Outbound NAT?
-
Hello,
I spent days trying a lot of possibilities and failed miserably. I am not sure if what I am trying to achieve is even possible.
Scenario is, PFsense with:
WAN IP and multiple LANsOne of the LANs is cut off from the internet, isolated management network. Pfsense is not the gateway for this LAN, it is a client. IP Address 192.168.1.9
I want to achieve access from this isolated LAN access ONLY to SMTP and NTP service on a public WAN IP.
So it would look like this:
192.168.1.10 (device that needs ntp and smtp access) ----> 192.168.1.9 (Pfsense) ---NAT--> 4.4.4.4 (NTP, SMTP server).
So the configured SMTP and NTP server address on the device (192.168.1.10) would be 192.168.1.9 (the Pfsense), Pfsense would NAT this traffic (SMTP TCP port 25 and NTP UDP port 123) to the Server on WAN IP 4.4.4.4.
Is this possible?
-
@gatenet
Yes, but not by outbound NAT. You need a simple port forwarding rule on the internal interface for 192.168.1.9 NTP and SMTP to whatever public server you want. -
^ yeah you could setup pfsense to forward ntp/smtp that hits pfsense from this 192.168.1.10 to where you want those to go. And then hit the 1.9 pfsense IP from this device vs whatever the normal public IPs of these services are.
Or you would need to setup a host route on this device that tells it to use pfsense when it wants to go to the public IPs of your ntp and smtp servers vs its normal gateway.
-
@viragomann Tnx for the reply.
That was the first attempt. But there must be some trick, since it doesn't work.
for the NAT rules I tried source "LAN interface net", "LAN interface address", "Network": 192.168.1.1/24 and the device directly "Single host or alias": 192.168.1.10.
At the same time tried destination any, this firewall (self) and 192.168.1.9.
Setting TCP/UDP 25,123 respectively for each rule.
Redirect target IP is 4.4.4.4
Redirect target port is either 123 or 25 for each of the rules.
When testing this nothing works. I even spun up a test linux machine on this LAN subnet, using telnet and nmap to test, these two ports on 192.168.1.9 (the pfsense) are completely dead.
Any hints on this?
Cant find anything useful in the logs on pfsense or the time/mail server 4.4.4.4.
-
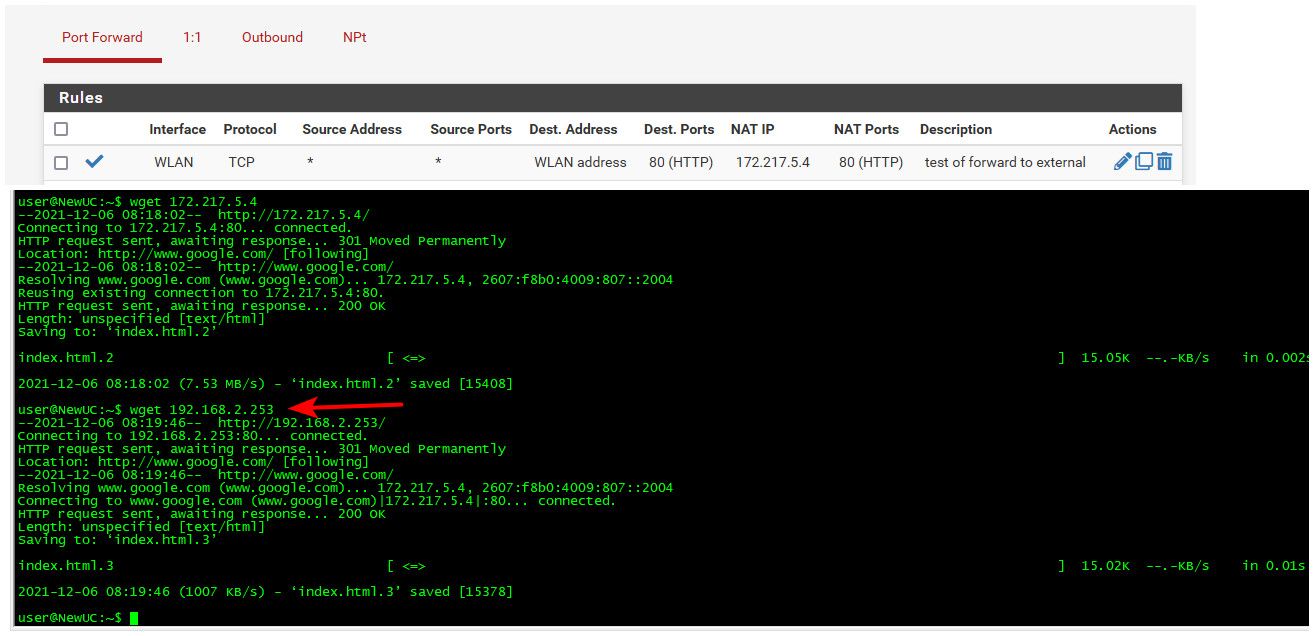
@gatenet here you go. an example.. I redirect pfsense IP 192.168.2.253 to ip of www.google.com
You can see in my first test going to the actual IP, and then my second test going to the IP of pfsense was directed to the www.google.com IP.
-
@johnpoz The devices on this isolated subnet are quite dumb with very little configuration options unfortunately. But in the end I might just change the gateway to the pfsense if all else fails...
-
@gatenet I just showed an example of how to do a port forward to direct traffic to some external IP. So your clients are so dumb you can not access pfsense IP in place of where they want to go..
If that is the case then setup a host override on dns to point whatever fqdn they are using to resolve to pfsense IP.
-
I tired this now again, this was one of my first attempts. Doesn't work.
I get Connection Timeout on telnet test.
If I do port test from Diagnostics - Test Port
connection fails if I select this LAN, connection succeeds if I select WAN.
Somehow this NAT rule does nothing :/
-
@gatenet
When you forward SMTP packets from pfSense IP 192.168.1.9 to 1.1.1.1 (or any other), pfSense re-translates the source IP in respond packets back to 192.168.1.9.
So there is no need to set specific routes or gateway on the client. -
@gatenet are you trying to telnet to some smtp server? From an ISP.. through a non isp connection (pfsense connection).
Its quite possible this is blocked, or also possible that your pfsense isp blocks outbound on 25 completely.
I showed you how to do the rule, if its not working then you either did not set it up correctly what what your wanting to do. Or there is some other connection sort of issue that is different from isp of pfsense and the isp connection of the other gateway this device is using, etc.
edit: what is the exact ip of this server your tying to test to? PM it to me if you want to not make it public. But pretty sure its not 4.4.4.4 ;)
-
@gatenet said in Outbound NAT?:
If I do port test from Diagnostics - Test Port
connection fails if I select this LAN, connection succeeds if I select WAN.
Somehow this NAT rule does nothing :/So possibly you're missing the outbound NAT rule for that subnet. However, this should have been added automatically by pfSense, unless you have disabled it.
-
-
@gatenet said in Outbound NAT?:
How would I go about checking this?
What that its working - simple sniff do you see the traffic go outbound to your dest?
What are the rules on your interface, whatever your wanting to forward - still has to be able to get to the interface to be forwarded.
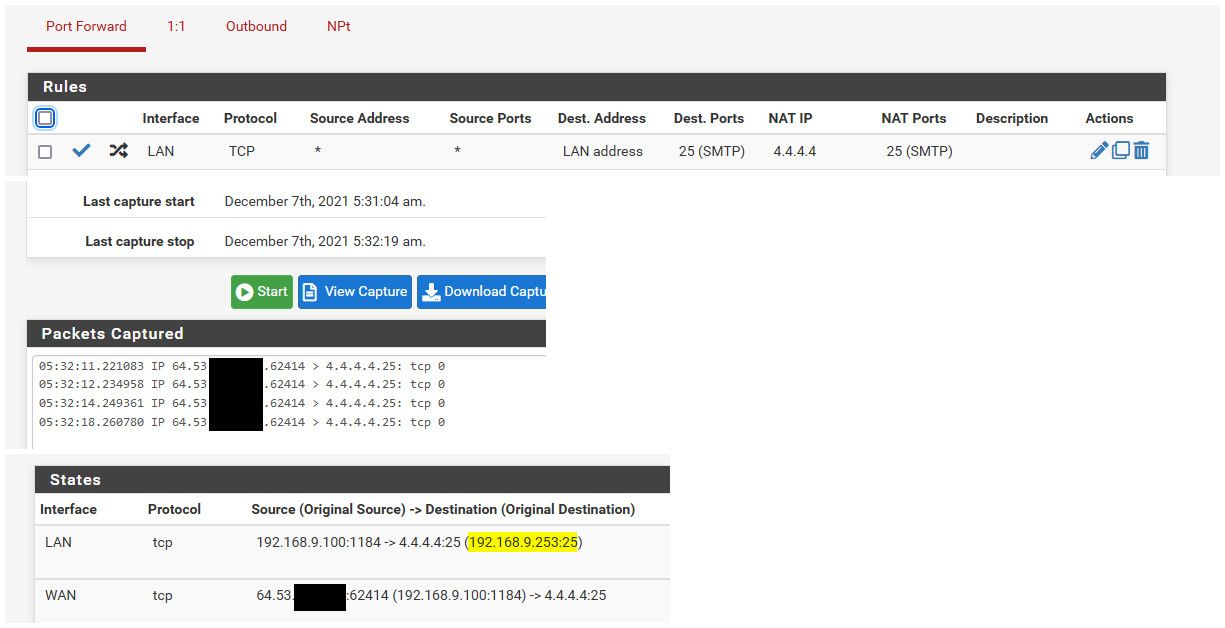
edit: here just did simple test forwarding traffic that hits my lan IP 192.168.9.253 on 25 (smtp) being sent to 4.4.4.4
So you can see from the sniff that pfsense sent that on to 4.4.4.4 on 25 from my wan IP.. It natted the traffic just like any other connection. But in the state tables you can see I actually went to 192.168.9.253
If you can not actually get where your going, or where your going doesn't want to talk back there is nothing pfsense can do about that.
-
Tnx for this. I tried and got the same results as you. Packets are captured and the state is open.
BUT, still doesn't work, the test linux machine from where I am trying to telnet to this server says just "Connection timeout".. For a test I tried a public smtp server, to avoid any possibility of issues on my mail server.
So looks like the packets go out, but the reply doesn't come back
maybe?The state says:
SYN_SENT:CLOSED 5 / 0 300 B / 0 BUpon further investigation, now on my mail server I discovered this in the firewall log on the mail server:
mailgw kernel: [14516908.918914] [UFW BLOCK] IN=ens192 OUT= MAC=00:50:56:89:99:fd:00:0c:29:2c:8b:f7:08:00 SRC=192.168.16.53 DST=PUBLICIPOFMAILSERVERHIDDEN LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=56610 DF PROTO=TCP SPT=49138 DPT=25 WINDOW=64240 RES=0x00 SYN URGP=0This is not ok right?

So in the log on the mail server I should see the WAN IP of the pfsense as the source. Not a 192.168.x.x. local address. The mail server can't return the reply to a LAN address of course...even If I allow this 192.168.16.0/24 subnet...
So something is messed up with the NAT on the pfsense, but I don't know where to start.
Or should I now NAT those packets on the mailserver back to the pfsense wan IP?
I am lost, such a basic thing became so complicated...bolded text
-
@gatenet said in Outbound NAT?:
So something is messed up with the NAT on the pfsense, but I don't know where to start.
dude I showed you exactly how to start.. Sniff on your wan - it will be clear as day if pfsense is not natting outbound traffic.
-
@johnpoz dude, sorry, I meant how to start fixing this. Are this the NAT reflection settings, Outbound NAT mode, something else in the Advanced Firewall & NAT settings. What am I supposed to do here?
:(Edit: I mean, now we know, that pfsense is not actually doing NAT? It just forwards the packet with the same source address out the wan interface.
-
@gatenet well for start - lets see your outbound nat rules.. Since this is what does the nat.
Did you alter them from auto? Are you sending out a different wan? Is the source IP downstream of pfsense, and not actually attached to pfsense?
How exactly is this client even getting to this public wan IP if not natted? This public IP must be actually on your network? Because rfc1918 are not routed over the public internet.. So if you sent data with source IP of rfc1918 while it might get to something internal to your ISP network, it wouldn't get past their network to get to your smtp server, that is showing that in the logs.. So where exactly is this server? Is it just sitting on your wan net of pfsense?
-
The outbound NAT for this interface is this, no mappings, just the automatic rules:
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24 * * 500 LAN2 address * Auto created rule for ISAKMP
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24 * * * LAN2 address * Auto created ruleI did not alter from auto. The pfsense has only one WAN.
The mailserver is a linux server with one WAN interface. Both WAN IPs (pfsense and the mailserver) are on the same /28 subnet. But this should not matter, I tested with a mailserver on a completely different public IP subnet, and the same happens.
Attached a basic diagram of the setup:
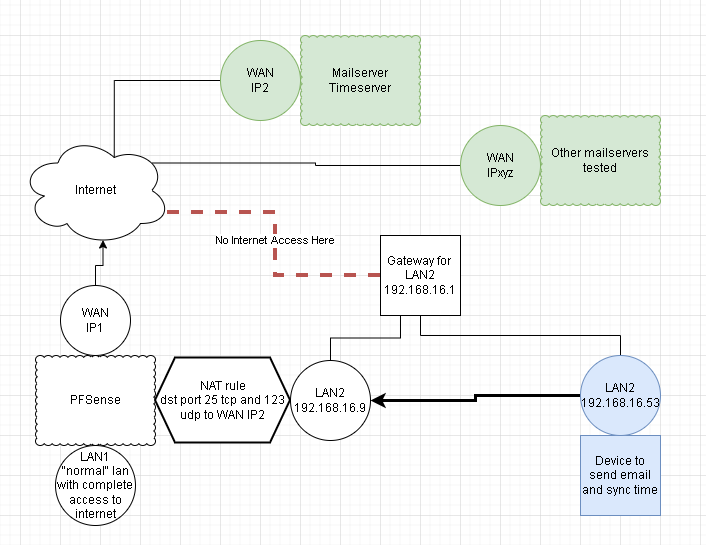
Just to clarify again here. On this client trying to send email, the server address configured for the mailserver is the LAN2 IP of the pfsense. NOT the WAN IP of the mail server. So the packets arrive from 192.168.16.53 (client) to 192.168.16.9 (pfsense) and it gets forwarded out, but pfsense should nat the packet with the source address of its WAN interface, right?
-
@gatenet said in Outbound NAT?:
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24
And where is this 192.168.16 network? If psfense sees source traffic from 192.168.16 and its allowed out, but there is no outbound nat for it, then no it wouldn't be natted.
I did not alter from auto. The pfsense has only one WAN.
If you created a gateway and route for pfsense to know how to talk to this 192.168.16 network then auto nat would of been created. But if you just altered your rules to allow for it, how would it be natted? And even if it was - how would pfsense know how to send back the return traffic without the route?
If lan 2 (192.168.16/24) is interface on pfsense then it would be listed in the auto outbound nat rules.
-
-
- LAN2 address
-
That looks like you created lan2 as a wan for pfsense? You put a gateway on it, which is wrong.
-
-
Well that did it, I just removed the gateway from the LAN2 interface, and now it works. I would never think of that.
Thank you so much for this. I already wanted to give up and just restart everything from scratch :)