Blocking traffic from/to other networks/interfaces
-
I have two main ports on my pfsense router. 1 is for my primary, personal network. The other is for gaming. They have different IPs. For the gaming network, I just created a rule to block any traffic that goes outside of that defined network (reject - used invert match). Is this the proper way to do this, or is there a better way to do this?
-
Depends on what you are trying to do.
If you are trying to block devices on the gaming network from reaching anything outside of the gaming network, you want to make a rule that rejects all non-gaming network traffic. This would include traffic to the primary, personal network as well as rejecting traffic to the internet. The rule on the gaming network interface would look like this, "source - any, destination - not gaming network"
If the goal is to prevent all devices on the gaming network from reaching the primary, personal network but device on the gaming network still have internet access, then you want to change the rule on the gaming network interface to "source - any, destination - primary, personal network".
-
@droidus said in Blocking traffic from/to other networks/interfaces:
or is there a better way to do this?
I have come to the conclusion that it is always best to be very explicit with your rules vs using ! or inverse rules.
If your goal is to block your game network from going to lan network, then I would put in a explicit rule that says that.. Or use a rule that lists all the rfc1918 networks, etc.
There can be some odd stuff that happens when there are vips and you use bang rules.. Also its easier to read the rules if your very explicit with them vs doing inverse stuff.
Here is an example of a network that is locked down from going to any of the other local networks.
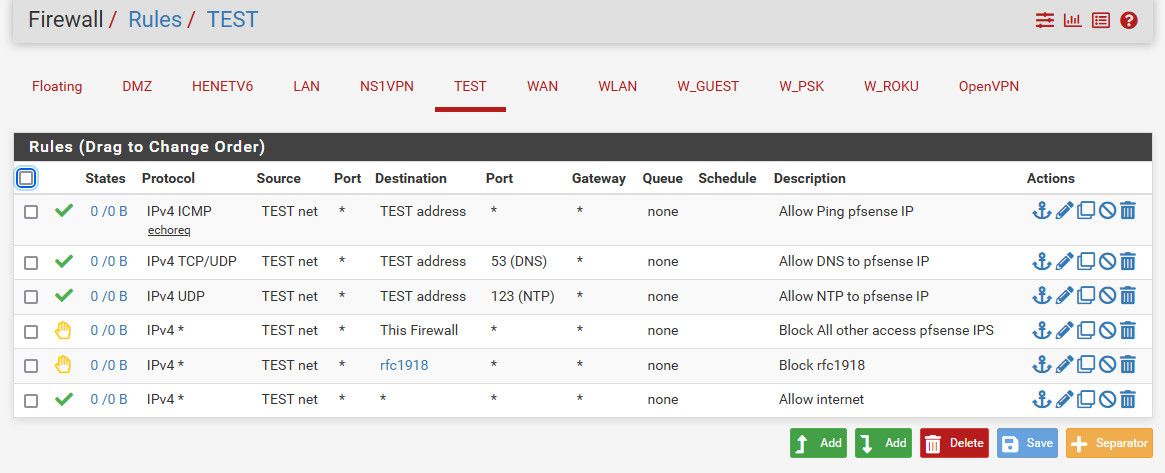
This network is allowed to ping pfsense, allowed to ask it for dns and ntp. But not allowed to talk to pfsense on any other port on any other interface (think gui or ssh for example). The this firewall alias is good because it includes your wan IP, which normally would be public and not included in the rfc1918 list, and it could change, etc. so the alias makes sure can not go to wan IP for access to say web gui, even if it changes.
And then it is specifically blocked from taking to any other rfc1918 network (10/8,192.16/16 or 172.16/12)
The last rule allows internet.