Configured pfSense 2.5.2 as OpenVPN Server - Use OpenVPN Client On Android - Problems With SSL/TLS
-
Hi,
I am new to pfSense but have managed so far to get it working with some packages.
However, I configured pfSense as an OpenVPN Server with a view to connecting my Android mobile to the box I am using.
I used the wizard and exported the client to my mobile with no problems.
I dl'd OpenVPN Connect from the Android Play Store and imported the profile with no problems.
The VPN connects ok but when I connect to pfSense to use the webGUI with https, I get an
error with SSL/TLS relating to the certificate. The webpage with Chrome on Android tells me the connection is not private and reports the error NET::CERT_COMMON_NAME_INVALID. When I press the website error icon in the search bar, it states : Servers certificate does not match the URL.
I can connect if I do not use https but this is not what I want to do.
The net for use with the VPN is 8.0.0.0/24. The gateway is allocated as 8.0.0.1 and my phone as 8.0.0.2. The LAN is net 192.168.1.0/24.
I am happy to provide settings for the OpenVPN Server to let you see settings.Settings for OpenVPN Server first;
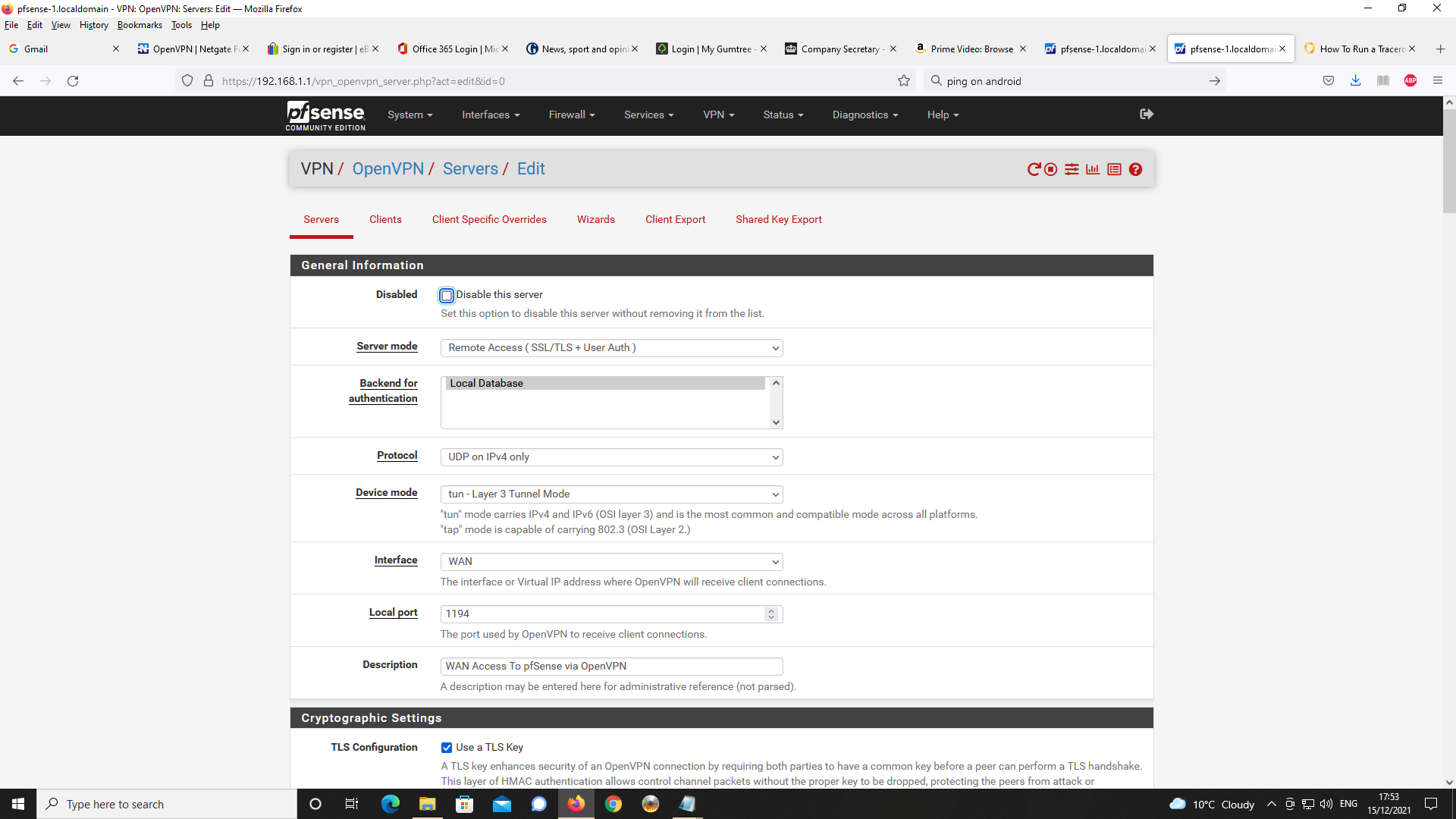
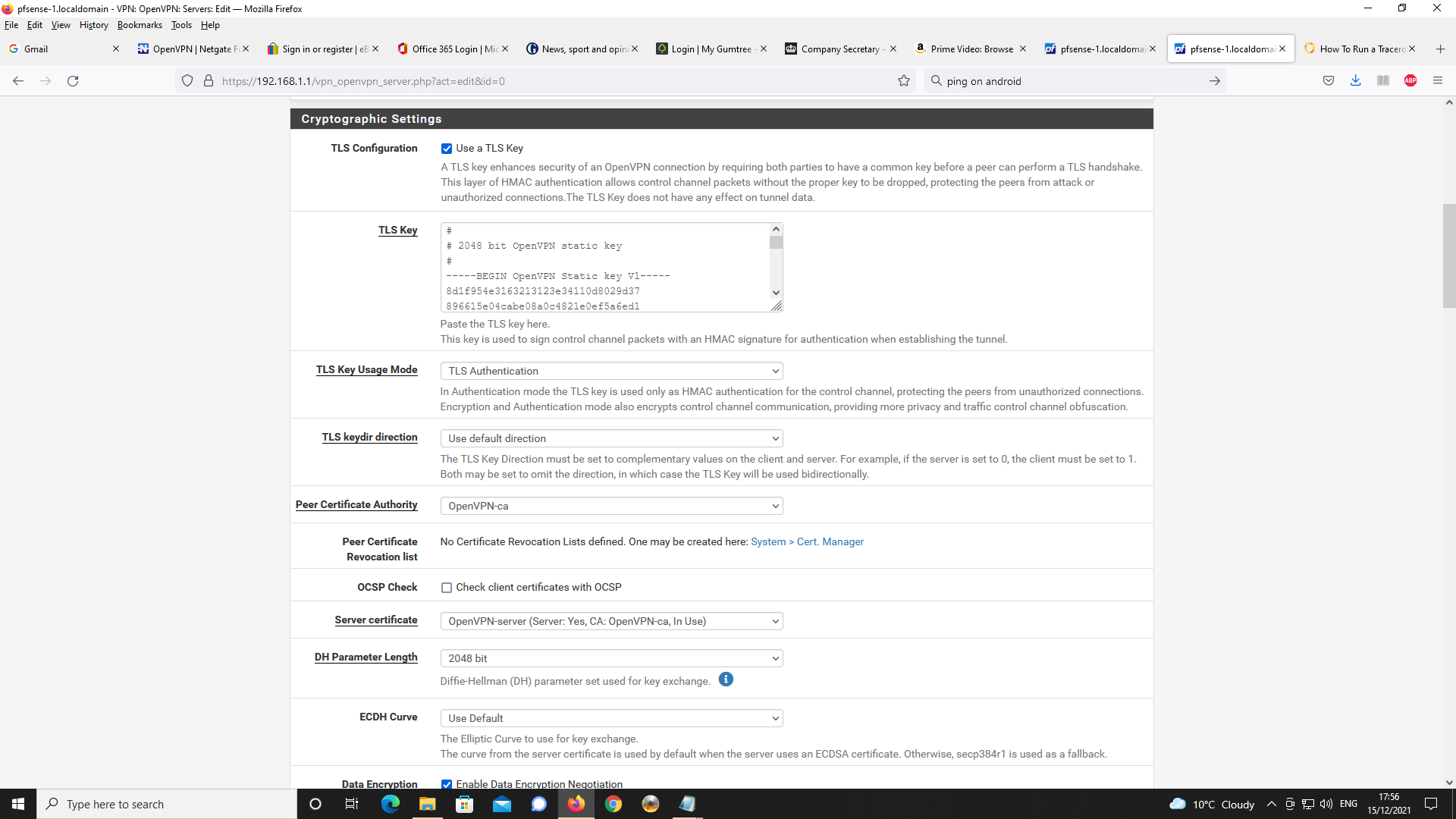
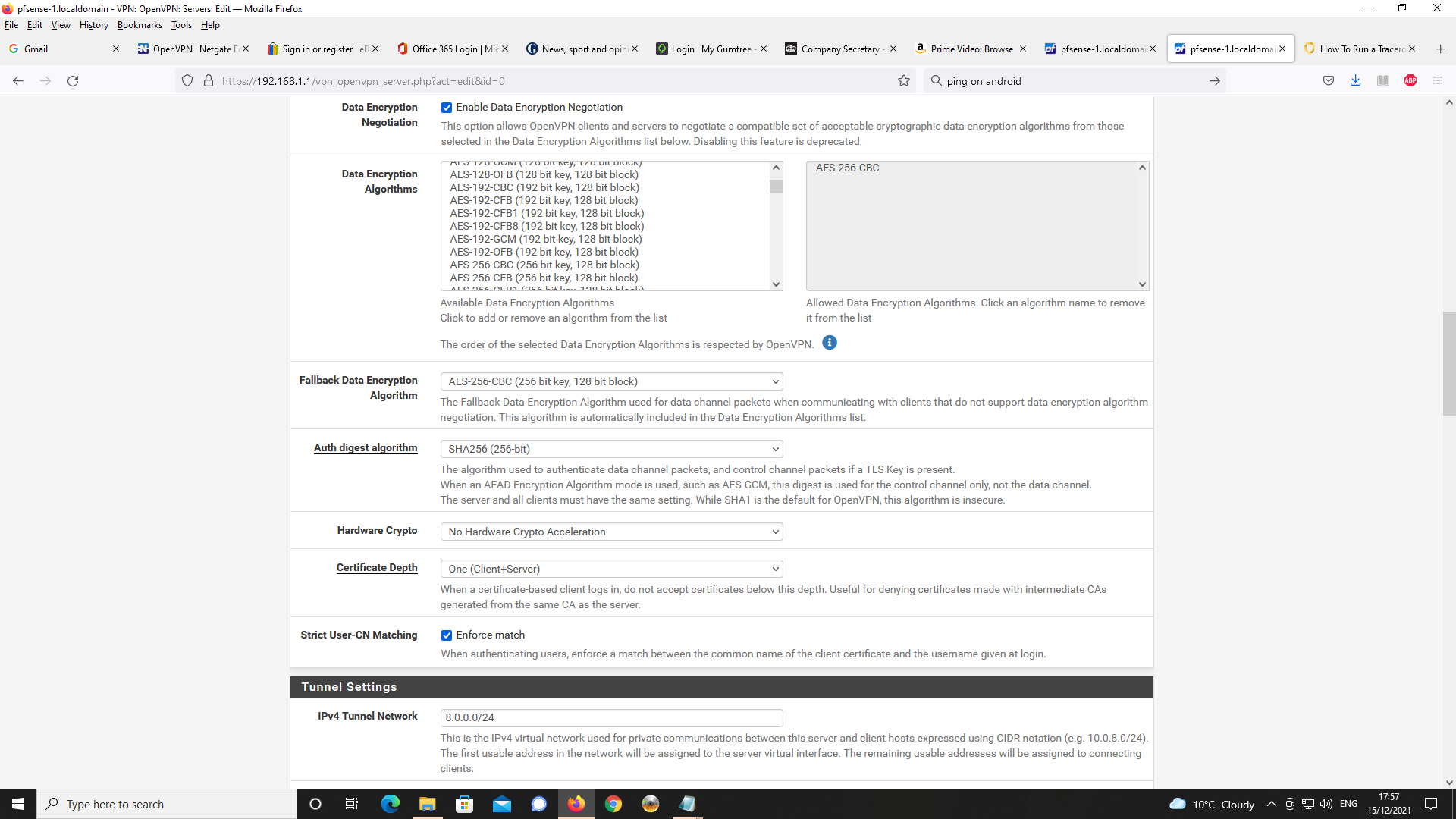
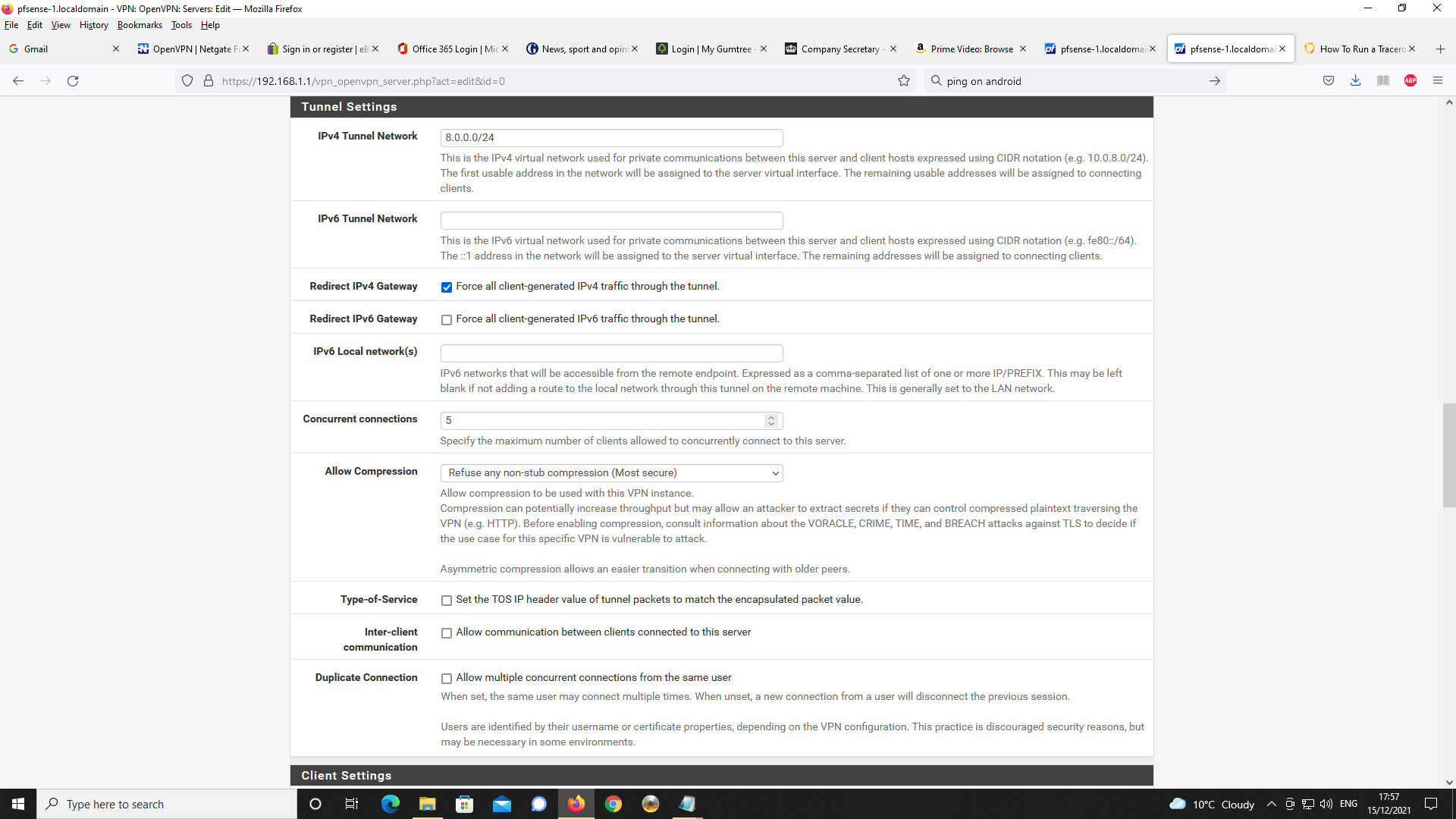
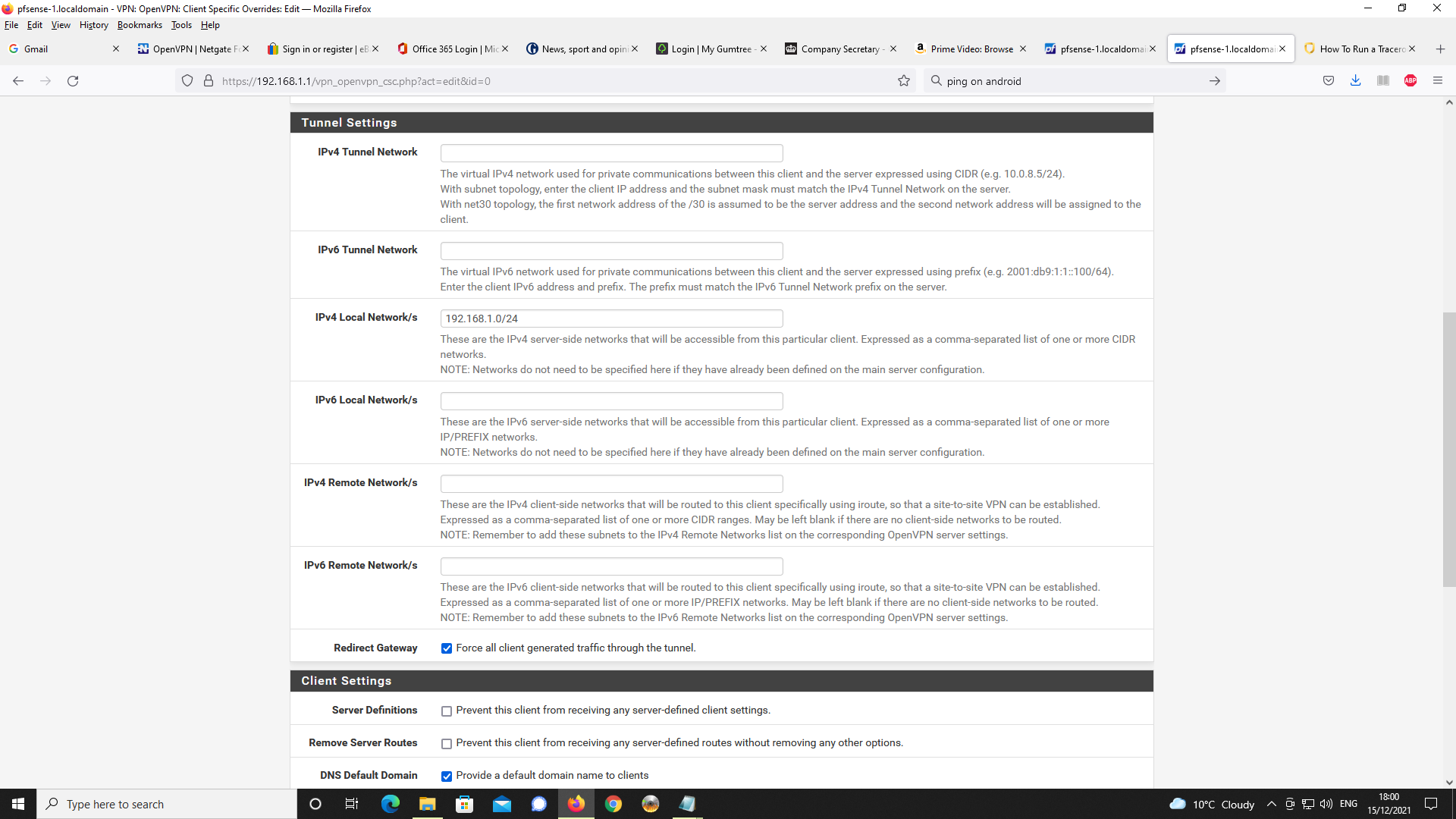
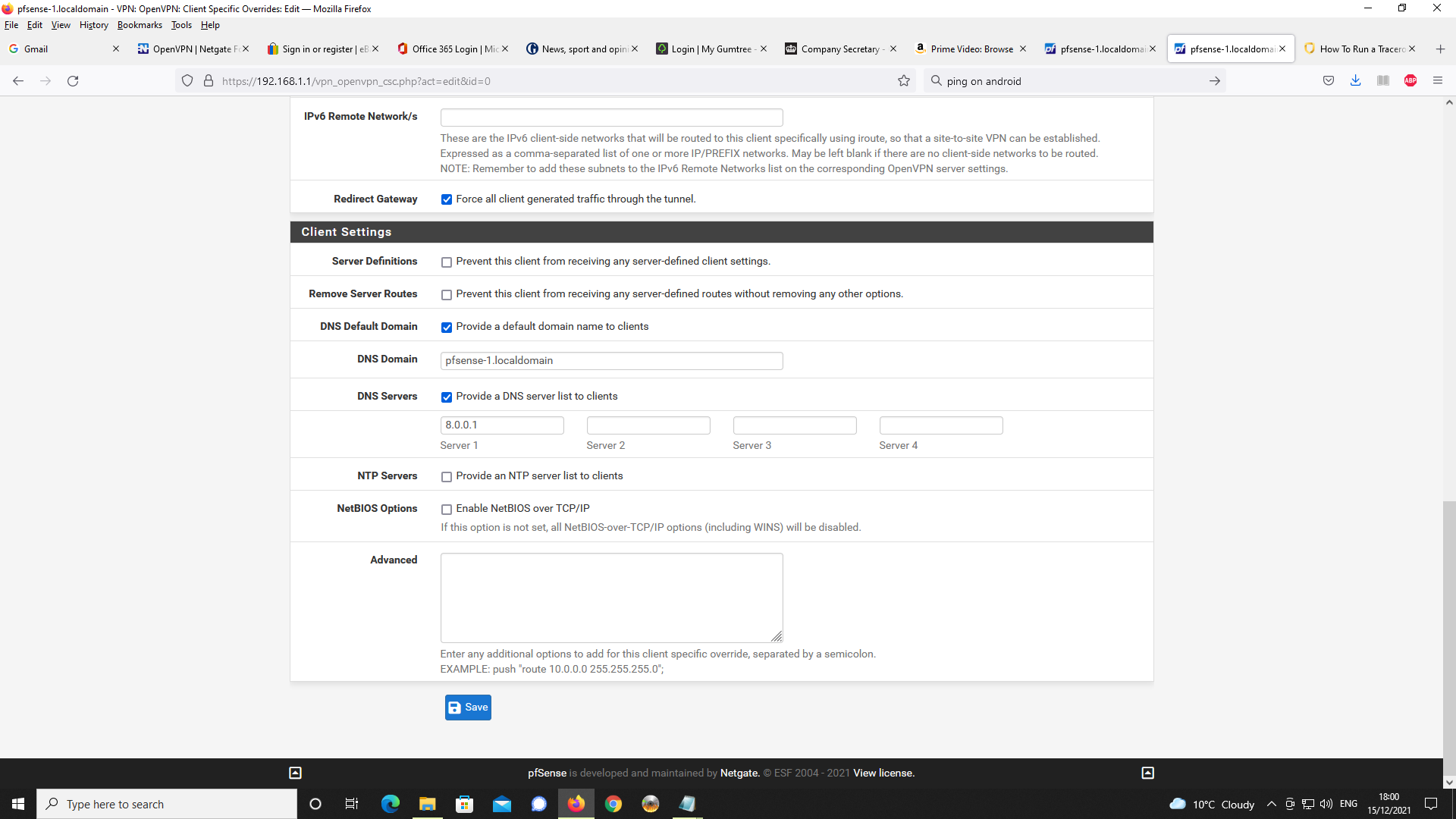
Next Client Specific Overrides
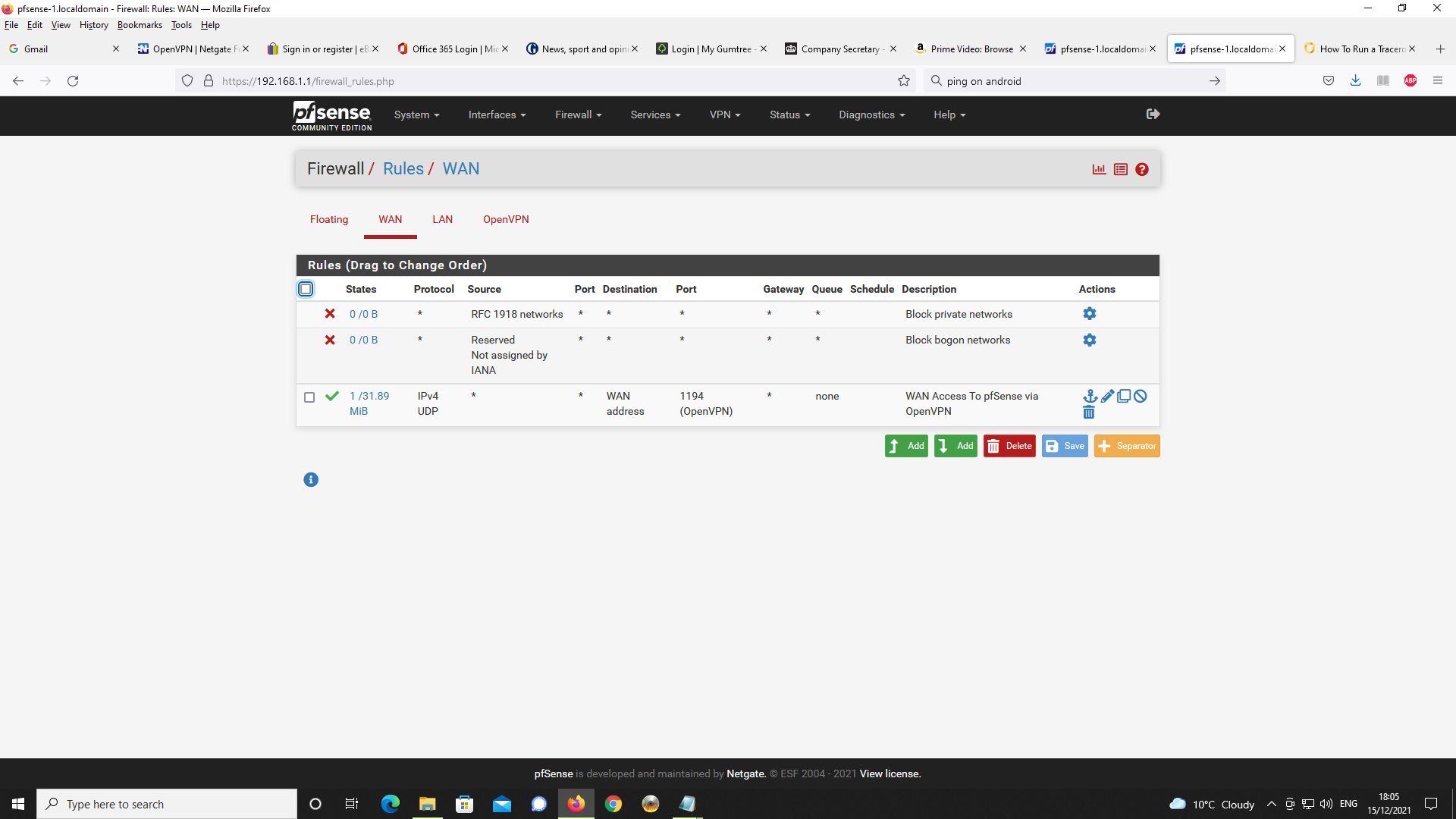
Firewall Rules for WAN
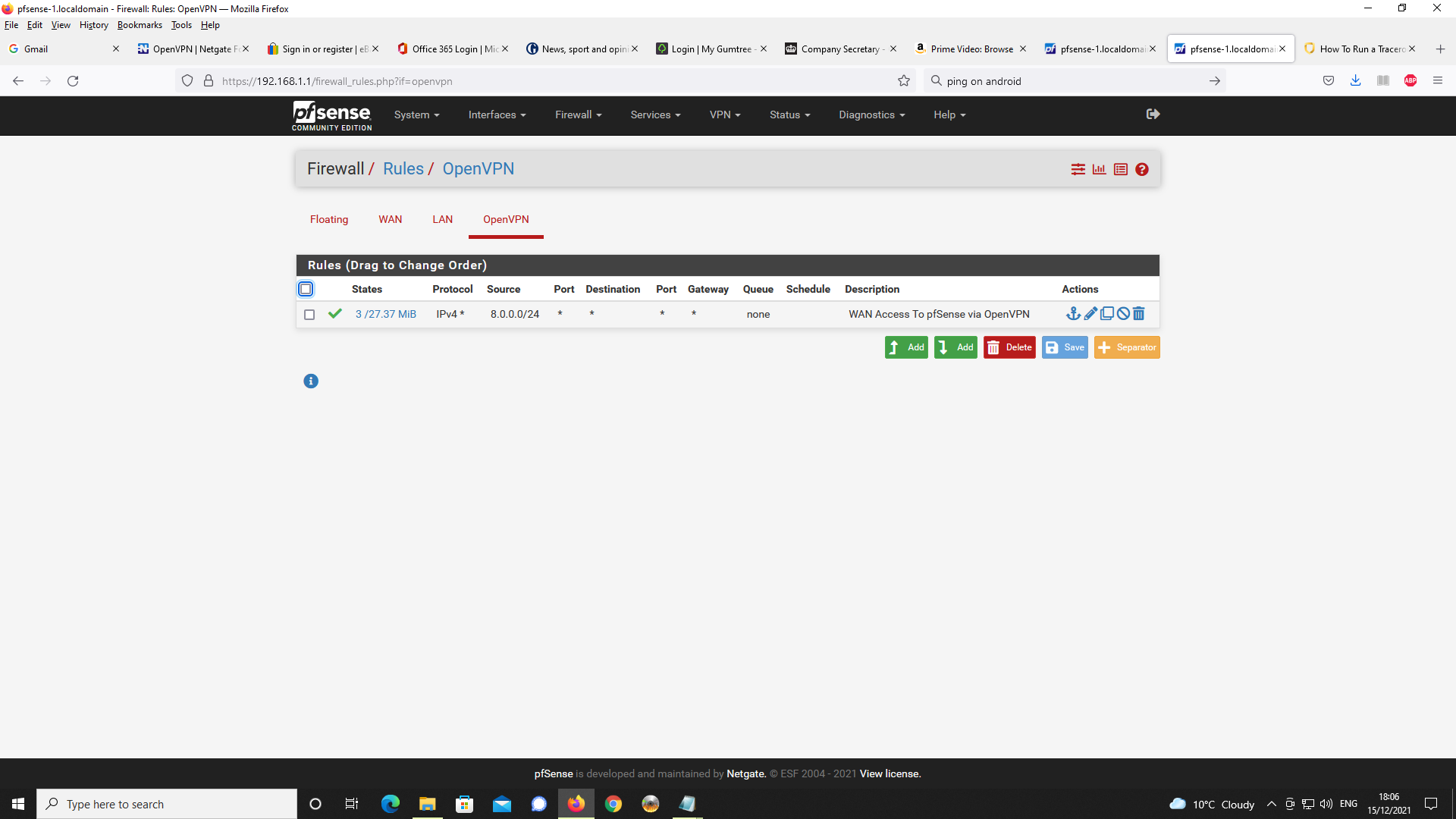
Firewall Rules for OpenVPN
Firewall NAT Outbound Settings
Status OpenVPN when connected
Services DNS Resolver
DNS Resolver ACLs
System CAs
System Certificates
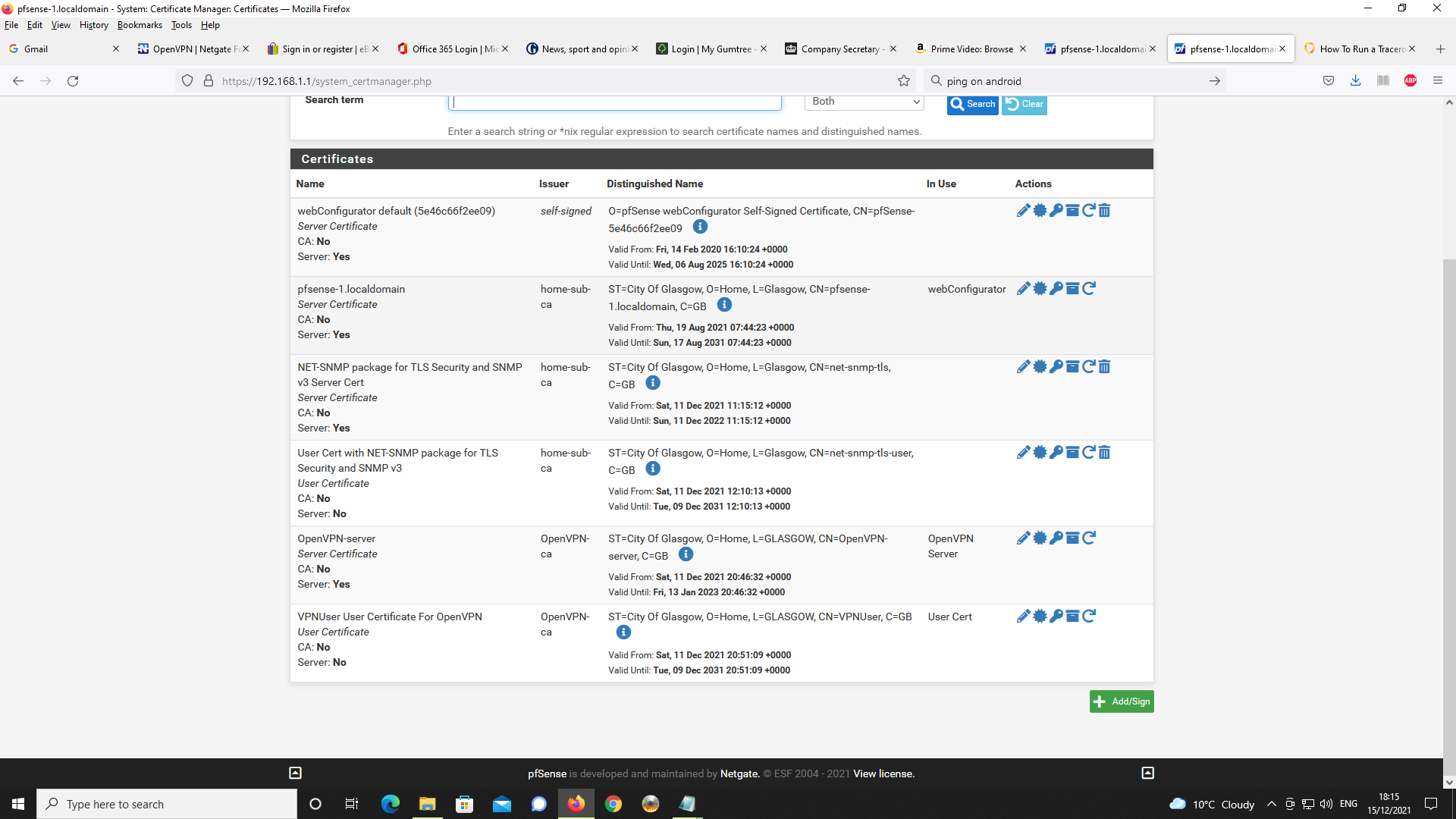
System User Manager - OpenVPN User Account
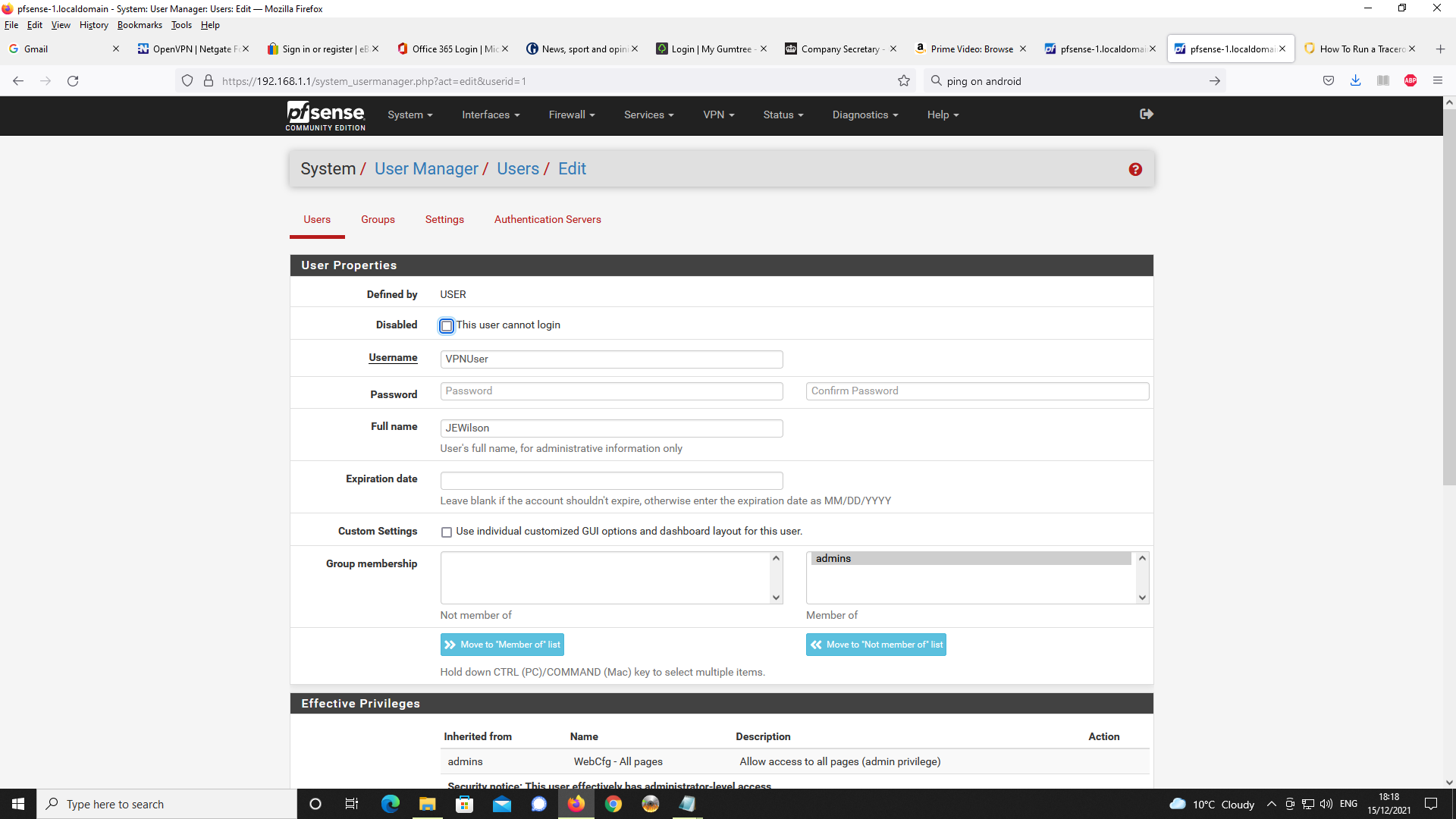
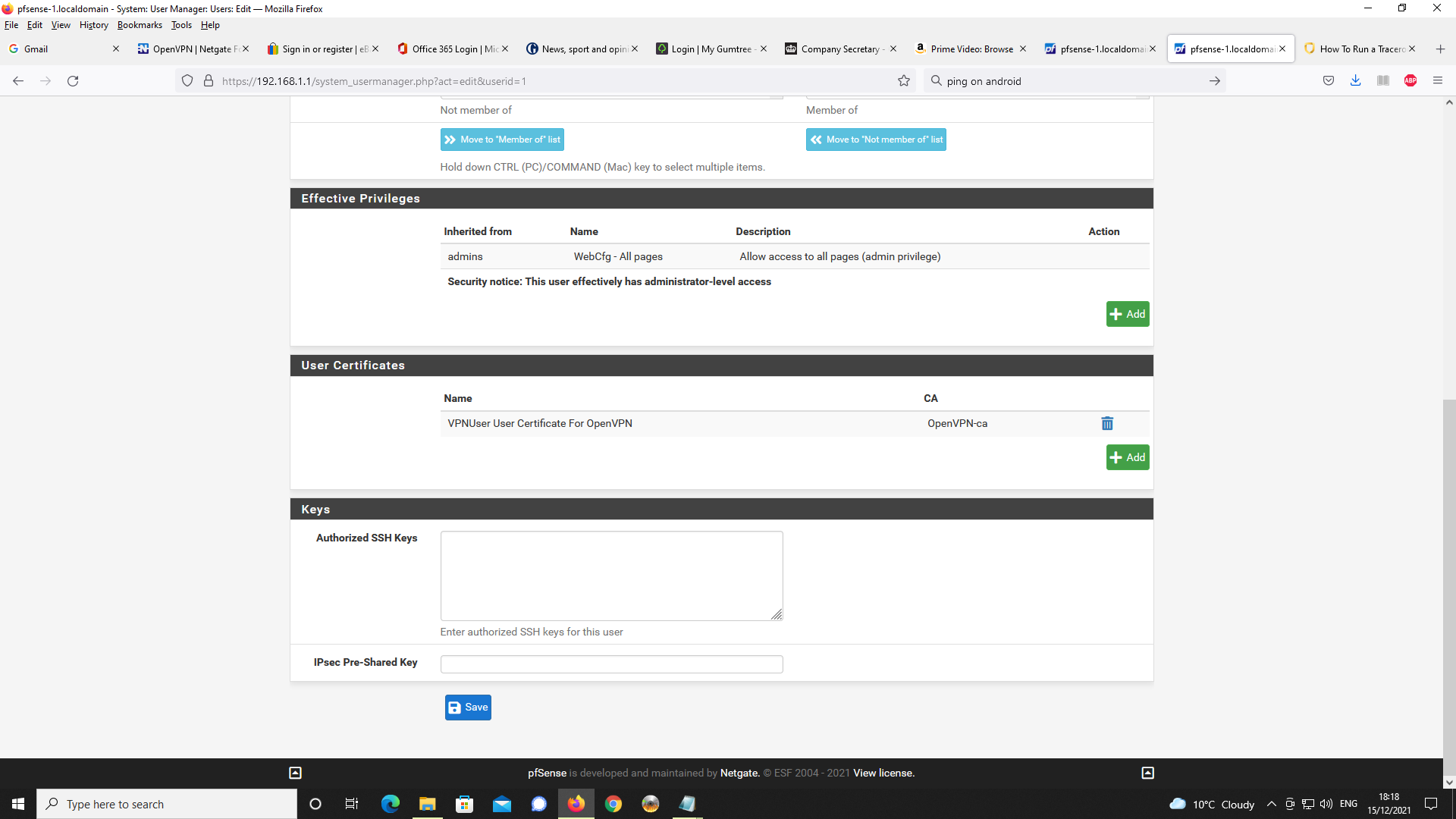
Would appreciate some help and insight into this.
Thanks in advance.
J -
@jewilson said in Configured pfSense 2.5.2 as OpenVPN Server - Use OpenVPN Client On Android - Problems With SSL/TLS:
The net for use with the VPN is 8.0.0.0/24. The gateway is allocated as 8.0.0.1 and my phone as 8.0.0.2. The LAN is net 192.168.1.0/24.
Hi,
More problems are possible here, say Android Chrome... :-) + 8.0.0.0/24
It seems to me that you are using IP ranges arbitrarily
what the hell is this ?8.0.0.0/24
GW: 8.0.0.1this is not your area, do you know this for example ?

8.8.8.8 ???pls. use the RFC private IP ranges for the internal IP addresses of the VPN connection
https://datatracker.ietf.org/doc/html/rfc1918+++edit:
Otherwise, if you're on your internal network, say via VPN, it doesn't matter if it's http or https in the pfSense admin interface, because the VPN encrypts your connection
https://docs.netgate.com/pfsense/en/latest/recipes/remote-firewall-administration.html
-
Thanks for the heads up.
You're right. I didn't think re - the 8.0.0.0/24!
Will take on board your recommendation and change to something more appropriate.Again, of course you are correct the VPN will protect web traffic whether http or https over
the link. Double doh!Funny, I figured there would be no isssues with Android Chrome.
I don't have any issues on my desktop browsers with Chrome and Firefox on Windows 10.
These connect via https to the WebGUI ok with no issues.
With Chrome on Win10, I imported the relevant certificates into the Windows Certificate Store
and it worked straight off the bat. With Firefox on Win10, I imported these into the Firefox certificate store that's built into the browser and again, no issues.With VPN Connect on Android set up as it is, albeit incorrectly per your comments, I can log in to the WebGUI via http only and the status dashboard reports me as being logged in as admin:@8.0.0.2(Local Database). So no issues with access.
I'll work on the changes you recommend.
Thanks, again for the insight.Regards,
J -
@jewilson said in Configured pfSense 2.5.2 as OpenVPN Server - Use OpenVPN Client On Android - Problems With SSL/TLS:
Funny, I figured there would be no isssues with Android Chrome.
Nothing serious has happened... :)
Yes, you're not the first to think you can roam between IP ranges...
Pls. trust no one especially BigTech companies, ergo Google = Android, hahahha
Let me know if you get stuck and I'll help and/or the forum.BTW:
pls. never forgetalthough it looks like a desktop Chrome, it's different on the phone, much worse....
-
@daddygo
HiSeem to have this matter resolved.
First, used a Class C private IP address subnet for the VPN client.
Second, the matter with the Android Chrome Browser SSL/TLS was resolved with
revoking the certficate I was using for the WebConfigurator, deleting it and creating
a new one. Only with the new one for the SAN (Subject Alternative Names) I specified the FQDN of the firewall as well as supplying the IP address for the local LAN and the WAN subnet.Connected without the error message after importing the relevant certs into the Android Cert
Store.Having checked the OpenVPN logs, I am getting a number of warnings such as;
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1601', remote='link-mtu 1585
WARNING: 'keysize' is used inconsistently, local='keysize 256', remote='keysize 128'as well as number of messages stating;
Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #6 / time = (1639703647) 2021-12-17 01:14:07 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
and
TLS Error: incoming packet authentication failed from [AF_INET]92.40.192.240:33082
The VPN link appears to be ok and holds up
I have a concern these may be producing problems. Do you have any insight as to how these
could be mitigated?
As stated, I have tested this on Android mobile and it could be down to link quality with 4G
but I'm not sure.Any insight as to these?
Thanks for your consideration.
Regards...