Changes made to default LAN affects every VLAN. Some clarifications needed.
-
Hi all,
I've got my networks up and running exactly how I want it, however, I am starting to worry I have misunderstood how the default LAN works and therefore potentially misconfigured some rules.
I decided to leave all my networking gear on the default LAN and then create VLAN's to split up all the other devices in my network. I have firewall block rules and inter-vlan block rules (RFC1918) configured on all the VLANs to stop them from getting to the firewall and other networks. Testing shows this all works which is great.
However, after messing with the default LAN rules, I decided to lock it down a bit as I didn't want those default Any > Any rules considering my switches etc. were on that network. As part of my test, I decided to remove the DNS rule to see if the LAN affects anything else. After saving, I realised every VLAN on my network went down in the sense that they couldn't resolve hostnames. This makes sense because I removed the DNS rule but it also doesn't make sense because all my VLANs have their own DHCP servers specifying my Pi-Hole DNS server.
So why are my VLANs going down when I make changes to my LAN rules, when they have their own network, DHCP server and upstream DNS. I feel like I am over complicating things so could really do with some clarification.
Is the default 'LAN' a logical or physical interface? I've read the documentation but unfortunately I need someone to dumb it down for me, as the LAN uplink and the LAN1 still confuse me too. LAN1 should be my physical port on the firewall (Netgate 2100) and the LAN uplink should be the logical right? I thought VLANs were their own network so why would changes to the LAN affect the other VLANs?
-
@3ronic said in Changes made to default LAN affects every VLAN. Some clarifications needed.:
I decided to lock it down a bit as I didn't want those default Any > Any rules considering my switches etc. were on that network
Huh? So you were trying to block your switches from going to the internet?
Love to help you but your going to need to show us your rules.. What vlan/network does your pihole sit on? Where does the pihole point to get its dns so it can find what clients are asking it for, etc.
with the 2100, all the lan ports are in the lan (these are switch ports).. Your going to have to show us how you configured that if you created vlans, etc. And how you have stuff actually connected to the 2100.
-
@johnpoz See my rules below:
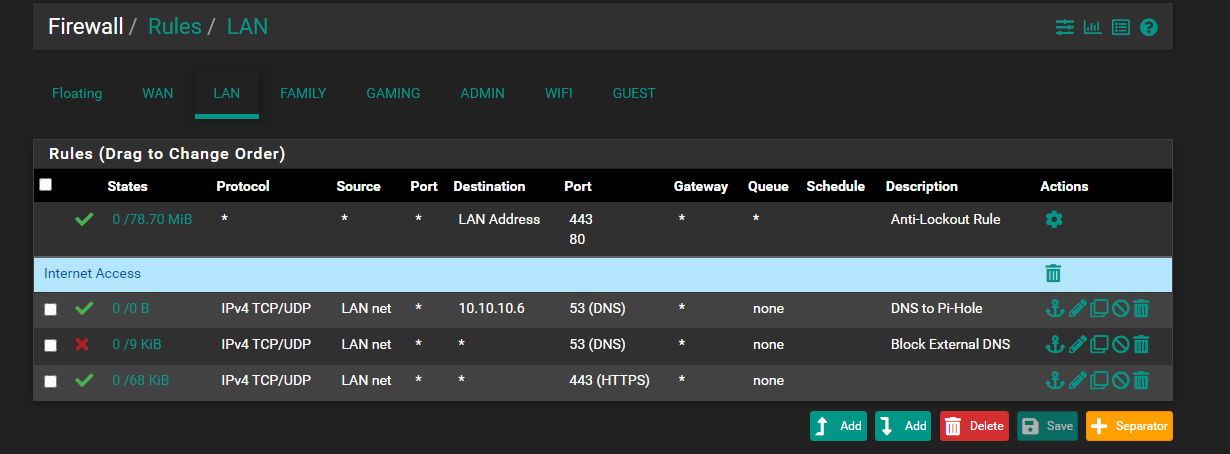
Default LAN 10.10.10.0/24:

VLAN 50 - 10.10.50.0/24 (Isolated network for Family):
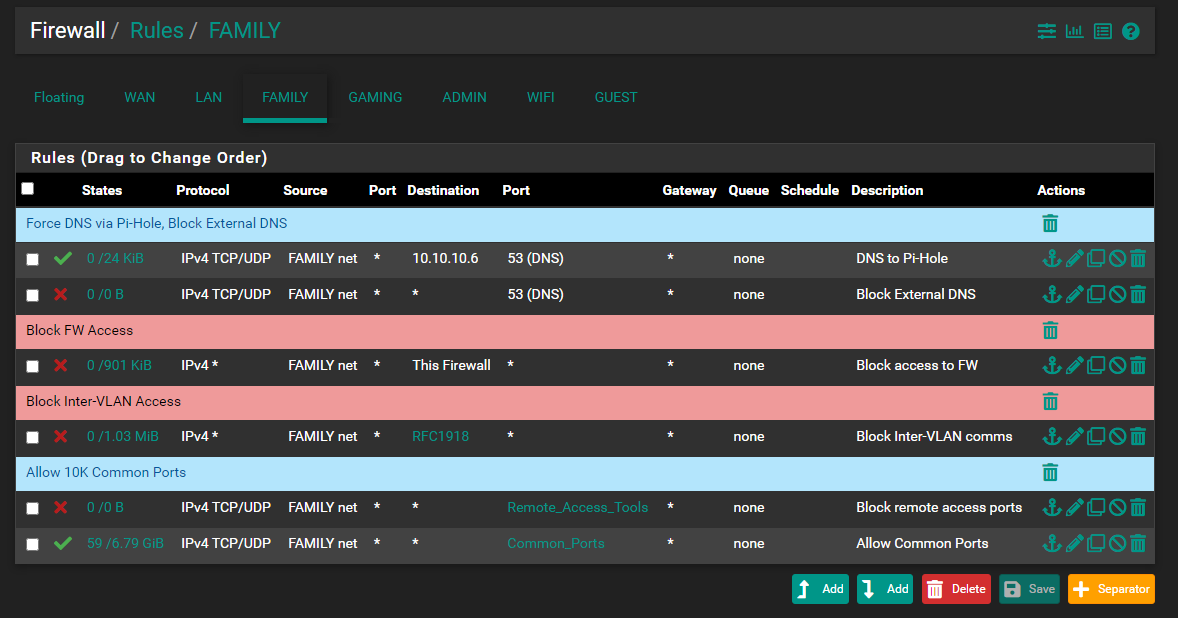
VLAN 69 - 10.10.69.0/24 (Admin VLAN for managing everything):

VLAN 80 - 192.168.80.0/24 (Guest network)

WAN Rules left as default to block everything incoming.
Pi-Hole (10.10.10.6) sits on the Default LAN network (10.10.10.0/24). All the VLANs have a rule to force DNS to the Pi-Hole and block external DNS.
Pi-Hole upstream DNS is Cloudflare. Conditional forwarding set to my pfSense so Pi-Hole can forward the requests to my DHCP server.

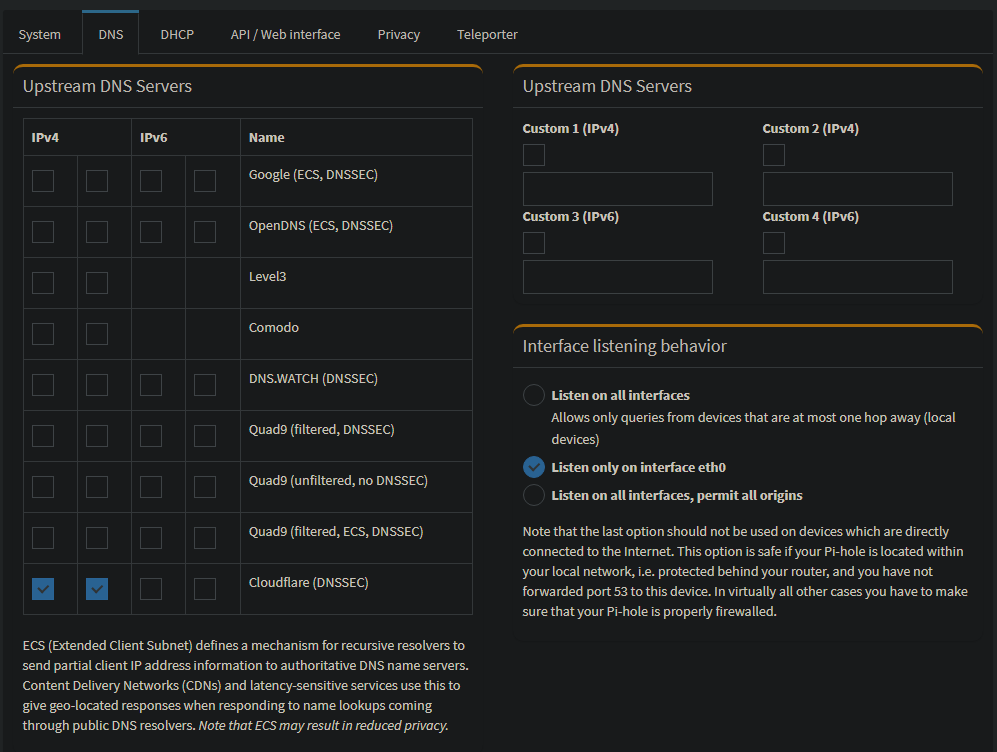
DNS resolver and forwarder disabled in pfSense as I am having Pi-Hole do my DNS.Is it worth creating a 'Management' VLAN and sticking all my switches, Pi-Hole and AP's there and then leaving the LAN with those default Any>Any rules?
I wasn't trying to block internet to the default LAN, I just decided to test DNS rule to see if it affected the other VLANs and it did. But the plan isn't to take internet access away from the switches sitting on the LAN. It was just for testing purposes. Blocking DNS also blocked DNS on my VLANs even though they have their own DNS servers configured. This is where I am confused.
Do the VLANs route to the LAN? I always assumed they had their own gateway, and if DHCP was set up properly they would also get a DNS server (Pi-Hole) in my case.
-
@johnpoz And here is my VLAN and switch config for the pfSense. I followed a couple Youtube tutorials that did the same.


I tried configuring discrete ports following the guide on official Netagte documentation but that messed up a few things for me so decided to keep it simple.
-
@3ronic ok first thing these lan rules don't make a lot of sense to me.

Rules are evalutated top down, first rule to trigger wins..
So you have a rule above that say anything anything can go anywhere.
So when do you think that specific lan net rule would trigger for your common ports..
Do you have networks downstream of lan net? Also why are you not allowing icmp?
This jumps out as pointless as well

You have a rule that says admin net can go anywhere all protocols, but then below that which would never trigger you allow icmp? The rule above that already allows that..
But at first glance I see nothing that pops out that should cause issue, rules look ok overall. Other than stuff like above.. Maybe rules were added for troubleshooting and other rules left in place? I think this might be the case because your rules that are below a rule that would already allow the traffic show some traffic on them. So it seems the rules above them were added after the fact.
Your vlan setup look ok, depending on the switch connected to lan1 port. But your tagging your vlans, and lan is native (untagged).. Which a typical setup.
You seem to have rules on your other vlans that allow access to to your pihole IP, and then your pihole would go out the lan rules and talk to clouldflare dns.. This all seems normal.
One thing that such a setup would have issue with resolving anything on your local network. But if your not running unbound or forwarder on pfsense, it wouldn't resolve anything anyway. The cond forwarder you have setup would try and resolve 10.10.10/24 PTR queries from 10.10.10.1 - but if unbound or dnsmasq not running - those would never resolve anyway.
So I could if your trying to resolve local records your going to have a hard time. A better setup might be to forward pihole to pfsense so your local stuff could be resolved. Or you need to make sure pihole can resolve all your local stuff.
But from a quick glance I don't see anything should should prevent say the internet from working..
Your client wants to resolve say www.google.com, it if your dhcp is set correctly would ask pihole, pihole would forward this request to clouldflare.. It gets an IP, and then your client goes to www.google.com through pfsense on its vlan. So unless say 80/443 was blocked by your remote access tools on say family net or not included in the common ports rule.. That should work just fine.
Do the VLANs route to the LAN?
No they would route to pfsense IP on the vlan, unless you modified dhcp to hand out some other gateway IP, which if not on the vlan wouldn't work, etc. By default dhcp server on pfsense running on a vlan or any network would hand out its interfaces IP as the gateway.
Nothing jumps out at to me as smoking gun here.. What exactly is not working?? Can your clients not resolve? A problem could be your browser is trying to use doh.. But I don't see anything that would actually stop that, unless in remote access tools alias for 443, or your common ports do not include 443.. Are you sure your clients are pointing to the pihole IP for dns - can they resolve, simple test would be go to a command line on a client in one of yoru vlans.. Use nslookup or dig or host, your fav dns tools and try and query something. Does the query work for say www.google.com?
Generally speaking I don't see anything wrong with those rules, vs maybe some tweaking of the stuff I pointed out above.. But that could of been just you adding rules to troubleshoot?
Are you clients trying to use IPv6? That your not allowing? Even if they were they should fall back to ipv4.
BTW - your not running say IPS or Proxy packages are you? Also I take it you have no rules on the floating tab?
edit: oh wait I just noticed the full details of the cond forwarder - that seems ok for local lan, coming from 10.10.10/24 but this wouldn't work for your vlans.. But again if your not running unbound or dnsmasq on pfsense, it wouldn't be able to resolve anything anyway.. But again that would only matter for local stuff, not something like internet domains.
-
@johnpoz Yeah the LAN rules were left whilst I was doing some troubleshooting so need to clean them up a bit.
No they would route to pfsense IP on the vlan, unless you modified dhcp to hand out some other gateway IP, which if not on the vlan wouldn't work, etc. By default dhcp server on pfsense running on a vlan or any network would hand out its interfaces IP as the gateway.
DHCP does not specify a different gateway, although the default gateway I get for each of my VLANs is not the IP of my pfSense (10.10.10.1). This is normal though as these are their own networks. See my admin VLAN which I created and gave the gateway 10.10.69.1 on the network 10.10.69.0/24.
Are you clients trying to use IPv6? That your not allowing? Even if they were they should fall back to ipv4.
No, although my LAN is set for IPv6 with 'Track Interface'. I couldn't disable this option as it says DHCPv6 is enabled and Router Advertisements Sever is active. Not sure if this could cause problems.
BTW - your not running say IPS or Proxy packages are you? Also I take it you have no rules on the floating tab?
No IPS or proxy packages. And no rules in floating.
I'll try to explain what I did when my VLANs couldn't resolve hostnames.
So right now, if I were to look up google.com I get the following results:

This is to be expected but sometimes I do get one or two timeouts before it gets the address of google.comNow if I then add a DNS rule on LAN to just my Pi-Hole and exclude all other external DNS servers (same rules as my VLANs), it brings down all the VLANs ability to resolve hostnames. I assume I am doing something extremely stupid here?

Do you think it's worth creating a management VLAN and sticking all my switches and the DNS server on, that way its not on the default VLAN 1?
-
@3ronic said in Changes made to default LAN affects every VLAN. Some clarifications needed.:
Now if I then add a DNS rule on LAN to just my Pi-Hole and exclude all other external DNS servers (same rules as my VLANs),
Well yeah - pihole is trying to ask cloudflare for IP address of google - you just blocked that.. So nothing on any of your networks would be able to resolve anything.. Because your blocking 10.10.10.6 from going to clouldflare..
Such a rule on lan makes not sense anyway allowing lan to talk to 10.10.10.6 stuff on lan doesn't route to pfsense to talk to stuff on lan.. So that rule is pointless, but what is a problem is your blocking all other dns so pihole can not talk to clouldflare.
As to getting timeouts now and then to cloudflare - that has something to do with your connection to them, or them, etc. It could be something as simple as your asking for something that is not cached by them, and it takes a bit for them to resolve it..
If you want to stop your lan from talking to other dns - then you would need at min a rule to allow your pihole to talk to clouldflare IPs.
If you want to disable IPv6, turn off the dhcpv6 and and RA, then you can change the tracking setting.