Allow any to WAN interface only
-
Hi all,

A simple question about Firewalling as I don't understand one thing.
The question was probably already answered before but I can't find any info.Is there a way to "Allow Any from LAN1 subnet to any on the WAN interface"?
I know how to "Allow Any from LAN1 subnet to any" but since it is not restricted just to the WAN interface, it will allow all the machines on LAN1 to access all the others networks and I therefore have to think to close manually the access to all others networks.
I find it dangerous as we might forget to close something.Thanks,

David
-
@djacquens said in Allow any to WAN interface only:
Is there a way to "Allow Any from LAN1 subnet to any on the WAN interface"?
When you create a new vlan/network - there are no default rules like the default lan interface of any any.
You will need to create the rules you want on this new interface. Sure you could create an any any rule like default on lan for this new network or you could just create the rules you want.
If you just create lan1 net to wan net, that is all that would be allowed.
edit: keep in mind, wan net is not "internet' if you allow traffic to wan net, that is all that will be allowed.. You wouldn't be able to access internet.
-
Thanks @johnpoz
I am still slightly confused.
I want on my new lan interface to access internet and nothing else.
As you said, I tried giving access to "WAN net" but this did not give me access to the internet.What rule am i supposed to set?
Thanks,
David
-
@djacquens the best solution to block a vlan/network you have created from accessing other stuff on your network but allowing internet would be something like this
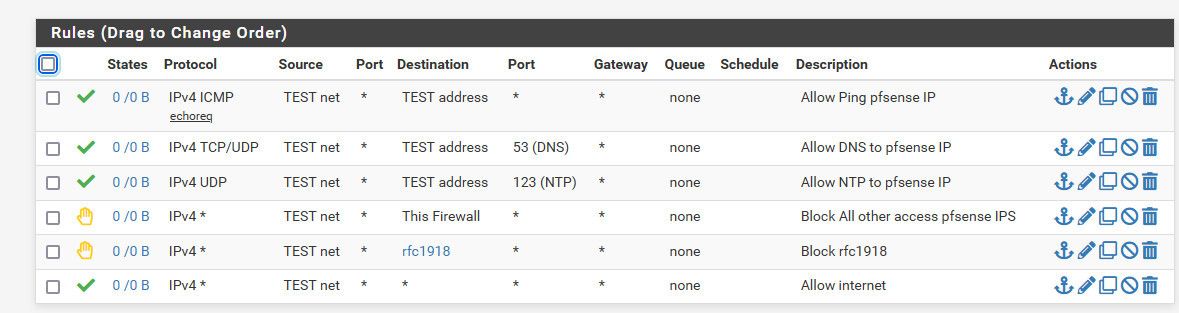
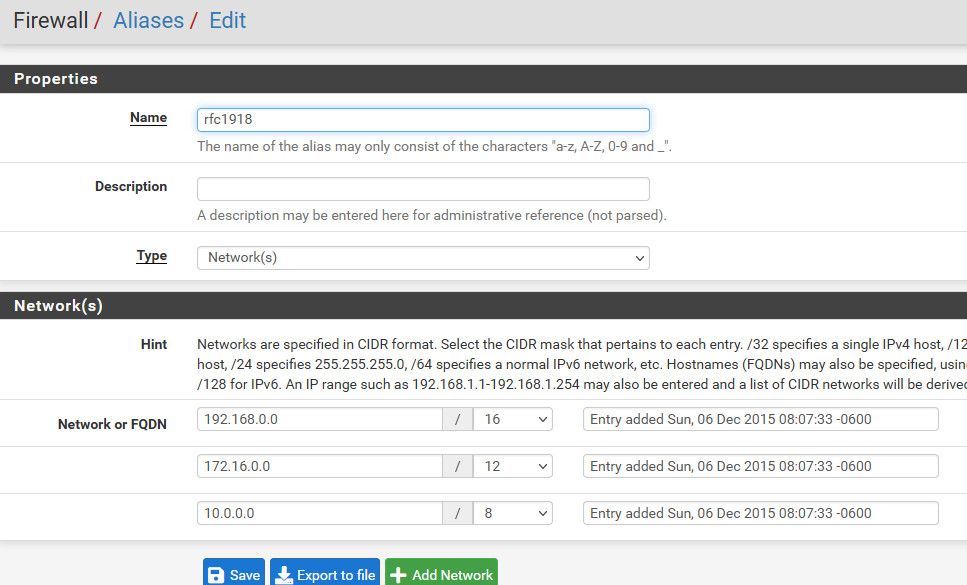
The rfc1918 is an alias that contains all the rfc1918 space, which I assume is what you would be using on your other networks ;)
You for sure could tweak as you desire. But this is an example interface I use for showing how to do specific set of rules. This is basic locked down setup.. Where I allow min stuff like ping pfsense IP on this vlan for testing connectivity. Allowing dns and ntp to pfsense IP and blocking all other access other than internet.
the block "this firewall" rule is there to keep this network from accessing the pfsense web gui or other things via the wan IP, which is normally public and could change. That is the use of the "this firewall" built in alias - it contains all the IPs on pfsense..
I use reject vs block - since this is a local network, no reason to let it spend cycles trying something to just time out. So actually send it a reject saying you can't get there!! Normal block would work too.
-
@djacquens You can do this with two rules, which might be clearer:
block LAN to (other networks)
allow LAN to anyIf you create an alias for your internal networks there is an "invert match" checkbox in the rule edit page so you can "allow LAN to not-local" in one rule. Vaguely I seem to recall reading about issues with the inverting, over the years...never done it myself.
-
@steveits yeah it would be possible to use bang rule (inverse/negate) But I wouldn't suggest that.. especially for someone new to firewalling in pfsense.
Better to use explict rules - much easier to read, and yes there can still be some issues if vips with inverse rules I do believe.
-
@djacquens said in Allow any to WAN interface only:
What rule am i supposed to set?
But first, what is "WAN Net".
Let's presume you WAN is 10.0.0.3/24, then your WAN net is 10.0.0.0/24 is 10.0.0.1 to 10.0.0.254. That's not what you would call 'the Internet'.
And you can't even route 10.0.0.x as it is RFC1918 so not routable over the Internet.The (or a) solution is rather simple :
You have 3 LAN interfaces, lets name then LAN1 LAN2, LAN3.
On LAN1 you put :
A first rule that forbids (block) any traffic from LAN1 to go to LAN2.
A second rule that forbids (block) any traffic from LAN1 to go to LAN3.
A third rule that allows (pass) any traffic. Thus going out of the WAN.On LAN2 you put :
A first rule that forbids (block) any traffic from LAN2 to go to LAN1.
A second rule that forbids (block) any traffic from LAN2 to go to LAN3.
A third rule that allows (pass) any traffic. Thus going out of the WAN.ON LAN3 you put .... well, I guess you get it by now.
-
@gertjan yup another solution to the problem.. But if I am locking down an interface, I would also add the "this firewall" in there to keep them from talking to the wan IP and access gui, etc.
-
Thank you all for these very interesting replies!!

David