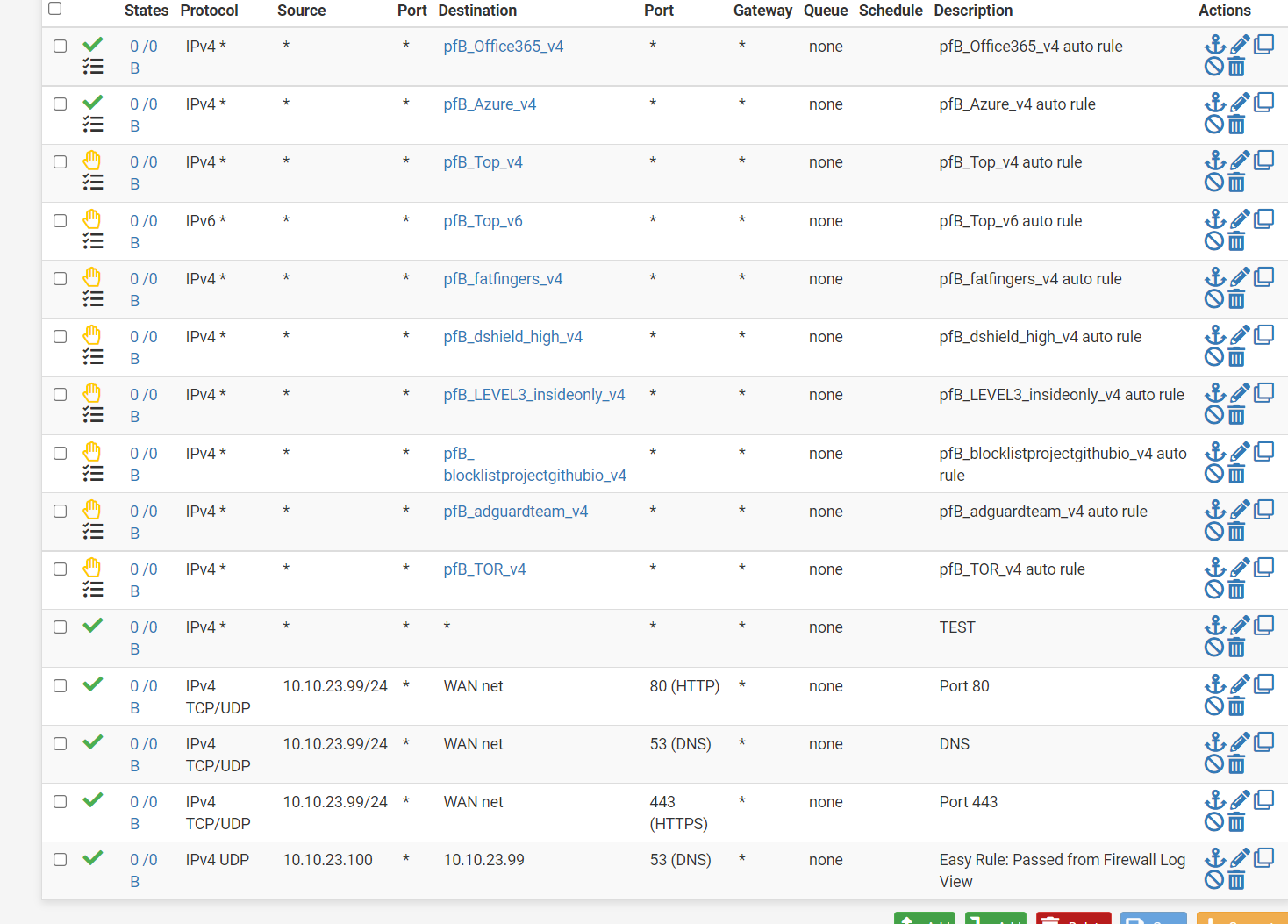
VLAN an Firewall rule not matching
-
@interessierter where did you set these rules, when you create a new interface vlan or native no rules are created.
Posting of your rules and what your seeing in the firewall log as blocked would be helpful in helping you figure out what is not right.
-
@johnpoz I have now under Firewall Rules a seperate Tab for the VLAN. On this VLAN I have created this rules with hand
-
@interessierter and if you do not show us them, how do we know if they are right?
Clearly they are not correct if you say you allow X on vlan Y, and your showing a block on vlan Y interface as blocked.
Maybe you allowed only tcp and what is being blocked is udp, maybe what your seeing in the blocks is out of state traffic ?
Without actually seeing the rules and what is being blocked..
-
-
@interessierter couple of things.. Wan net is NOT the internet, its just the Wan net.. So no that is not going to allow for internet.
Since you put in your test rule that is any any - are you seeing blocks?
Also vs ANY for the source, the any should be set to the "net" of that vlan.. Unless you had downstream networks, and this vlan was transit, should limit the source to the net interface is connected to.
I don't see any hits on any of those rules either they are all 0/0 - so is your client even talking to pfsense? On this vlan interface?
-
@johnpoz said in VLAN an Firewall rule not matching:
@interessierter couple of things.. Wan net is NOT the internet, its just the Wan net.. So no that is not going to allow for internet.
Since you put in your test rule that is any any - are you seeing blocks?
Also vs ANY for the source, the any should be set to the "net" of that vlan.. Unless you had downstream networks, and this vlan was transit, should limit the source to the net interface is connected to.
I don't see any hits on any of those rules either they are all 0/0 - so is your client even talking to pfsense? On this vlan interface?
I have tried as source everything, that was the last. There is also no change when I set it to the IP address or subnet as source.
Tried to put ANY ANY, does not change the situationI have on the firewall rules 3 tabs, the first one is the main without any VLANS. The screenshot only show the VLAN where my client is in. And yes, this network contains clients that are also working. It feels like that the main rules are blocking this.
-
@interessierter said in VLAN an Firewall rule not matching:
It feels like that the main rules are blocking this.
The lan rules have ZERO to do with what a vlan can do..
Let see these blocks your seeing..
-
@johnpoz I know that there should no relation. But when I have a ANY ANY Rule, and still the log tells me the default rule block the request, than it must be something else
-
@interessierter Hm after a restart of pfnblocker it works
-
@interessierter Please show us the blocks... And your rules - I want to see if there is any triggers 0/0 like you showed that none of those rules have matched.
-
@johnpoz its solved, its working after a reboot of pfnblocker
-
@interessierter said in VLAN an Firewall rule not matching:
@interessierter Hm after a restart of pfnblocker it works
The Part of DHCP is working now.
I got a xaomi vacuum cleaner, and this device needs WLAN to work fully. However I want to seperate this device from the rest of my network, but I strugle here.I have created vlans, a seperate WLAN SSID, and tag this SSID of VLAN ID 4000. This is configured on the switch between, the AP and the pfsense. But right now all other devices are NOT tagged with vlans, I have to do that step by step. However I want to start with the new xaomi device.
What I want to do is, to allow on the VLAN 4000 only Internet access, but DENY all access to my existing network infrastructure. I have tried several DENY rules on pfsense, but the access is still possible.
How should such a rule look like to work?
thanks -
@interessierter here is a typical common configuration for a locked down vlan

Create an alias that contains all the rfc1918 space, this way as you add more vlans you don't have to worry that they would not be blocked.
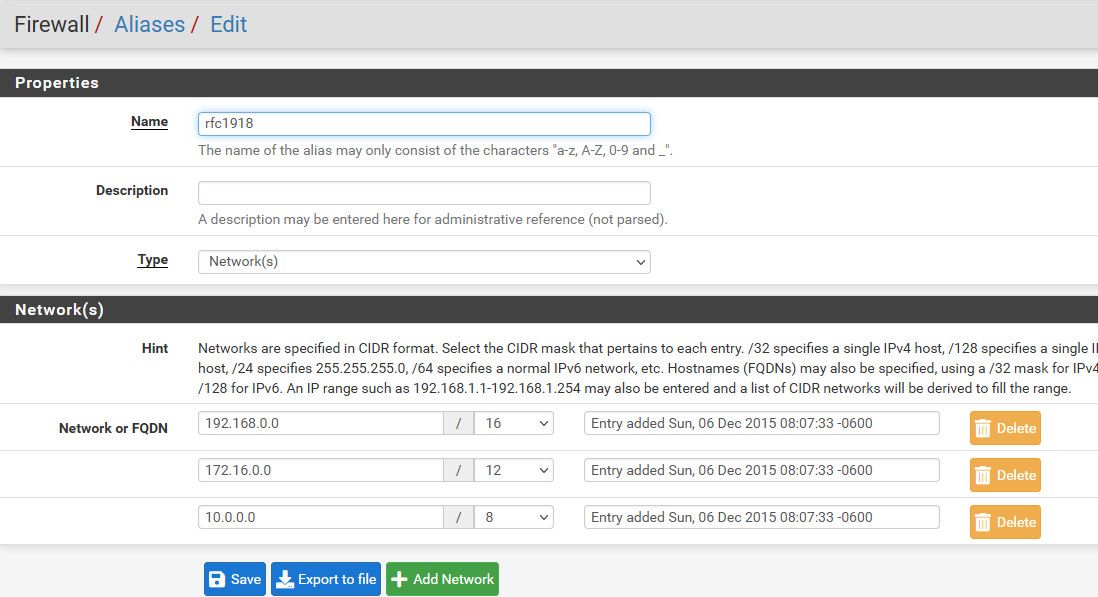
Certain services are normally required like dns, etc.. But if the device points to outside for dns, you could remove that, same with ntp, and if you don't want it to ping its gateway.
But this is a very limited vlan setup. It can not talk to anything on local networks, only internet
-
@johnpoz I have a Alias with 192.168.1.0/24 and this Firewall rule to block:
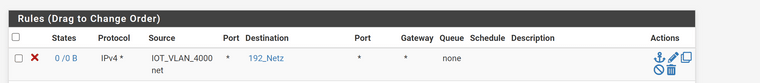
But the browser access to 192.168.1.30 is still possible. The Test Client is in 10.40.23.99 net.
-
@interessierter did you clear states after you created a block rule?
States are evaluated before rules, so if there was an existing state, that state would allow it before your rules are even looked at.
I don't see any triggers on that rule.. It shows 0/0 for states - so it was never evaluated.
Do you have any rules in floating that would allow the traffic?
-
@johnpoz I have found this in the logs. It seems like all traffic will be blocked, only the connection to 192.168.1.30 is working. Why is that threaded differently?
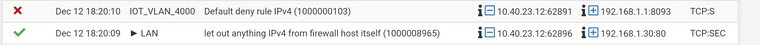
-
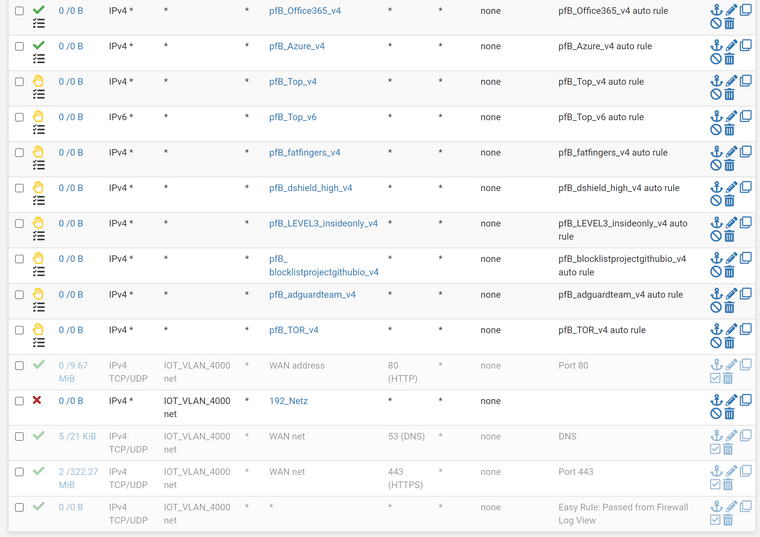
@interessierter the other rules on this vlan. No floating rules
-
@interessierter well your rule is not triggering, again you have a 0/0 for states..
You created your alias wrong maybe..
Rules are evaluated top down, first rule to trigger wins.. no other rules are evaluated. If default deny rule is being trigger then non of your rules above it either block or allowed were triggered.
As to that lan rule anything from the firewall itself are you natting this vlan for some reason?
-
@johnpoz The Alias is correct:
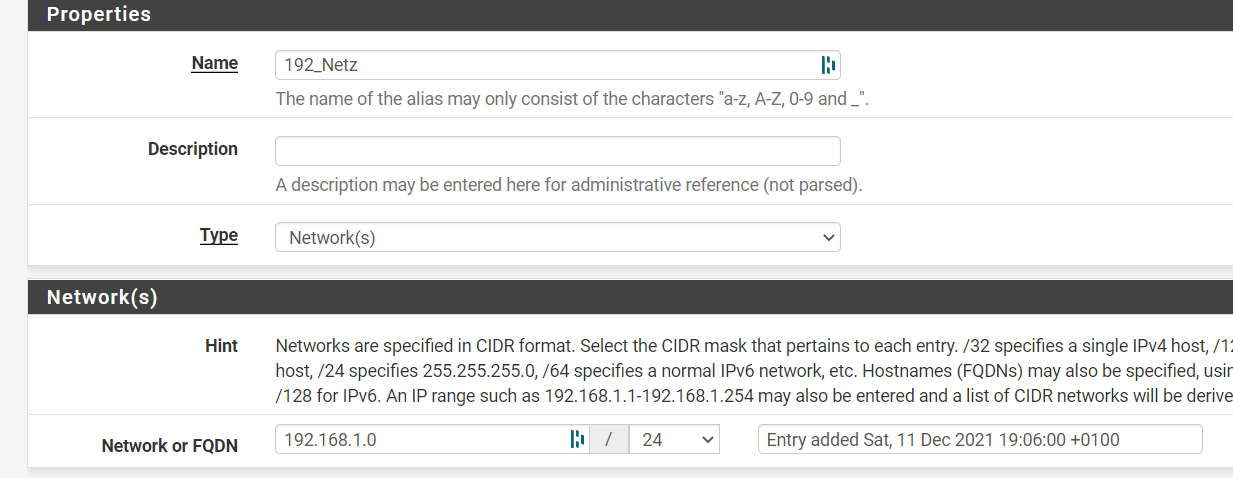
OK the Block rule was not on the first position, but it does not make any difference. Access is still possible.
What I found is here some old NAT rules from a TEST for VPN:
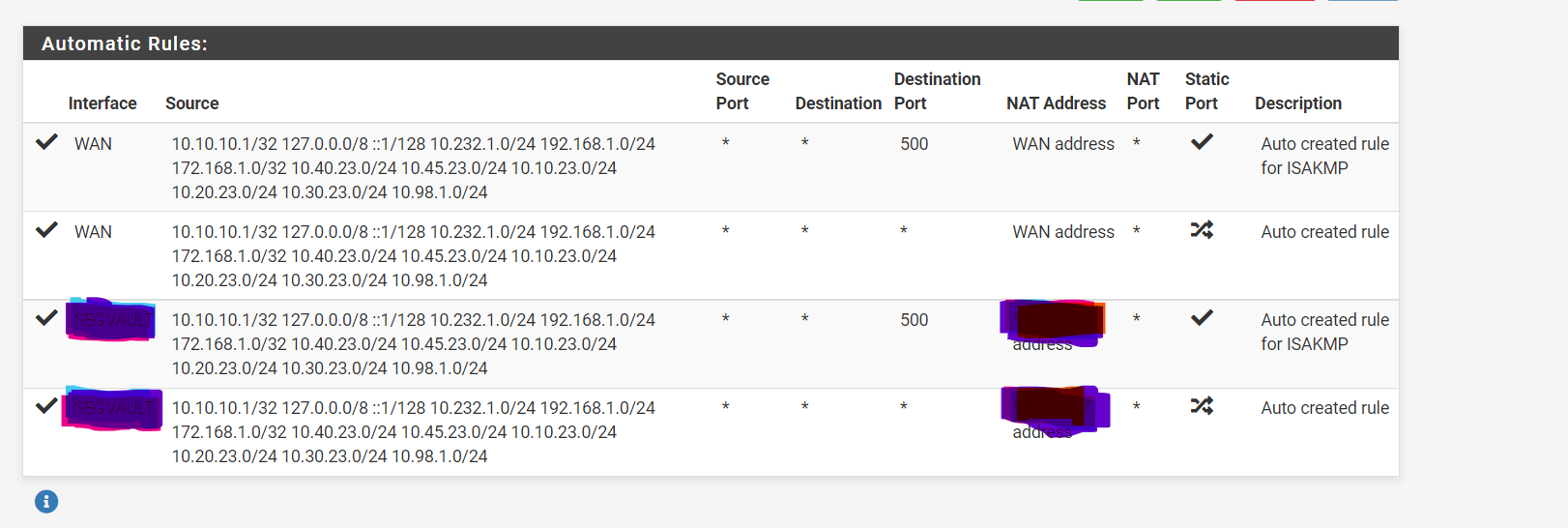
-
@interessierter said in VLAN an Firewall rule not matching:

Why are those IP ranges identical and why LAN has a triangle. Maybe your NAT rules are wrong? Better show all the NAT rules and Portforwarding too.
Or start with a fresh install.