Single device vlan
-
Like many, I'd like to separate wifi from the LAN using VLAN.
The wifi device itself doesn't seem to allow for VLAN but the switch it connects into does.
I created VLAN2 (untagged) on the switch and connected the AP to port 2 of the switch.
I then created a VLAN2 on the LAN interface of the pfsense but that's where problems start and I can't seem to find enough information to get this done. Been trying for two days now.The AP is connected to the LAN (192.168.1.1/24) and I know its MAC address.
The VLAN interface allows me to enter an IP but it won't accept an IP that is already on the LAN.
I can try entering a completely new LAN segment like 192.168.240.10 but then even if I set the AP to that IP, nothing works.
I don't need a DHCP server in this case and even when I tried setting one up, I have no way to tell the AP which DHCP to use.What am I missing here?
-
@lewis If your AP doesn't support vlans.. But you want all devices connected to the wifi to be on vlan X..
Create a vlan in pfsense with the ID you created on your switch - say 192.168.2/24 with pfsense IP 192.168.2.1, enable dhcp on it. Put this vlan on your lan physical interface.
Now on your switch tag this vlan ID to port connect to pfsense lan.
And port connected to your AP put in this vlan untagged. Now connect your wifi using one of its lan ports. Turn off dhcp server on your wifi router I assume. Set this old wifi router lan IP to say 192.168.2.2/24 and there you go all devices on your wifi would be on vlan X you created.
-
@johnpoz said in Single device vlan:
@lewis If your AP doesn't support vlans.. But you want all devices connected to the wifi to be on vlan X..
Create a vlan in pfsense with the ID you created on your switch - say 192.168.2/24 with pfsense IP 192.168.2.1, enable dhcp on it. Put this vlan on your lan physical interface.
Now on your switch tag this vlan ID to port connect to pfsense lan.
And port connected to your AP put in this vlan untagged. Now connect your wifi using one of its lan ports. Turn off dhcp server on your wifi router I assume. Set this old wifi router lan IP to say 192.168.2.2/24 and there you go all devices on your wifi would be on vlan X you created.
I think there is something I am missing here too. Let the pfsense DHCP server hand out IPs for the wifi users? The AP offers its own DHCP IPs. The AP is connected to the switch using its WAN port.
-
Sorry, I was trying to re-upload the images but the site flagged it as spam so here they are again.
Here is how things look.
Note that the AP WAN is set to 192.168.254.2/24 with a gateway of 192.168.254.1 but that probably doesn't work because I don't have a DHCP/gateway set up on pfsense. I tried using the 192.168.1.1 gateway but that didn't work either.


-
@lewis What hardware are you using, a Netgate device?
If the AP is connected using its WAN port then it (presumably) provides NAT to wireless clients. In essence it's a router. That config prevents LAN from accessing the wireless clients directly.
If you can set up a separate interface on the pfSense router then you have a separate network and are done. A VLAN is treated as a separate network/interface but then the AP would need to know to use that VLAN.
On the pfSense interface you have its IP as 192.168.254.2/32 meaning it can't talk to any other IPs. You probably want it to be a /24 subnet mask, and possibly 192.168.254.1/24. Otherwise the 192.168.254.2 address would then be the gateway for the AP, which would need to be a different IP like 192.168.254.3/24.
-
Yes, I do have multiple NICs with the networks separated by pfsense/rules however, I'm trying to learn about VLANs since I've never used one.
I understand the concept, creating multiple LAN segments that can see each other or can be blocked from each other but have never configured one to understand how to do that.
I should have mentioned that the wifi device is a router and clients are connecting to that. It hands out DHCP IPs so I'm working only on the WAN side of the AP.
The AP doesn't have VLAN capabilities but I thought I would accomplish this using a VLAN configured on one of the switch ports which pfsense could recognize by creating a similar VLAN2 on it.The APs WAN port is physically connected to port 2 of a netgear switch.
The switch has VLAN2 configured on it as does pfsense.From what I've read, I thought I could do this based on the port alone between the switch VLAN ID and the new VLAN interface I created on pfsense.
-
I guess I should add that the AP is an Archer ac1750 v2.
Maybe it has VLAN capabilities but I've yet to find anything and nothing in the manual. -
@lewis said in Single device vlan:
I should have mentioned that the wifi device is a router
A router which also does NAT (masquerading) on upstream traffic?
If so, there is no need for a VLAN at all. The whole upstream traffic from devices behind the router will get the routers WAN IP. So you can simply filter for this IP on LAN.
Maybe it has VLAN capabilities but I've yet to find anything and nothing in the manual.
Does it also have a real AP mode? Possibly in this mode VLAN capabilities come up.
-
Yes,it's a real AP. It's a wifi router/firewall. Yes, it does NATing.
It has an IP (192.168.1.2) on the primary LAN (192.168.1.1) so acts as just another client on the LAN. However, the wifi clients can see other devices on the LAN since there is no filtering and I've never looked at possibly filtering just one IP to block it from the LAN side.
Besides the above, I'm wanting to find a situation where I might want to use a VLAN to learn more about using such.
-
@lewis said in Single device vlan:
The AP offers its own DHCP IPs. The AP is connected to the switch using its WAN port.
All of which not the way to do what your asking.. Your just natting at your old wifi router then, and all your clients will just be behind whatever IP your wifi router gets on its wan.. While that works, does not give you any sort of control of what specific wifi clients might be doing or what you might want to allow specific ones to do, etc.
Yes,it's a real AP. It's a wifi router/firewall.
That is really not an AP, that is a router and AP and switch ports and will be doing nat. A real "AP" would just be that, and most likely actually support vlans, etc.,
What you have is a wifi router, and to use it as just AP does as I described above. Turn off its dhcp, connect it to your network via one of its lan ports. Change its lan IP to be on the network your going to connect it too - now its just an AP.
If you have an extra port on yoru pfsense to use for this network, then there is nothing to do for "vlans" on pfsense.. Its just another network... But keep in mind you can't have all ports on your switch untagged in multiple vlans on the switch..
Vlan 1 or some other vlan on yoru switch connected to lan port of pfsense, other vlan lets say 2 connected to other interface of pfsense. But ports can not be in both vlan 1 and vlan 2 untagged at the same time.. You can only ever have 1 vlan untagged on a port. Other vlans would have to be tagged.
If your going to tell pfsense there is a tag (ie vlan) then you would have to tag that on the port connected to this port..
You show your vlan on pfsense connected to your lan interface bce2, but what are you doing with bce0 and bce1
-
Ok, let's see if I can simplify this so it doesn't get too complicated.
To me, the wifi router is an AP in that it it a wifi access point so maybe I used the term wrong. It is a full router/firewall with wifi and LAN ports. Only the WAN port is used to connect physically to the LAN.
The other interfaces that you see I had mentioned are being used with different networks. For example, the main LAN (to me) is 192.168.1.1/24 and there are 10.0.0.1/24 on one of the interfaces and a free one for a 172.16.0.1/24 I'll put in later.
I don't want to use up a whole interface just for this wifi access point but more importantly, I want a reason to use a VLAN so that I can learn about it since I've never needed one before.
The netgear switch has a default VLAN1 so I created a second VLAN2 since VLAN1 is a default on most devices that have VLAN capability so I wanted to make sure that was not a conflict anywhere.
The switch seems to show that all ports are untagged, for VLAN1 which i think is the default. However, VLAN1 is also somehow associated to something called Unit 1. I need to look that up for netgear I guess.
What I am trying to learn or understand is that when a device doesn't have VLAN capability, what other options are there in this case? Can I VLAN by port? That's what I was trying to accomplish.
I connected the wifi access point to port 2 of the netgear.
I created a VLAN2 on the netgear tagged to port 2.
I created a VLAN2 on the LAN interface of pfsense.But, since I'm not yet familiar with VLAN's, I have no idea where to go from here.
-
@lewis said in Single device vlan:
To me, the wifi router is an AP
Not really if your letting it nat and hiding the wifi clients behind its wan IP it isn't. You can for sure just use it as an AP following my instructions or if it has some AP mode you can put it in, where it bridges its lan port to the switch ports and wifi radio.
I don't want to use up a whole interface just for this wifi access point
Thats great - then you will have to TAG the vlan you setup on your switch that you want to use connected to the pfsense lan port. And that vlan untagged on the port connected to your AP..
when a device doesn't have VLAN capability
I already went over how to do that, your AP or wifi router as just an AP has no vlan capability.. If you want to have different wifi networks and vlans - then you need an AP that supports that. But you can use any old wifi router as just an AP if all the clients on its wifi network will be in just 1 vlan.
-
The term 'AP' implies a layer 2 device that connects wifi to Ethernet. What you have is a device that includes an AP. It probably also includes a switch, a router and maybe a modem. As mentioned what you want here really is only the AP part.
https://docs.netgate.com/pfsense/en/latest/recipes/external-wireless-router.html#turning-a-wireless-router-into-an-access-pointIn your screenshot above from your switch you appear to have all ports untagged in VLAN 2. You need to have at least the port connected to pfSense set as tagged. Can we see a current screenshot of that?
Steve
-
I always thought AP simply meant a wireless access point.
Yes, that link shows how to set up the wifi device to be bridged or separate from the LAN using another interface but I'm trying to learn about VLANs.
I'm already using multiple interfaces and know (basics) how to do that.Sure, here is an image of how the switch it set up now.

-
@lewis said in Single device vlan:
I always thought AP simply meant a wireless access point.
True that is what it means... But what the soho wifi routers are more than just AP, they have one.. But they also have switch ports and routing/firewall engine.. They do NAT, etc. So while your device does have an AP as part of it. Its not just an AP, unless you just use it as that. If you are letting it nat, and provide a different L3 network to devices behind it on wifi or via its switch ports its not really an AP.. Its still in wifi router mode..
If what you want to do is play with vlans and such.. You need to put it in AP mode, so that now you just bridge wifi to the wire at L2.. Since your device can not do tagging or understand tagging for vlans. Then you can only ever put your wifi or wired clients on the device in 1 vlan.. But sure you can then play with vlans on pfsense. And you can handle multiple vlans on your network via your switch that does understand vlans. Its just your wifi device is going to be limited to just 1.. If you want to be able to put wifi clients on different vlans, you would need more wifi routers to use as AP. or get a true AP that supports vlans - the unifi AP are very popular around here. I have 3 of them, and they handle vlans quite easy, I have 4 different SSIDs all on different vlans for example.
-
Ok, I see what you're saying now.
I thought there might be a way of achievning VLAN by using a tagged port and pfsense knowing about it.
Thank you everyone for the clarification. Now I need to find something that does handle VLAN so I can continue with my quest :).
-
@lewis again you can do vlans with that device as an AP... Its just that all clients will be on the same vlan. This would be a different network than your lan.. That is all quite easy to setup and the instructions I gave first would accomplish that.
But if what you want is multiple vlans via different SSIDs - then yeah your going to need AP that does that, any of the unifi AP would.
Or you would need a wifi router that supports 3rd party software, like ddwrt or openwrt that can add vlan support depending on the specific hardware your actually running it on. DDwrt and Openwrt do support vlans, and works on most all hardware that will run it - but if I recall correctly there is some hardware it will run on that vlans don't actually work.. But maybe your hardware will run those, or some other third party firmware? Merlin is another, etc.
But best option is to get an actual AP meant to handle vlans..
What is really ironic if you ask me - is the hardware does vlans. That is how they isolate the wan from the lan, and how they allow for creation of a "guest" network.. The problem is they have no way for the user to adjust what tags are used, and for the device to actual put the tags on the traffic that leaves it physical ports. They are all just internal used vlans.. So simple change in the code running on the hardware would all that is needed for clients to be able to actually do vlans and used on the rest of their network or the different switch ports the are included with all of these devices.
My take is they believe the users of their products are too stupid to want or need vlans ;) What other reason could there be not to provide a feature their hardware supports? Maybe they believe such a feature would cause too many help requests ;) That is why if you device can run 3rd party you can normally do vlans.
Here is like a typical basic block diagram of pretty much any wifi router.
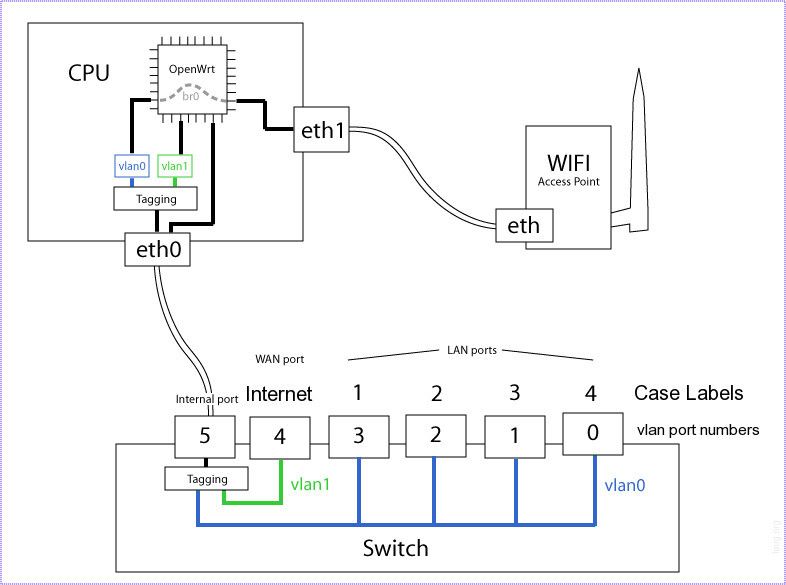
-
In addition to having port 2 set as tagged in VLAN 2 you will need to have whichever port is connected to the wifi AP/router set as untagged. If your AP also supported VLANs you could tag VLAN 2 straight it (trunk it) but since it doesn't you need to untag it on a separate port at the switch.
I don't think you said what the wifi device is but it may be possible to enable VLANs on it by reflashing it's firmware. Most SOHO routers do actually support VLANs it's just not exposed by the factory firmware. However I wouldn't attempt that until you get it working as it is.
Steve
-
Lot's of great info, thank you very much.
For now, I just set up the wifi as an AP based on the link that was shared. I did that because it was never really secured.
Works great and I like how I can see the wifi connections on pfsense now.Maybe the reason the wifi device doesn't have VLAN is because it's around 8 years old and version two of five since then. I could flash it to openwrt but in this configuration, it will be fine.
Now I'll fire up a little mini router running openwrt on it to keep trying to learn about vlans :).
Thanks again.
-
@lewis said in Single device vlan:
Maybe the reason the wifi device doesn't have VLAN is because it's around 8 years old and version two of five since then
No that is not it - even the lastest and greatest soho wifi routers that cost $300 don't have vlan support in native firmware.. Look yourself for one.. They don't support it because they don't want to because they don't think their user base wants it or needs it.
I have played with a lot of soho routers - I have never seen one that supports vlans in native firmware. If you want that option you need a AP designed for business use, or what they call prosumer - the unfi stuff does it.. But I will admit its a bit overkill for your typical home user. Its designed for small business or very budget enterprise setups, home networking enthusiasts, etc. Not all business want to spend the $$ for a cisco wireless deployment ;)
If you want vlans on your soho type wifi router you need to use 3rd party firmware on them. Or get a device that does it on purpose.. Unifi, Omada are 2 lower cost options. As you move up the food chain to cisco ;)
There are many other choices as well - enterprise AP via 2nd hand market, ebay etc also very common options for someone wanting to do wifi vlans on a budget.. Rukus very popular AP to get 2nd hand at good price, etc.
I personally don't get it - You would think that these companies that put out their so called "high end" mesh wifi devices. Designed for the home user would see that adding vlan support could be a differentiator from their competitors and add such support.. Once one of them would do it, sure they would all jump on the band wagon and it would be great for the end user..
Maybe the other problem is - just vlans, without the ability to firewall between them is kind of pointless.. So now verse just adding the ability to vlan, they would also need to allow for firewall between the vlans, etc. So it gets a bit more difficult.. So these systems that are your router and wired and wifi all in one become a bit more difficult to support.