WireGuard Road Warrior setup
-
Ive struggled with this for a few days.
I followed Christian McDonalds Youtube video to set it up.
The problem I had was I could either access my Lan with WireGuard on or turn it off and access the internet but not both.
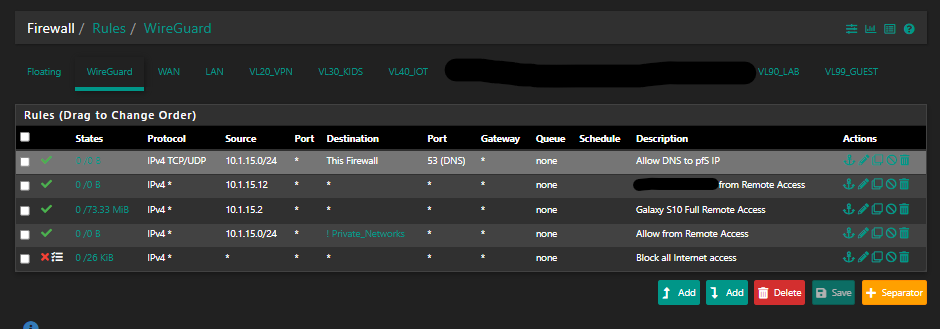
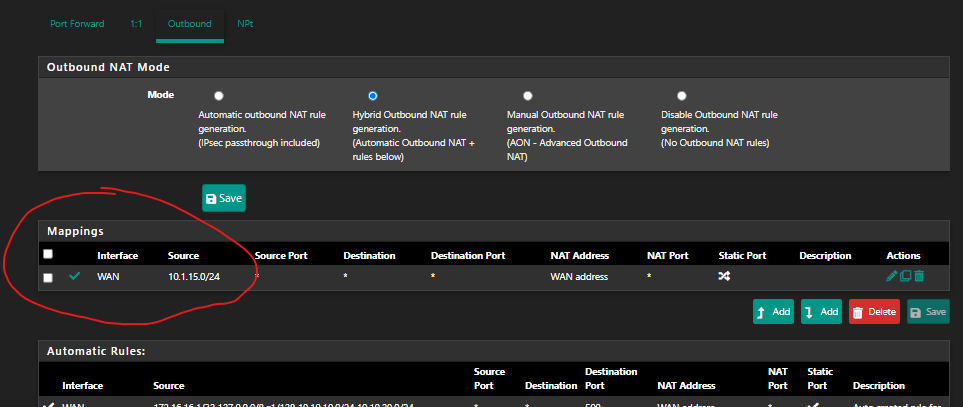
I finally got this working by assigning the tunnel to an interface, removing the NAT rule I created as per the video (its now an interface so comes under the auto rules) and it works fine now.
Maybe this info will help someone. The peer in this case was an iPhone.
One thing I did notice is that there doesn't seem to be any logging anywhere. (if ive missed it please let me know)
Rob
-
-
@ciscox hi thanks for the reply.
That is what I had before but I thought it was working and then suddenly it stopped. This would happen often, but I couldn't figure out what was going on.
However my new setup was working and then I changed my DNS server and now its exhibiting the same behaviour.
I need to work out what's going on, it would be great if there was more logging on the pfsense wireguard package so I can try and figure this out.
-
@hulleyrob
I see a similar issue but with Android.Followed the video (did not create an interface like you did) and most of the time it just works. But from time to time the DNS resolution just comes to a halt on my Android devices. I don't know what causes it and haven't had the time to figure it out yet (and as you say, logging seems difficult to come by).
With the Android devices, I just drop the VPN then reconnect and all seems to work again.
-
@jim-bob-the-grand interesting I had a similar experience with iOS before creating the interface. Thought It was something to do with the setup which is why I created the interface and is "seems" better now.
-
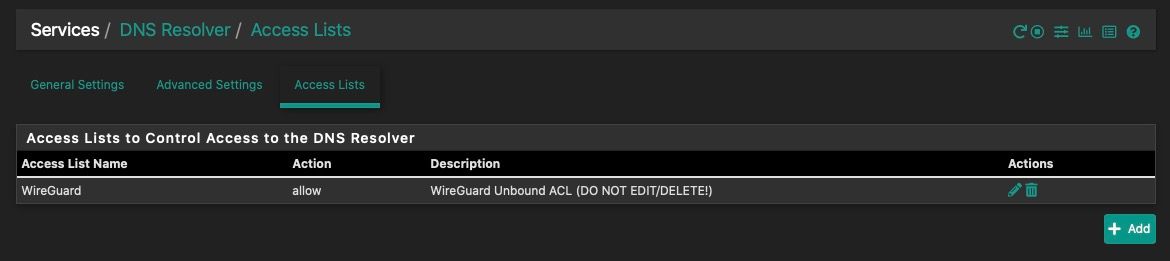
Can you confirm if the Unbound ACL is being created?
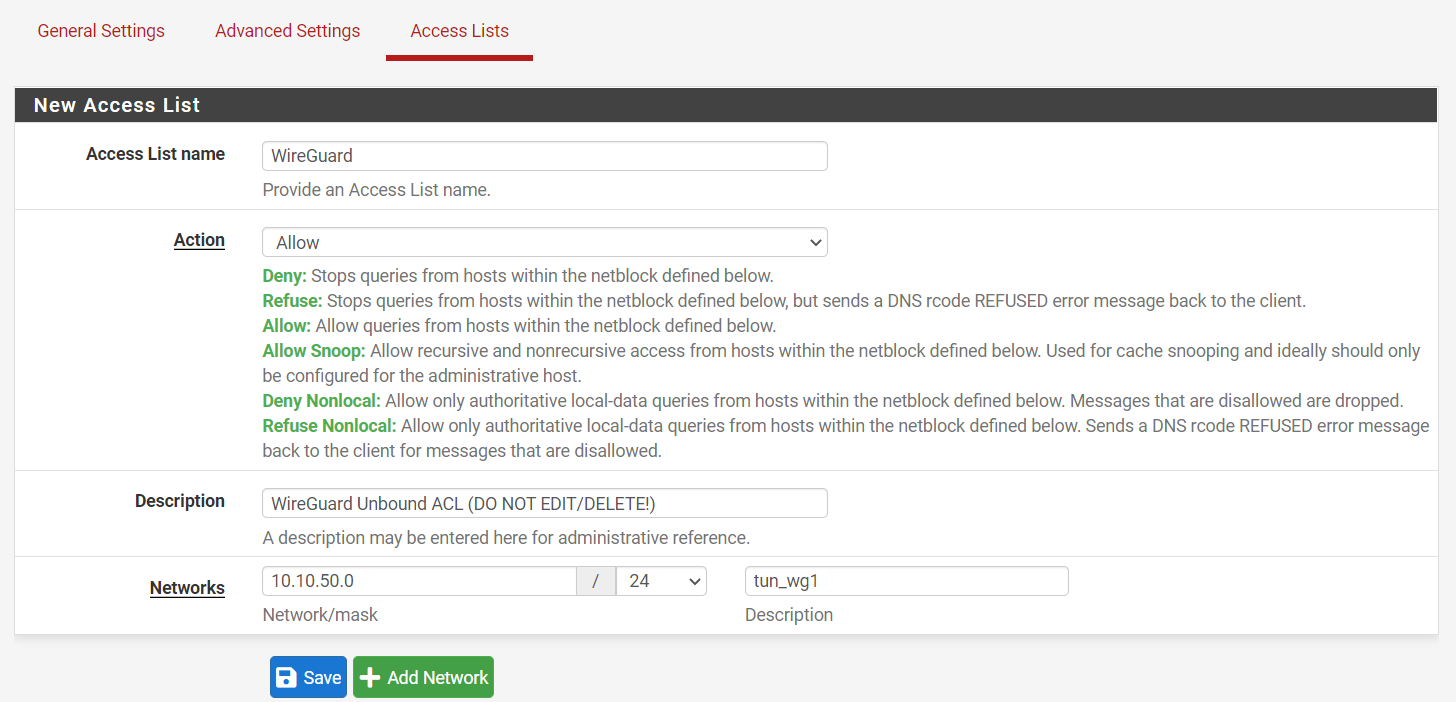
This isn't necessary for assigned tunnel interfaces as pfSense already appends these subnets to the Unbound config, but for unassigned tunnel interfaces this additional "step" is required. It should be automatic.
-
yes it was
-
Hi,
Is it normal that you see your other VPNs here?
tun_wg0 is my remote VPN server where I connect devices to have access to the home.
But the others are VPN connections to other VPN servers.
And I see one is missing from my list tun_wg3tun_wg1,2 and 3 are from the same VPN provider.
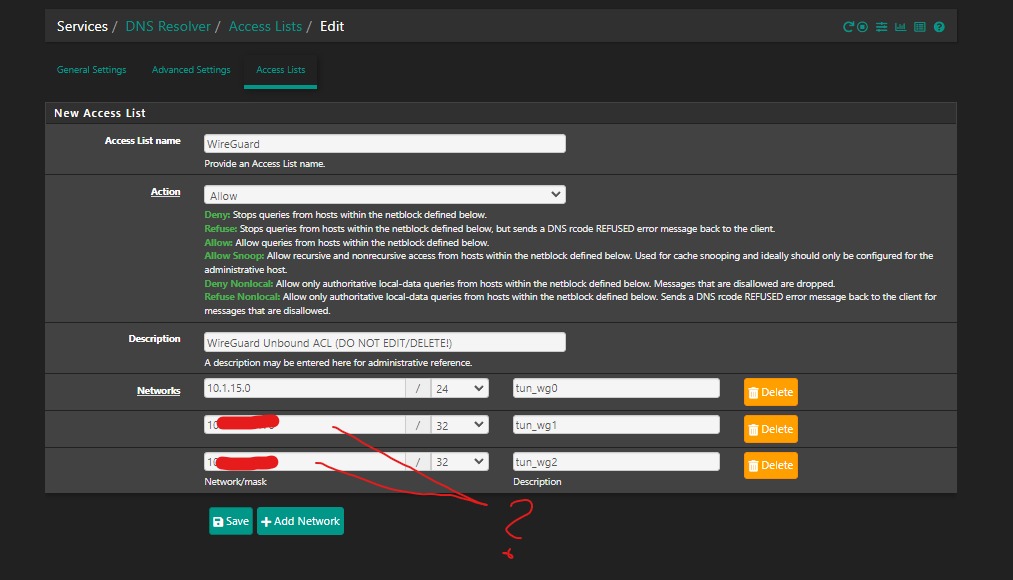
-
@cmcdonald said in WireGuard Road Warrior setup:
This isn't necessary for assigned tunnel interfaces as pfSense already appends these subnets to the Unbound config, but for unassigned tunnel interfaces this additional "step" is required. It should be automatic.
@hulleyrob said in WireGuard Road Warrior setup:
yes it was
I had the exact same thing happen to me. I have a Wireguard tunnel installed as an interface for my road warrior set up. I could not get it to resolve until I created in ACL for Unbound. This drove me nuts for days, the details are all in this thread https://forum.netgate.com/topic/165818/dns-not-working-with-phone-as-peer?_=1637700225107
It seems to me that there is an issue/bug where the Wireguard tunnel is not recognized by Unbound and therefore Unbound does not see the interface as an internal network and therefore requires the ACL.