Interface range setup
-
the common default networks are 192.168.0/24 and 192.168.1/24 - just use others than that and should be fine.
But its less and less of an issue to be honest, atleast if you have a phone.. For remote access - its becoming more and more rare to have to rely on the local wifi network.. I have seen 700/50 on my phone 5G connection... I could give 2 shits if there is a local wifi network ;) its not going to be that fast even if there was one ;)
My network I would really only ever need to get to while remote would be 192.168.9/24 - My others are 192.168.2-7, etc. Where you could run into a problem is the local site doing 192.168/16 or 10/8 ;) hehehe have seen this a few times.. If your concern is overlap of the remote network you would be coming from, its prob best to pick some random networks in the 172.16/12 space.
If your really worried about remote access while your away.. You could always setup some sort of other connection to use if your vpn fails for some reason. Chrome desktop vpn thing, or teamviewer, etc. Those almost always work as long as box you want to get to on your network has internet. Then you can get to your network stuff via that box your connecting to.
-
I'll reply on the items above when I can.
But one thing is not clear to me, how these IP ranges can overlap...
What's the point of the entire IPV4 if you can't use the same address in your LAN...
Now, despite this seems obvious, I'm not sure how the VPN could impact (precisely).
I can think of a VPN with the same IP range (that gives you the same IP range or even the same IP), but not the remote machine where I need to connect, is this the case?Every VPN I've seen out there gave me an IP like 10.x.x.x
Based on that, I should be fine with 192.168.x.x or eventually 172.16.x.x
The problem is that these are all different ranges, can they stay on the same firewall? (basically on different interfaces)Will the routing work through the WAN? (assuming I have the correct FW rules)
-
As mentioned, you can't have overlapping networks. I ran into that problem when I traveled with my work several years ago. So, I changed my home network to something in the 172.16.x.y range, which I have only seen in one other network. And yes, you can have multiple ranges on the same firewall, so long as they are different networks. Pfsense is a router, which takes care of all that.
-
@jt40
Imagine the VPN as network interface on the client computer. It's a virtual interface indeed, as well as it is on pfSense, and the client normally routes the server sites network over this interface, where the servers virtual IP is the gateway for routing. Let's say the servers LAN is 192.168.0.0/24 and the client want to access 192.168.0.8.But if the clients LAN is 192.168.0.0/24 as well, cause he didn't change the preset configuration of his router, so when the client calls 192.168.0.8, the packet will go out to his LAN interface and not be routed over the VPN.
Hence he is not able to access anything on the remote site. -
Thanks everyone, very interesting.
What about the gateway assigned to all the interfaces?
In my case, the gateway can be either the ISP router or directly the WAN (which will receive the gateway IP).How the other LANs will connect to that gateway?
- Is it supposed to happen automatically?
- Shall I add the gateway on each interface? But if that changes, I can't be there to change it every time...
- It can't be the WAN IP interface, because that should be the public address --> One IP, one interface, right?
-
@jt40
You should really take some basic network lessons. This is not the right place for such questions.What about the gateway assigned to all the interfaces?
In my case, the gateway can be either the ISP router or directly the WAN (which will receive the gateway IP).You mean the WAN IP on pfSense?
The gateway is the next node on the way. So if a packet go towards the internet, the gateway is the next IP to the WAN interface, mostly the ISP router.How the other LANs will connect to that gateway?
Is it supposed to happen automatically?Yes. The LAN devices have also a gateway set in their network configuration (it is set automatically when using DHCP). This is the LAN IP of pfSense.
Shall I add the gateway on each interface?
Never do this. This breaks upstream traffic.
-
@viragomann said in Interface range setup:
@jt40
You should really take some basic network lessons. This is not the right place for such questions.What about the gateway assigned to all the interfaces?
In my case, the gateway can be either the ISP router or directly the WAN (which will receive the gateway IP).You mean the WAN IP on pfSense?
The gateway is the next node on the way. So if a packet go towards the internet, the gateway is the next IP to the WAN interface, mostly the ISP router.How the other LANs will connect to that gateway?
Is it supposed to happen automatically?Yes. The LAN devices have also a gateway set in their network configuration (it is set automatically when using DHCP). This is the LAN IP of pfSense.
Shall I add the gateway on each interface?
Never do this. This breaks upstream traffic.
I think I got confused because WAN is not actually WAN in my case, is just another LAN port, I forgot that detail.
Having said that, normally I'd say that each LAN interface should point to the gateway (ISP modem/router).
Instead, if PfSense does it automatically without the need to specify the gateway on each interface, good to know, but that's not obvious I believe...I think that the routing happens automatically because the WAN (LAN) interface has the gateway assigned and it's on the same IP range as the ISP modem/router, with the same mask and it looks like another host.
Then, once a packet reaches the ISP modem/router, it is directly sent to the WAN.If it doesn't work in this way, please explain.
-
@jt40 said in Interface range setup:
I think I got confused because WAN is not actually WAN in my case,
It is still a WAN.. Any interface this used to get off your network(s) and talk to other network(s) is a WAN!! In context talking about that router.
The pfsense interface that talks top your ISP be it to modem another router, or 47 routers inline before it gets to the internet.. Is still the WAN interface of pfsense. It is how you get to the internet.. So its the wan..
-
@jt40 said in Interface range setup:
What about the gateway assigned to all the interfaces?
In my case, the gateway can be either the ISP router or directly the WANHow the other LANs will connect to that gateway?
It can be a little confusing. You have to think of gateways from pfsense perspective not your network architecture perspective.
From pfsense perspective you specify in pfsense gateways which pfsense can use as “servers”. These are external to your network.
You do not need to specify interfaces over which pfsense provides gateway access to pfsense “clients”. Pfsense is a router so this is what it does by default (limited by the firewall rules).
WAN (LAN) interface has the gateway assigned and it's on the same IP range as the ISP modem/router, with the same mask and it looks like another host.
Pfsense defines it as a WAN because it has a gateway specified in pfsense.
Your ISP router may well defines it as a valid client because it has an IP within the ISP modem set mask range.Btw
Why are you using an ISP router at all?
A modem would make sense to convert the physical modulation on the wires to your house to ethernet. Most combined modem / routers can be put in bridge mode to avoid double NAT. -
@johnpoz said in Interface range setup:
@jt40 said in Interface range setup:
I think I got confused because WAN is not actually WAN in my case,
It is still a WAN.. Any interface this used to get off your network(s) and talk to other network(s) is a WAN!! In context talking about that router.
The pfsense interface that talks top your ISP be it to modem another router, or 47 routers inline before it gets to the internet.. Is still the WAN interface of pfsense. It is how you get to the internet.. So its the wan..
This is the critical point, the gateway assigned to the LAN makes it a WAN, I didn't know it :D
Pfsense defines it as a WAN because it has a gateway specified in pfsense.
Precisely speaking, it's the same network, but it's another device or another NIC. My ISP modem/router is 192.168.0.1 and my PfSense WAN interface it 192.168.0.200, both with mask 255.255.255.0 or it wouldn't work, it's the same network but different network interfaces.
In essence, we can say that when you define a gateway and you assign it to an interface, the NIC becomes a WAN because the packets leave the NIC going to another device (Gateway IP), not another NIC on the same PfSense box (LAN traffic).
(even though here I have a doubt, I think that PfSense makes the distintion because these interfaces are devices attached on the system, it's not a pure network definition, it's the way PfSense categorizes a LAN or a WAN, which can be also similar to other routers. Otherwise if you look at the IP range ONLY, each interface is already a different network, which is also mandatory)It's not even a concept to be part of the same network in this case, it's the point of having the same mask which will allow the correct definition of IP range.
Did I understand correctly?If this correct, I should also be able to reserve 192.168.10.1 from the ISP router for the PfSense WAN interface, I had a few troubles initially between my browsers and other bs... I'll test it again.
Your ISP router may well defines it as a valid client because it has an IP within the ISP modem set mask range.
Yes, in this case it's on the same network, 100%.
Btw
Why are you using an ISP router at all?
A modem would make sense to convert the physical modulation on the wires to your house to ethernet. Most combined modem / routers can be put in bridge mode to avoid double NAT.I have vDSL or sort of, so I can't use that kind of modem with the optical fiber to home, which after that gives you the possibility to use a CAT 6a cable.
In any case, I can probably reduce the load on the ISP router disabling the WIFI, it doesn't properly put the modem in bridge mode if I remember well, but it improves performance. My modem doesn't support bridge mode, I think there is a trick like that thing for the WIFI, I need to search a bit.
I'll transfer all the WIFI traffic to another AP anyway. -
@jt40 said in Interface range setup:
This is the critical point, the gateway assigned to the LAN makes it a WAN
Almost.
The gateway assigned to the interface makes it a WAN interface. The interface could be a NIC or VLAN. If it does not have a gateway it is not a WAN.@jt40 said in Interface range setup:
I have vDSL or sort of, so I can't use that kind of modem with the optical fiber to home, which after that gives you the possibility to use a CAT 6a cable.
You have a combined modem router. You need to use it's modem function. Also using it's router function will make your network harder to manage. You make it a pure modem by putting the combined modem / router in bridge mode. It will then function just as a modem converting the fibre optic signals to copper Ethernet.
-
pfsene then handles all other network interface functions.
-
all other router functions on the ISP combined modem router will be disabled. So yes you will need a different access point for wifi.
-
-
Thank you everyone.
Today I dedicated a lot of of time on this setup:
(the issues I've met are uncountable :D , but let's start with the point that the connection works! )
)Modem --> pfsense --> switch --> Ui 6 lite AP
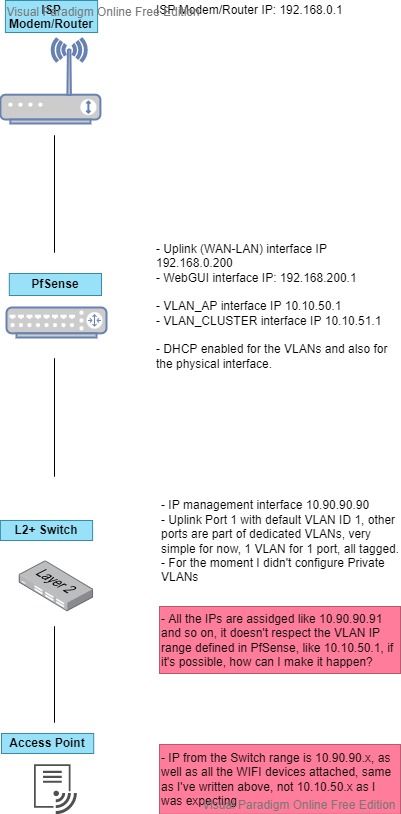
I have a couple of questions:
- As you can see highlighted in red, the VLANs IP range is not being respected, or not considered at all, I'm not sure why...
- I have no rule on the WAN interface, but the traffic goes through anyway :D
- In PfSense, on the UPLINK interface to the modem I have the following rule: allow ALL from this network (UPLINK net) to ANY.
I think this is the reason why the traffic is going through... The WAN interface is not considere at all, the traffic is being taken from this range and then forwarded to the gateway 192.168.0.1, the fact is that this interface doesn't have a gateway assigned, only the WAN has it... - I would need to create a floating rule, where each LAN can't connect to any other LAN, unfortunately I didn't see a simple option to do it... So, each LAN that I have now can go everywhere, that's how I got my internet traffic fully working...
This implies that each interface has access to PfSense and the modem, very bad... I tried with inverse rule but I can't find the way to stop all the traffic from/to other LANs...
-
@jt40 said in Interface range setup:
As you can see highlighted in red, the VLANs IP range is not being respected
You need to set up VLAN on the switch so the access point only see's the VLAN's you want it to see.
I suspect using VLAN 1 for your Management interface s a bad idea as some switches use that as the default so it behaves differently to other VLANs
You show an AP on your ISP modem. Are you intending to continue to enable that function or is that just historical?
-
@patch said in Interface range setup:
@jt40 said in Interface range setup:
As you can see highlighted in red, the VLANs IP range is not being respected
You need to set up VLAN on the switch so the access point only see's the VLAN's you want it to see.
I suspect using VLAN 1 for your Management interface s a bad idea as some switches use that as the default so it behaves differently to other VLANs
You show an AP on your ISP modem. Are you intending to continue to enable that function or is that just historical?
I already have VLANs on the switch and PfSense.
It seems that I need to configure the VLANs in the AP as well :D ... I'll also create different networks to make better separation between certain devices, or maybe not initially.
I forgot to mention that the default VLAN ID is 1 on the switch, as every other switch I think, but it's not tagged as far as I know, I mean, it's not enabled, I only tagged the way I wanted, the ports I wanted.
To keep it even easier anc cleaner, the VLAN of the AP will be only on that switch port, I won't use that VLAN for anything else.Yes, I'll remove the wireless from the modem, it will have less chances to crash and it's also less safe.
-
@jt40 said in Interface range setup:
It seems that I need to configure the VLANs in the AP as well
If the AP has multiple SSID then yes that is normally implemented as a different VLAN for each SSID.
If you just have one wifi network all with the same SSID then you just need to configure your switch to only connect to the AP via that VLAN (the AP does not have to be aware of VLANs at all.
-
@patch said in Interface range setup:
@jt40 said in Interface range setup:
It seems that I need to configure the VLANs in the AP as well
If the AP has multiple SSID then yes that is normally implemented as a different VLAN for each SSID.
If you just have one wifi network all with the same SSID then you just need to configure your switch to only connect to the AP via that VLAN (the AP does not have to be aware of VLANs at all.
Thank you.
I didn't understand that last sentence though.
Maybe you mean that the AP is not a switch, so actually I can't configure VLANs there, I can only tell the AP to tag the packets with the respective ID, is it right?I actually need to have 2 VLANs on the AP, or so called 2 different networks in Unifi, so I'll create 2 different networks which match the VLANs IP from the switch.
Then, in the switch I'll assign 2 different VLANs to the same port, is it right? -
@jt40 said in Interface range setup:
2 VLANs on the AP, or so called 2 different networks in Unifi,
Then you configure your switch to pass those 2 tagged VLANs to the Unifi AP
Btw, what is you swithch
-
I have a D-Link L2+ switch, it means that it does't have all the L3 functions.
I made some extensive testing, below you find the setup.
The graph is the same as before, I didn't change the network layout, I just changed the settings.-
The switch is configured with static IP 10.90.90.90, but there is also the option to set it with DHCP, I didn't think it was a good idea :D . This refers to the management interface only, normally, but it's also the start of the DHCP range in somehow, below you'll find more info.
-
The connecte devices get assigned all with the DHCP after that range, verified with cables :D but also with the AP, which wonderfully ignore the VLAN setup.
-
On the AP, if I set the VLAN ID on the network that I created, it fails to assign the IP address to the devices, and then the device fails to join the network.
I noticed that for a while, as IP it receives my public IP (LOL) instead of one from the DHCP, and the mask is 255.255.0.0, I never specified such mask, it must be the mask of that range, which in any case both don't make any sense in my private network... -
The connection works only if I specify the default LAN network auto-created by Unifi, which has the same exact setup as the one created by me, but you I can't touch the VLAN ID, it seems not existent or maybe by default is 1...
Interestingly, the range is 192.168.1.0/24, if I create it, in DHCP it takes 192.168.2.0/24, I also tried to set it up manually following the VLAN IP on PfSense (10.10.60.1), as well as the DHCP, but it fails immediately -
Prior these tests, I didn't have an IP interface on the switch.
-
I've set it up and it's the same result, it nicely ignores the IP range that I've set, same for the VLANs IP ranges in PfSense.
-
In case you wonder, this is under the L3 functions on my switch, I defined the VLAN tag again at L3.
Previously I created the VLANs in L2 and tagged the same in PfSense, but it didn't sort out any effect. -
There is an option for port truncate which I believe I should use, but I wonder why it didn't flag me that conflit, it may be a bug or a feature not present there, because normally this is a problem, if you have more than 1 VLAN per port you need to configure port truncate for my knowledge.
- I don't have a trusted DHCP server in the switch, what's the main IP on Pfsense? Due to this missing info, I still didn't test that functionality on the switch...
The whole point is that I was expecting PfSense to act as a DHCP server......... I already defined all the DHCP ranges, with all the firewall rules and all the VLANs tags... Not sure what else is missing to make it work with the switch...
-
I noticed that every device behind the switch takes as a router or DHCP server the IP of the PfSense interface where it's attached to, is this expected?
-
In any case, at the moment the switch assigns IPs as 10.90.90.91 and so on...
The UPLINK interface has IP 10.90.90.89, which becomes the router/DHCP. That's how it is respectively described in my phone and my desktop.
In all this mess:
-
I get into internet with stupid FW rules like "Allow ALL from Network to ANY", so basically I have the setup I don't want, plus the setup I should not have :D .
-
I can also access the WebGUI or PfSense without problems from any interface, I need to resolve this but blocking the traffic to the firewall doesnt' help, so I think I need to write a floating rule for all these scenarios, but with all these VLANs changes etc, it's too easy to screw up or to forget some interface/VLAN here and there... I'm pretty sure to leave some of them behind. How do you deal with these scenarios?
-
Plus, most of the machines can ping each other and eventually ssh etc, that's terrible :D , but I think that proper firewall rules will be sufficient.
-
There is still one main issue, what is the rule that should allow the traffic to the WAN? If I set the followings I can't reach the gateway and therefore internet:
- from this network to WAN net
- from this network to WAN address
- from this network to 192168.0.1 (gateway IP)
- It works only with: from this network to ANY
It doesn't make much sense to me...
-
-
ok, mistatch in the DHCP range :D , it's too late for me guys.
After I changed it, I noticed that the DHCP server is the IP of the UPLIN interface (for the switch) configured in PfSense.
The IPs are assigned correctly, also the AP received a new IP, I had to give it a kick but it works :D , from now on I won't finally lose the connection to the AP!Tomorrow I'll test the VLANs, but if I already got the IPs from that DHCP server instead of the one for each VLAN, then I already know that it's not working properly...
Each VLANs is on a different network range, so it's clearly not working, no space for mistakes here, unless this is an a mistake from top down :D -
@jt40 said in Interface range setup:
this is under the L3 functions on my switch
Thought you said your switch doesn't have L3?
D-Link L2+ switch, it means that it does't have all the L3 functions.
Which is it - what is the model number of this switch.
I need to resolve this but blocking the traffic to the firewall doesnt' help
Then your doing it wrong - and sure and the hell do not need a floating rule.. Nobody can help point out what your doing wrong - if you don't actually show us what your doing.
What are the vlan IDs you set? What are the port configurations of the switch, etc. etc.. What are you firewall rules..