and stopping it - acting swiftly. I remember Snort could do something like this... ah so I can install this directly at the router/firewall level?
It seems there is a lot more to learn...
-
@bworks said in 6100 + Zen FTTP (UK) + NordVPN Setup:
So if I understand correctly, you need to check “Don’t pull routes” for it to follow the firewall rules [and not just send every device straight to NordVPN]. And then set up the Rules to only allow my devices’ subnet IP(s). Are there any guidelines to follow exactly how to do this? I see this is in “NORD” and not “LAN” rules - does “NORD” appear automatically during setup?
My Nord network is a separate VLAN that I policy route all my stuff that I want to go via NORD, if you dont enable don't pull routes, the default gateway for everything goes via your NORD VPN connection.
I think my plan is to keep 1 network solely for business (e.g. with cryptocurrency/NFTs the result of being compromised is catastrophic - and other web developments), with no wifi, IOT, etc.
Then a second network (that I already have) for TV, streaming, gaming, everything else - until I move to the countryside when I don’t have to worry about my wifi being hacked by near-neighbours.I have my TV's, Apple TV's, etc ... on my IOT LAN and they can only connect out to the internet.
So I will probably only need to allow 1 device/subnet IP (my new Macbook Pro) for now & disallow everything else...
Although in the future I will likely set up VLANS / wifi network all in one.
Regarding IPv6 - do I actually need it, if everything is going through NordVPN anyway (that is only IPv4 in the end)? i.e. even if I set up IPv6, wouldn’t it just be forced through the VPN, which goes to IPv4 web addresses anyway? Or would there actually be extra security in place having a daily changing underlying IPv6 address, rather than 1 static IPv4?
But then also isn’t it more difficult to do the subnet IP filtering with constantly changing IPv6?
Many thanks!I use DHCPv6 to assign IPv6 addresses rather than SLACC.
-
@nogbadthebad Thanks, I think I definitely need to do a lot more research…
I am reading now about recent malware attacks on Mac. I can’t see how I can safely download 3rd party plugins without being at risk.
Or visiting websites/forums that don't have huge budgets for security, i.e. just stick to adobe.com, etc. - but then that rules out a lot of music plugin developers!?
What is the best way to detect & stop malware that is already installed on my Mac using the router (if Apple misses it, like they have done multiple times recently)?
e.g. I’m now looking at UTM (Unified Threat Management) as an important part of the security...
If my Mac gets infected, would the router/firewall/UTM pick it up? Or could the hacker even then attack the router?
Maybe I should have 1 [different] computer specifically/only for connecting to the router to do diagnostics/security checks? And never log in to my router with my Macbook?
I've already been hacked in the past, and these hackers know all the sites I visit. There are a lot of music production tools that I just can't see me be able to use securely, or forums. They would easily track me down again and do targetted attacks. I basically missed out on the crypto/NFT-craze due to this despite knowing early on. They have made it impossible for me to do business online (or made me believe).
I guess I do particularly need a VPN to stop them from getting my "static IP" & trying endlessly to break-in also? Bec. any exploits such as those recent Mac malware attacks, and that's it, they're in again, and again, and again.......
-
@bworks Snort or Suricata would be your best bet to detect malware.
-
@nogbadthebad Thanks! So years ago supposedly there were "no rootkits on Macs", of course "no malware", "router cannot be hacked whatsoever", etc.
I basically completely gave up trying & just accepted the situation (at this stage I think it's just a running meme, to keep hacking me until I'm x...)
However returning to the situation once again, it's likely I have the rootkit right now. What's the best way to detect it? I've installed Snort a long time ago and didn't find anything suspicious (or I don't know maybe I missed something). But I installed it on my Mac, not my Sky router that at the time couldn't even be changed to an external one.
If I get a new router and install Snort on it, then connect this Mac, will it then [finally] find something?
Or will the hackers just simply switch it off when they know I'm looking for it?
-
If anyone else comes across this in the future - I believe the only truly safe way is a combination with Chromebooks/extensions (that are much less likely to get malware).
https://cryptonews.com/news/trader-s-lesson-why-you-shouldn-t-keep-large-amounts-of-cry-9302.htm
"If you MUST use it, buy a Chromebook and a hardware wallet and use them STRICTLY for Metamask."
"According to him, while a Chromebook limits what can be installed on one’s computer, it still allows installation for potentially malicious browser plugins, so one must beware of installing them." (this is not really a big deal).
I will have to get a separate Mac for music software for 99.9% security, as so much is third party - but this will never connect to my router (I will block it) - damn Bluetooth is so nice but I can hard wire everything I think. And I will use a VPN to access my accounts & downloads to protect my IP, just in case.
Surely this is ultra-secure (with a UTM setup on main router/firewall)? Am I missing anything? New Macbook somehow gets malware, then it's isolated (like a VM, but hardware), and I can check the 'UTM' traffic with Chromebook. Crypto/NFT/MetaMask on Chromebook. 100% secure?
-
Ah yes I was missing VLANs!
https://www.routersecurity.org/vlan.php
"On a home network, the protection offered by isolating these devices is to minimize the impact of a hacked device. Likewise, a malware infested Windows machine can't spread its tentacles, if it can't see any other devices or computers."
This is clearly what happened to me & my family, where it was impossible to escape the hackers, despite spending thousands on buying new devices & changing ISPs. At the same time if I'd been able to invest that money in the cryptos & NFTs I wanted to (knowing the potential), I'd have around $6 billion, instead of being practically homeless.
Thanks @nogbadthebad for leading me on the right path.
-
And also as is proven here, it's very rare to actually find help.
Especially when someone claims/knows that they have been hacked for many years, yet they are constantly branded "delusional" & "crazy", especially if they own a Mac.
Back then I had phone calls with security experts where there was nothing they could do, "not possible", etc. All anyone was interested in is whether they stole any money.
But I guess there are much worse failures to act in this parasitic $hi hole world, so I should just count myself lucky & "stop going on about it" or "just ignore them"?
-
Well apparently all of that still won't be enough to stop them, according to the memes [puke]!
And yes... I see an issue with Zen sending out the PPPoE username & password via "email", which I cannot receive on a secure network bec. they are hacking everyone I know, and I can't even order it securely. Although hopefully/surely there is a way that Zen support can help with that over the phone...
Secondly it could be due to the use of VLANs, e.g.
https://security.stackexchange.com/questions/238796/what-are-the-security-issues-can-be-exploited-to-vlan-switches-to-compromise-net"As an abstraction, the operation of a managed switch can be described with three planes:
Management plane used to configure the switch (SSH, HTTP...).
Control plane that controls how the packets should be forwarded (L2) or routed (L3). It can learn from MAC addresses from the packets it sees and there are protocols swithes can use to share information, prevent loops (spanning-tree) or handle shortest routing paths (OSPF).
Data plane or forwarding plane that does the actual switching job.
Leaving aside the possible software vulnerabilities in the switch itself, the main issue remains how well the control plane and the management plane are protected from the data forwarded in the data plane. The data plane handles also all the control plane protocol traffic between the switches, and if the packet seen must be processed by the control plane, forwards the packet to it.In a secure configuration, every access port can only see the traffic inside its own VLAN, and the switch should not accept any control plane protocol traffic from them. If any of these protocols is open on an access port, an attacker connected to it might mimic another switch and
jailbreak from its own VLAN e.g. by
becoming a spanning-tree root or a node with MitM position.
activating trunking on the port and seeing all traffic with 802.1Q tags (DTP, VTP, HSRP...)
cause DoS attacks e.g. by flooding CDP table, or flooding any BPDUs that will cause too much processing on the control plane, exhausting its resources
disable 802.1Q VLANs altogether, making all networks see each other (VTP).
Yersinia is a tool that automates all these tricks...The management plane must be secured, because by altering the configuration its possible to remove any lower plane restrictions the port has. Ideally, you'd have a separated management VLAN altogether."
Since I am not a computer science degree university student, I'm not educated enough to understand how to stop them.
Just unbelievable really how there's not a better/consumer way to stay safe!? Normal people don't stand a chance.
-
@nogbadthebad Uff, do you have any idea what all of this means?
https://oneplus-x.github.io/2017/02/25/ISP-Hacking/
"What can ISPs do?
Enforce stronger authentication mechanisms like PPPoE-CHAP, with a strong password policy for the same."In my previous home, there was an incident where someone took the fiber box off the outside wall & did something suspicious!!! I actually saw 'him' when he stood up right at the window then walked off. I thought WTF? Then when I went outside the box/cover was off the wall & on the floor!?
I thought, and apparently according to everyone, nothing can be done to physically hack that way, such as connecting some kind of device, can they? F*kin insane what I've been through!
Even having to deal with 2 family deaths, clearly extreme PTSD (ongoing), health issues - nothing will stop these parasitic psychopaths! It's one big hilarious game to them, with endless memes or "lulz"............
-
@bworks said in 6100 + Zen FTTP (UK) + NordVPN Setup:
https://oneplus-x.github.io/2017/02/25/ISP-Hacking/
Not a clue, I'm not an ISP

-
@nogbadthebad Well I will have to get the cyber security experts in to figure this out, I guess.
Back in the day there was practically no one, other than starting prices of $300K for massive companies (and even them telling me things were impossible that have been proven today).
All of this that has been 100% confirmed was supposedly "impossible" back then:
https://www.theweek.co.uk/news/uk-news/952744/outdated-internet-routers-put-millions-at-risk-of-being-hackedEvery single expert said no malware or anything for Macs.
All of the security experts need to realise that these underground hacking gangs have their own little secrets. Look now, literally everything that was "impossible" has been proven. Even iPhones hacked into. The info comes out years down the line.
-
@bworks said in 6100 + Zen FTTP (UK) + NordVPN Setup:
https://oneplus-x.github.io/2017/02/25/ISP-Hacking/
That only really applies to an apartment building scenario as described. If you're using FTTC (VDSL) you are not in a broadcast domain like that. FTTP (GPON) is also not that though without testing it I'm unsure what you would see there. doubt you could MITM the PPP session though.
If you're on BT for example they use the same password for all clients, you don't actually need a password. You are authenticated by connecting from the right line so the PPP credentials are unimportant.Steve
-
@stephenw10 thanks! I agree it's probably a secure part of the network - but can't say 100% anymore.
There's likely another way they are thinking about...
There are ‘bugs’ in every single software! That’s why there are endless “security updates” / “make sure you install the latest firmware updates”, blah blah blah.
The fact is the software has already had the bug(s) long before the updates! And only ethical hackers are reporting them.
Check out this:
https://routersecurity.org/bugs.phpThe bug that scares me the most is the one that allows bad guys to bypass a router firewall and attack devices directly. He tested four consumer routers and found two were vulnerable, but he did not name names and did not say which of the 12 bugs they were vulnerable to.
“Bugs bugs bugs………”
2 years Virgin Media does nothing (I’ve been with them in the past)
Even Fortinet/Fortigate bugs / Cisco “backdoor account”, “flaw leaves small business networks wide open”
What is the history of “bugs” on Netgate hardware / PFSense?
Unfortunately as soon as there are any single flaws in the software, that's it. I'm not waiting for the hackers to come along.
-
And there goes "bluetooth is invincible" / "impossible" as well:
"Millions of Wi-Fi access points sold by Cisco, Meraki, and Aruba a critical Bluetooth bug that could allow attackers to run install and run malware on the devices. The bug was found by Armis. The malware could get access to all subnets, that is, it would not be stopped by a VLAN. The bug is in Bluetooth Low Energy (BLE), in software from Texas Instruments and they were aware of the issue, but they were not aware that it could be exploited in such a malicious manner."
"Not me, Bluetooth is always disabled on my phone."
"Way to go Aruba. An attacker can learn the password by sniffing a legitimate update or reverse-engineering the device. Game over. Bad guys can then install any firmware they want."
"Tin foil hat: a reader comment at Ars raised an issue that I first heard at a security conference this past summer. What if the removal of 3.5 mm audio ports in phones was to force more people to keep Bluetooth enabled, and thus, keep them traceable?
If that is true, we won't know for at least 30 years."