LAN Access to OpenVPN Clients without Site-to-Site
-
Hi all, long time listener first time caller
I'm having a bit of trouble configuring a specific OpenVPN setup I'd like to employ on my network. The setup is as follows:
- PfSense as OpenVPN server
- Clients connect to the server, but cannot access any local networks
- Local networks can ping + access the clients and the clients only (there is no 'remote site' behind the client to be routed - only the tunnel IP allocated to the client)
The application here is to deploy a handful of backup servers in relatively untrusted locations. These backup servers start an OpenVPN connection on boot, making them visible to the primary server but remaining cut-off from the internal network.
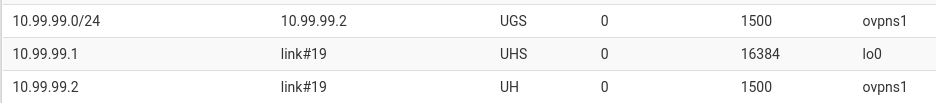
The primary issue here is that PfSense is routing the entire tunnel subnet (10.99.99.0/24) to the first client address (10.99.99.2), regardless of topology (subnet/net30). If a client is connected at 10.99.99.6, it is unroutable from the Pf box. This limits only a single pingable client at a time on 10.99.99.2, which is not desired for my use case. I'm using client specific overrides to allocate the tunnel IPs to each client.
Please find below the relevant entries in the routing table.
Both the server and client override configs only specify the tunnel IP range (as well as the local accessible range for the server, with deny rules in the firewall for the backup server clients).
Thanks in advance
-
@jaci said in LAN Access to OpenVPN Clients without Site-to-Site:
PfSense as OpenVPN server
Also as default gateway?
The primary issue here is that PfSense is routing the entire tunnel subnet (10.99.99.0/24) to the first client address (10.99.99.2), regardless of topology (subnet/net30). If a client is connected at 10.99.99.6, it is unroutable from the Pf box. This limits only a single pingable client at a time on 10.99.99.2, which is not desired for my use case.
Normally there shouldn't be any issue. Since all the OpenVPN clients are within an L2 which is connected to pfSense, there is no need for any route at all.
If pfSense is the default gateway and you have a proper firewall rule on the LAN, LAN devices direct traffic for 10.99.99.0/24 to pfSense LAN interface. pfSense passes it to OpenVPN and OpenVPN will know, how to forward the packets to the clients.
Both the server and client override configs only specify the tunnel IP range (as well as the local accessible range for the server, with deny rules in the firewall for the backup server clients).
The CSO overrides the server config, therefor it's called "override".
As long as there is no pass rule on the OpenVPN interface, no access will be allowed anyway.
If you have an interface assigned to the OpenVPN server, remember that the OpenVPN tab is an interface group including all OpenVPN instances. Rules on this tab will have priority over interface tabs.