Suricata - Snort IPS Policy selection
-
Hey folks,
I have suricata installed and I was wondering what is meant by "Snort IPS Policy selection".
if i check "use IPS Policy" it doesn't allow me to select all the snort rules, plus it gives me the option to choose various scanning profiles, from mild to wild..
Anyone out there feel like taking the time to tell me about this? I've been trying to find the answers online but it seems to be either one or the other without any description of the differences.
Which is better? if i enable "use ips policy" the process seems more efficient.. definitely cuts back on cpu resources.. but i don't care about that because i'm already overpowered as it is..
Thanks!
-
The Snort Subscriber Rules (and only those rules, not the Emerging Threats rules nor any other available rules) have added metadata tags in them that are put there by the rule authors and the Snort VRT (Vulnerability Research Team). These tags associate certain rules with an IPS Policy. There are four defined policies, but one of them is for testing only. The four policies are "Connectivity", "Balanced", "Security", and "Max Detect". The fourth one, "Max Detect", is for testing only! Never enable that policy on a production system. It will generate a ton of likely false-positive alerts.
The policy names indicate the philosophy of the rules selected by the policy. "Connectivity" means only rules that detect severe threats are enabled for blocking, while rules for other less severe threats are either not loaded, or are set to alert only. "Balanced" means more rules are selected to be enforced, but there is a rising possibility of false-positive alerts and blocks depending on what constitutes "normal traffic" in a given network. "Security" goes farther by enabling more rules, and having them block traffic. But there is also a much higher potential for false positives with this policy. I never recommend users pick this one unless they want to baby sit their IDS/IPS 24-hours a day to clear false positive blocks. I always recommend users begin by using the "IPS Connectivity" policy for several weeks once they decide to enable blocking. When you first install Snort or Suricata, you really need to run at least a month with no blocking enabled to get a feel for what kinds of alerts are going to be generated in your network. Then you can evaluate them to determine if they are false positives. For those, you likely want to suppress those alerts or disable those specific rule SIDs.
For each IPS Policy defined in the metadata tags, there is an associated action given for the rule. The action can be ALERT or DROP. For rules that are detecting threats the authors deem critical and severe, the action will probably be DROP for all policies. To give an example of the policy name works, some rules can be found in more than one policy. In fact, that's quite common. But the difference is that in the "Connectivity" policy the rule's designated policy action might be ALERT, but for the "Security" policy its action might be DROP. So the same rule, when used in multiple policies, likely has a different action in at least one of the policies. So maybe "ALERT" when the IPS-Connectivity policy is selected, but "DROP" when either IPS-Balanced or IPS-Security is selected.
There is a second Policy Mode drop-down selector under where you select the policy. That drop-down lets you set how the "action" metadata tag associated with each rule in the selected policy is handled. "Policy" means the action is determined by the metadata tag. "Alert" means force all the IPS Policy rules to be alert only (even those the metadata tag flags for drop).
Because the whole idea of using IPS Policy is letting the rule authors (presumed to be the experts) determine what rules are loaded and what action they take, manual selection of the Snort rule categories is disabled when using an IPS Policy. You can, however, use the SID MGMT features to still manually add Snort rule categories. But you would want to be careful and not duplicate what the IPS Policy is already doing.
-
so are you saying that by checking ips policy and choosing one of the 4 profiles, it "basically* automagically applies the snort rules from the list and saves me from having to go through said list and check each one? (connectivity applies the fewest snort rules, while Max detect applies them all)?
thanks for your time!
-
@jc1976 said in Suricata - Snort IPS Policy selection:
so are you saying that by checking ips policy and choosing one of the 4 profiles, it "basically* automagically applies the snort rules from the list
Hi,
yes
 , it is predefined at some level - ( in most cases we use the balanced setting)
, it is predefined at some level - ( in most cases we use the balanced setting)for other rules, for example ET use SID Mgmt...
pls. use Bill's great descriptions from the past...
https://forum.pfsense.com/topic/143812/snort-package-4-0-inline-ips-mode-introduction-and-configuration-instructions/55?lang=en-US
https://forum.netgate.com/topic/158515/using-suricata-sid-mgmt
https://forum.netgate.com/topic/128480/how-automatic-sid-management-and-user-rule-overrides-work-in-snort-and-suricata
++++edit:
f.e.:
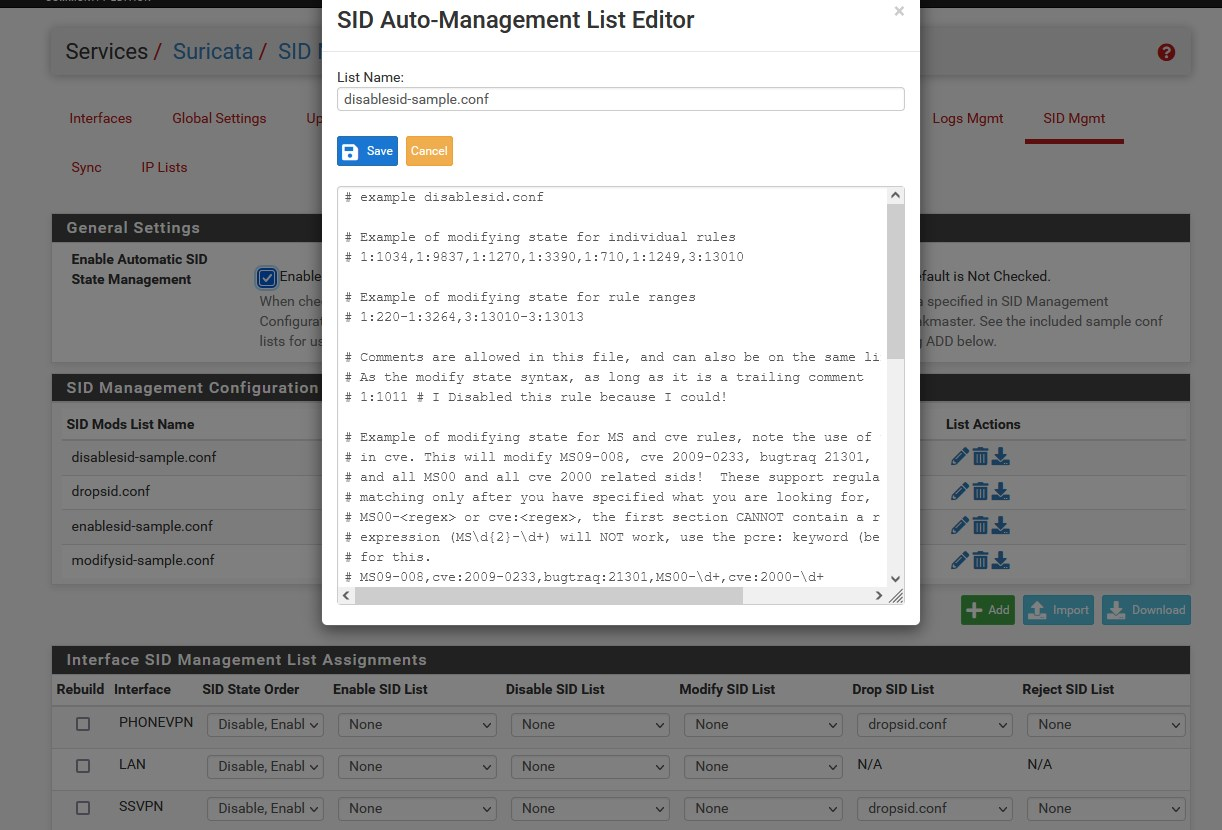
-
@daddygo definitely need to go over the whole "sid" thing... i haven't done anything with it.. no clue how to go about configuring it.
does that mean that while suricata is running, it's effectively doing nothing?
-
dropsid.conf.txt @jc1976 said in Suricata - Snort IPS Policy selection:
does that mean that while suricata is running, it's effectively doing nothing?
hmmm
 YES :) and NO
YES :) and NOYuppp...
as Bill has described many times many rules are depending on the supplier (# comment is in this state - this determines whether they are loaded into "memory") and most of the time its just an alert, as the ET rules - in IPS
and the process does nothing else with it, so you can specify in dropsid.conf which rules should be in DROP action
I won't talk about enable and disable here, because it is clear in Bill's description, although DROP is also clear :)
+++edit:
f.e.: dropsid.conf (in txt, because the forum SW)
dropsid.conf.txt -
I opened those sample sid conf files a few times however they seem to be just templates that i have to add to. is that the case?
or do i just specify each conf file under each list heading and ... well... there ya go?
-
@jc1976 said in Suricata - Snort IPS Policy selection:
they seem to be just templates
exactly, templates created by Bill (do you know that he is the package maintainer here? Suricata and Snort :))
and
pls. take a look for example at one of my home configurations that I uploaded and you'll find out everything
dropsid.conf.txt (in TXT, but TXT does not read, I just put it up in this format because of the forum software)
++++edit:
rename it simply this: dropsid.conf+++edit2:
or if you want to preserve the original template file (would be a good idea) then, for example:
mydropsid.conf or etc.