How to set the same VLANs between the switch and PfSense
-
Oh ok, I think I was a bit drunk, if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such, I think it works in this way as any other router :D , I tested it in the LAN just in case.
-
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
I could give a screenshot but it's really what I described.
What you described doesn't make any sense - lan5 could not or would or could ever be source of traffic into the wan interface..
-
In response to Steve -->
Is it not already disabled by default? Please look my message above.If you talk about the same LAN instead (for example LAN2 to LAN2), I don't want the communication between the devices on the same LAN, but I also don't want the communication between different LANs for now.
At the moment, due to no rule in place I think it's DENY ALL between LANs, I need to check between the devices of the same LAN.In any case, I'll configure such things in VLAN, where below that VLAN there will be a switch, which by itself will have the client isolation rule enabled.
I need to check what I need to do on the PfSense firewall about it... -
@jt40 said in How to set the same VLANs between the switch and PfSense:
I don't want the communication between the devices on the same LAN
pfsense has nothing to do with communication between devices on the network (lan) Pfsense is a router, it routes and firewall traffic between networks. It is not involved in devices talking to each other on the same network, only for traffic wanting to leave a network.
If you don't want devices talking to each other on the same network you would need to do that at your switch - lookup up a private vlan. Or via wireless this is often called AP or Client isolation.
https://en.wikipedia.org/wiki/Private_VLAN
https://support.denon.com/app/answers/detail/a_id/3746/~/wireless%2C-ap-or-client-isolation
-
@jt40 If you allow LAN2 to Any, that will allow to LAN5 as well. LAN5 is "any."
You can't do much about devices on the same network communicating. That normally is handled by a switch and those packets don't even get to the router.
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such
- Rules are evaluated from the top down.
- The first rule which matches is used and no further rules are evaluated.
- If no entered rules match the the packet is dropped / blocked.
So if no rules are entered every packet falls off the bottom of the rule list and is blocked.
I find it simplest to order my rules as
- Allowed local traffic
- Reject other local traffic
- Allowed Internet traffic
- Block other Internet traffic
An example of which for LAN2 is:
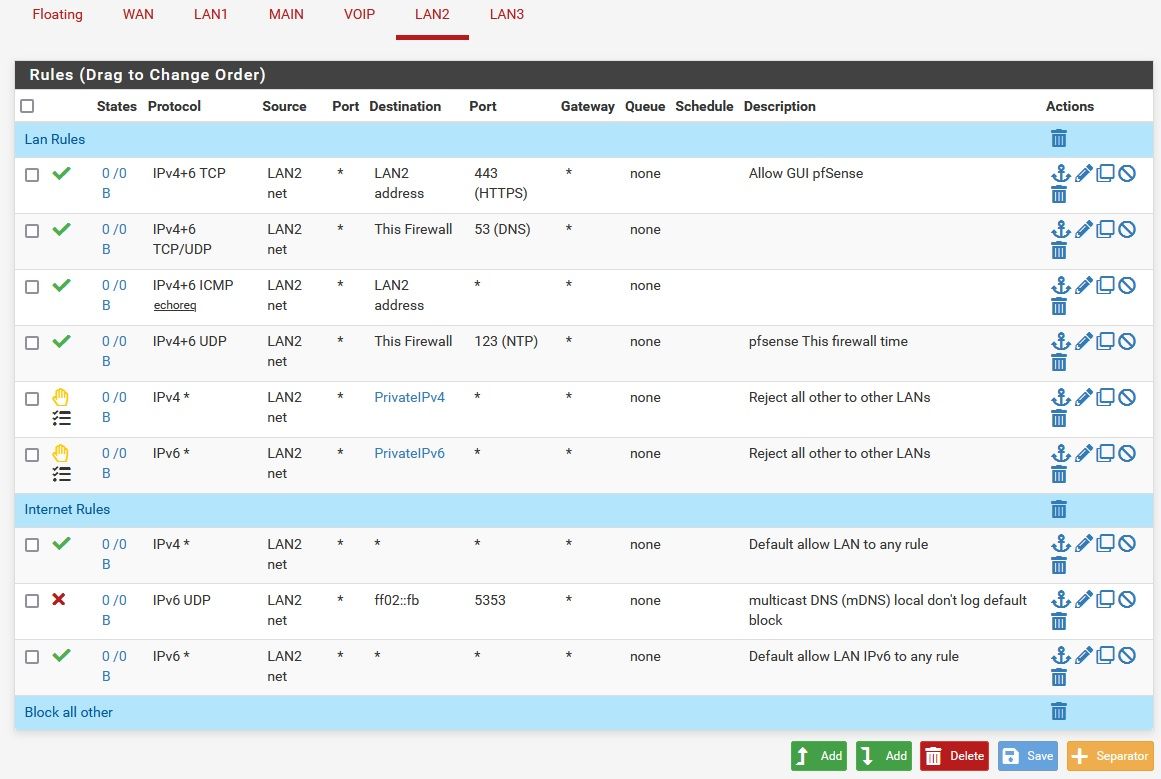
-
@jt40 said in How to set the same VLANs between the switch and PfSense:
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
I am with Akismet on this one.

-
@bob-dig said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
This Askimet spam filter is against me, I didn't post any link and I still can't write the message I need :D
I am with Akismet on this one.


@patch said in How to set the same VLANs between the switch and PfSense:
@jt40 said in How to set the same VLANs between the switch and PfSense:
if there is no rule then is DENY ALL, so all the INBOUND traffic is DENY currently because I have no rule as such
- Rules are evaluated from the top down.
- The first rule which matches is used and no further rules are evaluated.
- If no entered rules match the the packet is dropped / blocked.
So if no rules are entered every packet falls off the bottom of the rule list and is blocked.
I find it simplest to order my rules as
- Allowed local traffic
- Block other local traffic
- Allowed Internet traffic
- Block other Internet traffic
An example of which for LAN2 is:

Thank you.
I see that you have set also the REJECT rules, but my point is, is it not by default?
Precisely, I would expect DROP as by default, not REJECT.Look at the simplest case, if I have a rule do to something, I expect that rule to be evaluated.
If the device asks for something else and the rule is not present, I expect the packets to be dropped automatically...
This is also the easiest way a firewall can work to make my life easier :D -
@jt40 the default is drop, ie just block..
But internally it is sometime better to reject vs just drop. I want to let my internal client you can not go there right away - via a reject. Vs letting it bang its head with retrans trying to figure out why he is not getting an answer.
Externally no you would almost never want to send a reject to something out on the internet.. But internally - if your going to on purpose prevent something like vlan x from talking to vlan y.. its better to just let them know - hey stop trying to go there ;)
If the device asks for something else and the rule is not present, I expect the packets to be dropped automatically...
That is how it works.. If there is not allowed, then traffic dropped gone over this how many times already.. But yet to see a picture of your rules.. You have been told multiple times that pfsense will not route traffic unless there is an allow rule.
If the spam system is preventing you from uploading a picture - then link to it somewhere else, use something like my picture is here somewhere . domain . tld / whatever even if you have to but. But what I can tell you yet again yes default is deny. No rule to allow, traffic is dropped.
If you want to actually see it - then look at the full rule set. Since this default deny is not shown in the gui..
[21.05.2-RELEASE][admin@sg4860.local.lan]/root: pfctl -sr | grep "Default deny rule" block drop in inet all label "Default deny rule IPv4" block drop out inet all label "Default deny rule IPv4" block drop in inet6 all label "Default deny rule IPv6" block drop out inet6 all label "Default deny rule IPv6" [21.05.2-RELEASE][admin@sg4860.local.lan]/root: -
P Patch referenced this topic on
-
P Patch referenced this topic on