OPT1 and OPT2 are two networks with different VLANs but I can ping hosts on both the networks
-
Dear Users,
I'm a newbie and I'm still struggling with pfsense firewall rules.
I have a problem with the two different networks defined on OPT1 and OPT2 interfaces (192.168.12.0/24 and 192.168.13.0/24).
In particular, I just noticed that an host on OPT1 network can ping an host on OPT2 network. I don't know why it happens, the two networks have a different VLAN ID.I tried to set some firewall rules on the top lines for each interface:
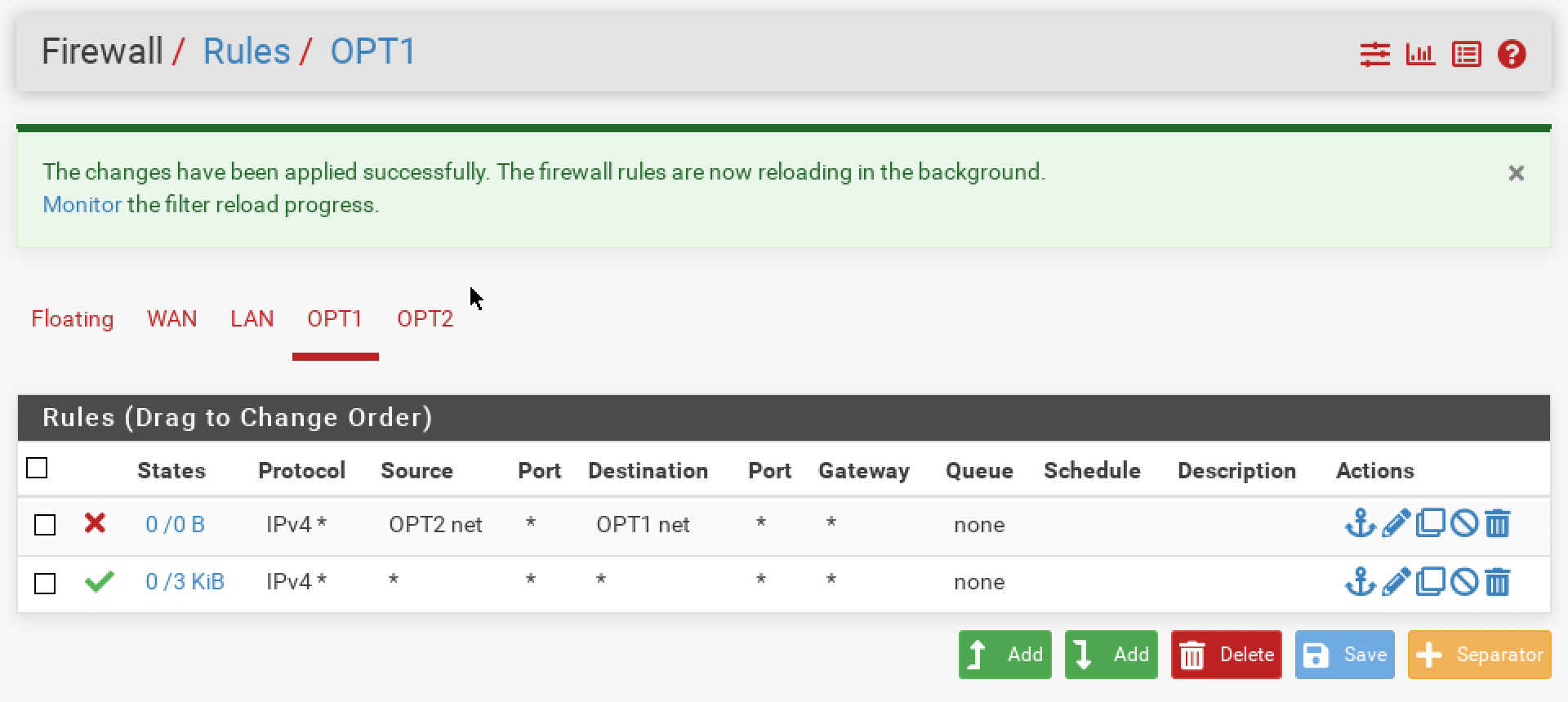
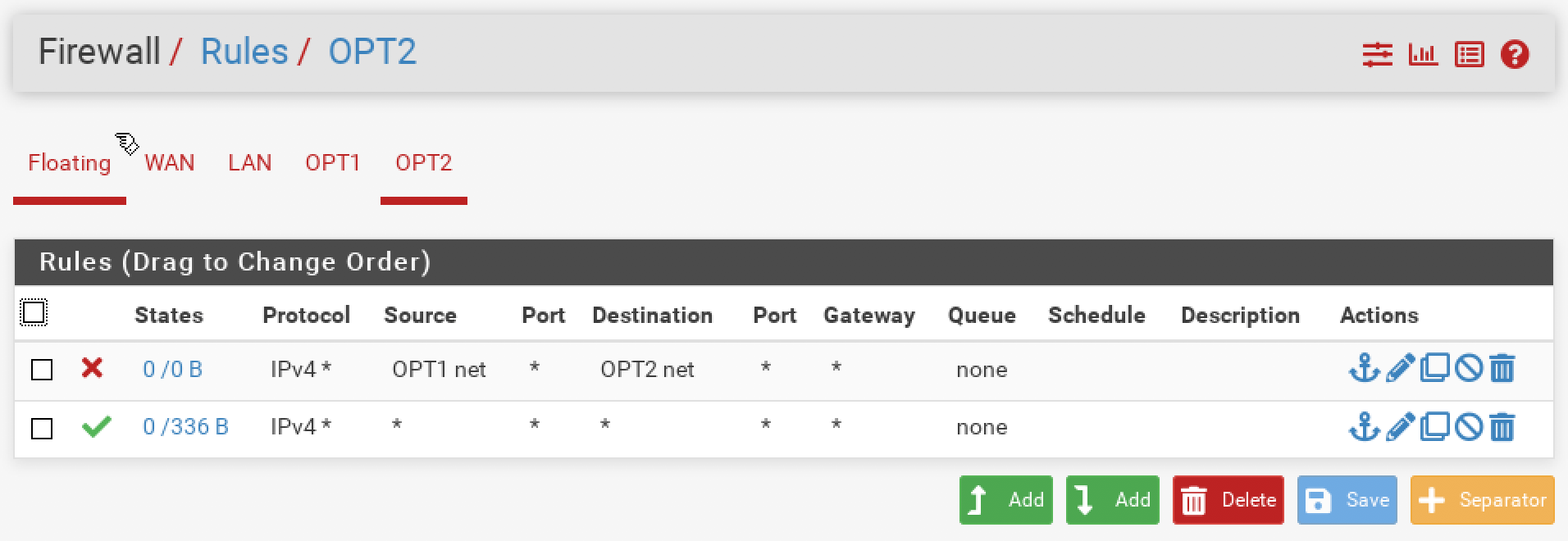
rule 1: block all traffic from OPT2 net to OPT1 net
rule 2: block all traffic from OPT1 net to OPT2 netbut nothing changed. All the hosts on the first net can ping the hosts on the second net.
Where is my error? How can fix this behaviour and permit to reach only the printers on both the networks?Could you please help desperate man? :)
Thank you in advance,
Mauro -
@mauro-tridici help if you actually show your rules on these interfaces.
If you want block opt1 from taking to opt2, this rule would go on the opt1 interface, yes top down, first rule to trigger wins, no other rules evaluated.
To stop opt2 from taking to opt1 the rule would go on the opt2 interface.
Also any existing state would allow your ping.. So if you ping something from say opt1 to opt2, and then put in a rule blocking it. The state could still be there allowing it. So you have to wait til the state timesout, or you kill it.
Also do you have any rules in floating that could be allowing the traffic, those are evaluated before the interface rules.
-
@johnpoz thank you for your support, I really appreciated it.
Unfortunately, I'm still having the same problem.
I added the block rule to each OPT interface and I reset the states, but nothing changed. Any hosts on OPT1 can ping the hosts on the OPT2.Please, take a look at the attached screenshots.
I also tried to change the second rule on each interface from ANY to ANY to WAN net to ANY. But in this way ping from hosts to 8.8.8.8 has been blocked also.
Any other idea?
Thank you,
Mauro -
@mauro-tridici
No, you misunderstood, what @johnpoz tried to suggest.
You have to put the rule on the incoming interface.I.e. on OPT1:
source: OPT1 net
dest: OPT2 netand on OPT2
source: OPT2 net
dest: OPT1 net -
@viragomann fantastic! now it works like a charm :) many thanks to all of you.
Anyway, I didn't understand the "logic" or how the rule works.
I read that firewall rules block the incoming traffic and that the rule should be created starting from this point of view.But, if I try to translate the current rule, I obtain the following:
"on interface OPT1, all the traffic generated by OPT1 network hosts should be blocked on interface OPT2"
Instead, before and in my mind, I was thinking:
"on interface OPT1, block all the incoming traffic generated by OPT2"
What is the logic that I should consider for the next rules I will create?
Sorry, I'm a newbie and I'm trying to understand how to think and set the firewall rules in the future.
Thank you for your patience.
Mauro -
@viragomann I forgot to ask you if there is a web page where I can find this kind of information. I read. the official documentation, but I'm still confused and something is not clear to me. Sorry
-
@mauro-tridici said in OPT1 and OPT2 are two networks with different VLANs but I can ping hosts on both the networks:
But, if I try to translate the current rule, I obtain the following:
"on interface OPT1, all the traffic generated by OPT1 network hosts should be blocked on interface OPT2"No, "on interface OPT1 block any protocol from OPT1 network which has the destination OPT2 network".
As mentioned rule have to be set on the incoming interface, no matter if it should block or pass traffic.
I forgot to ask you if there is a web page where I can find this kind of information. I read. the official documentation, but I'm still confused and something is not clear to me. Sorry
The Netgate docs are very good in my opinion. The Firewall chapter describes the behavior in a short and understandable manner and give some examples.
Also check out Ordering of NAT and Firewall Processing. -
@viragomann thank you very much for the time you spent for my problem.
I'm going to read the documentation carefully :)
Kind Regards,
Mauro -
@mauro-tridici yeah I am with @viragomann the docs are concise and to the point.
It seems to come up quite often where users put rules with the source being something other than the network the interface is connected too..
I just fail to comprehend why there is confusion like this... How would opt1 ever be the source IP of traffic entering the opt2 interface into pfsense from the opt2 network? Its an impossibility..
The only possible source into the opt2 interface is opt2 network..
Sure you could have other traffic, if you had downstream networks and opt2 was a transit connection. But its just plain impossible for source to be opt1 or lan, etc.
-
@johnpoz many thanks again and sorry for my misunderstanding.
Now, with your and viragoman help, everything is more clear.
Have a great day,
Mauro -
@johnpoz sorry to bump this topic
I just want to say that in my opinion most people will think as @mauro-tridici ... me included , in my mind the configuration in his screen captures make sense and are logic even though they are wrong.
I don't know if the docs make it clear on how to think about where to put the firewall rules, or i'm just dumb when it comes to networking and/or my logic/thinking is messed up. The multitude of topics about misplaced firewall rules on this forum should raise a question or two.
Clearly there are many people who get this wrong so that "click" or "aha, i get it" moment is missing.Hopefully somebody will come up with a better explanation and we will be eternally grateful :)
-
@aduzsardi the only way that makes sense is not understanding what a source or a destination is or what flow of the traffic is. That rules are evaluated INBOUND.. Not outbound..
There are many a thread where we go over this.. When would you like to stop traffic, before it enters and flows across your firewall, or on its way out..
The only time such a rule makes sense
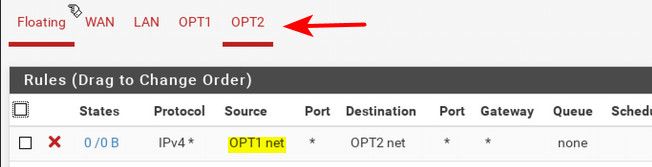
If you were trying to stop traffic from leaving the firewall..
https://docs.netgate.com/pfsense/en/latest/firewall/fundamentals.html#stateful-filtering
traffic need only be permitted on the interface where it enters the firewall.https://docs.netgate.com/pfsense/en/latest/firewall/rule-methodology.html#rule-methodology
rules on interface tabs are applied on a per-interface basis, always in the inbound direction on that interface. This means traffic initiated from the LAN is filtered using the LAN interface rules. Traffic initiated from the Internet is filtered with the WAN interface rules.
In the above rule shown, you would be blocking traffic as it exits the interface into the opt2 network. So the firewall already created a state, and had to process the traffic - just to block it?
Its better to stop the traffic before it enters the firewall, before it had to be processed and a state created. So if you do not want opt1 talking to opt2, you block that traffic at opt1 interface.
I have used this analogy before. If you wanted to prevent someone from getting to your back yard. Would you stop them at the front door before they even entered the house. Or would they just walk in the front door, track mud all over the clean floors in your house, and then just as they were trying to step into the backyard you would stop them at the back door?
So now you have to go clean up all the mud they tracked in, or would it be better to check that their feet are clean, and you know them and want them in your backyard before they even enter the front door ;)
Now if you want extra or special type of rules, you can add them in the floating tab in the "outbound" direction. Maybe you don't want anyone allowed into the master bedroom, but you already let them in the front door because they can go everywhere else, and you didn't want to check if they were going to master bedroom when you let them in..
This methodology is common across really any stateful firewall.. You filter traffic before it enters the firewall, since if you let into the firewall the firewall had to process it and create a state..
Is the issue the users are reading the docs and not grasping it.. If so then yes it needs to be explained better or with simpler terms. Or is it they are just not reading them at all. If the first - maybe we could add pictures or something explaining the concept better.
In my experience most users don't read the manual.. I know how this TV works, and sure they might plug it in, hook it up, get logged into "netflix" etc.. But only go to the manual when something is not working, and if they can not figure it out. Or just call support ;) because they don't want to read the manual ;)
I do this myself, pretty much everyone does.. I know how my new fridge works ;) But this new one connects to wifi.. I had to look in the docs for how to do that, sure I could of clicked on the little wifi button hoping it connected.. But in the docs it tells me hold it for 3 seconds until it starts flashing, and have to use the app on the phone and connect to the new wifi network the fridge creates to be able to tell it what wifi and psk to use to connect my network, etc..
If I didn't need/want to use the wifi function there would of been no need for me to reference the manual. Which is the case with many a post here.. Out of the box pfsense is pretty easy to use.. You plug it in, follow the bouncing ball guide as you access its web interface, click a few buttons and hey internet works.
Only when you want to start doing something outside that use case would they "need" to reference the manual.. Which did they do?? Or did they just post here when it didn't actually work.. Like the wifi button on my fridge ;)